sql注入漏洞
PreparedStatement
可以有效防止
sql
注入,PreparedStatement会预编译sql语句,然后再注入参数,这样防止sql拼凑注入。而
Statment
不能防止
sql
注入,它是直接发送执行,因此可以借机拼凑sql语句。


使用Statement发送sql
Login.java
package com.cn.statement;import java.io.BufferedInputStream;import java.io.BufferedReader;import java.io.IOException;import java.io.InputStream;import java.io.InputStreamReader;import java.sql.Connection;import java.sql.ResultSet;import java.sql.Statement;import java.util.Scanner;import org.junit.Test;import com.cn.Util.JdbcUtil;/** * 模拟用户登录的效果 * @author liuzhiyong * */public class Login { //模拟用户输入账号密码 private String name = "木丁西"; private String password = "1234"; /** * 使用Statement模拟用户登录 * @throws Exception */ @Test public void testByStatement() throws Exception { //创建Scanner对象 Scanner sc = new Scanner(System.in); System.out.print("请输入用户名:"); name = sc.nextLine();//读取键盘输入 System.out.print("请输入密码:"); password = sc.nextLine();//读取键盘输入 // //创建输入字符流// BufferedReader keyReader = new BufferedReader(new InputStreamReader(System.in));//这里用到了输入字节流转换字符流// System.out.print("请输入用户名:");// name = keyReader.readLine();//接受键盘输入// System.out.print("请输入密码:");// password = keyReader.readLine();//接受键盘输入 Connection conn = null; Statement stmt = null; ResultSet rs = null; try { //获取连接 conn = JdbcUtil.getConnection(); //获取Statement stmt = conn.createStatement(); //准备sql String sql = "select * from users where name = '" + name + "' and password = '" + password+ "'"; //执行sql rs = stmt.executeQuery(sql); if(rs.next()){ //登录成功 System.out.println(name + "登录成功!"); }else{ System.out.println("登录失败!"); } } catch (Exception e) { e.printStackTrace(); throw new RuntimeException(e); }finally{ JdbcUtil.close(conn, stmt, rs); } }}// select * from users where name = 'jkljjljllasf' and password = 'fdasfdsf' or 1='1'
获取Connection连接和释放资源用JdbcUtil.java
package com.cn.Util;import java.sql.Connection;import java.sql.DriverManager;import java.sql.ResultSet;import java.sql.SQLException;import java.sql.Statement;/** * jdbc的工具类 * @author liuzhiyong * */public class JdbcUtil { private static String url = "jdbc:mysql://localhost:3306/mydb"; private static String user = "root"; private static String password = "root"; /** * 静态代码块(只调用一次) */ static{ //注册驱动程序 try { Class.forName("com.mysql.jdbc.Driver"); } catch (ClassNotFoundException e) { // TODO Auto-generated catch block e.printStackTrace(); System.out.println("驱动程序注册出错!"); } } /** * 获取连接对象的方法 */ public static Connection getConnection(){ try { Connection conn = DriverManager.getConnection(url, user, password); return conn; } catch (SQLException e) { // TODO Auto-generated catch block e.printStackTrace(); throw new RuntimeException(e); } } /** * 释放资源的方法 */ public static void close(Connection conn, Statement stmt, ResultSet rs){ //关闭资源(顺序:后打开,先关闭) if(rs != null){ try { rs.close(); } catch (SQLException e) { System.out.println("ResultSet关闭失败!"); throw new RuntimeException(e); } }if(stmt != null){ try { stmt.close(); } catch (SQLException e) { System.out.println("Statement关闭失败!"); throw new RuntimeException(e); } } if(conn != null){ try { conn.close(); } catch (SQLException e) { System.out.println("Connection关闭失败!"); throw new RuntimeException(e); } } } public static void close(Connection conn, Statement stmt){ //关闭资源(顺序:后打开,先关闭) if(stmt != null){ try { stmt.close(); } catch (SQLException e) { System.out.println("Statement关闭失败!"); throw new RuntimeException(e); } } if(conn != null){ try { conn.close(); } catch (SQLException e) { System.out.println("Connection关闭失败!"); throw new RuntimeException(e); } } } }
用户输入1:

其实sql注入拼凑成的代码为:
select * from users where name = '随便输入什么内容' and password = '' or '1'='1'
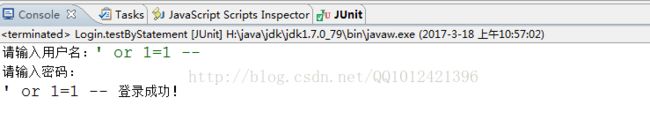
用户输入2:

其实sql注入拼凑成的代码为: (后面输入的被-- 注释掉了)
select * from users where name = '这是随便输入什么也可以不输入' or 1=1 -- ' and password = '这是随便输入什么也可以不输入'
用户输入3:
其实sql注入拼凑成的代码为:
(后面输入的被-- 注释掉了)

select * from users where name = '' or 1=1 -- ' and password = ''
使用PreparedStatement发送sql
package com.cn.statement;import java.sql.Connection;import java.sql.PreparedStatement;import java.sql.ResultSet;import java.sql.Statement;import java.util.Scanner;import org.junit.Test;import com.cn.Util.JdbcUtil;/** * 模拟用户登录的效果 * @author liuzhiyong * */public class Login { //模拟用户输入账号密码 private String name = "木丁西"; private String password = "1234"; /** * 使用PreparedStatement模拟用户登录 * @throws Exception */ @Test public void testByPrepatedStatement() throws Exception { //创建Scanner对象 Scanner sc = new Scanner(System.in); System.out.print("请输入用户名:"); name = sc.nextLine();//读取键盘输入 System.out.print("请输入密码:"); password = sc.nextLine();//读取键盘输入 Connection conn = null; PreparedStatement pstmt = null; ResultSet rs = null; try { //获取连接 conn = JdbcUtil.getConnection(); //准备sql String sql = "select * from users where name = ? and password = ?"; //预编译 pstmt = conn.prepareStatement(sql); //设置参数 pstmt.setString(1, name); pstmt.setString(2, password); //执行sql rs = pstmt.executeQuery(); if(rs.next()){ //登录成功 System.out.println(name + "登录成功!"); }else{ System.out.println("登录失败!");//select * from users where name = '' or 1=1 -- ' and password = '' } } catch (Exception e) { e.printStackTrace(); throw new RuntimeException(e); }finally{ JdbcUtil.close(conn, pstmt, rs); } }}
用户输入:
