华为IPSEC-×××-典型配置举例1-采用手工方式建立IPsec 安全隧道
1, 某公司(总部在北京)有两个子公司分别在上海和广州,要求通过×××实现公司之间相互通信!
2, 实验环境如下:要求192.168.1.0/24网段的员工分别与192.168.2.0/24,192.168.3.0/24的员工通信!(中间的为公网)
3, 本实验要求采用手工方式建立IPsec 安全隧道
firewall zone trust
add interface Ethernet 0/2
firewall zone untrust
add interface Ethernet 0/1
interface Ethernet0/2
ip address 192.168.1.1 255.255.255.0
interface Ethernet0/1
ip address 1.1.1.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 1.1.1.2 preference 60
firewall zone trust
add interface Ethernet 0/2
firewall zone untrust
add interface Ethernet 0/1
ip address 192.168.2.1 255.255.255.0
interface Ethernet0/1
ip address 2.1.1.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 2.1.1.2 preference 60
firewall zone trust
add interface Ethernet 0/2
firewall zone untrust
add interface Ethernet 0/1
interface Ethernet0/2
ip address 192.168.3.1 255.255.255.0
interface Ethernet0/1
ip address 3.1.1.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 3.1.1.2 preference 60
interface Vlan-interface3
interface Vlan-interface7
interface Vlan-interface10
interface Ethernet0/1
interface Ethernet0/3
interface Ethernet0/7
rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 20 deny ip source any destination any
rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 20 deny ip source any destination any
ipsec proposal zhu-1
encapsulation-mode tunnel
esp authentication-algorithm md5
esp encryption-algorithm des
display ipsec proposal
ipsec proposal zhu-2
encapsulation-mode tunnel
esp authentication-algorithm md5
esp encryption-algorithm des
display ipsec proposal
ipsec policy policy1 10 manual
tunnel local 1.1.1.1
tunnel remote 2.1.1.1
sa spi outbound esp 12345
sa spi inbound esp 54321
sa string-key outbound esp zzu
sa string-key inbound esp zzdx
ipsec policy policy1 20 manual
tunnel local 1.1.1.1
tunnel remote 3.1.1.1
sa spi outbound esp 123456
sa spi inbound esp 654321
sa string-key outbound esp abcbef
sa string-key inbound esp qazwsx
interface Ethernet0/1
ipsec policy policy1
display ipsec proposal
rule 10 permit ip source 192.168.2.0 0.0.0.255 dest 192.168.1.0 0.0.0.255
rule 20 deny ip source any dest any
ipsec policy policy2 10 manual
sa spi inbo esp 12345
sa spi outbo esp 54321
sa string inbo esp zzu
sa str outbo esp zzdx
display ipsec proposal
rule 10 permit ip source 192.168.3.0 0.0.0.255 dest 192.168.1.0 0.0.0.255
rule 20 deny ip source any dest any
ipsec policy policy3 20 manual
sa spi inbo esp 123456
sa spi outbo esp 654321
sa string inbo esp abcbef
sa str outbo esp qazwsx
ipsec poli policy3
display ipsec proposal
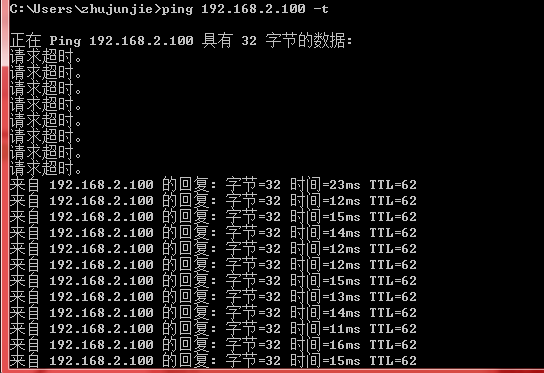
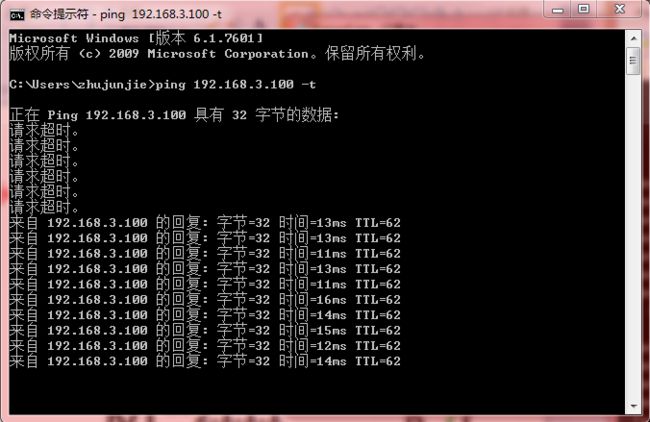
192.168.1.100客户端ping测试192.168.3.100,应用以后ipsec以后可以通信。
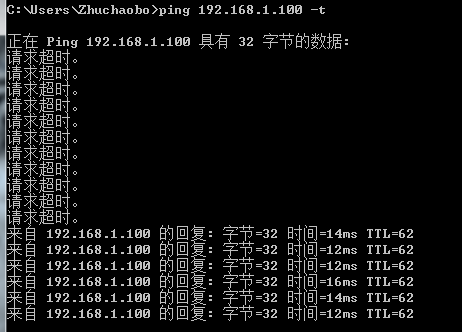
192.168.3.100客户端ping测试192.168.1.100,应用以后ipsec以后可以通信。
查看fw-1,fw-2.fw-3的ipsec信息和当前配置: