(一)实验简介
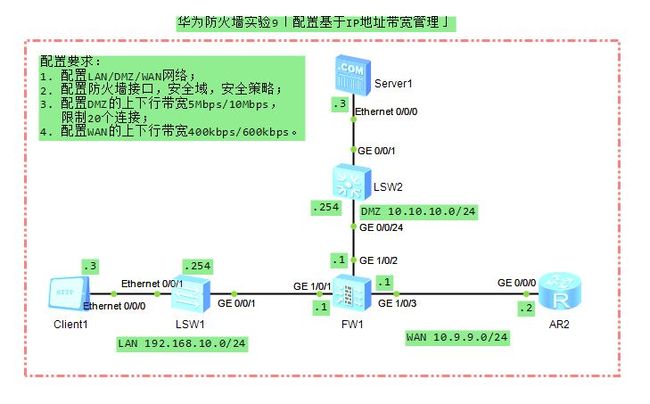
如拓朴图所示,为防止 FTP 服务器受攻击,在防火墙上限制从服务器受攻击,在防火墙上限制从 Trust区域和 Untrust区域 到 FTP 端口的连接数上限为 20 ,并且限制其上传 ,并且限制其上传 /下载带宽为: 5Mbps/10Mbps。限制trust域内每个 PC 到Internet的上传 /下载带宽为:400kbps/600kbps。
(二)实验目的
- 掌握网关对网关的组网;
- 掌握手工方式配置两个网络的IPSecVPN;
(三)实验条件
- 一台CPU支持VT技术,内存4GB以上的计算机;
- 安装eNSP模拟器B510版,导入USG6000V镜像;
- 终端工具:SecuretyCRT,Putty,Psftp,XShell等。
(四)网络拓朴图
打开ENSP软件,按如下拓朴图创建实验环境,设置地址:
- LAN地址:192.168.10.0/24;
- WAN地址:10.9.9.0/24;
- DMZ地址:10.10.10.0/24;
(五)配置思路
- 配置LAN/DMZ/WAN网络;
- 配置防火墙接口,安全域,安全策略;
- 配置IP带宽通道,配置带宽策略;
(六)配置步骤
(1)配置LAN网络
先设置Client1的IP地址
配置LAN交换机:
The device is running!
system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname LSW1
[LSW1]interface Vlanif 1
[LSW1-Vlanif1]ip address 192.168.10.254 24
[LSW1-Vlanif1]quit
[LSW1]
[LSW1]ospf 1
[LSW1-ospf-1]area 0
[LSW1-ospf-1-area-0.0.0.0]network 192.168.10.0 0.0.0.255
[LSW1-ospf-1-area-0.0.0.0]quit
[LSW1-ospf-1]quit
[LSW1]
[LSW1]quit
(2)配置DMZ网络
先设置Server1的IP地址
配置DMZ交换机:
The device is running!
system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname LSW2
[LSW2]interface Vlanif 1
[LSW2-Vlanif1]ip address 10.10.10.254 24
[LSW2-Vlanif1]quit
[LSW2]
[LSW2]ospf 1
[LSW2-ospf-1]area 0
[LSW2-ospf-1-area-0.0.0.0]network 10.10.10.0 0.0.0.255
[LSW2-ospf-1-area-0.0.0.0]quit
[LSW2-ospf-1]quit
[LSW2]
[LSW2]quit
(3)配置WAN网络
配置AR1路由器
The device is running!
system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR2
[AR2]interface GigabitEthernet 0/0/0
[AR2-GigabitEthernet0/0/0]
[AR2-GigabitEthernet0/0/0]ip address 10.9.9.2 24
[AR2-GigabitEthernet0/0/0]
[AR2-GigabitEthernet0/0/0]quit
[AR2]ospf 1
[AR2-ospf-1]
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]
[AR2-ospf-1-area-0.0.0.0]network 10.9.9.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]
[AR2-ospf-1-area-0.0.0.0]quit
[AR2-ospf-1]
[AR2-ospf-1]quit
[AR2]quit
(4)配置FW的网络及策略
The device is running!
An initial password is required for the first login via the console.
Set a password and keep it safe. Otherwise you will not be able to login via the
console.
Please configure the login password (8-16)
Enter Password:
Confirm Password:
Warning: The authentication mode was changed to password authentication and the
user level was changed to 15 on con0 at the first user login.
Warning: There is a risk on the user-interface which you login through. Please c
hange the configuration of the user-interface as soon as possible.
*************************************************************************
* Copyright (C) 2014-2015 Huawei Technologies Co., Ltd. *
* All rights reserved. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
system-view
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info en
Info: Information center is disabled.
