如何设置SSH公钥身份验证
Being familiar with SSH and the command-line is essential to good web development. This article is geared towards people who already have a basic understanding of the command line and using Secure Shell (SSH), but would like to improve and streamline remotely connecting to servers. Things that we'll cover are:
熟悉SSH和命令行对于良好的Web开发至关重要。 本文适用于已经对命令行有基本了解并使用安全外壳(SSH),但是希望改进和简化远程连接服务器的人员。 我们将介绍的内容包括:
| 1 | Understanding public and private key cryptography |
| 2 | Security implications for SSH public-key authentication vs. password authentication. |
| 3 | Generating SSH keys |
| 4 | Setting it all up |
| 5 | Different methods for copying your public key to remote servers |
| 6 | Creating SSH shortcuts |
| 1个 | 了解公钥和私钥加密 |
| 2 | SSH公钥身份验证与密码身份验证的安全隐患。 |
| 3 | 生成SSH密钥 |
| 4 | 全部设置 |
| 5 | 将公钥复制到远程服务器的不同方法 |
| 6 | 创建SSH快捷方式 |
什么是公钥密码术? (What is Public Key Cryptography?)
SSH is short for Secure Shell. The most commonly used SSH server on Linux is called OpenSSH. Luckily, unless you're truly building a server from scratch, OpenSSH is probably bundled on your local machine and remote server. If it's not, a simple Google Search should help you get started on that front.
SSH是Secure Shell的缩写。 Linux上最常用的SSH服务器称为OpenSSH 。 幸运的是,除非您是从头开始真正构建服务器,否则OpenSSH可能会捆绑在本地计算机和远程服务器上。 如果不是这样,一个简单的Google搜索应该可以帮助您入门。
Open SSH is awesome because it allows for Public and Private Key Pairing. Public and Private Key Pairing can be used for all sorts of stuff. Some common examples include, plain-old encryption, server authentication, and Git authentication.
Open SSH非常棒,因为它允许公钥和私钥配对。 公钥和私钥配对可用于各种东西。 一些常见的示例包括普通加密,服务器身份验证和Git身份验证。
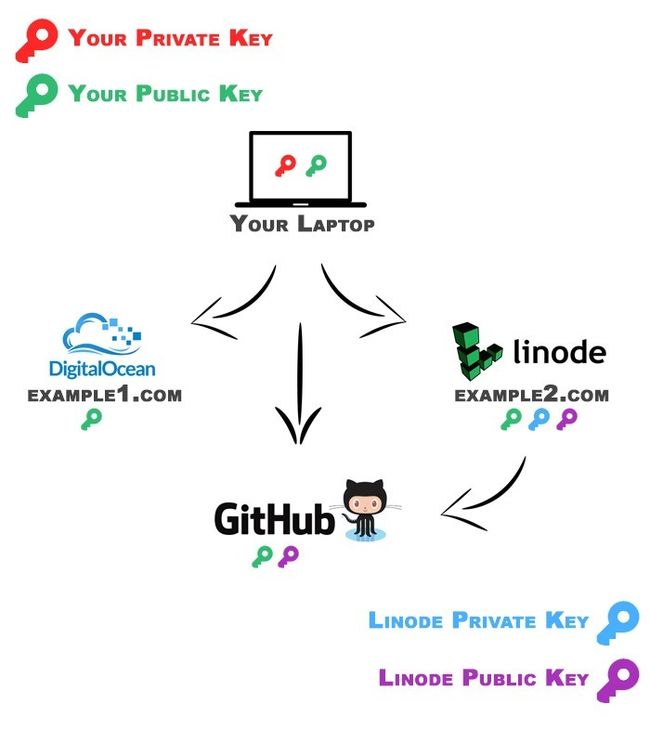
Key Pairs work by having two keys: a Public and a Private Key. The Private Key is not meant to be shared anywhere but the computer it is on (if it be the private key of your local laptop or the private key of a remote server). The Public Key, however, is intended to be put on any other computer/server you would like to pair the private key with. You can put the public key on as many different computers or servers as you would like. Here's an example to help explain:
密钥对通过具有两个密钥来工作:公钥和私钥。 私钥不是要在任何地方共享,而是要在其所在的计算机上共享(如果它是本地笔记本电脑的私钥或远程服务器的私钥)。 但是, 公钥应放置在要与私钥配对的任何其他计算机/服务器上。 您可以将公用密钥放置在任意多台不同的计算机或服务器上。 这是一个示例以帮助说明:
Your Laptop" has its Public Key on Digital Ocean, Linode, and GitHub. This means that if Your Laptop communicates with these servers, its Private Key will sign and authenticate with the Public Key. Once this happens, Your Laptop is now authenticated and verified to be given access.您的笔记本电脑 ”在Digital Ocean , Linode和GitHub上都有其公共密钥。 这意味着,如果您的笔记本电脑与这些服务器通信,则其私钥将使用公钥签名并进行身份验证。 一旦发生这种情况,便可以对您的笔记本电脑进行身份验证和验证,使其具有访问权限。
This authentication can only occur one-way, meaning that although Your Laptop can access Digital Ocean, Linode, and Github, they won't be able to access Your Laptop from the pairing.
此身份验证只能单向发生,这意味着尽管您的笔记本电脑可以访问Digital Ocean,Linode和Github,但它们将无法从配对中访问您的笔记本电脑。
Lastly, you'll also notice that Key Pairing has been setup with the Linode server and Github as well.
最后,您还会注意到Linode服务器和Github也已经设置了密钥配对。
This is a brief and general explanation. I definitely advise anyone interested in learning more specifically how it works to read up on it more than my laymen terms explanation. Here's some more sources:
这是一个简短而笼统的解释。 我绝对建议那些有兴趣更具体地学习它的人,而不是我的外行术语解释。 这里有更多的来源:
- Wikipedia: Public-key cryptography 维基百科:公钥加密
- Ubuntu Docs Ubuntu文档
公钥认证与密码认证 (Public Key Authentication versus Password Authentication)
In terms of security, this is somewhat hotly debated. They're both secure methods, but which one offers more protection is generally the topic of debate. The answer to this is it really just comes down to how much you trust the users.
在安全性方面,这引起了激烈的争论。 它们都是安全的方法,但是哪种方法提供更多的保护通常是争论的话题。 答案是,这实际上取决于您对用户的信任程度。
It's assumed by most that the a user won't remember or cannot be trusted enough to use a secure password. This means it's probably safer to use key-pair authentication. Some server admins will even recommend disabling password authentication. The main issue with this though is that if the user's computer gets compromised, they're essentially losing their key to multiple servers (needing to reset the key-pair for each one). Here's an awesome excerpt by Tek Tengu that helps explain the issue:
大多数人认为用户将不会记住或无法信任用户使用安全密码。 这意味着使用密钥对身份验证可能更安全。 一些服务器管理员甚至建议禁用密码身份验证。 但是,这样做的主要问题是,如果用户的计算机受到威胁,则他们实际上会将其密钥丢失给多个服务器(需要为每个服务器重置密钥对)。 这是Tek Tengu的精彩摘录,可帮助解释该问题:
It's kind of like this... I am divorced and have a vitriolic ex wife. I also have three great boys, who like most boys, can be forgetful, lose things, as well as love their mom. When my boys got old enough to need a key to my house, I had a decision to make. Do I put a key'ed lock or one of those numeric key pads. If I put the key'ed lock it was certain that my sons would regularly be losing keys, I would be getting calls to come home from work to let them in, and there was a big possibility I would have to replace the lock or have it re-keyed from time-to-time because well, the number of "lost keys" (or probability my vitriolic ex wife now possessed one) reached an uncomfortable limit.
有点像...我离婚了,有一个有硫酸的前妻。 我还有三个好孩子,他们和大多数孩子一样,可以健忘,丢东西,也可以爱他们的妈妈。 当我的男孩长大到需要一把房子的钥匙时,我便做出了决定。 我是否要放置钥匙锁或这些数字键盘之一。 如果我放上钥匙锁,可以肯定的是我的儿子经常会丢失钥匙,我会接到下班回家的电话让他们进去,而我很有可能不得不更换锁或它会不时地重新设置密钥,因为好吧,“丢失的密钥”的数量(或者说我的前妻现在已经拥有了这个概率)达到了令人不舒服的极限。
The numeric lock on the other hand, while not maybe the safest in the world, I had no concerns about the keys being lost, I could text my son's the combo from work (without coming home) when they forgot it), and I could periodically change it when I felt it was compromised. I also could decided how long and/or complex I wanted it. If I thought my ex had it, I could change it as well. A lot simpler and less total cost of ownership.
另一方面,数字锁虽然可能不是世界上最安全的数字锁,但我不担心丢失钥匙,可以在儿子忘记工作时发短信给儿子上班的组合(不用回家),我可以当我感到它受到损害时,请定期更改它。 我也可以决定要多长时间和/或复杂。 如果我认为我的前任有,也可以更改。 更简单,总拥有成本更低。
The key'ed lock is like PK. The numeric lock is like passwords. In the end, I can tell you, I am a lot safer with the numeric lock, because I choose my own destiny and can do so as dynamically as I want. And remember, the reality is, that is just one way into my house.
