Linux 远程访问及控制
远程访问及控制
文章目录
- 远程访问及控制
- SSH协议
- OpenSSH服务
- 构建密钥对验证的ssh体系
- 设置免密登录
- TCP Wrappers概述
SSH协议
是一种安全通道协议
为客户机提供安全的shell环境,用于远程管理
默认端口:TCP 22
OpenSSH服务
服务名称:sshd
服务端主程序:/usr/sbin/sshd
服务端配置文件:/etc/ssh/sshd_config
密钥
对称密钥:加密和解密用同一个密钥。AES DES 3DES 加密速度快,但是不安全
非对称密钥:加密和解密使用不同密钥,分为公钥和私钥。不可以从其中一种密钥推导出另一个密钥。RSA 加密速度慢 安全
ssh_config:针对客户端
sshd_config:针对服务端
访问形式 端口号
SSH:密文访问默认端口 TCP:22,一般广域网
Telnet:明文形式的访问 TCP 23,一般局域网
服务监听选项
端口号,协议版本,监听IP地址
禁用反向解析
进行远程登录
[root@localhost ~]# hostnamectl set-hostname test01
[root@localhost ~]# su
[root@test01 ~]# netstat -ntap | grep 22
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 9748/dnsmasq
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 9135/sshd
tcp 0 0 20.0.0.41:22 20.0.0.1:50684 ESTABLISHED 73425/sshd: root@pt
tcp6 0 0 :::22 :::* LISTEN 9135/sshd
[root@test01 ~]# grep "bash" /etc/passwd
root:x:0:0:root:/root:/bin/bash
hu:x:1000:1000:hu:/home/hu:/bin/bash
[root@test01 ~]# useradd zhangsan
[root@test01 ~]# passwd zhangsan
在另一台主机上
[root@localhost ~]# hostnamectl set-hostname test02
[root@localhost ~]# su
[root@test02 ~]# ssh [email protected]
The authenticity of host '20.0.0.41 (20.0.0.41)' can't be established.
ECDSA key fingerprint is SHA256:W+MleaejDosjJJV1F2noJPAGWA/d2qESydwosqTqWWw.
ECDSA key fingerprint is MD5:68:5f:ee:e5:76:ca:96:01:5d:d8:b9:1f:4b:5a:58:91.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '20.0.0.41' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Mon Jul 13 11:26:09 2020
[root@test01 ~]#
[root@test01 ~]# exit //退出当前bash环境
登出
Connection to 20.0.0.41 closed.
[root@test01 ~]# vim /etc/ssh/sshd_config
...
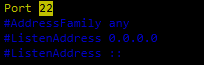
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
用户登录控制
禁止root用户,空密码用户
限制登录验证时间、重试次数
AllowUsers(白名单,仅允许某些用户,拒绝所有人 安全性场合高)
DenyUsers(黑名单,仅拒绝某些用户,允许所与人 安全性场合低)
AllowUsers不要与DenyUsers同时用
[root@localhost ~]# vim /etc/ssh/sshd_config
……
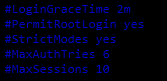
#LoginGraceTime 2m //会话时间
#PermitRootLogin yes //允许管理员进行登录
#StrictModes yes
#MaxAuthTries 6 //最大尝试次数
#MaxSessions 10 //最大会话连接
AllowUsers zhangsan [email protected]
验证方式
密码验证:核对用户名、密码是否匹配
密钥对验证:核对客户的私钥、服务端公钥是否匹配
[root@localhost ~]# vim /etc/ssh/sshd_config
……
PasswordAuthentication yes 是否使用密码
PermitEmptyPasswords no 禁止空密码
PubkeyAuthentication yes 开启公钥验证
AuthorizedKeysFile .ssh/authorized_keys 指定公钥库位置
构建密钥对验证的ssh体系
构建密钥对验证的SSH体系
在客户机创建密钥对
ssh-keygen命令
可用的加密算法:RSA、ECDSA或DSA
将公钥文件上传至服务器
任何方式均可(FTP、Email、SCP、HTTP……)
在服务器中导入公钥文本
将公钥文本添加至目标用户的公钥库
默认公钥库位置:~/.ssh/authorized_keys
[root@test01 ~]# vim /etc/ssh/sshd_config
![]()
![]()
[root@test01 ~]# systemctl restart sshd
[root@test02 ~]# useradd lisi
[root@test02 ~]# passwd lisi
[root@test02 ~]# su lisi
[lisi@test02 root]$ ssh-keygen -t ecdsa
Generating public/private ecdsa key pair.
