转载自https://blog.51cto.com/3381847248/1977073
前面我已经介绍了haproxy结合keepalive做简单的双主高可用,如果不清楚的话,可以去我的上一
篇博客http://3381847248.blog.51cto.com/13408601/1977014看看,根据haproxy的性能和特点,我们可以对haproxy进行优化调整,体现出haproxy的价值。
假设一家公司有多台后端web服务器(或者多台图片服务器),每一台web服务器都有自己唯一的域
名,在还没有做haproxy之前,我们需要把域名的对应关系给写到hosts文件里或者需要在DNS服务器上进
行配置,这样的话,就会给我们后端的服务器带来一定的风险;通过haproxy,我们可以把域名都解析到
haproxy服务器上,然后通过haproxy服务器进行转发,当我需要访问某个域名的时候,haproxy服务器就
会跳到那个域名所对应的后端服务器上,而我后端服务器只开放所需要的端口,这样就大大减少了对后
端服务器的风险了。
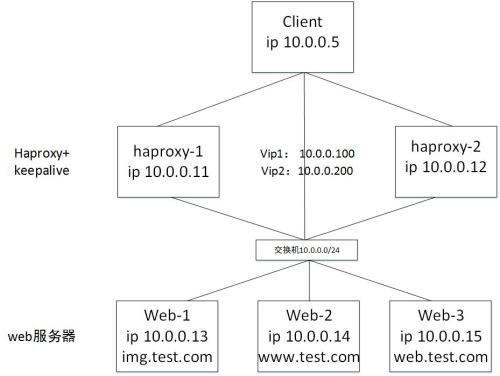
实验环境
拓扑图:
| 主机 | ip | 域名 | 角色 | |
| haproxy-1 | 10.0.0.11 | haproxy+keepalive |
vip1:10.0.0.100 vip2:10.0.0.200 |
|
| haproxy-2 | 10.0.0.12 | haproxy+keepalive | ||
| web-1 | 10.0.0.13 | img.test.com | web服务器 | |
| web-2 | 10.0.0.14 | www.test.com | web服务器 | |
| web-3 | 10.0.0.15 | web.test.com | web服务器 | |
| client | 10.0.0.5 | client |
开始配置
1、配置好各主机ip地址,关闭selinux和防火墙,修改hosts文件
##修改hosts文件
[root@haproxy-1 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.100 img.test.com www.test.com web.test.com
10.0.0.200 img.test.com www.test.com web.test.com
[root@haproxy-2 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.100 img.test.com www.test.com web.test.com
10.0.0.200 img.test.com www.test.com web.test.com
[root@web1 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.13 img.test.com
[root@web2 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.14 www.test.com
[root@web-3 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.15 web.test.com
[root@client ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.100 img.test.com www.test.com web.test.com
10.0.0.200 img.test.com www.test.com web.test.com
2、配置web服务器
##安装Apache
yum install -y httpd
##具体配置略
##查看web网页
[root@web1 ~]# curl 10.0.0.13
10.0.0.13 img.test.com
[root@web2 ~]# curl 10.0.0.14
10.0.0.14 www.test.com
[root@web-3 ~]# curl 10.0.0.15
10.0.0.15:80 web.test.com
[root@web-3 ~]# curl 10.0.0.15:8080
10.0.0.15:80803、配置haproxy
3.1、安装haproxy
yum install -y haproxy##性能调优相关参数:
maxconn : //设定单haproxy进程的最大并发连接数;
maxconnrate : //设定单haproxy进程每秒接受的连接数;
maxsslconn : //设定单haproxy进程的ssl连接最大并发连接数;
maxsslrate : //单haproxy进程的ssl连接的创建速率上限;
spread-checks <0..50, in percent>
tune.rcvbuf.client //接收客户端请求的缓冲大小
tune.rcvbuf.server //接收服务端响应的缓冲大小
tune.sndbuf.client //向客户端发送响应的缓冲大小
tune.sndbuf.server //向服务端发送请求的缓冲大小
tune.ssl.cachesize //ssl会话的缓存大小
tune.ssl.lifetime //ssl会话缓存的有效时长
##配置参数:
bind:
作用:设定监听的地址和端口;
语法:bind []: [, ...]
使用位置:frontend,listen
mode { tcp|http|health }
作用:定义haproxy的工作模型:
tcp:基于layer4实现代理,可代理大多数基于tcp的应用层协议,例如ssh,mysql,pgsql等;
http:客户端的http请求会被深度解析;
health:工作为健康状态检查响应模式,当请求到达时仅回应“OK”即断开连接;
开启统计页面,相关信息:
maxconn :最大并发连接数,默认为2000,使用位置:frontend、default、listen
stats enable:作用:启用内建的统计页,在缺少其它必要的参数时,会使用默认配置;
默认配置:
- stats uri : /haproxy?stats
- stats realm : "HAProxy Statistics"
- stats auth : no authentication
- stats scope : no restriction
说明:
stats uri :自定义stats页面的uri;
stats realm :启用统计信息并设置身份认证域。
stats auth ::定义认证使用的账号和密码;
stats hide-version:隐藏版本信息
stats refresh :自动刷新相关页面的时间间隔;
stats admin { if | unless } :条件满足时启用stats内建的管理功能接口;不建议启用,有安全隐患
##ACL匹配的如下所示:
1、ACL derivatives :
path : exact string match(字符窜精确匹配)
path_beg : prefix match(前缀匹配)
path_dir : subdir match(子目录匹配)
path_dom : domain match(域匹配)
path_end : suffix match(后缀匹配)
path_len : length match(长度匹配)
path_reg : regex match(正则匹配)
path_sub : substring match(子串匹配)
例如:
acl test_path path -i /test.txt ##匹配具体路径
acl test_path_beg path_beg -i /test. #匹配前缀包含
acl test_path_end path_end -i .html ##匹配.html结尾
2、可以基于字符串做检测:
req.hdr([[,]]) : string
对请求报文中的内容做检查
This extracts the last occurrence of header in an HTTP request.
ACL derivatives :
hdr([[,]]) : exact string match
hdr_beg([[,]]) : prefix match
hdr_dir([[,]]) : subdir match
hdr_dom([[,]]) : domain match
hdr_end([[,]]) : suffix match
hdr_len([[,]]) : length match
hdr_reg([[,]]) : regex match
hdr_sub([[,]]) : substring match
res.hdr([[,]]) : string
对响应报文中的内容做检测
ACL derivatives :
shdr([[,]]) : exact string match
shdr_beg([[,]]) : prefix match
shdr_dir([[,]]) : subdir match
shdr_dom([[,]]) : domain match
shdr_end([[,]]) : suffix match
shdr_len([[,]]) : length match
shdr_reg([[,]]) : regex match
shdr_sub([[,]]) : substring match
3.2、配置haproxy日志文件
##添加日志(haproxy.cfg):
[root@haproxy-1 haproxy]# vim haproxy.cfg
log 127.0.0.1 local2
##修改syslog.conf:
[root@haproxy-1 haproxy]# vim /etc/rsyslog.conf
# Provides UDP syslog reception
$ModLoad imudp
$UDPServerRun 514
# Provides TCP syslog reception
$ModLoad imtcp
$InputTCPServerRun 514
local2.* /var/log/haproxy.log
##重启两个服务即可看到日志文件:
[root@haproxy-1 ~]# systemctl restart rsyslog
[root@haproxy-1 ~]# systemctl restart haproxy
[root@haproxy-1 ~]# cd /var/log/
[root@haproxy-1 log]# ls haproxy.log
haproxy.log
##把日志文件配置同步到主机haproxy-2上
[root@haproxy-1 ~]# scp /etc/haproxy/haproxy.cfg 10.0.0.12:/etc/haproxy/haproxy.cfg
[root@haproxy-1 ~]# scp /etc/rsyslog.conf 10.0.0.12:/etc/rsyslog.conf
[root@haproxy-2 ~]# systemctl restart rsyslog
[root@haproxy-2 ~]# systemctl restart haproxy
3.3、配置haproxy(两台机的配置是一样的)
[root@haproxy-1 ~]# cat /etc/haproxy/haproxy.cfg
#---------------------------------------------------------------------
# Example configuration for a possible web application. See the
# full configuration options online.
#
# http://haproxy.1wt.eu/download/1.4/doc/configuration.txt
#
#---------------------------------------------------------------------
#---------------------------------------------------------------------
# Global settings
#---------------------------------------------------------------------
global
# to have these messages end up in /var/log/haproxy.log you will
# need to:
#
# 1) configure syslog to accept network log events. This is done
# by adding the '-r' option to the SYSLOGD_OPTIONS in
# /etc/sysconfig/syslog
#
# 2) configure local2 events to go to the /var/log/haproxy.log
# file. A line like the following can be added to
# /etc/sysconfig/syslog
#
# local2.* /var/log/haproxy.log
#
log 127.0.0.1 local2
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
maxconn 4000
user haproxy
group haproxy
daemon
# turn on stats unix socket
stats socket /var/lib/haproxy/stats
#---------------------------------------------------------------------
# common defaults that all the 'listen' and 'backend' sections will
# use if not designated in their block
#---------------------------------------------------------------------
defaults
mode http
log global
option httplog
option dontlognull
option http-server-close
option forwardfor except 127.0.0.0/8
option redispatch
retries 3
timeout http-request 10s
timeout queue 1m
timeout connect 10s
timeout client 1m
timeout server 1m
timeout http-keep-alive 10s
timeout check 10s
maxconn 3000
#---------------------------------------------------------------------
# main frontend which proxys to the backends
#---------------------------------------------------------------------
frontend main *:80
stats enable ##添加监控页面
stats uri /test?stats ##自定义URL
stats realm Stats\ Page\ Area ##去掉空格转译
stats auth admin:admin ##配置账号密码
stats refresh 5s ##没5s刷新一次
stats hide-version ##隐藏版本信息
stats admin if TRUE
maxconn 10000 ##定义最大并发为10000
acl url_static path_beg -i /static /p_w_picpaths /javascript /stylesheets
##匹配目录是如下的地址
acl url_static path_end -i .jpg .gif .png .css .js
##匹配结尾是.jpg.gif的地址
acl usr_www hdr(host) -i www.test.com
acl usr_img hdr(host) -i img.test.com
acl usr_web hdr_end(host) -i .test.com ##所有访问test.com的二级域名的,都转发到hdr_end这个位置
use_backend img if usr_img
use_backend www if usr_www
use_backend web if usr_web
use_backend static if url_static
default_backend web
backend static
balance roundrobin
server static 127.0.0.1:4331 check
backend img
balance roundrobin
server web-1 10.0.0.13:80 check inter 2000 rise 3 fall 3 weight 3
#check inter 2000 是检测心跳频率(check 默认 );
#rise 3 表示 3次正确认为服务器可用;
#fall 3 表示 3次失败认为服务器不可用;
#weight 表示权重。
backend www
balance roundrobin
server web-2 10.0.0.14:80 check inter 2000 rise 3 fall 3 weight 3
backend web
balance roundrobin
server web-3 10.0.0.15:80 check inter 2000 rise 3 fall 3 weight 3
server web-3 10.0.0.15:8080 check inter 2000 rise 3 fall 3 weight 3##启动haproxy
[root@haproxy-1 haproxy]# systemctl restart haproxy
[root@haproxy-2 ~]# systemctl restart haproxy
3.4、配置keepalive
##安装keepalive
[root@haproxy-1 ~]# yum install -y keepalived
[root@haproxy-2 ~]# yum install -y keepalived##haproxy-1的keepalive配置文件
[root@haproxy-1 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
vrrp_script check_haproxy {
script "/etc/keepalived/check_haproxy.sh"
interval 2
weight 2
}
global_defs {
notification_email {
[email protected]
}
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
state MASTER
interface ens33
virtual_router_id 50
nopreempt
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
10.0.0.100
}
track_script {
check_haproxy
}
}
vrrp_instance VI_2 {
state BACKUP
interface ens33
virtual_router_id 51
nopreempt
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
10.0.0.200
}
track_script {
check_haproxy
}
}##haproxy-2的keepalive配置文件
[root@haproxy-2 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
vrrp_script check_haproxy {
script "/etc/keepalived/check_haproxy.sh"
interval 2
weight 2
}
global_defs {
notification_email {
[email protected]
}
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
state BACKUP
interface ens33
virtual_router_id 50
nopreempt
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
10.0.0.100
}
track_script {
check_haproxy
}
}
vrrp_instance VI_2 {
state MASTER
interface ens33
virtual_router_id 51
nopreempt
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
10.0.0.200
}
track_script {
check_haproxy
}
}##haproxy检测脚本
[root@haproxy-1 ~]# cat /etc/keepalived/check_haproxy.sh
#!/bin/bash
h=`ps -C haproxy --no-header |wc -l`
if [ $h -eq 0 ];then
systemctl stop keepalived
fi
[root@haproxy-1 ~]# chmod a+x /etc/keepalived/check_haproxy.sh
[root@haproxy-2 ~]# cat /etc/keepalived/check_haproxy.sh
#!/bin/bash
h=`ps -C haproxy --no-header |wc -l`
if [ $h -eq 0 ];then
systemctl stop keepalived
fi
[root@haproxy-2 ~]# chmod a+x /etc/keepalived/check_haproxy.sh##启动keepalive
[root@haproxy-1 ~]# systemctl restart keepalived
[root@haproxy-1 ~]# systemctl status keepalived
● keepalived.service - LVS and VRRP High Availability Monitor
Loaded: loaded (/usr/lib/systemd/system/keepalived.service; disabled; vendor preset: disabled)
Active: active (running) since Sat 2017-10-28 16:00:23 CST; 12s ago
Process: 3806 ExecStart=/usr/sbin/keepalived $KEEPALIVED_OPTIONS (code=exited, status=0/SUCCESS)
Main PID: 3807 (keepalived)
CGroup: /system.slice/keepalived.service
├─3807 /usr/sbin/keepalived -D
├─3808 /usr/sbin/keepalived -D
└─3809 /usr/sbin/keepalived -D
Oct 28 16:00:28 haproxy-1 Keepalived_vrrp[3809]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:29 haproxy-1 Keepalived_vrrp[3809]: VRRP_Instance(VI_2) Received advert with higher priori... 102
Oct 28 16:00:29 haproxy-1 Keepalived_vrrp[3809]: VRRP_Instance(VI_2) Entering BACKUP STATE
Oct 28 16:00:29 haproxy-1 Keepalived_vrrp[3809]: VRRP_Instance(VI_2) removing protocol VIPs.
Oct 28 16:00:30 haproxy-1 Keepalived_vrrp[3809]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 16:00:30 haproxy-1 Keepalived_vrrp[3809]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs o....100
Oct 28 16:00:30 haproxy-1 Keepalived_vrrp[3809]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 16:00:30 haproxy-1 Keepalived_vrrp[3809]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 16:00:30 haproxy-1 Keepalived_vrrp[3809]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 16:00:30 haproxy-1 Keepalived_vrrp[3809]: Sending gratuitous ARP on ens33 for 10.0.0.100
Hint: Some lines were ellipsized, use -l to show in full.
[root@haproxy-1 ~]# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:1d:7a:63 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.11/24 brd 10.0.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet 10.0.0.100/32 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::8ec5:50ac:d71:20d7/64 scope link
valid_lft forever preferred_lft forever
inet6 fe80::f87c:449f:eb4a:ba03/64 scope link tentative dadfailed
valid_lft forever preferred_lft forever [root@haproxy-2 ~]# systemctl restart keepalived
[root@haproxy-2 ~]# systemctl status keepalived
● keepalived.service - LVS and VRRP High Availability Monitor
Loaded: loaded (/usr/lib/systemd/system/keepalived.service; disabled; vendor preset: disabled)
Active: active (running) since Sat 2017-10-28 16:00:28 CST; 19s ago
Process: 27168 ExecStart=/usr/sbin/keepalived $KEEPALIVED_OPTIONS (code=exited, status=0/SUCCESS)
Main PID: 27169 (keepalived)
CGroup: /system.slice/keepalived.service
├─27169 /usr/sbin/keepalived -D
├─27170 /usr/sbin/keepalived -D
└─27171 /usr/sbin/keepalived -D
Oct 28 16:00:29 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:29 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:29 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:29 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:34 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:34 haproxy-2 Keepalived_vrrp[27171]: VRRP_Instance(VI_2) Sending/queueing gratuitous ARPs o...200
Oct 28 16:00:34 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:34 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:34 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:00:34 haproxy-2 Keepalived_vrrp[27171]: Sending gratuitous ARP on ens33 for 10.0.0.200
Hint: Some lines were ellipsized, use -l to show in full.
[root@haproxy-2 ~]# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:76:bf:48 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.12/24 brd 10.0.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet 10.0.0.200/32 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::f87c:449f:eb4a:ba03/64 scope link
valid_lft forever preferred_lft forever
##在client上访问
[root@client ~]# curl img.test.com
10.0.0.13 img.test.com
[root@client ~]# curl www.test.com
10.0.0.14 www.test.com
[root@client ~]# curl web.test.com
10.0.0.15:80 web.test.com
[root@client ~]# curl web.test.com
10.0.0.15:8080
[root@client ~]# curl web.test.com
10.0.0.15:80 web.test.com
[root@client ~]# curl web.test.com
10.0.0.15:8080
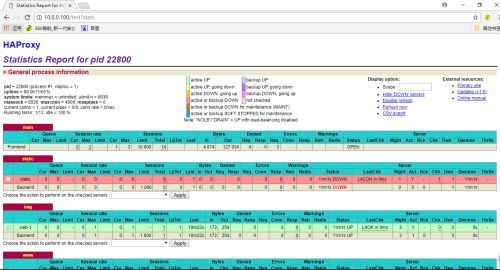
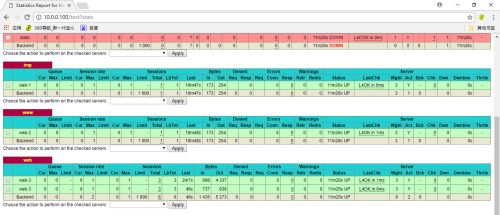
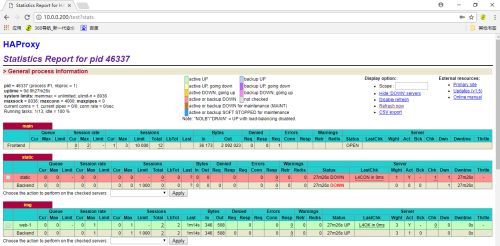
##查看监控界面,打开浏览器,输入10.0.0.100/test?stats,输入之前设置的账号密码(admin:admin),如图1,之后就可以看到我们配置的haproxy的内容了,如图2和图3。
图1
图2
图3
验证
当haproxy-1上的haproxy服务宕掉了之后,vip1就会从haproxy-1上飘到haproxy-2上,也就是说haproxy-2上有两个vip,而且还能正常访问web服务
##在haproxy-1上查看keepalive和vip的状态,可以看到vip已经不在了
[root@haproxy-1 ~]# systemctl stop haproxy
[root@haproxy-1 ~]# systemctl status keepalived
● keepalived.service - LVS and VRRP High Availability Monitor
Loaded: loaded (/usr/lib/systemd/system/keepalived.service; disabled; vendor preset: disabled)
Active: inactive (dead)
Oct 28 16:50:36 haproxy-1.test.com Keepalived_vrrp[11327]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:50:36 haproxy-1.test.com Keepalived_vrrp[11327]: Sending gratuitous ARP on ens33 for 10.0.0.200
Oct 28 16:50:36 haproxy-1.test.com Keepalived_vrrp[11327]: VRRP_Instance(VI_2) Received advert with high...102
Oct 28 16:50:36 haproxy-1.test.com Keepalived_vrrp[11327]: VRRP_Instance(VI_2) Entering BACKUP STATE
Oct 28 16:50:36 haproxy-1.test.com Keepalived_vrrp[11327]: VRRP_Instance(VI_2) removing protocol VIPs.
Oct 28 18:28:11 haproxy-1 Keepalived[11325]: Stopping
Oct 28 18:28:11 haproxy-1 systemd[1]: Stopping LVS and VRRP High Availability Monitor...
Oct 28 18:28:11 haproxy-1 Keepalived_vrrp[11327]: VRRP_Instance(VI_1) sent 0 priority
Oct 28 18:28:11 haproxy-1 Keepalived_vrrp[11327]: VRRP_Instance(VI_1) removing protocol VIPs.
Oct 28 18:28:12 haproxy-1 systemd[1]: Stopped LVS and VRRP High Availability Monitor.
Hint: Some lines were ellipsized, use -l to show in full.
[root@haproxy-1 ~]# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:1d:7a:63 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.11/24 brd 10.0.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::8ec5:50ac:d71:20d7/64 scope link
valid_lft forever preferred_lft forever
inet6 fe80::f87c:449f:eb4a:ba03/64 scope link tentative dadfailed
valid_lft forever preferred_lft forever
##在haproxy-2上查看keepalive和vip的状态,可以看到vip1已经从haproxy-1飘到haproxy-2上了
[root@haproxy-2 ~]# systemctl status keepalived
● keepalived.service - LVS and VRRP High Availability Monitor
Loaded: loaded (/usr/lib/systemd/system/keepalived.service; disabled; vendor preset: disabled)
Active: active (running) since Sat 2017-10-28 16:50:35 CST; 1h 41min ago
Process: 34787 ExecStart=/usr/sbin/keepalived $KEEPALIVED_OPTIONS (code=exited, status=0/SUCCESS)
Main PID: 34788 (keepalived)
CGroup: /system.slice/keepalived.service
├─34788 /usr/sbin/keepalived -D
├─34789 /usr/sbin/keepalived -D
└─34790 /usr/sbin/keepalived -D
Oct 28 18:28:12 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:12 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:12 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:12 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:17 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:17 haproxy-2 Keepalived_vrrp[34790]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs o...100
Oct 28 18:28:17 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:17 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:17 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Oct 28 18:28:17 haproxy-2 Keepalived_vrrp[34790]: Sending gratuitous ARP on ens33 for 10.0.0.100
Hint: Some lines were ellipsized, use -l to show in full.
[root@haproxy-2 ~]# ip addr
1: lo: mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:76:bf:48 brd ff:ff:ff:ff:ff:ff
inet 10.0.0.12/24 brd 10.0.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet 10.0.0.200/32 scope global ens33
valid_lft forever preferred_lft forever
inet 10.0.0.100/32 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::f87c:449f:eb4a:ba03/64 scope link
valid_lft forever preferred_lft forever
##访问web服务
[root@client ~]# curl img.test.com
10.0.0.13 img.test.com
[root@client ~]# curl img.test.com
10.0.0.13 img.test.com
[root@client ~]# curl www.test.com
10.0.0.14 www.test.com
[root@client ~]# curl www.test.com
10.0.0.14 www.test.com
[root@client ~]# curl web.test.com
10.0.0.15:80 web.test.com
[root@client ~]# curl web.test.com
10.0.0.15:8080
[root@client ~]# curl web.test.com
10.0.0.15:80 web.test.com
[root@client ~]# curl web.test.com
10.0.0.15:8080
##访问监控页面
这次的优化haproxy的实验就已经到此结束了。如果有写错的地方,欢迎各位大神指出来,我会去改正的。如果有写的不好的地方,请多多见谅!!!