钥匙锁就像PK。 数字锁就像密码。 最后,我可以告诉您,使用数字锁会更安全,因为我可以选择自己的命运,并且可以根据需要动态地进行选择。 记住,现实是,那只是进入我家的一种方式。
生成您的SSH密钥 (Generating Your SSH Keys)
检查现有密钥 (Check for Existing Keys)
The first step is to check to see if you have any existing keys setup. To do this open up your terminal and type:
第一步是检查是否有任何现有的按键设置。 为此,请打开您的终端并输入:
cd ~/.ssh
ls -alOr, in one beautiful line:
或者,在一条漂亮的一行中:
ls -al ~/.sshIf you see id_rsa and id_rsa.pub, it means your computer already has a Public and Private Key setup. If it doesn't, you'll need to run this command:
如果看到id_rsa和id_rsa.pub ,则表明您的计算机已经具有公共和专用密钥设置。 如果没有,则需要运行以下命令:
ssh-keygen -t rsa -C "your-email-here"Then just press enter all the way through. We're skipping over creating a passphrase. If you want to learn more about this, you can head over to GitHub. They have great explanations of this.
然后只需完全按Enter键即可。 我们跳过了创建密码的过程。 如果您想了解更多有关此的信息,可以转到GitHub。 他们对此有很好的解释 。
That's it! Now if you run:
而已! 现在,如果您运行:
ls -al ~/.sshYou'll see that you have both a id_rsa and id_rsa.pub file now. You'll most likely never touch the Private Key (id_rsa). Then, made obvious by the name, id_rsa.pub is your machine's Public Key which you can now put on other computers/servers you want to pair with.
您会看到现在同时拥有一个id_rsa和id_rsa.pub文件。 您极有可能永远不会触摸私钥( id_rsa )。 然后,以名称名显而易见, id_rsa.pub是计算机的公共密钥,您现在可以将其放置在要配对的其他计算机/服务器上。
确保远程服务器已准备好使用公钥 (Making Sure the Remote Server is Ready for Public Keys)
So now that we have our Private and Public Keys setup, we'll need to copy the Public Keys to the remote server we want to be paired with. There are multiple ways to do this, but, first, we need to make sure everything is setup on correctly on the remote server. SSH into the remote server and run this same command:
因此,既然我们已经有了“私钥”和“公钥”设置,就需要将“公钥”复制到要配对的远程服务器上。 有多种方法可以执行此操作,但是首先,我们需要确保在远程服务器上正确设置了所有内容。 SSH到远程服务器并运行以下相同命令:
ls -al ~/.sshIf there is no .ssh folder in your Home directory, you'll need to create one. You can either do this manually or just follow the steps from above on generating an SSH Key to automatically have it create the folder. Once it is created, you'll need to create an authorized_keys file. Here's how you can do it from the command line:
如果主目录中没有.ssh文件夹,则需要创建一个。 您可以手动执行此操作,也可以按照上面的步骤生成SSH密钥以自动创建它来创建文件夹。 创建完成后,您需要创建一个authorized_keys文件。 您可以通过命令行执行以下操作:
cd ~/.ssh
touch authorized_keysNow if you run ls -al ~/.ssh you'll see an authorized_keys file. The next step is to make sure that permissions are setup correctly for this file and its parent folder. Simply run these commands:
现在,如果您运行ls -al ~/.ssh您将看到一个authorized_keys文件。 下一步是确保为此文件及其父文件夹正确设置权限。 只需运行以下命令:
chmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keysOr, in one beautiful command:
或者,通过一个漂亮的命令:
chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keysThat's it! The remote server is now ready to have Public Keys put on it. Each line of the authorized_keys file is for a Public Key. So you'll paste your Public Key on Line 1. If you have another Public Key for a different user, paste it on Line 2 directly below it.
而已! 现在,远程服务器已准备就绪,可以在上面放置公钥了。 authorized_keys文件的每一行都是一个公共密钥。 因此,您将在第1行粘贴您的公钥。如果您有其他用户的另一个公钥,请将其粘贴在第2行的正下方。
将公钥复制到远程服务器 (Copying Public Keys to a Remote Server)
Copying and pasting to a remote server isn't always as easy as it sounds. Here's some methods on how to do it:
复制和粘贴到远程服务器并不总是听起来那么简单。 以下是一些操作方法:
老式复制和粘贴 (Old-Fashioned Copying and Pasting)
You could technically just open up the authorized_keys file with an editor that has remote access and paste the Public Key in the authorized_keys file. Alternatively, if you're using iTerm on a Mac, you could just copy-and-paste the key through the terminal using Vim, Vi, or Nano CLI editors.
从技术上讲,您可以使用具有远程访问权限的编辑器打开authorized_keys文件,然后将公共密钥粘贴到authorized_keys文件中。 另外,如果您在Mac上使用iTerm,则可以使用Vim,Vi或Nano CLI编辑器通过终端复制并粘贴密钥。
If you're on a Mac, you can run this command to copy your Public Key to your clipboard:
如果您使用的是Mac,则可以运行以下命令将“公共密钥”复制到剪贴板:
pbcopy < ~/.ssh/id_rsa.pub花式命令行方法 (Fancy Command Line Method)
If you're a beast and want to speed things up, you could always just utilize the UNIX cat command. This should come bundled on Macs, and if you're on a Windows machine, you'll probably need to run this from a console like this. Just enter this in your terminal (first changing user@host):
如果您是野兽并且想要加快速度,那么您始终可以仅使用UNIX cat命令。 这应该捆绑在Mac上,如果您使用的是Windows计算机,则可能需要从这样的控制台运行它 。 只需在您的终端中输入以下内容(首先更改user @ host):
cat ~/.ssh/id_rsa.pub | ssh user@host 'cat >> .ssh/authorized_keys'You should have been prompted with a password for the server, enter it, and you are done. Pretty simple and slick way of doing this. If you open up the authorized_keys file on the remote server, you'll now see your Public Key copied over there. You'll also notice that now when you SSH into your server you won't be prompted with a password at all. You've just successfully setup Public-Key authentication with SSH!
应该已经提示您输入服务器密码,输入密码,然后完成。 做到这一点非常简单而流畅。 如果您在远程服务器上打开authorized_keys文件,现在将看到公共密钥复制到那里。 您还会注意到,现在当您通过SSH进入服务器时,根本不会提示您输入密码。 您刚刚使用SSH成功设置了公共密钥身份验证!
创建SSH快捷方式 (Create SSH Shortcuts)
At this point, we've obtained a basic understanding of Key Pairing and Public-Private Key Authentication. We're also now able to SSH into our servers without a password. The last thing I would like to share is setting up SSH shortcuts.
至此,我们已经对密钥配对和公私钥认证有了基本的了解。 现在,我们无需密码即可通过SSH进入我们的服务器。 我要分享的最后一件事是设置SSH快捷方式。
If you're managing sites across many different servers, it's hard to keep track of all the different username/passwords, IP Address, and hostnames. There's a way to create shortcuts for all your sites. For example, you can create a shortcut that's as simple as this:
如果要在许多不同的服务器上管理站点,则很难跟踪所有不同的用户名/密码,IP地址和主机名。 有一种方法可以为您所有的站点创建快捷方式。 例如,您可以创建一个如下所示的快捷方式:
ssh scotchSetting this up is quite easy. On your local machine (your laptop), navigation to the ssh folder and create a file called config. Here's how to do it from the command line:
设置起来很容易。 在本地计算机(笔记本电脑)上,导航到ssh文件夹并创建一个名为config的文件。 这是从命令行执行的方法:
cd ~/.ssh
touch configNext, you can create shortcuts inside of this file. The format looks just like this:
接下来,您可以在此文件内创建快捷方式。 格式如下所示:
Host scotch
HostName scotch.io
User nick
Host example2
HostName example.com
User root
Host myclient
HostName 64.233.160.0
User user2ab1
Host myotherclient
HostName 64.233.160.0
User userxyz123
Port 56000
Host amazon
HostName ec2.amazon.com
User ec2-user123
Port 12345
IdentityFile /path/to/special/privatekey/amazon.pemNow, if can simply type these commands to SSH into those respective servers:
现在,如果可以简单地将以下命令键入SSH到相应的服务器中:
ssh scotch
ssh example2
ssh myclient
ssh myotherclient
ssh amazon结语 (Wrap-Up)
So that's it! I'm sure a lot of you already do this, but I know when this was first shown to me it was super helpful. Not all of us have a deep experience with servers and know this. This is only intended as a quick tutorial to get your foot in the door. So, I encourage you to read up on it and learn more than this article explains. I hope you enjoyed the read!
就是这样了! 我敢肯定你们中的很多人都已经这样做了,但是我知道当第一次向我展示这个功能时非常有帮助。 并非所有人都对服务器有深刻的经验,并且知道这一点。 这仅是作为入门的快速教程。 因此,我鼓励您阅读并学习更多的知识,而不是本文介绍的内容。 希望您喜欢阅读!
翻译自: https://scotch.io/tutorials/how-to-setup-ssh-public-key-authentication