Kubernetes K8S之SSL证书有效期修改
如何修改Kubernetes的SSL证书有效期
主机配置规划
| 服务器名称(hostname) | 系统版本 | 配置 | 内网IP | 外网IP(模拟) |
|---|---|---|---|---|
| k8s-master | CentOS7.7 | 2C/4G/20G | 172.16.1.110 | 10.0.0.110 |
| k8s-node01 | CentOS7.7 | 2C/4G/20G | 172.16.1.111 | 10.0.0.111 |
| k8s-node02 | CentOS7.7 | 2C/4G/20G | 172.16.1.112 | 10.0.0.112 |
为什么要修改证书有效期
Kubernetes默认的证书有效期都是1年,因此需要我们每年都更新证书,显然这对我们实际生产环境来说是很不友好的;因此我们要对Kubernetes的SSL证书有效期进行修改。
证书有效期查看
[root@k8s-master pki]# pwd
/etc/kubernetes/pki
[root@k8s-master pki]# ll
total 56
-rw-r--r-- 1 root root 1224 May 12 15:51 apiserver.crt
-rw-r--r-- 1 root root 1090 May 12 15:51 apiserver-etcd-client.crt
-rw------- 1 root root 1675 May 12 15:51 apiserver-etcd-client.key
-rw------- 1 root root 1675 May 12 15:51 apiserver.key
-rw-r--r-- 1 root root 1099 May 12 15:51 apiserver-kubelet-client.crt
-rw------- 1 root root 1675 May 12 15:51 apiserver-kubelet-client.key
-rw-r--r-- 1 root root 1025 May 12 15:51 ca.crt
-rw------- 1 root root 1675 May 12 15:51 ca.key
drwxr-xr-x 2 root root 162 May 12 15:51 etcd
-rw-r--r-- 1 root root 1038 May 12 15:51 front-proxy-ca.crt
-rw------- 1 root root 1675 May 12 15:51 front-proxy-ca.key
-rw-r--r-- 1 root root 1058 May 12 15:51 front-proxy-client.crt
-rw------- 1 root root 1675 May 12 15:51 front-proxy-client.key
-rw------- 1 root root 1679 May 12 15:51 sa.key
-rw------- 1 root root 451 May 12 15:51 sa.pub
[root@k8s-master pki]#
[root@k8s-master pki]# for i in $(ls *.crt); do echo "===== $i ====="; openssl x509 -in $i -text -noout | grep -A 3 'Validity' ; done
===== apiserver.crt =====
Validity
Not Before: May 12 07:51:36 2020 GMT
Not After : May 12 07:51:36 2021 GMT
Subject: CN=kube-apiserver
===== apiserver-etcd-client.crt =====
Validity
Not Before: May 12 07:51:37 2020 GMT
Not After : May 12 07:51:38 2021 GMT
Subject: O=system:masters, CN=kube-apiserver-etcd-client
===== apiserver-kubelet-client.crt =====
Validity
Not Before: May 12 07:51:36 2020 GMT
Not After : May 12 07:51:37 2021 GMT
Subject: O=system:masters, CN=kube-apiserver-kubelet-client
===== ca.crt =====
Validity
Not Before: May 12 07:51:36 2020 GMT
Not After : May 10 07:51:36 2030 GMT
Subject: CN=kubernetes
===== front-proxy-ca.crt =====
Validity
Not Before: May 12 07:51:37 2020 GMT
Not After : May 10 07:51:37 2030 GMT
Subject: CN=front-proxy-ca
===== front-proxy-client.crt =====
Validity
Not Before: May 12 07:51:37 2020 GMT
Not After : May 12 07:51:37 2021 GMT
Subject: CN=front-proxy-client
[root@k8s-master pki]#
由上可见,除了ca根证书,其他证书有效期都是1年。
证书有效时限修改
go环境部署
go语言中文网
https://studygolang.com/
在Linux命令行下载
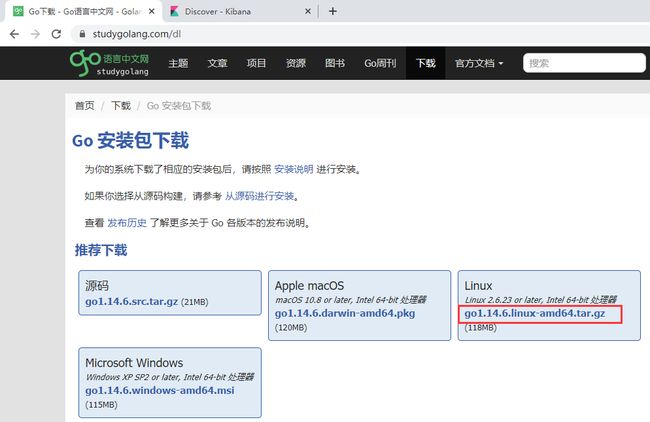
[root@k8s-master software]# wget https://studygolang.com/dl/golang/go1.14.6.linux-amd64.tar.gz
[root@k8s-master software]# tar xf go1.14.6.linux-amd64.tar.gz -C /usr/local/
[root@k8s-master software]# vim /etc/profile # 最后面添加如下信息
# go语言环境变量
export PATH=$PATH:/usr/local/go/bin
[root@k8s-master software]# source /etc/profile
Kubernetes源码下载与更改证书策略
当期k8s版本
[root@k8s-master software]# kubectl version
Client Version: version.Info{Major:"1", Minor:"17", GitVersion:"v1.17.4", GitCommit:"8d8aa39598534325ad77120c120a22b3a990b5ea", GitTreeState:"clean", BuildDate:"2020-03-12T21:03:42Z", GoVersion:"go1.13.8", Compiler:"gc", Platform:"linux/amd64"}
Server Version: version.Info{Major:"1", Minor:"17", GitVersion:"v1.17.4", GitCommit:"8d8aa39598534325ad77120c120a22b3a990b5ea", GitTreeState:"clean", BuildDate:"2020-03-12T20:55:23Z", GoVersion:"go1.13.8", Compiler:"gc", Platform:"linux/amd64"}
根据k8s版本下载源码
操作步骤
[root@k8s-master software]# wget https://github.com/kubernetes/kubernetes/archive/v1.17.4.tar.gz
[root@k8s-master software]# tar xf v1.17.4.tar.gz && cd kubernetes-1.17.4
[root@k8s-master kubernetes-1.17.4]# vim cmd/kubeadm/app/util/pkiutil/pki_helpers.go
………………
func NewSignedCert(cfg *certutil.Config, key crypto.Signer, caCert *x509.Certificate, caKey crypto.Signer) (*x509.Certificate, error) {
// 添加如下行 有效时间 100 年
const effectyear = time.Hour * 24 * 365 * 100
serial, err := cryptorand.Int(cryptorand.Reader, new(big.Int).SetInt64(math.MaxInt64))
if err != nil {
return nil, err
}
if len(cfg.CommonName) == 0 {
return nil, errors.New("must specify a CommonName")
}
if len(cfg.Usages) == 0 {
return nil, errors.New("must specify at least one ExtKeyUsage")
}
certTmpl := x509.Certificate{
Subject: pkix.Name{
CommonName: cfg.CommonName,
Organization: cfg.Organization,
},
DNSNames: cfg.AltNames.DNSNames,
IPAddresses: cfg.AltNames.IPs,
SerialNumber: serial,
NotBefore: caCert.NotBefore,
// NotAfter: time.Now().Add(kubeadmconstants.CertificateValidity).UTC(),
NotAfter: time.Now().Add(effectyear).UTC(), // 修改行
KeyUsage: x509.KeyUsageKeyEncipherment | x509.KeyUsageDigitalSignature,
ExtKeyUsage: cfg.Usages,
}
[root@k8s-master kubernetes-1.17.4]#
# 注意路径
[root@k8s-master kubernetes-1.17.4]# make WHAT=cmd/kubeadm GOFLAGS=-v
# 将更新后的kubeadm拷贝到指定位置
[root@k8s-master kubernetes-1.17.4]# cp -a _output/bin/kubeadm /root/kubeadm-new
更新kubeadm并备份原证书
# kubeadm更新
mv /usr/bin/kubeadm /usr/bin/kubeadm_20200725
mv /root/kubeadm-new /usr/bin/kubeadm
chmod 755 /usr/bin/kubeadm
# 原证书备份
cp -a /etc/kubernetes/pki/ /etc/kubernetes/pki_20200725
证书更新
操作如下:
# 证书更新
[root@k8s-master ~]# kubeadm alpha certs renew all --config=/root/k8s_install/kubeadm-config.yaml
# 查看新证书有效期
[root@k8s-master ~]# cd /etc/kubernetes/pki
[root@k8s-master pki]# ll
total 56
-rw-r--r-- 1 root root 1224 Jul 25 18:44 apiserver.crt
-rw-r--r-- 1 root root 1094 Jul 25 18:44 apiserver-etcd-client.crt
-rw------- 1 root root 1675 Jul 25 18:44 apiserver-etcd-client.key
-rw------- 1 root root 1679 Jul 25 18:44 apiserver.key
-rw-r--r-- 1 root root 1103 Jul 25 18:44 apiserver-kubelet-client.crt
-rw------- 1 root root 1679 Jul 25 18:44 apiserver-kubelet-client.key
-rw-r--r-- 1 root root 1025 May 12 15:51 ca.crt
-rw------- 1 root root 1675 May 12 15:51 ca.key
drwxr-xr-x 2 root root 162 May 12 15:51 etcd
-rw-r--r-- 1 root root 1038 May 12 15:51 front-proxy-ca.crt
-rw------- 1 root root 1675 May 12 15:51 front-proxy-ca.key
-rw-r--r-- 1 root root 1058 Jul 25 18:44 front-proxy-client.crt
-rw------- 1 root root 1679 Jul 25 18:44 front-proxy-client.key
-rw------- 1 root root 1679 May 12 15:51 sa.key
-rw------- 1 root root 451 May 12 15:51 sa.pub
[root@k8s-master pki]#
[root@k8s-master pki]# for i in $(ls *.crt); do echo "===== $i ====="; openssl x509 -in $i -text -noout | grep -A 3 'Validity' ; done
===== apiserver.crt =====
Validity
Not Before: May 12 07:51:36 2020 GMT
Not After : Jul 1 10:44:20 2120 GMT
Subject: CN=kube-apiserver
===== apiserver-etcd-client.crt =====
Validity
Not Before: May 12 07:51:37 2020 GMT
Not After : Jul 1 10:44:20 2120 GMT
Subject: O=system:masters, CN=kube-apiserver-etcd-client
===== apiserver-kubelet-client.crt =====
Validity
Not Before: May 12 07:51:36 2020 GMT
Not After : Jul 1 10:44:20 2120 GMT
Subject: O=system:masters, CN=kube-apiserver-kubelet-client
===== ca.crt =====
Validity
Not Before: May 12 07:51:36 2020 GMT
Not After : May 10 07:51:36 2030 GMT
Subject: CN=kubernetes
===== front-proxy-ca.crt =====
Validity
Not Before: May 12 07:51:37 2020 GMT
Not After : May 10 07:51:37 2030 GMT
Subject: CN=front-proxy-ca
===== front-proxy-client.crt =====
Validity
Not Before: May 12 07:51:37 2020 GMT
Not After : Jul 1 10:44:22 2120 GMT
Subject: CN=front-proxy-client
由上可见,除了CA根证书,其他证书有效期已经改为 100 年。
kubeadm-config.yaml文件参见如下
[root@k8s-master k8s_install]# pwd
/root/k8s_install
[root@k8s-master k8s_install]# kubeadm config print init-defaults > kubeadm-config.yaml
# 做了适当修改
[root@k8s-master k8s_install]# cat kubeadm-config.yaml
apiVersion: kubeadm.k8s.io/v1beta2
bootstrapTokens:
- groups:
- system:bootstrappers:kubeadm:default-node-token
token: abcdef.0123456789abcdef
ttl: 24h0m0s
usages:
- signing
- authentication
kind: InitConfiguration
localAPIEndpoint:
# 改为本机内网IP
advertiseAddress: 172.16.1.110
bindPort: 6443
nodeRegistration:
criSocket: /var/run/dockershim.sock
name: k8s-master
taints:
- effect: NoSchedule
key: node-role.kubernetes.io/master
---
apiServer:
timeoutForControlPlane: 4m0s
apiVersion: kubeadm.k8s.io/v1beta2
certificatesDir: /etc/kubernetes/pki
clusterName: kubernetes
controllerManager: {}
dns:
type: CoreDNS
etcd:
local:
dataDir: /var/lib/etcd
imageRepository: k8s.gcr.io
kind: ClusterConfiguration
# 本次部署的版本为 v1.17.4
kubernetesVersion: v1.17.4
networking:
dnsDomain: cluster.local
# 添加如下行,指定pod网络的IP地址范围,因为flannel 就是这个网段
podSubnet: 10.244.0.0/16
# 默认值即可,无需改变。服务VIP使用可选的IP地址范围。默认10.96.0.0/12
serviceSubnet: 10.96.0.0/12
scheduler: {}
---
# 添加如下配置段,调度方式从默认改为ipvs方式【如果上面初始化没有做ipvs,那么这段就不需要】
apiVersion: kubeproxy.config.k8s.io/v1alpha1
kind: KubeProxyConfiguration
featureGates:
SupportIPVSProxyMode: true
mode: ipvs
相关阅读
1、基于kubeadm快速部署kubernetes K8S V1.17.4集群-无坑完整版
完毕!
![]()