前言:
上回博客说道域的概念DNS服务器的解析过程,这篇博客我们就来说一下关于配置一个服务器为DNS服务器多需要做到的工作。
FQDN-->IP:正向解析库区域
IP-->FQDN:反向解析库区域
区域数据库文件:主要由资源记录组成
资源记录:Resource Record,简称rr;
记录类型:A,AAAA,PTR,SOA,NS,CNAME,MX
资源记录的定义格式:
语法: name [TTL] IN RR_TYPE value
SOA:Start Of Authority,起始授权记录,一个区域解析库有且只能有一个SOA记录,并且必须放在资源记录的第一条。
name:当前区域的名字,例如“mageedu.com.",或者"2.3.4.in-addr-arpa.".
value:有多部分组成
(1)当前区域的区域名称(也可以使用主DNS服务器名称);
(2)当前区域管理员的邮箱地址;但地址中不能使用@符号,一般使用点号代替;
(3)(主从服务协调属性的定义以及否定答案的TTL)
magedu.com. IN SOA ns1.magedu.com. dnssdmin.magedu.com. ( 2016010801 1H 10M 3D 1D )
NS:Name Service,域名服务记录,一个区域解析库可以有多个NS记录,其中一个为主。
name:当前区域的区域名称
value:当前区域的某DNS服务器名字,例如:ns.magedu.com.;
(一个区域可以哟多个NS记录);
magedu.com. IN NS ns1.magedu.com.
A:Address,地址记录;FQDN-->IPv4(并不是一一对应关系)
name:某FQDN,例如:www.magedu.com.
value:某IPv4地址
ns1 IN A 172.16.249.130 mx1 IN A 172.16.249.10 mx2 IN A 172.16.249.11 www IN A 172.16.249.130
AAAA:Address,地址记录;FQDN-->IPv6(并不是一一对应关系)
CNAME:Canonical Name,别名记录
name:FQDN格式的别名;
value:FQDN格式的正式名字;
web IN CNAME www
PTR:Pointer,IP-->FQDN
name:IP地址,有特定格式,IP反过来写,而且加特定后缀,例如1.2.3.4的记录应该写为4.3.2.1.in-addr.arpa.;
value:FQDN
$TTL 3600 $ORIGIN 249.16.172.in-addr.arpa. @ IN SOA ns1.stu61.com. tz.stu61.com. ( 2016010801 1H 10M 3D 12H ) IN NS ns1.stu61.com. 130 IN PTR ns1.stu61.com.
MX:Mail exchanger,邮件交换器;优先级:0-99,数字越小优先级越高
name:当前区域的区域名称
value:当前区域某文件交换器的主机名
(注,MX记录可以有多个,但每一个MX记录要有一个优先级)
magedu.com. IN MX 10 mx1 magedu.com. IN MX 20 mx2
注意:
(1) TTL可以从全局继承;
(2) @表示当前区域的名称;
(3) 相邻的两条记录其name相同时,后面的可省略;
(4) 对于正向区域来说,各MX,NS等类型的记录的value为FQDN,此FQDN应该有一个A记录
配置一个DNS服务器所需要的环境
BIND的安装配置:
BIND: Berkeley Internet Name Domain, ISC.org
dns: 协议
bind: dns协议的一种实现
named:bind程序的运行的进程名
程序包:
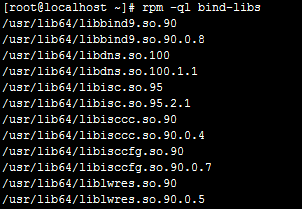
bind-libs:被bind和bind-utils包中的程序共同用到的库文件;
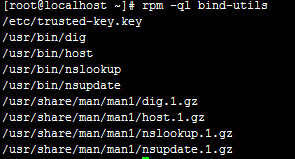
bind-utils:bind客户端程序集,例如dig, host, nslookup等;
bind:提供的dns server程序、以及几个常用的测试程序;
bind-chroot:选装,让named运行于jail模式下;
bind
主配置文件:/etc/named.conf
主配置文件格式:
全局配置段:
options{....}
日志配置段:
logging{...}
区域配置段:
zone{...}:那些由本机负责解析的区域,或转发的区域。
[root@localhost named]# cat /etc/named.conf
options {
listen-on port 53 { 172.16.249.130; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
//allow-query { localhost; };
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
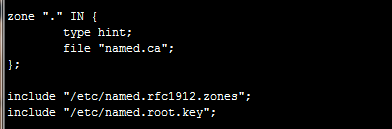
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
要想作为缓存服务器,必须配置监听地址
缓存名称服务器的配置:
监听能与外部主机通信的地址;
listen-on port 53;
listen-on port 53 { 172.16.100.67; };
学习时,建议关闭dnssec
dnssec-enable no;
dnssec-validation no;
dnssec-lookaside no;
关闭仅允许本地查询:
//allow-query { localhost; };
注:每个配置语句必须以分号结尾;
[root@localhost ~]# vim /etc/named.conf
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
options {
listen-on port 53 { 172.16.249.130; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
//allow-query { localhost; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable no;
dnssec-validation no;
dnssec-lookaside no;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
修改后要检查配置文件是否有语法错误:
named-checkconf [/etc/named.conf]
除了主配置文件还有其他配置文件;
/etc/named.iscdlv.key
/etc/named.rfc1912.zones(在CentOS7上也被当作主配置文件)
/etc/named.root.key
解析库文件:(工作目录)
/var/named/
该目录下存放了各区域的解析库文件,一般名字为:ZONE_NAME.zone
注(1)一台DNS服务器可以同时为多个区域提供解析
(2)必须要有根区域解析库文件;named.ca
(3)还应该有两个区域解析库文件:localhost和127.0.0.1的正反向解析库;
正向:named.localhost
反向:named.loopback
[root@localhost ~]# cat /var/named/named.localhost $TTL 1D @ IN SOA @ rname.invalid. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS @ A 127.0.0.1 AAAA ::1 [root@localhost ~]# cat /var/named/named.loopback $TTL 1D @ IN SOA @ rname.invalid. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS @ A 127.0.0.1 AAAA ::1 PTR localhost.
