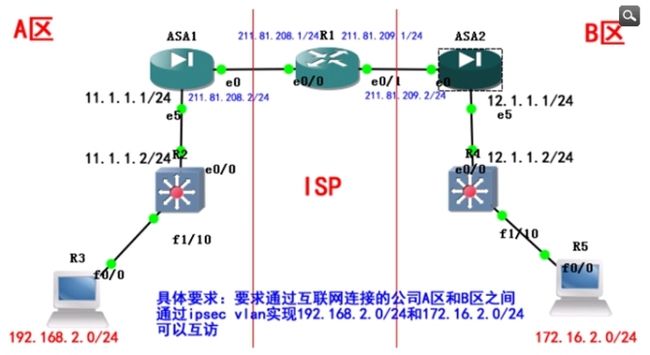
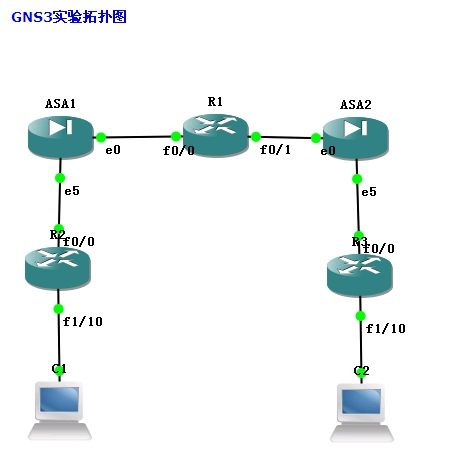
R1配置说明 :R1只需要按照图在接口上配置好ip地址。
!
version 12.4
!
hostname R1
!
interface FastEthernet0/0
ip address 211.81.208.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 211.81.209.1 255.255.255.0
duplex auto
speed auto
!
end
R2配置说明:R2在这里使用的是c3660-telco-mz.124-15.T5.bin的IOS,再在slot1插槽上加上NM-16ESW模块模拟交换机;R3同R2模拟交换机。
!
version 12.4
!
hostname R2
!
interface FastEthernet0/0
ip address 11.1.1.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/10
switchport access vlan 2
!
interface Vlan1
no ip address
!
interface Vlan2
ip address 192.168.2.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 11.1.1.1
!
end
R3配置说明
!
version 12.4
!
hostname R3
!
interface FastEthernet0/0
ip address 12.1.1.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/10
switchport access vlan 2
!
interface Vlan1
no ip address
!
interface Vlan2
ip address 172.16.2.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 12.1.1.1
!
end
ASA1配置说明
: Saved
:
ASA Version 8.0(2)
!
hostname asa1
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 211.81.208.2 255.255.255.0
!
interface Ethernet0/5
nameif inside
security-level 100
ip address 11.1.1.1 255.255.255.0
!
access-list icmp extended permit icmp any any
access-list nonat extended permit ip 192.168.2.0 255.255.255.0 172.16.2.0 255.255.255.0
access-list *** extended permit ip 192.168.2.0 255.255.255.0 172.16.2.0 255.255.255.0
global (outside) 1 interface
nat (inside) 0 access-list nonat
nat (inside) 1 0.0.0.0 0.0.0.0
access-group icmp in interface outside
route outside 0.0.0.0 0.0.0.0 211.81.208.1 1
route inside 192.168.2.0 255.255.255.0 11.1.1.2 1
crypto ipsec transform-set set esp-des esp-md5-hmac
crypto map map 111 match address ***
crypto map map 111 set peer 211.81.209.2
crypto map map 111 set transform-set set
crypto map map interface outside
crypto isakmp enable outside
crypto isakmp policy 11
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
tunnel-group 211.81.209.2 type ipsec-l2l
tunnel-group 211.81.209.2 ipsec-attributes
pre-shared-key *
: end
ASA2配置说明
asa2# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname asa2
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 211.81.209.2 255.255.255.0
!
interface Ethernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
nameif inside
security-level 100
ip address 12.1.1.1 255.255.255.0
!
access-list icmp extended permit icmp any any
access-list nonat extended permit ip 172.16.2.0 255.255.255.0 192.168.2.0 255.255.255.0
access-list *** extended permit ip 172.16.2.0 255.255.255.0 192.168.2.0 255.255.255.0
global (outside) 1 interface
nat (inside) 0 access-list nonat
nat (inside) 1 0.0.0.0 0.0.0.0
access-group icmp in interface outside
route outside 0.0.0.0 0.0.0.0 211.81.209.1 1
route inside 172.16.2.0 255.255.255.0 12.1.1.2 1
crypto ipsec transform-set set esp-des esp-md5-hmac
crypto map map 111 match address ***
crypto map map 111 set peer 211.81.208.2
crypto map map 111 set transform-set set
crypto map map interface outside
crypto isakmp enable outside
crypto isakmp policy 11
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
!
tunnel-group 211.81.208.2 type ipsec-l2l
tunnel-group 211.81.208.2 ipsec-attributes
pre-shared-key *
: end
配置过程详细:
ASA1配置详细:
1.端口基础配置
asa1(config)# interface ethernet 0/5
asa1(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
asa1(config-if)# security-level 100
asa1(config-if)# ip address 11.1.1.1 255.255.255.0
asa1(config-if)# no shutdown
asa1(config-if)# interface ethernet 0/0
asa1(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
asa1(config-if)# security-level 0
asa1(config-if)# ip address 211.81.208.2 255.255.255.0
asa1(config-if)# no shutdown