领航杯部分Writeup
编码解码
V2VsY29tZXRvdGhlUGlsb3RDdXA=
签到题,base64解码一下得到:
WelcometothePilotCup
取证分析
给了一个pacp.pcap,CTF Wiki里面收录过这一道例题…
wireshark 打开发现全部为DNS协议,查询名为大量字符串xxxxx.skullseclabs.org
好像是BSides San Francisco CTF 2017原题,参考这篇文章:https://volatilevirus.home.blog/2018/12/30/bsidessf17-ctf-dnscap-write-up/
先用下面命令进行提取:
tshark -r pacp.pcap -T fields -e dns.qry.name > hex
然后用如下脚本得到flag.png:
from scapy.all import *
r = rdpcap("pacp.pcap")
a = ""
b = ""
c = ""
new = ""
f = open("flag.png","w")
for i in range (0,len(r)):
if r[i].haslayer(DNSQR) and not r[i].haslayer(DNSRR):
a = r[i][DNSQR].qname
b = a.replace(".skullseclabs.org.","")
b = b.replace(".","").decode("hex")[9:]
if b == c:
continue
c = b
if 6 < i <365:
new = new + b
f.write(new)
f.close()
直接打不开,用010 Editor看一下:

删掉上面选中的部分,再打开,得到flag:b91011fc
lsb
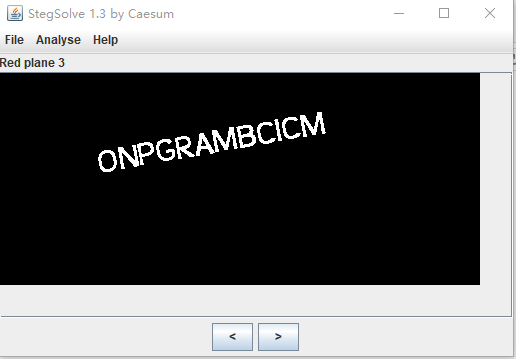
根据题目名字lsb,用Stegsolve打开,移位到下面位置得到flag:ONPGRAMBCICM
恢复与解密
题目描述:公安人员在犯罪分子的电脑中发现一些磁盘文件,但是发现关键信息已经被删除,现需要你对磁盘进行恢复,并对恢复出来的一些秘密文件里面的加密信息进行解密。 注意:通过strings获取到的yc4pl0fvjs2k1t7T为假flag,请尝试使用其他正确的做题方式获取flag。
所以可以判断这题为磁盘恢复,并且有假flag。
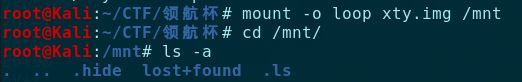
附件给的是一个xty.img,在kali下面命令进行挂载:
mount -o loop xty.img /mnt
发一下一个隐藏文件夹.hide,里面有一个secret.odg,打开得到如下内容:
好像没什么用,想到题目描述中的磁盘恢复,所以需要用到sstat 和 ext3grep这两个工具,先用下面命令查看相关信息:
fsstat xty.img

注意这里Root Directory: 2中的2是我们要用到的。
再用ext3grep工具,查看目录如下:
ext3grep --inode 2 xty.img
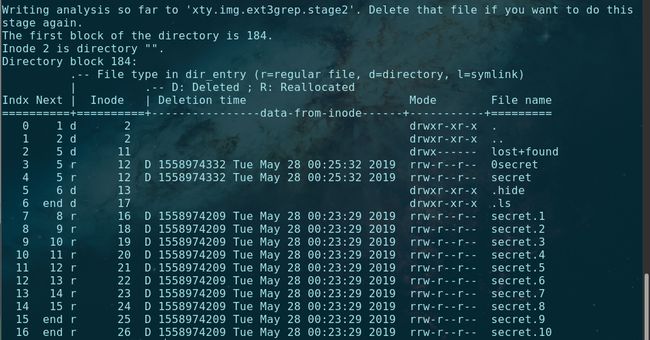
可以看到很多secret文件,实际上内容都一样,用下面命令将其恢复出来:
ext3grep --restore-file secret xty.img
aWdxNDs3NDFSOzFpa1I1MWliT08waWdx
base64一下得到:
igq4;741R;1ikR51ibOO0igq
异或解密脚本如下:
import string
c = "igq4;741R;1ikR51ibOO0igq"
for i in range(0,200):
p = ""
for j in range(len(c)):
p += chr(ord(c[j])^i)
print (p)
得到的唯一一个无特殊字符的即为flag:jdr78472Q82jhQ62jaLL3jdr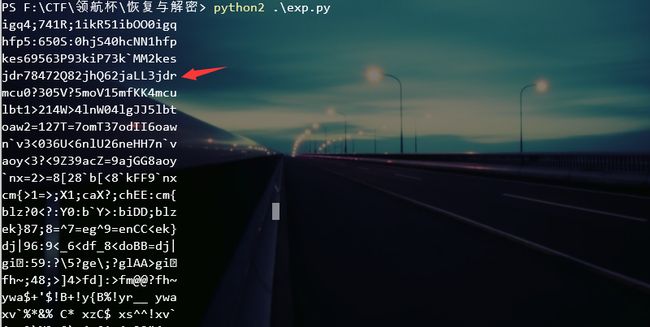
文件提取
给了一个flag.exe,strings一下可以看到是图片转base64后的字符串:

随便找个在线网站转回图片如下:

然后strings一下这个图片得到flag:flag{068EEF6A7BAD3FDF}

forensics
一开始分析了好久这个图片,但是无果…然后对整个docx文档foremost提取一下,得到flag:360HA360

OldCypher-Easy
给了密文如下:
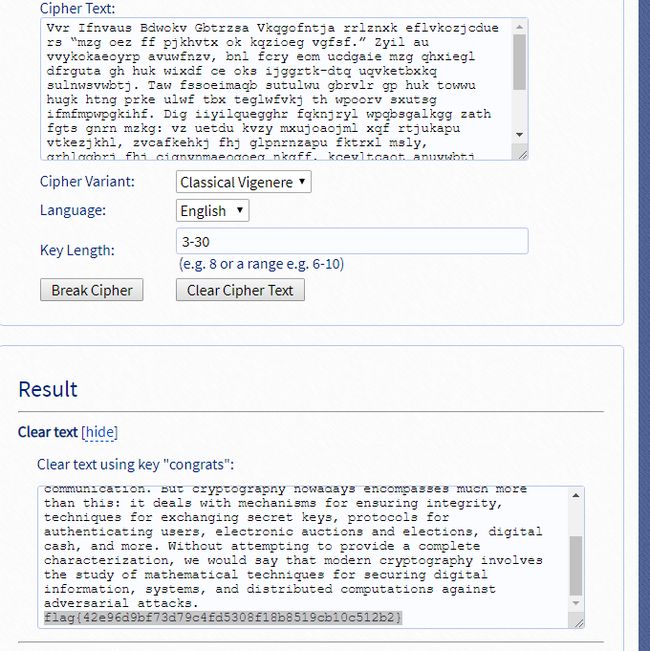
Vvr Ifnvaus Bdwokv Gbtrzsa Vkqgofntja rrlznxk eflvkozjcdue rs “mzg oez ff pjkhvtx ok kqzioeg vgfsf.” Zyil au vvykokaeoyrp avuwfnzv, bnl fcry eom ucdgaie mzg qhxiegl dfrguta gh huk wixdf ce oks ijggrtk-dtq uqvketbxkq sulnwsvwbtj. Taw fssoeimaqb sutulwu gbrvlr gp huk towwu hugk htng prke ulwf tbx teglwfvkj th wpoorv sxutsg ifmfmpwpgkihf. Dig iiyilquegghr fqknjryl wpqbsgalkgg zath fgts gnrn mzkg: vz uetdu kvzy mxujoaojml xqf rtjukapu vtkezjkhl, zvcafkehkj fhj glpnrnzapu fktrxl msly, grhlqqbrj fhj cignvnmaeogoeg nkgff, kcevltcaot anuvwbtj agv gzrikihfu, rvmzttd eofn, rnw eqfr. Cztagwh nzkefhvwam ko ijqjvjv a vgodykke vzcfnikekabogofn, pw ychru stq vvnz dowwtb pxppmgifnvyy bfxcybvs mzg ggauy hx oognvmtlkqnr kevzpwdavs ygt grilrbfi rvmzttd kbsuimtlkca, ypsmwog, ntu dbkvfvhltxv eczvlttlkcay rgtapgg guvxjuoeorl tlvopqj. fesi{42s96q9hw73d79v4xf5308t18o8519is10c512u2}
最后一串明显像flag的格式,在这个网站进行维吉尼亚解密:https://www.guballa.de/vigenere-solver
得到flag:flag{42e96d9bf73d79c4fd5308f18b8519cb10c512b2}
MasterofZip-Middle
level1
给了一个压缩包,和一个Readme.md内容如下:
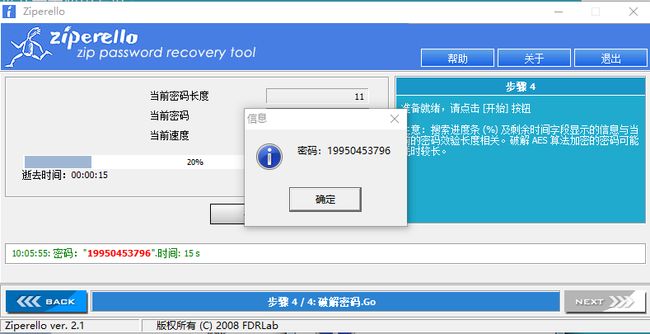
小明喜欢用自己的手机号来加密zip,我们通过社工只查到了他手机号的前三位为199,你能解开这个压缩包吗?(手机号为伪造手机号,请不要试图拨打或社工)
于是爆破199开头的手机号,得到密码:19950453796
level2
第一层解压后得到一个压缩包和一个Readme.txt,内容不重要,但是看到level2.zip里面也有一个Readme.txt,所以尝试明文攻击,成功恢复密钥并解压:

level3
第二层解压后,只给了一个压缩包,于是尝试伪加密:

将箭头位置修该为0,成功解压,得到下面这张图片:

然后修改发图片高度:

得到flag:flag{4537ec3bd52ba2b41c4a780db841efc3ddccc4a4}

数据包分析-Easy
题目给了一个http3.pcap,进行流量分析,根据题目描述,直接导出HTTP对象列表,发现flag.php:

导出后,即可在里面看到flag:flag{3eyufhnj87}

EasyRSA
题目给了加密脚本如下:
from Crypto.Util.number import getPrime, inverse
flag = 'flag{a-z0-9}'
nbits = 2048
p = getPrime(nbits / 2)
q = getPrime(nbits / 2)
assert p != q
N = p * q
e = 0x10001
phiN = (p - 1) * (q - 1)
d = inverse(e, phiN)
phint = d % (p - 1)
qhint = q % (p - 1)
def str2int(s):
return int(s.encode('hex'), 16)
with open('pubkey.txt', 'w') as f:
f.write(str(e) + '\n')
f.write(str(N) + '\n')
f.write(str(phint) + '\n')
f.write(str(qhint) + '\n')
plain = str2int(flag)
c = pow(plain, e, N)
with open('cipher.txt', 'w') as f:
f.write(hex(c))
但实际上没什么用,只是告诉了我们pubkey.txt里面分别对应的内容,即:
e = 65537
N = 16969752165509132627630266968748854330340701692125427619559836488350298234735571480353078614975580378467355952333755313935516513773552163392952656321490268452556604858966899956242107008410558657924344295651939297328007932245741660910510032969527598266270511004857674534802203387399678231880894252328431133224653544948661283777645985028207609526654816645155558915197745062569124587412378716049814040670665079480055644873470756602993387261939566958806296599782943460141582045150971031211218617091283284118573714029266331227327398724265170352646794068702789645980810005549376399535110820052472419846801809110186557162127
phint = 1781625775291028870269685257521108090329543012728705467782546913951537642623621769246441122189948671374990946405164459867410646825591310622618379116284293794090970292165263334749393009999335413089903796624326168039618287078192646490488534062803960418790874890435529393047389228718835244370645215187358081805
qhint = 10450978538445496868237560522155647855468044038637044818500580506745232482415364474390893285539835615564332910332708101539048528242011762736342572650763270501265440674647489375438852377280494520168349154604800218665628586180057648386859933274414030182106920793492451577530884172876623074281199949317487086975
而这里的phint和qhint实际上就是常说的dp和dq。
还给了密文如下:
0x7b5d1ea2d92df27239817ce8d885e1f66569dd41e075efc13d09dd1df673a8fba68ec7487c1552028e9eb9ba6663983f96d01925bbdfd18398e44f970257fa0f96b6ec915d05d637ebb4c8f4c56c44b2bb46bd1afe5a67acd640585dccf1681155308c0663cb57fccdc10c097c454dafdd2a96ccd08e9a2a8b0a9727bbe9945e579b0652d1c1d826305f0dd716cfb647cadb8eca1a0286dfb938b60b89981403d4faa6df54cfac0fa4699c97aeba6e82ab575cd6aa4421018cf9b404836c02b5301dbc475a0bcc5eef86bcbeb89a73355dbeb80e7b4d23c7a39f32c6b6138125c73892633f46b0bf1114aa67f09e1d394dfa4020e318f7d8004b84fc835b1ee9L
所以这题我们有c、e、n、dp、dq,足够解出明文了。
参考这篇文章:https://skysec.top/2018/08/24/RSA%E4%B9%8B%E6%8B%92%E7%BB%9D%E5%A5%97%E8%B7%AF(1)/
最终解密脚本如下:
import gmpy2
import libnum
e = 65537
n = 16969752165509132627630266968748854330340701692125427619559836488350298234735571480353078614975580378467355952333755313935516513773552163392952656321490268452556604858966899956242107008410558657924344295651939297328007932245741660910510032969527598266270511004857674534802203387399678231880894252328431133224653544948661283777645985028207609526654816645155558915197745062569124587412378716049814040670665079480055644873470756602993387261939566958806296599782943460141582045150971031211218617091283284118573714029266331227327398724265170352646794068702789645980810005549376399535110820052472419846801809110186557162127
dp = 1781625775291028870269685257521108090329543012728705467782546913951537642623621769246441122189948671374990946405164459867410646825591310622618379116284293794090970292165263334749393009999335413089903796624326168039618287078192646490488534062803960418790874890435529393047389228718835244370645215187358081805
c = "0x7b5d1ea2d92df27239817ce8d885e1f66569dd41e075efc13d09dd1df673a8fba68ec7487c1552028e9eb9ba6663983f96d01925bbdfd18398e44f970257fa0f96b6ec915d05d637ebb4c8f4c56c44b2bb46bd1afe5a67acd640585dccf1681155308c0663cb57fccdc10c097c454dafdd2a96ccd08e9a2a8b0a9727bbe9945e579b0652d1c1d826305f0dd716cfb647cadb8eca1a0286dfb938b60b89981403d4faa6df54cfac0fa4699c97aeba6e82ab575cd6aa4421018cf9b404836c02b5301dbc475a0bcc5eef86bcbeb89a73355dbeb80e7b4d23c7a39f32c6b6138125c73892633f46b0bf1114aa67f09e1d394dfa4020e318f7d8004b84fc835b1ee9L"
c = int(c[:-1], 16)
for i in range(1,65538):
if (dp*e-1)%i == 0:
if n%(((dp*e-1)/i)+1)==0:
p=((dp*e-1)/i)+1
q=n/(((dp*e-1)/i)+1)
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)%phi
print libnum.n2s(pow(c,d,n))
运行得到flag:flag{6b85823e6f121a7bb3407ff2e9f5f2f27efcc5a6}