ansible配置管理windows主机
1、ansible服务器端的配置
服务端一定是LINUX的服务器,实验采用了CENTOS7,先安装python的一些模块
pip install pywinrm paramiko PyYAML Jinja2 httplib2 six
pywinrm下载地址
https://files.pythonhosted.org/packages/73/ad/ec5951e3b489c44f41cabc015bb64dea901f8ec805c825fe4b8d86d27fb7/pywinrm-0.2.1-py2.py3-none-any.whl
https://files.pythonhosted.org/packages/74/a7/1093100bcff3857035798f55b34640befb3179da38001e181995f4fdc1da/pywinrm-0.2.1.tar.gz
修改/etc/ansible/hosts,添加以下内容
[windows]
192.168.156.81
[windows:vars]
ansible_connection=winrm
ansible_user=administrator
ansible_ssh_pass=密码
ansible_ssh_port=5985
ansible_winrm_server_cert_validation=ignore
ansible_winrm_transport=ntlm
2、配置WINDOWS
实验当中采用的操作系统是WINDOWS2008,需要先升级.NET4.5和POWERSHELL4.0
https://download.microsoft.com/download/B/A/4/BA4A7E71-2906-4B2D-A0E1-80CF16844F5F/dotNetFx45_Full_setup.exe
https://download.microsoft.com/download/3/D/6/3D61D262-8549-4769-A660-230B67E15B25/Windows6.1-KB2819745-x64-MultiPkg.msu
安装好以后重启
打开powershell,执行命令
PS C:\Users\Administrator> set-executionpolicy remotesigned
执行策略更改
执行策略可帮助你防止执行不信任的脚本。更改执行策略可能会产生安全风险,如 http://go.microsoft.com/fwl
中的 about_Execution_Policies 帮助主题所述。是否要更改执行策略?
[Y] 是(Y) [N] 否(N) [S] 挂起(S) [?] 帮助 (默认值为“Y”): y
PS C:\Users\Administrator> winrm quickconfig
已在此计算机上运行 WinRM 服务。
WinRM 没有设置成为了管理此计算机而允许对其进行远程访问。
必须进行以下更改:
在 HTTP://* 上创建 WinRM 侦听程序接受 WS-Man 对此机器上任意 IP 的请求。
启用 WinRM 防火墙异常。
配置 LocalAccountTokenFilterPolicy 以远程向本地用户授予管理权限。
执行这些更改吗[y/n]? y
WinRM 已经进行了更新,以用于远程管理。
在 HTTP://* 上创建 WinRM 侦听程序接受 WS-Man 对此机器上任意 IP 的请求。
WinRM 防火墙异常已启用。
已配置 LocalAccountTokenFilterPolicy 以远程向本地用户授予管理权限。
PS C:\Users\Administrator> winrm enumerate winrm/config/listener
Listener
Address = *
Transport = HTTP
Port = 5985
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint
ListeningOn = 127.0.0.1, 192.168.156.81, ::1, fe80::5efe:192.168.156.81%12, fe80::29ef:9851:dfe6
PS C:\Users\Administrator> winrm set winrm/config/service/auth '@{Basic="true"}'
Auth
Basic = true
Kerberos = true
Negotiate = true
Certificate = false
CredSSP = false
CbtHardeningLevel = Relaxed
PS C:\Users\Administrator> winrm set winrm/config/service '@{AllowUnencrypted="true"}'
Service
RootSDDL = O:NSG:BAD:P(A;;GA;;;BA)(A;;GR;;;IU)S:P(AU;FA;GA;;;WD)(AU;SA;GXGW;;;WD)
MaxConcurrentOperations = 4294967295
MaxConcurrentOperationsPerUser = 1500
EnumerationTimeoutms = 240000
MaxConnections = 300
MaxPacketRetrievalTimeSeconds = 120
AllowUnencrypted = true
Auth
Basic = false
Kerberos = true
Negotiate = true
Certificate = false
CredSSP = false
CbtHardeningLevel = Relaxed
DefaultPorts
HTTP = 5985
HTTPS = 5986
IPv4Filter = *
IPv6Filter = *
EnableCompatibilityHttpListener = false
EnableCompatibilityHttpsListener = false
CertificateThumbprint
AllowRemoteAccess = true
注意后面的命令是配置允许非加密方式,不改的话可能会出现如下错误:
[root@v72 ~]# ansible windows -m win_command -a 'ipconfig'
192.168.156.81 | UNREACHABLE! => {
"changed": false,
"msg": "ntlm: (u'http', u'Bad HTTP response returned from server. Code 500')",
"unreachable": true
}
3、在服务端执行命令验证
[root@v72 ~]# ansible windows -m win_command -a 'ipconfig'
192.168.156.81 | SUCCESS | rc=0 >>
Windows IP Configuration
Ethernet adapter ????????:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::29ef:9851:dfe6:200a%11
IPv4 Address. . . . . . . . . . . : 192.168.156.81
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.156.2
Tunnel adapter isatap.{E0F743D2-D506-4F10-8584-0BA0295C3DD9}:
Connection-specific DNS Suffix . :
[root@v72 ~]# ansible windows -m win_ping
192.168.156.81 | SUCCESS => {
"changed": false,
"ping": "pong"
}
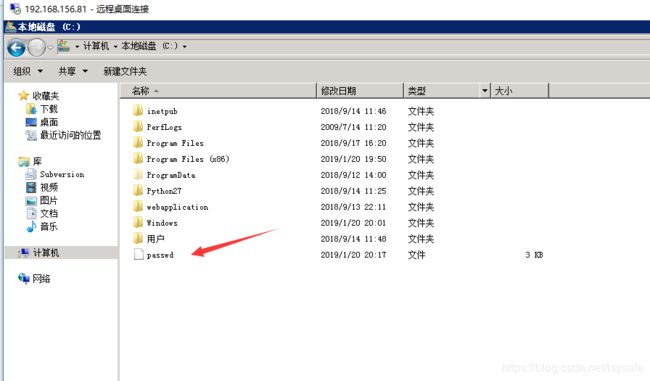
拷贝文件
[root@v72 ~]# ansible windows -m win_copy -a "src=/etc/passwd dest=c:\passwd"
192.168.156.81 | SUCCESS => {
"changed": true,
"checksum": "fe51e4f7b0b6efa8ed5f1debe2b29e9434429e5d",
"dest": "c:\\passwd",
"operation": "file_copy",
"original_basename": "passwd",
"size": 2595,
"src": "/etc/passwd"
}
文件已拷贝,配置成功了