centos平台搭建snort入侵检测系统
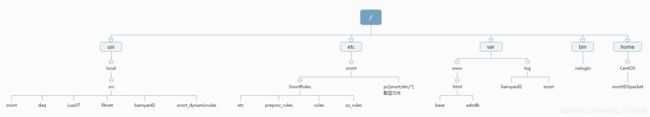
文件结构
一、配置更新源
yum install -y wget
wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-6.repo
yum clean all #清除缓存
yum makecache #生成缓存
yum -y update #更新系统二、安装基本环境和依赖包
yum install -y epel-release gcc gcc-c++ flex bison zlib* libxml2 libpcap* pcre* tcpdump git libtool curl man make flex bison-devel libcap-devel openssl-devel三、编译安装snort
cd /usr/local/src/
#编译安装libdnet
tar -zxvf /home/centos/snortIDSpacket/libdnet-1.11.tar.gz
cd libdnet-1.11/
./configure
make && make install
#编译安装LuaJIT
tar -zxvf /home/centos/snortIDSpacket/LuaJIT-2.0.5.tar.gz
cd LuaJIT-2.0.5/
make && make install
#编译安装daq
tar -zxvf /home/centos/snortIDSpacket/daq-2.0.6.tar.gz
cd daq-2.0.6/
./configure
make && make install
#编译安装snort
tar -zxvf /home/centos/snortIDSpacket/snort-2.9.12.tar.gz
cd snort-2.9.12/
./configure --enable-sourcefire
make && make install四、配置snort
mkdir /etc/snort
cd /etc/snort
cp /usr/local/src/snort-2.9.12/etc/* /etc/snort/
mkdir SnortRules && cd SnortRules
tar -zvxf /home/centos/snortIDSpacket/snortrules-snapshot-29120.tar.gz
touch rules/white_list.rules rules/black_list.rulesgedit /etc/snort/snort.conf修改的内容:var RULE_PATH ../ruls --> var RULE_PATH /etc/snort/SnortRules/rules
var SO_RULE_PATH ../so_rules --> var SO_RULE_PATH /etc/snort/SnortRules/so_rules
var PREPROC_RULE_PATH ../preproc_rules --> var PREPROC_RULE_PATH /etc/snort/SnortRules/preproc_rules
var WHITE_LIST_PATH ../rules --> varWHITE_LIST_PATH /etc/snort/SnortRules/rules
var BLACK_LIST_PATH ../rules --> var BLACK_LIST_PATH /etc/snort/SnortRules/rules
config logdir : /var/log/snort(记得去掉前面的注释)
output unified2:filename snort.log,limit 128(记得去掉前面的注释)
五、添加用户和组
groupadd -g 40000 snort 创建一个新的组snort
useradd snort -u 40000 -d /var/log/snort -s /sbin/nologin -c SNORT_IDS -g snort
chown -R snort:snort * 六、开机自启
cd /usr/local/src/snort-2.9.12/rpm
cp snortd /etc/init.d/snortd
cp /usr/local/src/snort-2.9.12/rpm/snort.sysconfig /etc/sysconfig/snort
chkconfig --add /etc/init.d/snortd
chkconfig snortd on七、新建链接文件
cd /usr/sbin
ln -s /usr/local/bin/snort snort 八、新建目录设置权限
mkdir -p /usr/local/lib/snort_dynamicrules
chown -R snort:snort /usr/local/lib/snort_dynamicrules
chown -R 755 /usr/local/lib/snort_dynamicrules九、测试
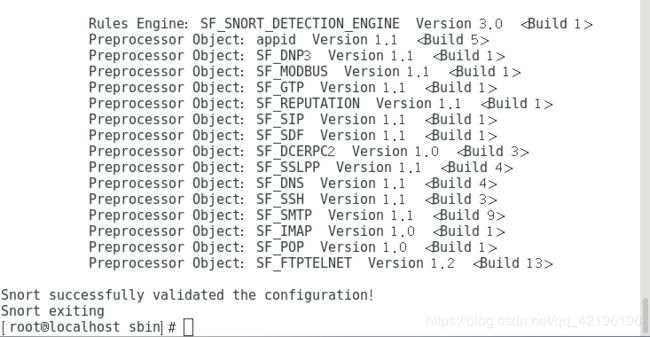
snort -T -i ens33 -u snort -g snort -c /etc/snort/snort.confgedit /etc/snort/SnortRules/rules/local.rules
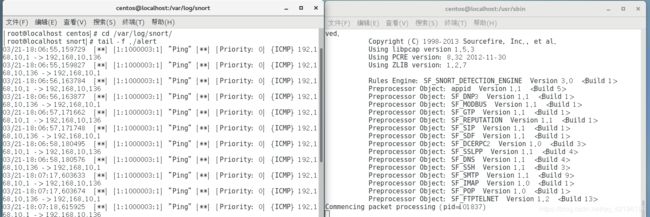
添加:alert icmp any any -> $HOME_NET any (msg:”Ping”;sid:1000003;rev:1;)snort -i ens33 -c /etc/snort/snort.conf -A fast -l /var/log/snort/
#另开一个终端
cd /var/log/snort/
tail -f ./alert十、安装mysql
wget http://repo.mysql.com/mysql57-community-release-el7.rpm #添加更新源
rpm -ivh mysql57-community-release-el7.rpm #安装更新源
yum install -y mysql-devel php-mysql php-adodb php-pear php-gd libtool php-imap php-ldap php-mbstring php-odbc php-pear php-xml php-pecl-apc mysql-server
chkconfig --levels 235 mysqld on
systemctl start mysqld十一、编译安装barnyard2
cd /usr/local/src/
tar -zxvf /home/centos/snortIDSpacket/barnyard2-1.9.tar.gz
cd barnyard2-1.9/
./configure --with-mysql --with-mysql-libraries=/usr/lib64/mysql
make && make install十二、配置数据库
grep "password" /var/log/mysqld.log #查看密码,复制粘贴
mysql -u root -p #登陆
