DES算法理解--附《密码编码学与网络安全(第七版)》课后练习题答案
本文对EDS算法进行整理,并基于《密码编码学与网络安全(第七版)》中DES章节两道经典课后练习题,对DES加密和解密算法进行深化理解。
1 准备篇
这篇博客对DES算法原理进行了系统的讲述:
https://blog.csdn.net/qq_27570955/article/details/52442092
2 框架梳理
有了前面的准备工作,建立起自己对DES算法认知的流程框架。
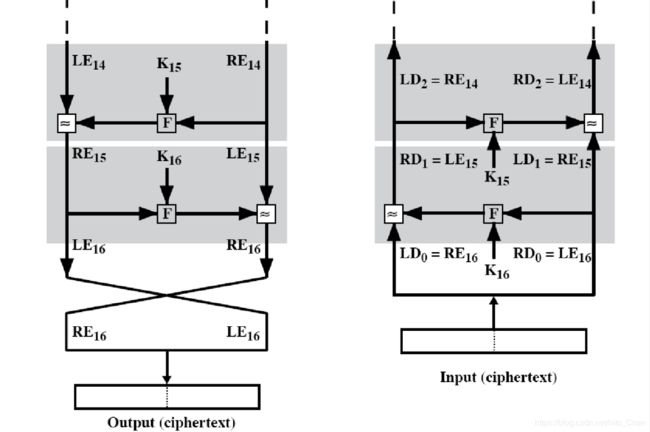
2.1 DES加密过程整体框架

2.2 DES加密过程乘积变换单轮迭代框架
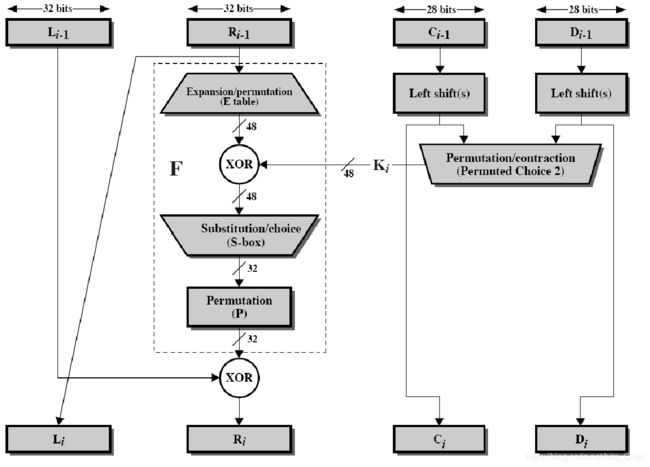
2.3 加密解密乘积变换(16轮迭代)框架
3 查询表
3.1 Initial Permutation (IP) and Inverse IP(置换和逆置换)
a. IP(置换)
58,50,42,34,26,18,10,2,
60,52,44,36,28,20,12,4,
62,54,46,38,30,22,14,6,
64,56,48,40,32,24,16,8,
57,49,41,33,25,17, 9,1,
59,51,43,35,27,19,11,3,
61,53,45,37,29,21,13,5,
63,55,47,39,31,23,15,7,
b. Inverse IP(逆置换)
40,8,48,16,56,24,64,32,39,7,47,15,55,23,63,31,
38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29,
36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,
34,2,42,10,50,18,58 26,33,1,41, 9,49,17,57,25,
3.2 Subkey子密钥生成
a. Permuted Choice One (PC-1)
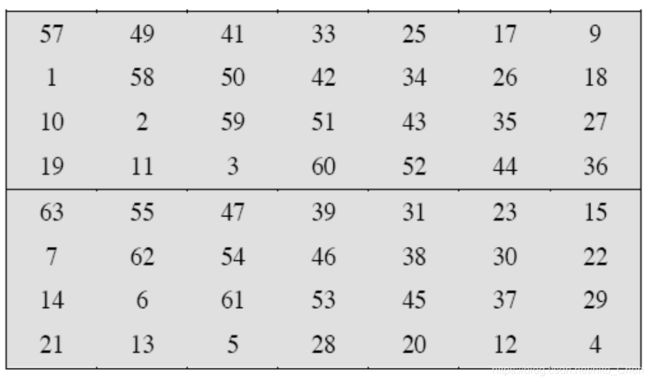
b. Permuted Choice Two (PC-2)

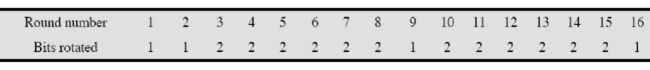
c. Schedule of Left Shifts
3.3 F 函数生成
a. Expansion Permutation (E-table)
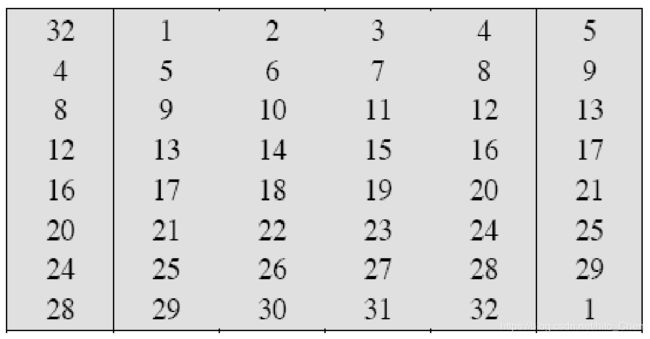
b. S-Boxes
S1:
14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7,
0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8,
4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0,
15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13,
S2:
15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10,
3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5,
0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15,
13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9,
S3:
10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8,
13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1,
13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7,
1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12,
S4:
7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15,
13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9,
10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4,
3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14,
S5:
2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9,
14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6,
4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14,
11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3,
S6:
12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11,
10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8,
9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6,
4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13,
S7:
4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,
13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6,
1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2,
6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12,
S8:
13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,
1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,
7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,
2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11,
c. Permutation Boxes (P(B))
16,7,20,21,29,12,28,17,1,15,23,26,5,18,31,10,
2,8,24,14,32,27,3,9,19,13,30,6,22,11,4,25,
4 XOR性质(计算技巧)
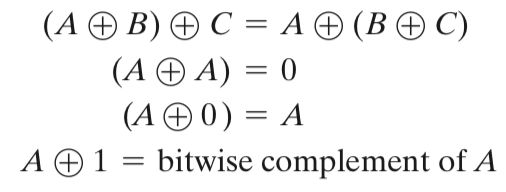

5 实操篇
下面,用《密码编码学与网络安全(第七版)》中DES章节两道课后练习题4.10和4.11,分别对解密和加密进行讨论和深化理解。
(PS: 字迹确实有点丑,将就着看吧…)
4.10 Compute the bits number 4, 17, 41, and 45 at the output of the first round of the DES decryption, assuming that the ciphertext block is composed of all ones and the external key is composed of all ones.
4.11 This problem provides a numerical example of encryption using a one-round version of DES. We start with the same bit pattern for the key K and the plaintext, namely:
Hexadecimal notation: 0 1 2 3 4 5 6 7 8 9 A B C D E F
Binary notation: 0000 0001 0010 0011 0100 0101 0110 0111
1000 1001 1010 1011 1100 1101 1110 1111
a. Derive K1, the first-round subkey.
b. Derive L0, R0.
c. Expand R0 to get E[R0], where E[·] is the expansion function of Table S.1.
d. Calculate R0
e. Group the 48-bit result of (d) into sets of 6 bits and evaluate the corresponding S-box substitutions.
f. Concatenate the results of (e) to get a 32-bit result, B.
g. Apply the permutation to get P(B).
h. Calculate.
i. Write down the ciphertext.
此为个人第一篇博客,内容均来自原创及互联网转载,最终目的为记录自己需要的内容或自己的学习感悟。如有任何勘误,望批评指正!!!