Enter file in which to save the key (/home/lisi/.ssh/id_ecdsa):
Created directory '/home/lisi/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/lisi/.ssh/id_ecdsa.
Your public key has been saved in /home/lisi/.ssh/id_ecdsa.pub.
The key fingerprint is:
SHA256:h1Nb+dtsaNr/+oDgDc9gbtKDX+63gas3cZ9yyxPdX30 lisi@test02
The key's randomart image is:
+---[ECDSA 256]---+
| |
| . |
| . o |
| o o . |
| S B . +|
| O B.o.*E|
| o * Bo*.X|
| + +o*oBo|
| o+=o*BB|
+----[SHA256]-----+
[lisi@test02 root]$ cd ~
[lisi@test02 ~]$ cd .ssh/
[lisi@test02 .ssh]$ ls -a
. .. id_ecdsa id_ecdsa.pub
[lisi@test02 .ssh]$ ssh-copy-id -i id_ecdsa.pub [email protected]
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "id_ecdsa.pub"
The authenticity of host '20.0.0.41 (20.0.0.41)' can't be established.
ECDSA key fingerprint is SHA256:W+MleaejDosjJJV1F2noJPAGWA/d2qESydwosqTqWWw.
ECDSA key fingerprint is MD5:68:5f:ee:e5:76:ca:96:01:5d:d8:b9:1f:4b:5a:58:91.
Are you sure you want to continue connecting (yes/no)? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '[email protected]'"
and check to make sure that only the key(s) you wanted were added.
[root@test01 ~]# cd /home/zhangsan
[root@test01 zhangsan]# ls -a
. .. .bash_history .bash_logout .bash_profile .bashrc .cache .config .mozilla .ssh
[root@test01 zhangsan]# cd .ssh/
[root@test01 .ssh]# ls -a
. .. authorized_keys
[root@test01 .ssh]# cat authorized_keys
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDUz9pe7DeEX87424oxSLxGB7RCbr0KwA6mDMaq4oyuU0FfgeQ7J9+VusH1+UgPVAwvCtoLUT+W8xi12dvHtmdQ= lisi@test02
[root@test01 .ssh]#
[lisi@test02 .ssh]$ ssh [email protected]
Enter passphrase for key '/home/lisi/.ssh/id_ecdsa':
Last login: Mon Jul 13 11:48:11 2020
[zhangsan@test01 ~]$
设置免密登录
[lisi@test02 .ssh]$ ssh-agent bash //代理终端
[lisi@test02 .ssh]$ ssh-add //添加免密密码
Enter passphrase for /home/lisi/.ssh/id_ecdsa:
Identity added: /home/lisi/.ssh/id_ecdsa (/home/lisi/.ssh/id_ecdsa)
[lisi@test02 .ssh]$ ssh [email protected]
Last login: Mon Jul 13 12:10:36 2020 from 20.0.0.51
[zhangsan@test01 ~]$
使用SSH客户端程序
ssh命令——远程安全登录
scp命令——远程安全复制
sftp命令——安全FTP上下载
TCP Wrappers概述
保护原理
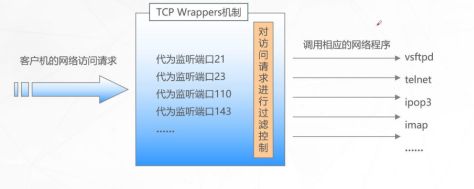
保护机制的实现方式
方式1:通过tcpd程序对其他服务程序进行包装
方式2:有其他服务程序调用libwrap.so.*.链接库
访问控制策略的配置文件
/etc/hosts.allow
/etc/hosts.deny
设置访问控制策略
策略格式
服务列表:客户机地址列表
服务列表
多个服务以逗号分隔,ALL表示所有服务
客户机地址列表
多个地址以逗号分隔,ALL表示所有服务
允许使用通配符*和?
网段地址,如192.168.1 或者 192.168.1.0/255.255.255.0
区域地址,如.benet.com
策略的应用顺序
先检查hosts.allow,找到匹配则允许访问
再检查hosts.deny,找到则拒绝访问
若两个文件中均无匹配策略,则默认允许访问