mysql>set global validate_password_policy=0; #降低密码强度要求
mysql>set global validate_password_length=1;#降低密码长度要求
mysql>alter user 'root'@'localhost' identified by 'root'; #设置密码
mysql> grant create,select,update,insert,delete on snort.* to snort@localhost identified by 'mysql';
mysql> set password for 'snort'@'localhost'=password('mysql');
mysql>create database snort;
mysql>use snort;
mysql>source /usr/local/src/barnyard2-1.9/schemas/create_mysql;
mysql>show tables;
mysql>desc signature;
mysql>ALTER TABLE signature MODIFY sig_class_id int(10) NULL;
mysql>flush privileges;
mysql>exit;十三、配置barnyard2
barnyard2-1.9文件夹下
mkdir /var/log/barnyard2
touch /var/log/snort/barnyard2.waldo
chown snort.snort /var/log/snort/barnyard2.waldo
cp /usr/local/src/barnyard2-1.9/etc/barnyard2.conf /etc/snortgedit /etc/snort/barnyard2.conf
修改:
config logdir:/var/log/barnyard2 \该目录权限snort.snort(记得去掉注释)
config hostname: localhost(记得去掉注释)
config interface: ens33(记得去掉注释)
config waldo_file:/var/log/snort/barnyard2.waldo(记得去掉注释)
output database: log,mysql,user=snort password=mysql dbname=snort host=localhost(记得去掉注释)touch /var/log/snort/barnyard2.waldo
chown snort.snort /var/log/barnyard2
chown snort.snort /var/log/snort/barnyard2.waldo
cp /etc/snort/SnortRules/etc/sid-msg.map /etc/snort十四、snort和barnyard2联合测试
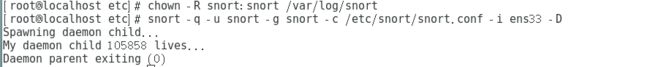
chown -R snort:snort /var/log/snort
snort -q -u snort -g snort -c /etc/snort/snort.conf -i ens33 -D十五、安装pear插件
yum install -y httpd mysql-server php php-mysql php-mbstring php-mcrypt mysql-devel php-gd mcrypt libmcrypt libmcrypt-devel php-pear
pear channel-update pear.php.net
