高校抗役Writeup-MISC
目录
- ez_mem&usb
- 流量包分析
- 内存取证
- 隐藏的信息
ez_mem&usb
本题考察流量包分析以及内存取证
流量包分析
解压,发现是个流量包,扔进wireshark里,先把HTTP文件倒出来看看

在upload_file.php中发现上传了一个文件
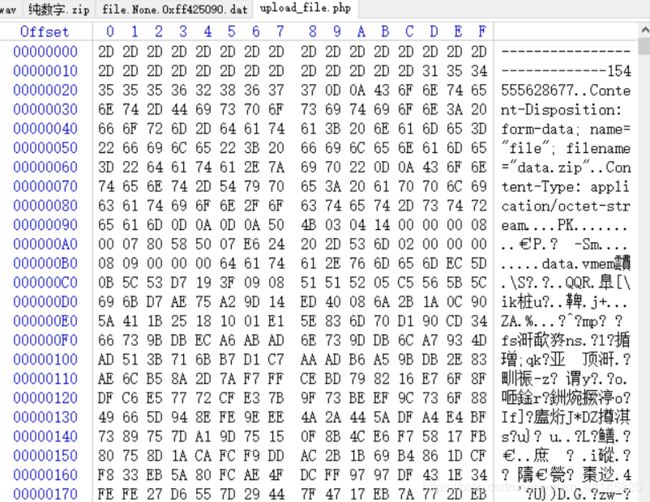
除去文件头和文件尾,保存为data.zip
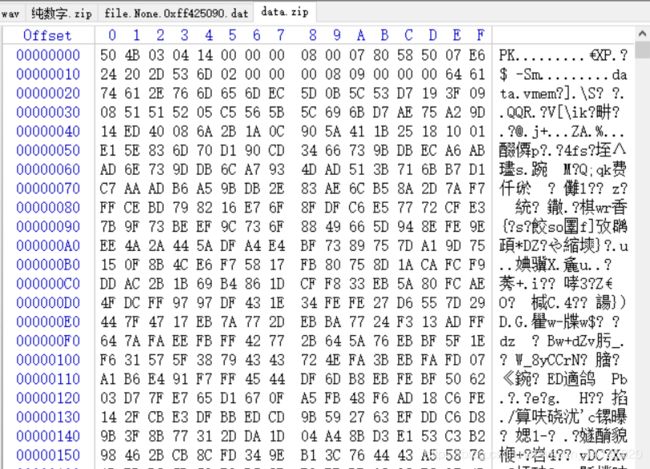

解压,得到一个data.vmem
内存取证
我们使用kali linux 中的volatility来进行内存取证
- 首先判断操作系统类型
volatility imageinfo -f data.vmem
volatility -f data.vmem --profile=WinXPSP2x86 pslist
- 提取命令历史记录
volatility -f data.vmem --profile=WinXPSP2x86 cmdscan
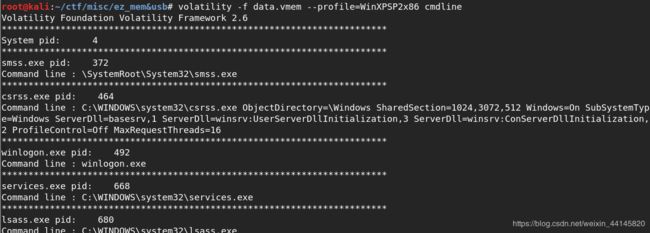
- . 通过cmdline查看命令行用到的参数,不过似乎没有什么重要信息
volatility -f data.vmem --profile=WinXPSP2x86 cmdline
- 查看文件目录,看看有没有flag文件
volatility -f data.vmem --profile=WinXPSP2x86 filescan | grep flag
- 导出文件
volatility -f data.vmem --profile=WinXPSP2x86 dumpfiles -Q 0x1155f90 --dump-dir=./
直接用binwalk和foremost提取出文件
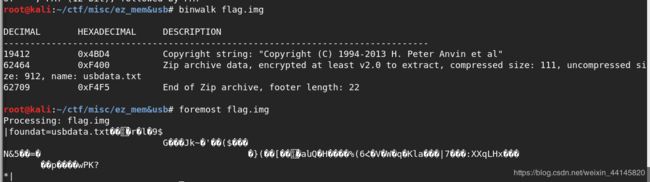
提取出一个加密的压缩包,回想起之前查看命令行记录看见的信息,故压缩包密码为 weak_auth_top100

解压之后发现如下文件
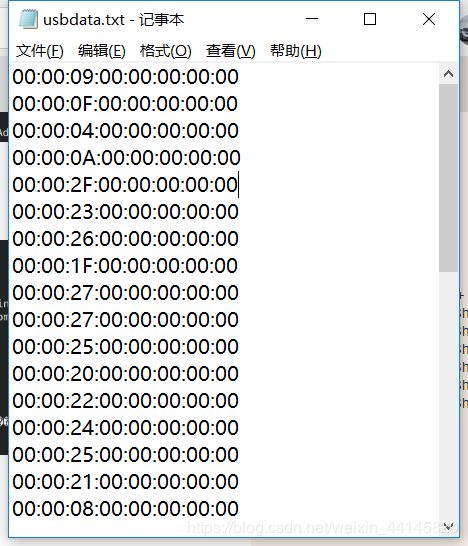
根据文件名usbdata,怀疑是抓到的键盘传输的数据包,使用以下脚本获得flag
hids_codes = {"0x04":"a","0x05":"b","0x06":"c","0x07":"d","0x08":"e","0x09":"f","0x0A":"g","0x0B":"h","0x0C":"i","0x0D":"j","0x0E":"k","0x0F":"l","0x10":"m","0x11":"n","0x12":"o","0x13":"p","0x14":"q","0x15":"r","0x16":"s","0x17":"t","0x18":"u","0x19":"v","0x1A":"w","0x1B":"x","0x1C":"y","0x1D":"z","0x1E":"1","0x1F":"2","0x20":"3","0x21":"4","0x22":"5","0x23":"6","0x24":"7","0x25":"8","0x26":"9","0x27":"0","0x36":",","0x33":":","0x28":"\n","0x2C":" ","0x2D":"_","0x2E":"=","0x2F":"{","0x30":"}"}
flag = ''
file = open('/root/ctf/misc/usbdata.txt','r')
for line in file.readlines():
conv = '0x' + line.split(':')[2].upper()
if conv in hids_codes:
if line[0:2] == '00':
flag += hids_codes[conv]
else:
flag += hids_codes[conv].upper()
print(flag)
隐藏的信息
使用AU打开WAV文件(这里的压缩包用了伪加密,使用360压缩可以直接解压)
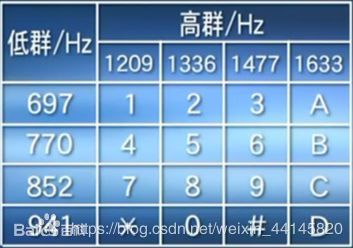
发现了开头和结尾有声音,开头听不出来,结尾可以听出是电话的按键声(DTMF)
把音乐开头和结尾的DTMF信号提取出来

根据下面的表对比得到12个数字:187485618521
在二维码中发现提示:


把得到的数字用base64加密得到flag:MTg3NDg1NjE4NTIx