- SQLite数据库文件损坏的可能几种情况(一)
界忆
人工智能数据库SQLite数据库sqlitec++
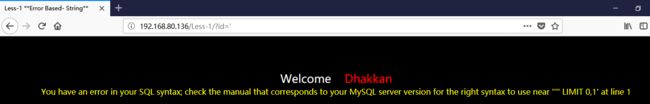
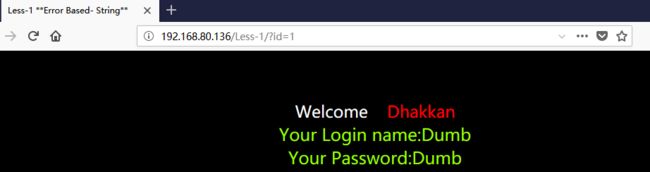
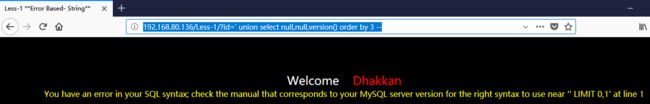
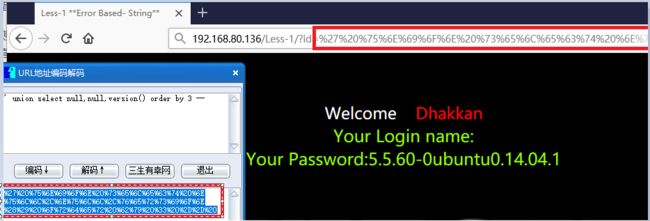
返回:SQLite—系列文章目录上一篇:SQLiteC/C++接口详细介绍sqlite3_stmt类(十三)下一篇:SQLite使用的临时文件(二)概述SQLite数据库具有很强的抗损坏能力。如果应用程序崩溃,或操作系统崩溃,甚至电源故障发生在事务中间,部分写入的事务应在下次自动回滚将访问数据库文件。恢复过程已完全完成自动,不需要用户采取任何行动或应用程序。尽管SQLite可以抵抗数据库损坏,但它
- Jfinal 使用Druid对Sqlserver数据库配置文件中的密码项进行加密解密实现
迟到的微笑
javawebJfinaDruid
由于最近业务表较多,导致我好久没写博客了,今天为大家奉上一篇sqlserver配置文件如何加密和解密。网上看了下有mysql的我是sqlserver的忠实用户,居然没有sqlserver的,我瞬间不淡定了,决定写一篇帮助萌新。首先我们需要一个jar包,网上有,我就不提供下载地址了。第二步就是需要用这个jar来对密码进行加密了。网上有很多是下面这样的写法。这种写法对于懒惰的我来说就是一种折磨。我使用
- sqlite数据库字段类型
鹿灏楷silves
pythonwebsqlsqlite3djangopython数据库
数据库字段类型:字符型字段topic=models.CharField(max_length=)#需要传入参数,设置字符串的最长长度email=models.EmailTield()#电子邮箱字段,在CharField基础上,增加了邮箱的正则验证a=models.SlugField()#仅含有字母下划线数字和连字符的字符串url=models.URLField()#url字段,默认长度200字符f
- SQLite可视化管理工具汇总
班力勤
程序员sqlitejvm数据库
截至2012/9/14最新版本SQLiteSpy1.9.1–28Jul2011单文件,界面设计紧凑,较稳定,功能较少,创建表与添加数据均需sql语句,快捷键教方便,作为数据浏览和修改工具极佳,视图编码为utf-8,对gbk2312显示乱码。能满足一般的应用,但没有导出数据表功能,同时只能打开一个数据库文件不支持二进制字段编辑2、SQLiteStudio(推荐)开源免费单文件http://sqlit
- Jfinal+SQLite解决MYSQL迁移表未复制索引问题,完善迁移工具
原mysql表查询存在索引,查询sql含forceindex(字段),SQLite不支持,会报错解决办法,要么删除索引,要么强制执行索引换成INDEXEDBY,Stringselectsql="select*";StringfromSql="fromtableNameforceindex(START_TIME_TYPE)where1=1if(fromSql.contains("forceindex
- 用Flink实现的一个实时订单对账功能, Flink的双流实时对账
1.为什么业务订单数据不用Mysql之类的强事务性数据库监控反而用Flink的实时?一般这种涉及到订单的数据流都要用mysql监控实现,但是鉴于减少mysql的数据库压力和提高更实时性,可以考虑用Flink实时的数据流做实时的参考2.如何处理乱序数据?使用watermark水位保证第一层数据延迟.PS:这里的水位不能设置太长延迟使用processfuntion更加灵活的处理迟到数据,设置一个定时器
- 2024 前端技术指南:从趋势到实战,构建你的知识地图
王旭晨
前端
一、2024前端领域的“破局者”与“新势力”2024年的前端圈依然热闹非凡,技术迭代与行业焦虑并存。React19带来的useActionState与服务端渲染升级,Vite6的多线程编译挑战Webpack的地位,Bun和Deno对Node.js发起的性能冲击,都在重塑开发者的选择。而尤雨溪创立VoidZero融资460万美金,更是为开源商业化注入了一剂强心针。尽管“前端已死”的论调此起彼伏,但技
- Navicat操作指南:MySQL数据库配置与Todo应用部署
像风一样自由2020
数据库mysqladb
Navicat操作指南:MySQL数据库配置与Todo应用部署前言本文档详细记录了使用Navicat管理MySQL数据库,并配置Todo应用的完整操作步骤。适用于使用Navicat作为MySQL管理工具的开发者。操作目标启动MySQL服务使用Navicat连接MySQL数据库创建todoapp数据库配置Todo应用环境变量验证应用正常运行步骤一:启动MySQL服务Windows用户方法1:通过Wi
- 九块九付费进群系统 wxselect SQL注入漏洞复现
0xSecl
漏洞复现v1安全web安全
0x01产品简介九块九付费进群系统是一种新的社群管理方式,用户通过支付9.9元人民币即可加入特定的微信群,享受群内提供的服务或资源。这种模式通常用于知识分享、资源下载、专业交流等社群,通过设置门槛来筛选成员,提高群组的专业性和互动质量。0x02漏洞概述九块九付费进群系统wxselect接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息(例如,管理员后台密码
- Redux-thunk:10行代码重构异步控制权
止观止
#React核心原理深度剖析reactreduxreact-thunk状态管理前端
redux-thunk作为Redux生态中最精简的异步处理中间件,其核心价值源于对“函数型Action”的设计突破。这种范式通过将传统的静态Action对象转化为动态可执行函数,为Redux的单向数据流注入了异步控制能力,成为中小型项目异步管理的首选方案。⚙️一、核心设计:函数型Action(ActionasFunction)传统ReduxAction本质是携带{type,payload}的静态数
- 【MySQL】性能优化实战指南:释放数据库潜能的艺术
文章目录MySQL性能优化实战指南:释放数据库潜能的艺术引言为什么需要MySQL性能优化?性能优化基础知识MySQL性能瓶颈分析1.硬件资源瓶颈2.MySQL内部瓶颈优化配置策略大全内存配置优化InnoDB缓冲池配置查询缓存配置连接和线程配置磁盘I/O优化InnoDB存储引擎配置临时表配置独特优化创意配置创意1:分层存储优化创意2:动态配置自适应创意3:负载感知配置高级优化技巧并行处理优化索引和查
- 毕业设计基于python + flask +mysql + Layui新闻系统项目源码
love0everything
flaskpython课程设计
毕业设计基于python+flask+mysql+Layui新闻系统项目源码介绍该项目采用Flask框架开发,数据库采用mysql。这是一个作业项目。该项目采用Flask框架开发的一个新闻、论坛、博客系统。。前端采用的是layui框架,后端模板是X-admin下载地址:毕业设计基于python+flask+mysql+Layui新闻系统项目源码模块版本PyMysql1.0.2Flask1.1.2M
- Paimon:Range Partition and Sort优化无主键表(Append-Only Table)查询
lifallen
Paimon数据库大数据数据结构javaapache
这个优化是通过对数据进行全局排序,从而让查询时能够跳过大量不相关的数据文件(DataSkipping),极大地减少I/O,提升查询速度。只需要在执行INSERT语句时,通过OPTIONSHint来启用和配置这个功能即可。RangePartitionAndSortForUnawareBucketTableITCase测试文件本身就是最好的例子。比如测试中的这句SQL:INSERTINTOtest_t
- PHP MySQL 读取数据
froginwe11
开发语言
PHPMySQL读取数据引言在Web开发中,PHP和MySQL是两个常用的技术栈。PHP作为服务器端脚本语言,而MySQL作为关系型数据库管理系统,两者结合能够构建强大的动态网站。本文将详细介绍如何使用PHP从MySQL数据库中读取数据,包括连接数据库、执行查询、处理结果等关键步骤。连接MySQL数据库在PHP中,首先需要连接到MySQL数据库。以下是一个示例代码,展示了如何使用mysqli扩展连
- Mysql基本语法到表设计
吴鹰飞侠
mysql数据库
由于笔者之前了解过sql所以此篇仅作复习使用。1.MySQL基本语法1.1创建数据库createdatabaselogin_demo;1.2使用数据库uselogin_demo;1.3创建表CREATETABLEusers(idintprimarykeyauto_increment,usernamevarchar(50)notnull,passwordvarchar(255)notnull,ema
- linux安装Node.js 环境,Docker 环境,Ruby 环境,MongoDB 环境,PostgreSQL 数据库,Go 开发环境,Python 虚拟环境
2401_87017622
数据库linuxnode.js
在Linux上安装其他常见的开发环境可以根据具体需求而定,以下是一些常见的安装步骤:1.Node.js环境Node.js是一个基于ChromeV8引擎的JavaScript运行环境,适用于服务器端开发。安装Node.js:通过包管理器安装:sudoyuminstall-ygcc-c++makecurl-sLhttps://rpm.nodesource.com/setup_14.x|sudo-Eba
- 3步!用代码生成工具秒建SqlSugar Winform项目?手把手教学,小白也能轻松上手!
墨瑾轩
数据库学习oracle数据库
关注墨瑾轩,带你探索编程的奥秘!超萌技术攻略,轻松晋级编程高手技术宝库已备好,就等你来挖掘订阅墨瑾轩,智趣学习不孤单即刻启航,编程之旅更有趣(对比传统开发效率:人工写代码vs魔法生成器,谁才是真正的“代码魔法师”?)代码生成工具——程序员的“魔法棒”你有没有试过用Excel表格生成代码?或者像搭积木一样拼出一个完整的Winform项目?SqlSugar+代码生成工具(比如Database2Shar
- 3步搞定Java漏洞修复?别再让黑客当“家”!
关注墨瑾轩,带你探索编程的奥秘!超萌技术攻略,轻松晋级编程高手技术宝库已备好,就等你来挖掘订阅墨瑾轩,智趣学习不孤单即刻启航,编程之旅更有趣Java城堡的“裂缝”与程序员的救赎想象一下:你的Java应用是一座巍峨的城堡,而安全漏洞就是那些悄悄蔓延的裂缝。SQL注入:像是小偷从窗户溜进来,偷偷改写数据库的账本。XSS攻击:像在城堡里偷偷放了一张带毒的地毯,路过的人会被“刺”伤。SSRF漏洞:像让城堡
- MySQL 索引详解:从原理到实战的全方位指南
一切皆有迹可循
mysqlmysql数据库后端javasql
前言索引是MySQL高性能查询的核心驱动力,合理设计索引能将查询性能提升几个数量级,而不当使用则可能导致严重的性能瓶颈。本文从索引的基础概念出发,深入解析数据结构、分类特性、设计原则及实战优化,帮助开发者掌握索引的核心原理与最佳实践。一、索引基础概念1.索引定义与本质索引是存储引擎用于快速查找数据的一种数据结构,本质是「数据项→数据地址」的映射表类比:相当于书籍的目录,通过目录(索引)快速定位章节
- MySQL 锁详解:从原理到实战的并发控制指南
一切皆有迹可循
mysqlmysql数据库后端javasql
前言在高并发场景下,锁是MySQL保证数据一致性的核心机制。正确理解锁的类型、行为及适用场景,能有效避免数据竞争、死锁等问题,是构建可靠数据库应用的关键。本文从锁的分类、存储引擎差异到实战优化,结合代码示例,系统解析MySQL锁机制的核心原理与最佳实践。一、锁分类:按粒度与功能划分1.按锁粒度划分(1)全局锁(GlobalLock)作用范围:锁定整个数据库实例典型场景:全库逻辑备份(FLUSHTA
- 容器中敏感信息泄露路径排查与修复机制:构建、运行与发布全链条实战指南
观熵
DockerDocker安全
容器中敏感信息泄露路径排查与修复机制:构建、运行与发布全链条实战指南关键词:容器安全、敏感信息泄露、环境变量、构建路径排查、Dockerfile安全、CI/CD安全、镜像扫描、密钥管理摘要:在容器化构建与交付流程中,敏感信息泄露问题屡见不鲜,覆盖了硬编码密钥、构建残留、环境变量注入、配置文件外泄等多个维度。本文将基于真实的工程实践,梳理容器生命周期中潜在的敏感信息泄露路径,结合Trivy、Dock
- 浅谈MySQL SQL优化的底层原理
干净的坏蛋
mysqlsql数据库
深入理解MySQL的SQL优化底层原理,需要从查询的执行流程出发,结合优化器原理、执行计划生成机制、索引原理和存储引擎行为全面剖析。以下是完整的底层视角分析:✅一、MySQLSQL查询的底层执行流程客户端->SQL解析器->查询优化器->执行器->存储引擎(如InnoDB)1.SQL解析(Parser)词法分析+语法分析→生成抽象语法树(AST)比如:识别出SELECT、FROM、WHERE、字段
- MySQL MVCC解密:多版本并发控制的魔法世界
码农技术栈
MySQLmysql数据库开发语言javajvm后端性能优化
当多个用户同时读写数据库时,MySQL如何避免数据混乱?本文将揭开MVCC的神秘面纱,带你探索这个让数据库高并发运行的魔法引擎!一、为什么需要MVCC?并发控制的困境想象图书馆借阅场景:传统方式:一本书只能一个人看(锁机制)MVCC方式:复印多份,每人看不同版本(多版本控制)传统锁机制的痛点:事务A读数据加锁事务B写数据等待锁释放长时间等待系统卡顿二、MVCC是什么?时间旅行的艺术MVCC核心概念
- IoC容器深度解析:架构、原理与实现
liulilittle
MarkdownExtensionC#架构网络c#IoCDI依赖倒置依赖注入
IoC容器深度解析:架构、原理与实现引用:.NETIoC容器原理与实现等巫山的雲彩都消散撒下的碧色如何看淡一、引言:从服务定位器到IoC的演进类签名修改集中式管理依赖反转+动态注入强耦合直接依赖全量代码重构服务定位器模式圈复杂度指数级增长IoC容器方案低耦合+高扩展性历史痛点在早期软件开发中(如2000年代JavaEE体系),开发者面临两大核心问题:强耦合依赖链:上层模块直接实例化下层对象(new
- PostgreSQL 中的 pg_trgm 扩展详解
Yashar Qian
数据库(SQL)随笔postgresql数据库
PostgreSQL中的pg_trgm扩展详解pg_trgm是PostgreSQL提供的一个核心扩展,用于实现基于三元组(trigram)的文本相似度计算和高效搜索。它特别适合优化模糊匹配、部分匹配和相似度查询。核心功能三元组(trigram)概念:将字符串拆解为连续的3个字符组例如:“hello”→["h","he",“hel”,“ell”,“llo”,"lo"]主要用途:优化LIKE'%pat
- 【MySQL基础】MySQL事务详解:原理、特性与实战应用
GG Bond.ฺ
MySQL学习mysql数据库
MySQL学习:https://blog.csdn.net/2301_80220607/category_12971838.html?spm=1001.2014.3001.5482前言:事务是数据库管理系统的核心概念之一,它确保了数据库操作的可靠性和一致性。本文将深入探讨MySQL事务的各个方面,包括基本概念、ACID特性、隔离级别、锁机制以及实战应用。目录一、事务的基本概念1.1什么是事务?1.
- CentOS7环境卸载MySQL5.7
Hadoop_Liang
mysql数据库mysql
备份重要数据切记,卸载之前先备份mysql重要的数据。备份一个数据库例如:备份名为mydatabase的数据库到backup.sql的文件中mysqldump-uroot-ppassword123mydatabase>backup.sql备份所有数据库mysqldump-uroot-ppassword123--all-databases>all_databases_backup.sql注意:-p后
- centos7安装 mysql5.7(安装包)
heiPony
linuxmysqlmariadbcentosmysql
一.卸载centos7自带数据库查看系统自带的Mariadbrpm-qa|grepmariadbmariadb-libs-5.5.44-2.el7.centos.x86_64卸载rpm-e--nodepsmariadb-libs-5.5.44-2.el7.centos.x86_64删除etc目录下的my.cnfrm/etc/my.cnf二.检查mysql是否存在(有就卸载,删除相关文件)rpm-q
- MySQL Explain 详解:从入门到精通,让你的 SQL 飞起来
引言:为什么Explain是SQL优化的“照妖镜”?在Java开发中,我们常常会遇到数据库性能瓶颈的问题。一条看似简单的SQL语句,在数据量增长到一定规模后,可能会从毫秒级响应变成秒级甚至分钟级响应,直接拖慢整个应用的性能。此时,你是否曾困惑于:为什么这条SQL突然变慢了?索引明明建了,为什么没生效?到底是哪里出了问题?答案就藏在MySQL的EXPLAIN命令里。EXPLAIN就像一面“照妖镜”,
- Linux/Centos7离线安装并配置MySQL 5.7
有事开摆无事百杜同学
LInux/CentOS7linuxmysql运维
Linux/Centos7离线安装并配置MySQL5.7超详细教程一、环境准备1.下载MySQL5.7离线包2.使用rpm工具卸载MariaDB(避免冲突)3.创建系统级别的MySQL专用用户二、安装与配置1.解压并重命名MySQL目录2.创建数据目录和配置文件3.设置目录权限4.初始化MySQL5.配置启动脚本6.配置环境变量三、启动与验证1.启动MySQL服务2.获取初始密码3.登录并修改密码
- ztree设置禁用节点
3213213333332132
JavaScriptztreejsonsetDisabledNodeAjax
ztree设置禁用节点的时候注意,当使用ajax后台请求数据,必须要设置为同步获取数据,否者会获取不到节点对象,导致设置禁用没有效果。
$(function(){
showTree();
setDisabledNode();
});
- JVM patch by Taobao
bookjovi
javaHotSpot
在网上无意中看到淘宝提交的hotspot patch,共四个,有意思,记录一下。
7050685:jsdbproc64.sh has a typo in the package name
7058036:FieldsAllocationStyle=2 does not work in 32-bit VM
7060619:C1 should respect inline and
- 将session存储到数据库中
dcj3sjt126com
sqlPHPsession
CREATE TABLE sessions (
id CHAR(32) NOT NULL,
data TEXT,
last_accessed TIMESTAMP NOT NULL,
PRIMARY KEY (id)
);
<?php
/**
* Created by PhpStorm.
* User: michaeldu
* Date
- Vector
171815164
vector
public Vector<CartProduct> delCart(Vector<CartProduct> cart, String id) {
for (int i = 0; i < cart.size(); i++) {
if (cart.get(i).getId().equals(id)) {
cart.remove(i);
- 各连接池配置参数比较
g21121
连接池
排版真心费劲,大家凑合看下吧,见谅~
Druid
DBCP
C3P0
Proxool
数据库用户名称 Username Username User
数据库密码 Password Password Password
驱动名
- [简单]mybatis insert语句添加动态字段
53873039oycg
mybatis
mysql数据库,id自增,配置如下:
<insert id="saveTestTb" useGeneratedKeys="true" keyProperty="id"
parameterType=&
- struts2拦截器配置
云端月影
struts2拦截器
struts2拦截器interceptor的三种配置方法
方法1. 普通配置法
<struts>
<package name="struts2" extends="struts-default">
&
- IE中页面不居中,火狐谷歌等正常
aijuans
IE中页面不居中
问题是首页在火狐、谷歌、所有IE中正常显示,列表页的页面在火狐谷歌中正常,在IE6、7、8中都不中,觉得可能那个地方设置的让IE系列都不认识,仔细查看后发现,列表页中没写HTML模板部分没有添加DTD定义,就是<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3
- String,int,Integer,char 几个类型常见转换
antonyup_2006
htmlsql.net
如何将字串 String 转换成整数 int?
int i = Integer.valueOf(my_str).intValue();
int i=Integer.parseInt(str);
如何将字串 String 转换成Integer ?
Integer integer=Integer.valueOf(str);
如何将整数 int 转换成字串 String ?
1.
- PL/SQL的游标类型
百合不是茶
显示游标(静态游标)隐式游标游标的更新和删除%rowtyperef游标(动态游标)
游标是oracle中的一个结果集,用于存放查询的结果;
PL/SQL中游标的声明;
1,声明游标
2,打开游标(默认是关闭的);
3,提取数据
4,关闭游标
注意的要点:游标必须声明在declare中,使用open打开游标,fetch取游标中的数据,close关闭游标
隐式游标:主要是对DML数据的操作隐
- JUnit4中@AfterClass @BeforeClass @after @before的区别对比
bijian1013
JUnit4单元测试
一.基础知识
JUnit4使用Java5中的注解(annotation),以下是JUnit4常用的几个annotation: @Before:初始化方法 对于每一个测试方法都要执行一次(注意与BeforeClass区别,后者是对于所有方法执行一次)@After:释放资源 对于每一个测试方法都要执行一次(注意与AfterClass区别,后者是对于所有方法执行一次
- 精通Oracle10编程SQL(12)开发包
bijian1013
oracle数据库plsql
/*
*开发包
*包用于逻辑组合相关的PL/SQL类型(例如TABLE类型和RECORD类型)、PL/SQL项(例如游标和游标变量)和PL/SQL子程序(例如过程和函数)
*/
--包用于逻辑组合相关的PL/SQL类型、项和子程序,它由包规范和包体两部分组成
--建立包规范:包规范实际是包与应用程序之间的接口,它用于定义包的公用组件,包括常量、变量、游标、过程和函数等
--在包规
- 【EhCache二】ehcache.xml配置详解
bit1129
ehcache.xml
在ehcache官网上找了多次,终于找到ehcache.xml配置元素和属性的含义说明文档了,这个文档包含在ehcache.xml的注释中!
ehcache.xml : http://ehcache.org/ehcache.xml
ehcache.xsd : http://ehcache.org/ehcache.xsd
ehcache配置文件的根元素是ehcahe
ehcac
- java.lang.ClassNotFoundException: org.springframework.web.context.ContextLoaderL
白糖_
javaeclipsespringtomcatWeb
今天学习spring+cxf的时候遇到一个问题:在web.xml中配置了spring的上下文监听器:
<listener>
<listener-class>org.springframework.web.context.ContextLoaderListener</listener-class>
</listener>
随后启动
- angular.element
boyitech
AngularJSAngularJS APIangular.element
angular.element
描述: 包裹着一部分DOM element或者是HTML字符串,把它作为一个jQuery元素来处理。(类似于jQuery的选择器啦) 如果jQuery被引入了,则angular.element就可以看作是jQuery选择器,选择的对象可以使用jQuery的函数;如果jQuery不可用,angular.e
- java-给定两个已排序序列,找出共同的元素。
bylijinnan
java
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
public class CommonItemInTwoSortedArray {
/**
* 题目:给定两个已排序序列,找出共同的元素。
* 1.定义两个指针分别指向序列的开始。
* 如果指向的两个元素
- sftp 异常,有遇到的吗?求解
Chen.H
javajcraftauthjschjschexception
com.jcraft.jsch.JSchException: Auth cancel
at com.jcraft.jsch.Session.connect(Session.java:460)
at com.jcraft.jsch.Session.connect(Session.java:154)
at cn.vivame.util.ftp.SftpServerAccess.connec
- [生物智能与人工智能]神经元中的电化学结构代表什么?
comsci
人工智能
我这里做一个大胆的猜想,生物神经网络中的神经元中包含着一些化学和类似电路的结构,这些结构通常用来扮演类似我们在拓扑分析系统中的节点嵌入方程一样,使得我们的神经网络产生智能判断的能力,而这些嵌入到节点中的方程同时也扮演着"经验"的角色....
我们可以尝试一下...在某些神经
- 通过LAC和CID获取经纬度信息
dai_lm
laccid
方法1:
用浏览器打开http://www.minigps.net/cellsearch.html,然后输入lac和cid信息(mcc和mnc可以填0),如果数据正确就可以获得相应的经纬度
方法2:
发送HTTP请求到http://www.open-electronics.org/celltrack/cell.php?hex=0&lac=<lac>&cid=&
- JAVA的困难分析
datamachine
java
前段时间转了一篇SQL的文章(http://datamachine.iteye.com/blog/1971896),文章不复杂,但思想深刻,就顺便思考了一下java的不足,当砖头丢出来,希望引点和田玉。
-----------------------------------------------------------------------------------------
- 小学5年级英语单词背诵第二课
dcj3sjt126com
englishword
money 钱
paper 纸
speak 讲,说
tell 告诉
remember 记得,想起
knock 敲,击,打
question 问题
number 数字,号码
learn 学会,学习
street 街道
carry 搬运,携带
send 发送,邮寄,发射
must 必须
light 灯,光线,轻的
front
- linux下面没有tree命令
dcj3sjt126com
linux
centos p安装
yum -y install tree
mac os安装
brew install tree
首先来看tree的用法
tree 中文解释:tree
功能说明:以树状图列出目录的内容。
语 法:tree [-aACdDfFgilnNpqstux][-I <范本样式>][-P <范本样式
- Map迭代方式,Map迭代,Map循环
蕃薯耀
Map循环Map迭代Map迭代方式
Map迭代方式,Map迭代,Map循环
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
蕃薯耀 2015年
- Spring Cache注解+Redis
hanqunfeng
spring
Spring3.1 Cache注解
依赖jar包:
<!-- redis -->
<dependency>
<groupId>org.springframework.data</groupId>
<artifactId>spring-data-redis</artifactId>
- Guava中针对集合的 filter和过滤功能
jackyrong
filter
在guava库中,自带了过滤器(filter)的功能,可以用来对collection 进行过滤,先看例子:
@Test
public void whenFilterWithIterables_thenFiltered() {
List<String> names = Lists.newArrayList("John"
- 学习编程那点事
lampcy
编程androidPHPhtml5
一年前的夏天,我还在纠结要不要改行,要不要去学php?能学到真本事吗?改行能成功吗?太多的问题,我终于不顾一切,下定决心,辞去了工作,来到传说中的帝都。老师给的乘车方式还算有效,很顺利的就到了学校,赶巧了,正好学校搬到了新校区。先安顿了下来,过了个轻松的周末,第一次到帝都,逛逛吧!
接下来的周一,是我噩梦的开始,学习内容对我这个零基础的人来说,除了勉强完成老师布置的作业外,我已经没有时间和精力去
- 架构师之流处理---------bytebuffer的mark,limit和flip
nannan408
ByteBuffer
1.前言。
如题,limit其实就是可以读取的字节长度的意思,flip是清空的意思,mark是标记的意思 。
2.例子.
例子代码:
String str = "helloWorld";
ByteBuffer buff = ByteBuffer.wrap(str.getBytes());
Sy
- org.apache.el.parser.ParseException: Encountered " ":" ": "" at line 1, column 1
Everyday都不同
$转义el表达式
最近在做Highcharts的过程中,在写js时,出现了以下异常:
严重: Servlet.service() for servlet jsp threw exception
org.apache.el.parser.ParseException: Encountered " ":" ": "" at line 1,
- 用Java实现发送邮件到163
tntxia
java实现
/*
在java版经常看到有人问如何用javamail发送邮件?如何接收邮件?如何访问多个文件夹等。问题零散,而历史的回复早已经淹没在问题的海洋之中。
本人之前所做过一个java项目,其中包含有WebMail功能,当初为用java实现而对javamail摸索了一段时间,总算有点收获。看到论坛中的经常有此方面的问题,因此把我的一些经验帖出来,希望对大家有些帮助。
此篇仅介绍用
- 探索实体类存在的真正意义
java小叶檀
POJO
一. 实体类简述
实体类其实就是俗称的POJO,这种类一般不实现特殊框架下的接口,在程序中仅作为数据容器用来持久化存储数据用的
POJO(Plain Old Java Objects)简单的Java对象
它的一般格式就是
public class A{
private String id;
public Str