pear install mail Image_Graph-alpha Image_Canvas-alpha Image_Color Numbers_Roman mail_mime十六、配置adodb base
cd /var/www/html/
unzip /home/centos/snortIDSpacket/adodb-5.20.14.zip
mv adodb5 adodb
tar -zxvf /home/centos/snortIDSpacket/base-1.4.5.tar.gz
mv base-1.4.5 base
gedit /etc/php.ini
修改>>error_reporting = E_ALL & ~E_NOTICE
chmod 777 /var/www/html/adodb
chmod 777 /var/www/html/base十七、启动
service mysqld start #启动mysql服务
service httpd start #启动http
systemctl stop firewalld.service #关闭防火墙
firewall-cmd --state #查看防火墙状态十八、Web配置
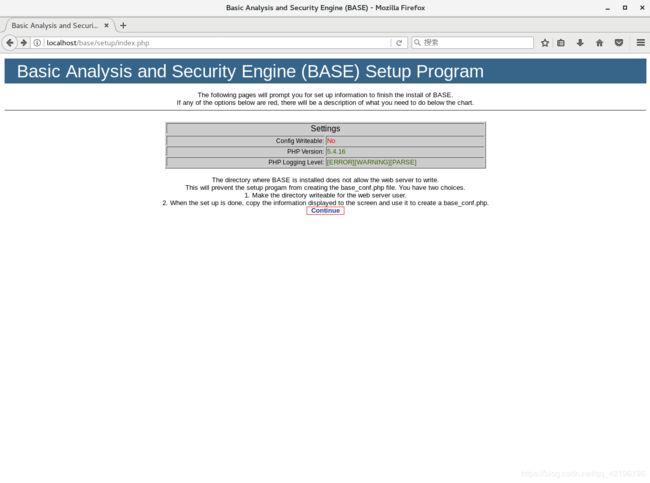
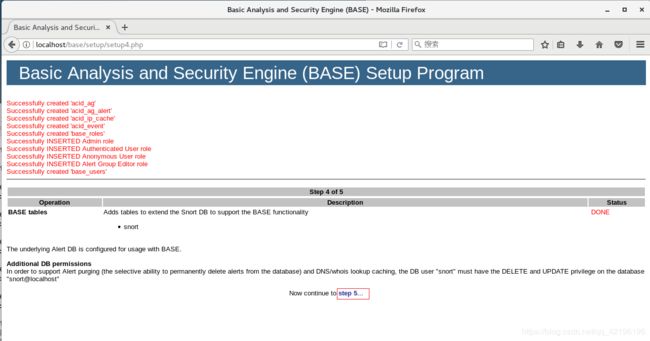
访问:http://localhost/base/setup/index.php
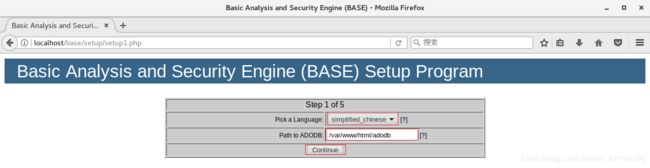
>>
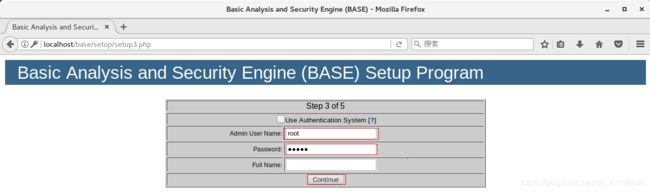
>>
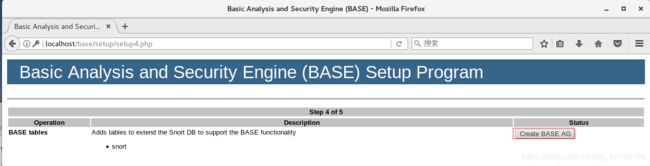
>>
>>
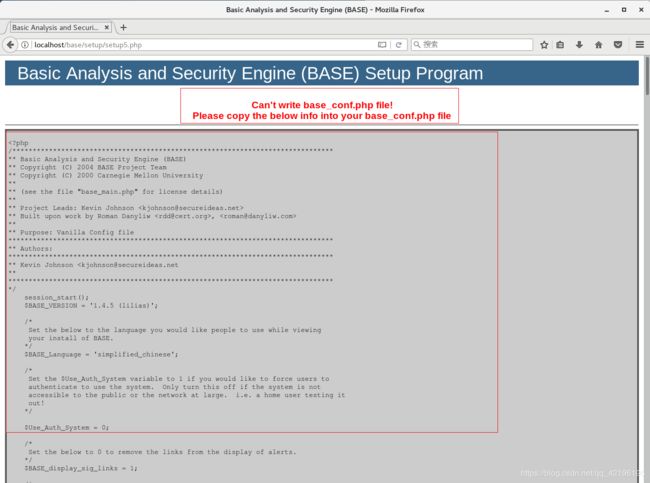
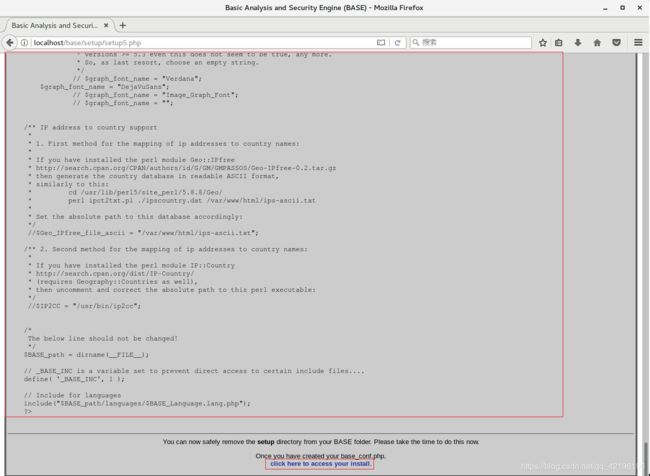
touch /var/www/html/base/base_conf.php
gedit /var/www/html/base/base_conf.php
将显示的代码复制上去
十九、启动IDS
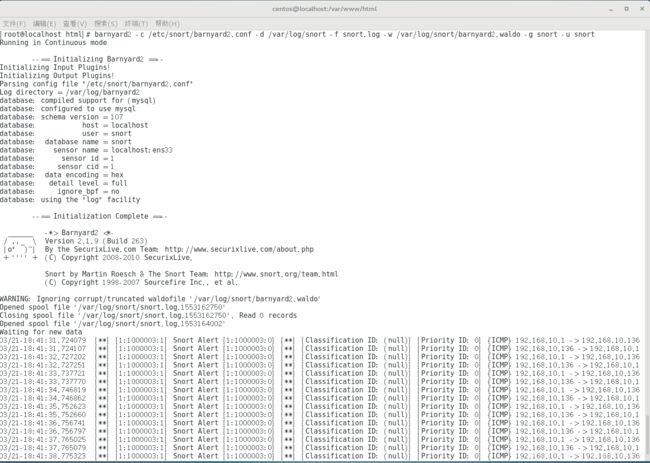
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snort
如果报错可能是权限问题
>>chown -R snort:snort /var/log/snort二十、其他
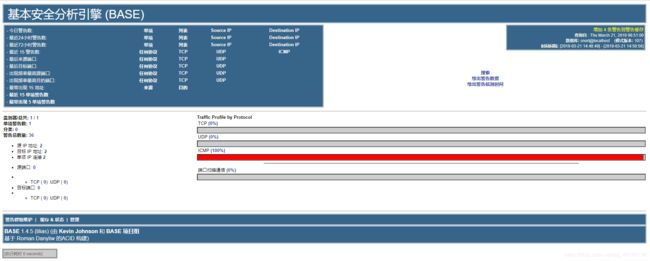
http://localhost/base/base_main.php
mysql -u snort -p -D snort -e "select count(*) from event" #检查告警是否存库
mysql -u snort -p -D snort -e "delete from event" #清空告警库
snort -q -u snort -g snort -c /etc/snort/snort.conf -i ens33 -D
-T:指定启动模式:测试
-i:指定网络接口
-u:指定运行用户
-g:指定运行时用户组
-c: 指定配置文件
-q:以静默方式运行
-D:后台以Daemon方式运行
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snort
snort -i ens33 -c /etc/snort/snort.conf -A fast -l /var/log/snort/
cd /var/log/snort/
tail -f ./alert