bind程序安装完成后,默认即可做缓存名称服务器使用;如果没有专门负责解析的区域,可直接启动服务
centos6:service named start
centos7:systemctl start named.service
启动bind服务:
[root@localhost ~]# systemctl status named.service named.service - Berkeley Internet Name Domain (DNS) Loaded: loaded (/usr/lib/systemd/system/named.service; disabled) Active: active (running) since Sat 2016-01-09 19:31:24 CST; 18s ago Process: 6825 ExecStart=/usr/sbin/named -u named $OPTIONS (code=exited, status=0/SUCCESS) Process: 6822 ExecStartPre=/bin/bash -c if [ ! "$DISABLE_ZONE_CHECKING" == "yes" ]; then /usr/sbin/named-checkconf -z /etc/named.conf; else echo "Checking of zone files is disabled"; fi (code=exited, status=0/SUCCESS) Main PID: 6827 (named) CGroup: /system.slice/named.service ?..6827 /usr/sbin/named -u named Jan 09 19:31:23 localhost.localdomain named[6827]: zone 0.in-addr.arpa/IN: loaded serial 0 Jan 09 19:31:24 localhost.localdomain named[6827]: zone 1.0.0.127.in-addr.arpa/IN: loaded serial 0 Jan 09 19:31:24 localhost.localdomain named[6827]: zone 1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0....l 0 Jan 09 19:31:24 localhost.localdomain named[6827]: zone localhost/IN: loaded serial 0 Jan 09 19:31:24 localhost.localdomain named[6827]: zone localhost.localdomain/IN: loaded serial 0 Jan 09 19:31:24 localhost.localdomain named[6827]: all zones loaded Jan 09 19:31:24 localhost.localdomain named[6827]: running Jan 09 19:31:24 localhost.localdomain systemd[1]: Started Berkeley Internet Name Domain (DNS). Jan 09 19:31:24 localhost.localdomain named[6827]: error (network unreachable) resolving './DNSKEY/IN': ...#53 Jan 09 19:31:24 localhost.localdomain named[6827]: error (network unreachable) resolving './NS/IN': 2001...#53 Hint: Some lines were ellipsized, use -l to show in full.
查看网络连接状态tcp和udp的53号端口被named监听,说明DNS可以正常使用
[root@localhost ~]# netstat -tunlp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 172.16.249.130:53 0.0.0.0:* LISTEN 6827/named udp6 0 0 ::1:53 :::* 6827/named
配置DNS配置文件地址为自己的ip地址,这样就把自己当作DNS服务器
[root@localhost ~]# vim /etc/resolv.conf # Generated by NetworkManager search magelinux.com nameserver 172.16.249.130
测试工具:
dig, host, nslookup等
dig命令:
dig [-t RR_TYPE] name [@SERVER] [query options]
用于测试dns系统,因此其不会查询hosts文件;
查询选项:
+[no]trace:跟踪解析过程;
+[no]recurse:进行递归解析;
注意:反向解析测试
dig -x IP
模拟完全区域传送:
dig -t axfr DOMAIN [@server]
[root@localhost ~]# dig -t A www.baidu.com ; <<>> DiG 9.9.4-RedHat-9.9.4-29.el7_2.1 <<>> -t A www.baidu.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7319 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 5, ADDITIONAL: 6 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.baidu.com. IN A ;; ANSWER SECTION: www.baidu.com. 103 IN CNAME www.a.shifen.com. www.a.shifen.com. 300 IN A 61.135.169.121 www.a.shifen.com. 300 IN A 61.135.169.125 ;; AUTHORITY SECTION: a.shifen.com. 103 IN NS ns1.a.shifen.com. a.shifen.com. 103 IN NS ns5.a.shifen.com. a.shifen.com. 103 IN NS ns2.a.shifen.com. a.shifen.com. 103 IN NS ns4.a.shifen.com. a.shifen.com. 103 IN NS ns3.a.shifen.com. ;; ADDITIONAL SECTION: ns3.a.shifen.com. 103 IN A 61.135.162.215 ns4.a.shifen.com. 103 IN A 115.239.210.176 ns5.a.shifen.com. 103 IN A 119.75.222.17 ns1.a.shifen.com. 103 IN A 61.135.165.224 ns2.a.shifen.com. 103 IN A 180.149.133.241 ;; Query time: 138 msec ;; SERVER: 172.16.249.130#53(172.16.249.130) ;; WHEN: Sat Jan 09 20:32:50 CST 2016 ;; MSG SIZE rcvd: 271
host命令:
host [-t RR_TYPE] name SERVER_IP
[root@localhost ~]# host -t A www.baidu.com www.baidu.com is an alias for www.a.shifen.com. www.a.shifen.com has address 61.135.169.121 www.a.shifen.com has address 61.135.169.125 [root@localhost ~]# host -t NS baidu.com baidu.com name server ns2.baidu.com. baidu.com name server ns7.baidu.com. baidu.com name server ns4.baidu.com. baidu.com name server dns.baidu.com. baidu.com name server ns3.baidu.com.
nslookup命令:
nslookup [-options] [name] [server]
交互式模式:
nslookup>
server IP:以指定的IP为DNS服务器进行查询;(不指明IP表示以本机默认的DNS服 务器进行查询)
set q=RR_TYPE:要查询的资源记录类型;
name:要查询的名称;
[root@localhost ~]# nslookup > > set q=A > www.baidu.com Server: 172.16.249.130 Address: 172.16.249.130#53 Non-authoritative answer: www.baidu.com canonical name = www.a.shifen.com. Name: www.a.shifen.com Address: 61.135.169.125 Name: www.a.shifen.com Address: 61.135.169.121
rndc命令:named服务控制命令
rndc status 查看dns信息
rndc flush(清空服务器缓存)
rndc reload 重载配置文件
接下来我们就可以为这台DNS服务器配置区域解析库
配置正向区域解析库:
(以stu61.com域为例)
第一步:定义区域
在主配置文件中或主配置文件辅助配置文件中实现,但在CentOS7中主配置文件只配置了根域但我们可以在/etc/named.rfc1912.zones中配置
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "stu61.com" IN {
type master;
file "stu61.com.zone";
};
第二步:建立正向区域解析库数据文件(主要记录为A或AAAA记录)
[root@localhost named]# vim stu61.com.zone $TTL 3600 @ IN SOA ns1.stu61.com. tz.stu61.com. ( 2016010801 1H 10M 3D 1D ) @ IN NS ns1.stu61.com. IN MX 10 mx1 IN MX 20 mx2 ns1 IN A 172.16.249.130 mx1 IN A 172.16.249.10 mx2 IN A 172.16.249.11 www IN A 172.16.249.130 web IN CNAME www
第三步:让服务器重载配置文件和区域数据文件
①检查主配置文件是否有语法错误:
[root@localhost named]# named-checkconf
②检查区域文件是否有语法格式错误:
# named-checkzone zonename filename
[root@localhost named]# named-checkzone stu61.com /var/named/stu61.com.zone zone stu61.com/IN: loaded serial 2016010801 OK
③重载配置文件和区域文件
[root@localhost named]# rndc reload server reload successful
或者使用
[root@localhost named]# systemctl reload named.service
④使用本机地址测试解析结果,从而验证我们配置的正向解析文件是否能正常使用:
[root@localhost named]# dig -t www.stu61.com ;; Warning, ignoring invalid type www.stu61.com ; <<>> DiG 9.9.4-RedHat-9.9.4-29.el7_2.1 <<>> -t www.stu61.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10248 ;; flags: qr rd ra; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 25 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;. IN NS ;; ANSWER SECTION: . 511058 IN NS e.root-servers.net. . 511058 IN NS g.root-servers.net. . 511058 IN NS m.root-servers.net. . 511058 IN NS k.root-servers.net. . 511058 IN NS a.root-servers.net. . 511058 IN NS i.root-servers.net. . 511058 IN NS d.root-servers.net. . 511058 IN NS h.root-servers.net. . 511058 IN NS b.root-servers.net. . 511058 IN NS f.root-servers.net. . 511058 IN NS c.root-servers.net. . 511058 IN NS j.root-servers.net. . 511058 IN NS l.root-servers.net. ;; ADDITIONAL SECTION: a.root-servers.net. 601418 IN A 198.41.0.4 a.root-servers.net. 601418 IN AAAA 2001:503:ba3e::2:30 b.root-servers.net. 601418 IN A 192.228.79.201 b.root-servers.net. 601418 IN AAAA 2001:500:84::b c.root-servers.net. 601417 IN A 192.33.4.12 c.root-servers.net. 601417 IN AAAA 2001:500:2::c d.root-servers.net. 601414 IN A 199.7.91.13 d.root-servers.net. 601414 IN AAAA 2001:500:2d::d e.root-servers.net. 601416 IN A 192.203.230.10 f.root-servers.net. 601416 IN A 192.5.5.241 f.root-servers.net. 601416 IN AAAA 2001:500:2f::f g.root-servers.net. 601418 IN A 192.112.36.4 h.root-servers.net. 601415 IN A 198.97.190.53 h.root-servers.net. 601416 IN AAAA 2001:500:1::53 i.root-servers.net. 601414 IN A 192.36.148.17 i.root-servers.net. 601414 IN AAAA 2001:7fe::53 j.root-servers.net. 601417 IN A 192.58.128.30 j.root-servers.net. 601417 IN AAAA 2001:503:c27::2:30 k.root-servers.net. 601415 IN A 193.0.14.129 k.root-servers.net. 601415 IN AAAA 2001:7fd::1 l.root-servers.net. 601418 IN A 199.7.83.42 l.root-servers.net. 601418 IN AAAA 2001:500:3::42 m.root-servers.net. 601416 IN A 202.12.27.33 m.root-servers.net. 601416 IN AAAA 2001:dc3::35 ;; Query time: 2 msec ;; SERVER: 172.16.249.130#53(172.16.249.130) ;; WHEN: Sat Jan 09 21:33:46 CST 2016 ;; MSG SIZE rcvd: 755
第四步:修改库文件的属组和权限
[root@localhost named]# chown :named stu61.com.zone [root@localhost named]# chmod o= stu61.com.zone
配置反向区域解析库:
第一步:定义区域
在主配置文件中或主配置文件辅助配置文件中实现
[root@localhost named]# vim /etc/named.rfc1912.zones
zone "249.16.172.in-addr.arpa" IN {
type master;
file "172.16.249.zone";
};
第二步:定义反向区域解析库文件
[root@localhost named]# vim 172.16.249.zone $TTL 3600 $ORIGIN 249.16.172.in-addr.arpa. @ IN SOA ns1.stu61.com. tz.stu61.com. ( 2016010801 1H 10M 3D 12H ) IN NS ns1.stu61.com. 130 IN PTR ns1.stu61.com. 10 IN PTR mx1.stu61.com. 11 IN PTR mx2.stu61.com. 130 IN PTR www.stu61.com.
第三步:让服务器重载配置文件和区域数据文件
①检查主配置文件是否有语法错误:
[root@localhost named]# named-checkconf
②检查区域文件是否有语法格式错误:
[root@localhost named]# named-checkzone 249.16.172.in-addr.arpa 172.16.249.zone zone 249.16.172.in-addr.arpa/IN: loaded serial 2016010801 OK
③重载配置文件和区域文件
[root@localhost named]# rndc reload server reload successful
④使用本机地址测试解析结果,从而验证我们配置的反向解析文件是否能正常使用:
[root@localhost named]# dig -x 172.16.249.130 ; <<>> DiG 9.9.4-RedHat-9.9.4-29.el7_2.1 <<>> -x 172.16.249.130 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6749 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;130.249.16.172.in-addr.arpa. IN PTR ;; ANSWER SECTION: 130.249.16.172.in-addr.arpa. 3600 IN PTR www.stu61.com. 130.249.16.172.in-addr.arpa. 3600 IN PTR ns1.stu61.com. ;; AUTHORITY SECTION: 249.16.172.in-addr.arpa. 3600 IN NS ns1.stu61.com. ;; ADDITIONAL SECTION: ns1.stu61.com. 3600 IN A 172.16.249.130 ;; Query time: 1 msec ;; SERVER: 172.16.249.130#53(172.16.249.130) ;; WHEN: Sat Jan 09 22:04:58 CST 2016 ;; MSG SIZE rcvd: 131
第四步:修改库文件的属组和权限
[root@localhost named]# chmod o= 172.16.249.zone [root@localhost named]# chown :named 172.16.249.zone
到此为止我们就为这台服务器创建了正向解析区域和反向解析区域,此服务器就能当作完整的DNS服务器使用了