snort 联动iptables 配置为IPS,NIDS
一、环境准备
Ubuntu16.10,snort2.9.9,iptables1.6.0,daq-2.0.6
二、snort安装
首先关掉网卡的“Large Receive Offload” (lro) and “Generic Receive Offload” (gro).
看snort手册:
Some network cards have features named “Large Receive Offload” (lro) and “Generic Receive Offload” (gro). With these features enabled, the network card performs packet reassembly before they’re processed by the kernel. By default, Snort will truncate packets larger than the default snaplen of 1518 bytes. In addition, LRO and GRO may cause issues with Stream5 target-based reassembly. We recommend that you turn off LRO and GRO.
执行以下命令:
sudo vi /etc/network/interfaces
打开interfaces后加入下面两句:
post-up ethtool -K enp0s3 gro off
post-up ethtool -K enp0s3 lro off
根据自己的网卡名进行更改,关于网卡名的变更详见
Important note for people running Ubuntu 16: Begining with Ubuntu 15.10, network interfaces no longer follow the ethX standard (eth0, eth1, …). Instead, interfaces names are assigned as Predictable Network Interface Names. This means you need to check the names of your interfaces using ifconfig -a. In my case, what was originally eth0 is now ens160. If you are running Ubuntu 15.10, anywhere in this guide you see eth0, you will need to replace with your new interface name.
安装依赖包
sudo apt-get install -y build-essential libpcap-dev libpcre3-dev libdumbnet-dev bison flex zlib1g-dev liblzma-dev openssl libssl-dev
相关包的解释
build-essential: provides the build tools (GCC and the like) to
compile software.
bison, flex: parsers required by DAQ (DAQ is installed later below).
libpcap-dev: Library for network traffic capture required by Snort.
libpcre3-dev: Library of functions to support regular expressions required by Snort.
libdumbnet-dev: the libdnet library provides a simplified, portable interface to several low-level networking routines. Many
guides for installing Snort install this library from source, although
that is not necessary.
zlib1g-dev: A compression library required by Snort.
liblzma-dev: Provides decompression of swf files (adobe flash)
openssl and libssl-dev: Provides SHA and MD5 file signatures
创建一个目录作为snort安装的主目录
mkdir ~/snort_src
cd ~/snort_src
安装支持HTTP/2相关的包,在ubuntu16和14下安装方式是不同的
# Ubuntu 16 only:
sudo apt-get install -y libnghttp2-dev
ubuntu14需要从源码编译
# Ubuntu 14 only (not Ubuntu 16)
sudo apt-get install -y autoconf libtool pkg-config
cd ~/snort_src
wget https://github.com/nghttp2/nghttp2/releases/download/v1.17.0/nghttp2-1.17.0.tar.gz
tar -xzvf nghttp2-1.17.0.tar.gz
cd nghttp2-1.17.0
autoreconf -i --force
automake
autoconf
./configure --enable-lib-only
make
sudo make install
安装daq,因为我们要用到NFQ模式所以先要安装它的依赖包,需要到官网www.netfilter.org下载libnfnetlink.tar.bz2、libmnl.tar.bz2、libnetfilter_queue.tar.bz2源码,注意libnetfilter_queue.tar.bz2需要在其它两个包安装好后安装,完成后安装daq
cd ~/snort_src
wget https://snort.org/downloads/snort/daq-2.0.6.tar.gz
tar -xvzf daq-2.0.6.tar.gz
cd daq-2.0.6
./configure
make
sudo make install
如安装成功configure时可以看到NFQ后面为yes,如果没有就没成功
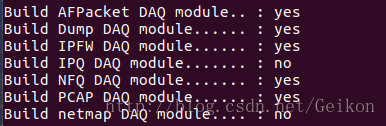
安装snort
cd ~/snort_src
wget https://snort.org/downloads/snort/snort-2.9.9.0.tar.gz
tar -xvzf snort-2.9.9.0.tar.gz
cd snort-2.9.9.0
./configure --enable-sourcefire
make
sudo make install
enable-sourcefire参数作用:Snort can provide statistics on rule and preprocessor performance. Each require only a simple config option to snort.conf and Snort will print statistics on the worst (or all) performers on exit. When a file name is provided in profile_rules or profile_preprocs, the statistics will be saved in these files. If append is not specified, a new file will be created each time Snort is run. The filenames will have timestamps appended to them. These files will be found in the logging directory.To use this feature, you must build snort with the -enable-perfprofiling option to the configure script.
之后需要更新shared libraries,做个链接,然后查看版本验证安装是否成功
sudo ldconfig
sudo ln -s /usr/local/bin/snort /usr/sbin/snort
snort -V
三、配置snort为NIDS
这里主要是创建一些文件夹并修改一些基本的配置选项,配置文件会放在/etc/snort, 规则放在 /etc/snort/rules, /usr/local/lib/snort_dynamicrules, 产生的日志文件默认存在 /var/log/snort,
# Create the Snort directories:
sudo mkdir /etc/snort
sudo mkdir /etc/snort/rules
sudo mkdir /etc/snort/rules/iplists
sudo mkdir /etc/snort/preproc_rules
sudo mkdir /usr/local/lib/snort_dynamicrules
sudo mkdir /etc/snort/so_rules
# Create some files that stores rules and ip lists
sudo touch /etc/snort/rules/iplists/black_list.rules
sudo touch /etc/snort/rules/iplists/white_list.rules
sudo touch /etc/snort/rules/local.rules
sudo touch /etc/snort/sid-msg.map
# Create our logging directories:
sudo mkdir /var/log/snort
sudo mkdir /var/log/snort/archived_logs
# Adjust permissions:
sudo chmod -R 5775 /etc/snort
sudo chmod -R 5775 /var/log/snort
sudo chmod -R 5775 /var/log/snort/archived_logs
sudo chmod -R 5775 /etc/snort/so_rules
sudo chmod -R 5775 /usr/local/lib/snort_dynamicrules
将配置文件移动到/etc/snort
cd ~/snort_src/snort-2.9.9.0/etc/
sudo cp *.conf* /etc/snort
sudo cp *.map /etc/snort
sudo cp *.dtd /etc/snort
cd ~/snort_src/snort-2.9.9.0/src/dynamic-preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/
sudo cp * /usr/local/lib/snort_dynamicpreprocessor/
完成可以执行以下命令,查看/etc/snort的文件结构
tree /etc/snort
接下来修改配置文件,执行下面的命令注释掉snort.conf里面自动加载规则的 547 到651行,因为我们没有下载这些规则,如果不注释掉snort初始化时会出错
sudo sed -i 's/include \$RULE\_PATH/#include \$RULE\_PATH/' /etc/snort/snort.conf
在45行设置本机的ip,下面的10.0.0.0/24 替换为你自己的ip
sudo vi /etc/snort/snort.conf
ipvar HOME_NET 10.0.0.0/24 # (line 45) make this match your internal (friendly) network
告诉snort之前创建文件的位置,按下面的修改snort.conf
var RULE_PATH /etc/snort/rules # line 104
var SO_RULE_PATH /etc/snort/so_rules # line 105
var PREPROC_RULE_PATH /etc/snort/preproc_rules # line 106
var WHITE_LIST_PATH /etc/snort/rules/iplists # line 113
var BLACK_LIST_PATH /etc/snort/rules/iplists # line 114
之后可以添加一个自己的规则文件,将下面的语句加在snort.conf后
include $RULE_PATH/local.rules
保存退出,执行下面的命令测试配置文件,wlan0改你自己实际使用的网卡
sudo snort -T -c /etc/snort/snort.conf -i wlan0
四、测试IPS
以拦截百度为例,先在snort中添加规则,打开本地的规则文件
sudo vim /etc/snort/rules/local.rules
添加拦截百度的规则,保存退出
drop tcp any any -> any any (msg:"find baidu tcp";content:"baidu.com";nocase;sid:26288;)
drop udp any any -> any any (msg:"find baidu dns ";content:"baidu.com";nocase;sid:26299;)
执行以下命令启动snort inline模式
sudo snort -Q --daq nfq --daq-var device=wlan0 --daq-var queue=1 -c /etc/snort/snort.conf -A console
在另一个命令终端中,执行以下命令为iptables添加规则
iptables -I INPUT -j NFQUEUE --queue-num 1 --queue-bypass
由于百度的拦截规则写的不是很严格所以不是所有跟百度相关的都能拦截,但是经测试可以拦截百度贴吧,百度文档等使其无法访问。