[USG6000V1]sysname FW1
[FW1]
[FW1]int g 1/0/1
[FW1-GigabitEthernet1/0/1]ip addr 192.168.10.1 24
[FW1-GigabitEthernet1/0/1]service-manage ping permit
[FW1-GigabitEthernet1/0/1]service-manage http permit
[FW1-GigabitEthernet1/0/1]quit
[FW1]
[FW1]int g 1/0/2
[FW1-GigabitEthernet1/0/2]ip addr 10.10.10.1 24
[FW1-GigabitEthernet1/0/2]service-manage ping permit
[FW1-GigabitEthernet1/0/2]service-manage http permit
[FW1-GigabitEthernet1/0/2]quit
[FW1]
[FW1]int g 1/0/3
[FW1-GigabitEthernet1/0/3]ip addr 10.9.9.1 24
[FW1-GigabitEthernet1/0/3]service-manage ping permit
[FW1-GigabitEthernet1/0/3]service-manage http permit
[FW1-GigabitEthernet1/0/3]quit
[FW1]
[FW1]firewall zone trust
[FW1-zone-trust]add int g 1/0/1
[FW1-zone-trust]quit
[FW1]
[FW1]firewall zone dmz
[FW1-zone-dmz]add int g 1/0/2
[FW1-zone-dmz]quit
[FW1]
[FW1]firewall zone untrust
[FW1-zone-untrust]add int g 1/0/3
[FW1-zone-untrust]quit
[FW1]
[FW1]ospf 1
[FW1-ospf-1]area 0
[FW1-ospf-1-area-0.0.0.0]network 10.10.10.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]network 10.9.9.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]network 192.168.10.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]quit
[FW1-ospf-1]quit
[FW1]
[FW1]security-policy
[FW1-policy-security]rule name trust_dmz
[FW1-policy-security-rule-trust_dmz]source-zone trust local
[FW1-policy-security-rule-trust_dmz]destination-zone dmz local
[FW1-policy-security-rule-trust_dmz]action permit
[FW1-policy-security-rule-trust_dmz]quit
[FW1-policy-security]
[FW1-policy-security]rule name trust_untrust
[FW1-policy-security-rule-trust_untrust]source-zone trust local
[FW1-policy-security-rule-trust_untrust]destination-zone untrust local
[FW1-policy-security-rule-trust_untrust]action permit
[FW1-policy-security-rule-trust_untrust]quit
[FW1-policy-security]
[FW1-policy-security]security-policy
[FW1-policy-security]rule name untrust_dmz
[FW1-policy-security-rule-untrust_dmz]source-zone untrust local
[FW1-policy-security-rule-untrust_dmz]destination-zone dmz local
[FW1-policy-security-rule-untrust_dmz]action permit
[FW1-policy-security-rule-untrust_dmz]quit
[FW1-policy-security]quit
[FW1]
[FW1]traffic-policy //配置带宽通道及带宽策略
[FW1-policy-traffic]profile profile_traffic_1 //配置带宽通道1
[FW1-policy-traffic-profile-profile_traffic_1]bandwidth maximum-bandwidth whole
upstream 5000
[FW1-policy-traffic-profile-profile_traffic_1]bandwidth maximum-bandwidth whole
downstream 10000
[FW1-policy-traffic-profile-profile_traffic_1]bandwidth connection-limit whole b
oth 20
[FW1-policy-traffic-profile-profile_traffic_1]quit
[FW1-policy-traffic]
[FW1-policy-traffic]profile profile_traffic_2 //配置带宽通道2
[FW1-policy-traffic-profile-profile_traffic_2]bandwidth maximum-bandwidth whole
upstream 400
[FW1-policy-traffic-profile-profile_traffic_2]bandwidth maximum-bandwidth whole
downstream 600
[FW1-policy-traffic-profile-profile_traffic_2]quit
[FW1-policy-traffic]
[FW1-policy-traffic]rule name policy_traffic_1 //配置带宽策略1,引用带宽通道1
[FW1-policy-traffic-rule-policy_traffic_1]source-zone trust
[FW1-policy-traffic-rule-policy_traffic_1]source-zone untrust
[FW1-policy-traffic-rule-policy_traffic_1]destination-zone dmz
[FW1-policy-traffic-rule-policy_traffic_1]action qos profile profile_traffic_1
[FW1-policy-traffic-rule-policy_traffic_1]quit
[FW1-policy-traffic]
[FW1-policy-traffic]rule name policy_traffic_2 //配置带宽策略2,引用带宽通道2
[FW1-policy-traffic-rule-policy_traffic_2]source-zone trust
[FW1-policy-traffic-rule-policy_traffic_2]destination-zone untrust
[FW1-policy-traffic-rule-policy_traffic_2]action qos profile profile_traffic_2
[FW1-policy-traffic-rule-policy_traffic_2]quit
[FW1-policy-traffic]
[FW1-policy-traffic]quit
[FW1]
(5)测试
服务器启动FTP服务,并用FTP客户端登录,但因ENSP是模拟器,无法测试使用traffic-policy前后的速度变化:
(七)参考资料
华为模拟器eNSP软件,
华为模拟器eNSP社区,
HCNA-Security 华为认证网络安全工程师,
HCNP-Security 华为认证网络安全资深工程师,
HUAWEI USG6000V V500R001C10SPC100 典型配置案例,
HUAWEI USG6000V V500R001C10SPC100 管理员指南,
HUAWEI USG6000V V500R001C10SPC100 命令参考 ,
华为ICT相关的英文简称 。