Scan Websites for Vulnerabilities with Arachni
Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.
Most of my experience I have acquired using the trial of fire method, I love to tinker and push the boundaries of my field. Enough about me let's get stuck in.
Before we get started I should state that this tutorial is for Linux based operating system's as I feel everyone who is in IT Security or interested in becoming an Ethical Hacker should be using some flavour of Linux.
Step 1 Downloading, Extraction, Moving and Renaming.
Let's begin by heading to the link below and downloading the 32 or 64bit version of Arachni. Reason's for choosing Linux is that the package is self-contained and no need to install any dependencies.
http://www.arachni-scanner.com/download/
Let's unpack this package, my default download location is /home/Downloads so let's cd and move it to the desktop
cd /home/Downloads
tar -xvzf arachni-1.4-0.5.10-linux-x8664.tar.gz
Now we want to open up our explorer and drag and drop the extracted file to the Desktop, and right click rename to arachni.
Step 2 Starting Everything Up.
From here we are going to open a Terminal and execute the following commands
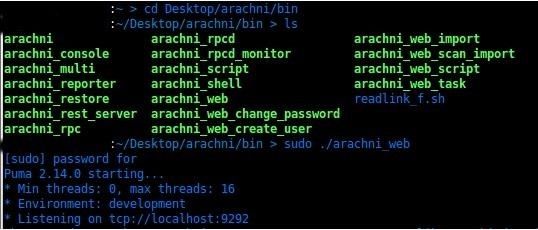
cd /Desktop/arachnid/bin
ls - to display all the files in the bin folder, we want to load arachniweb
sudo ./arachniweb
ctrl + shift + t - opens a new tab in your current terminal session.
sudo ./arachnirpcd
This start's our arachni web scanner which we can access at: localhost:9292
User Name: [email protected]
Password: administrator
Once logged in, we are greeted with a Welcome page that has some useful information on the homepage, such as Issues per scans and notifications about what you are involved with.
Step 3Executing Our Scan.
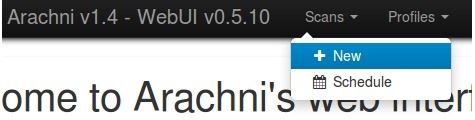
For this tutorial, we are going to be using it straight out of the box, head to the Scan's tab while hovering over it, you are presented with a couple of options. Click on + New which takes you to a new page.
From here it is pretty straight forward, input the target URL for this example we are using https://www.hackthissite.org/.
To the right of the Target, URL is a couple of options you can choose but we are going to keep it Default for this tutorial.
In advanced options, you get a couple of choices like how many instances's you would like or scheduling options which you can setup to scan your site(s) and when you would like the scans to stop.
Once you've filled in all the information click go, now all you have to do is wait.
I left my scan running for a total of 18 minutes before hitting stop, which once you do it generates a report listing all the vulnerabilities. This was just a simple scan using the default scan, the other scan's are XSS and SQL Injection.
So that's it for my tutorial on using Arachni for Web Vulnerability Assesment. Hope you enjoyed my tutorial as I might be making more depending on how this one goes.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter