【弄nèng - SearchGuard】应用篇 —— Windows下elasticsearch5.2.2 安装SearchGuard5.2.2
文章目录
-
- 1. Search Guard 简介
- 2. ES安装Search Guard插件
- 3. 配置TLS/SSL
- 4. 配置elasticsearch.yml
- 5. 测试
- 6. 配置searchguard权限
-
- 6.1 用户和密码修改
- 6.2 search-guard配置文件说明
- 7. es head插件使用Search Guard
- 8. Kibana使用Search Guard
- 9. Zipnkin使用Search Guard
- 10. Java中连接es使用Search Guard
- 11. 坑
-
- 11.1 禁用https
- 11.1 java TransportClient启动报错
- 12. 文献
- 项目推荐
本文是Windows 下elasticsearch 5.2.2 安装Search Guard5.2.2 教程,请知悉~
官方文档传送门
按照文档中配置似乎不起作用,好像是版本问题,不同的版本还是有区别的。
1. Search Guard 简介
Search Guard 是 Elasticsearch 的安全插件。它为后端系统(如LDAP或Kerberos)提供身份验证和授权,并向Elasticsearch添加审核日志记录和文档/字段级安全性。
Search Guard 所有基本安全功能都是免费的,并且内置在Search Guard中。 Search Guard 支持OpenSSL并与Kibana和logstash配合使用。
2. ES安装Search Guard插件
每个节点都要安装
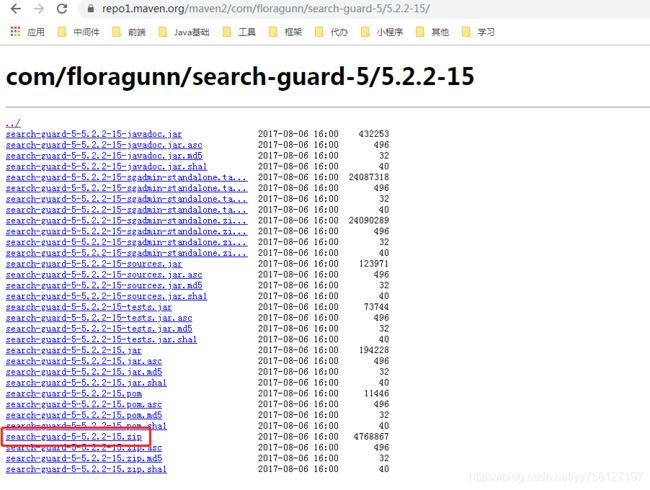
下载地址:传送门
在以上链接中选择你要的版本,版本注意与elasticsearch对应,下载ZIP包,例如:
启动安装
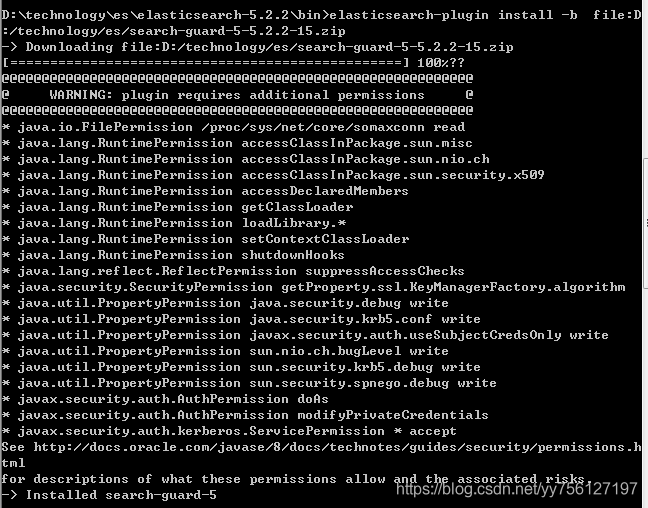
cmd进入elasticsearch-5.2.2\bin目录下执行:
elasticsearch-plugin install -b file:D:/technology/es/search-guard-5-5.2.2-15.zip
3. 配置TLS/SSL
在一个主节点安装就可以
我使用在线生成证书方式,适合开发测试,生产中不建议。
访问https://search-guard.com/tls-certificate-generator/ ,输入邮箱和公司名,所在国家等参数后证书会发送到邮箱中。
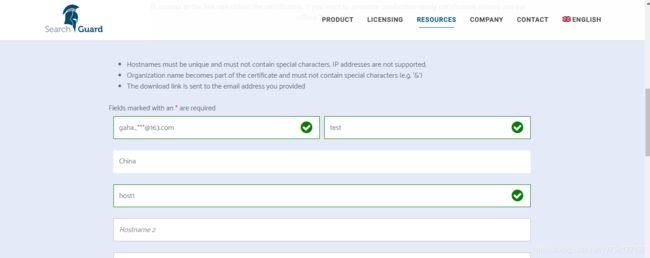
收到的邮件
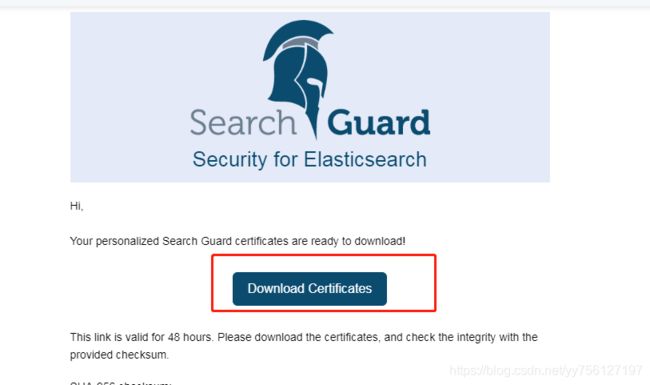
下载证书:
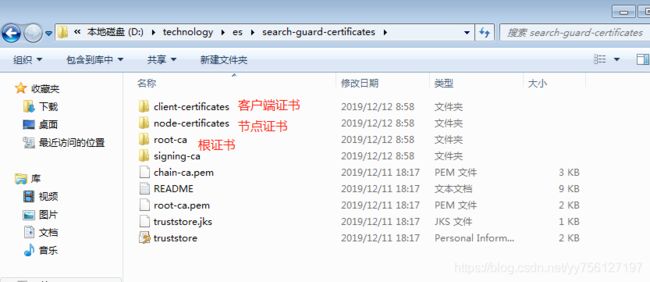
证书复制
- truststore.jks和CN=host1-keystore.jks 复制到es的config路径下。
- CN=sgadmin-keystore.jks和truststore.jks 复制到 plugins\search-guard-5\tools路径下
其他es节点一样,只是把CN=host1-keystore.jks换成对应的node证书
注意: CN=sgadmin-keystore.jks和truststore.jks 在 linux中放在sgconfig目录下,其实放在哪个目录下无所谓,sgadmin初始化时能读取到就行
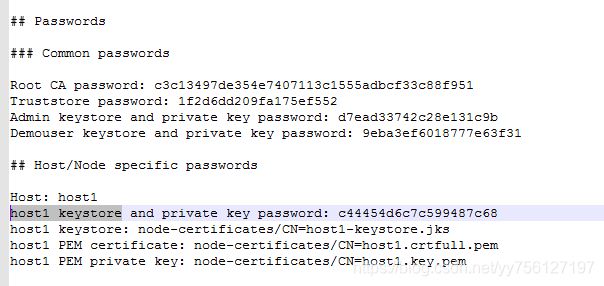
注意:证书相关密码在README文件中
4. 配置elasticsearch.yml
证书README.txt
ES配置
配置内容参照readme.txt
# head插件访问
http.cors.allow-headers: Authorization,X-Requested-With,Content-Length,Content-Type
# ssl
searchguard.ssl.transport.keystore_filepath: CN=host1-keystore.jks
# 对应证书README文件中host1 keystore
searchguard.ssl.transport.keystore_password: c44454d6c7c599487c68
searchguard.ssl.transport.truststore_filepath: truststore.jks
# 对应证书README文件中Truststore password
searchguard.ssl.transport.truststore_password: 1f2d6dd209fa175ef552
searchguard.ssl.transport.enforce_hostname_verification: false
# http,禁用https
searchguard.ssl.http.enabled: false
searchguard.ssl.http.keystore_filepath: CN=host1-keystore.jks
# 对应证书README文件中host1 keystore
searchguard.ssl.http.keystore_password: c44454d6c7c599487c68
searchguard.ssl.http.truststore_filepath: truststore.jks
# 对应证书README文件中Truststore password
searchguard.ssl.http.truststore_password: 1f2d6dd209fa175ef552
# dn
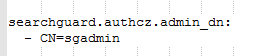
searchguard.authcz.admin_dn:
- CN=sgadmin
注意:上述配置中的dn一定要跟签名中的一致,在README.txt中
5. 测试
初始化
cmd进入cd plugins/search-guard-5/tools/
执行
sgadmin -ts truststore.jks -tspass 1f2d6dd209fa175ef552 -ks CN=sgadmin-keystore.jks -kspass d7ead33742c28e131c9b -nhnv -cn my-application -cd ../sgconfig/ --diagnose
- -cn: 是集群名,换成你自己的
- -h: 主节点IP
- -ts: truststore.jks所在路径
- -tspass:truststore密码
- -ks:keystore.jks所在路径
- -kspass:keystore密码
- –diagnose 打印日志(可以不加)
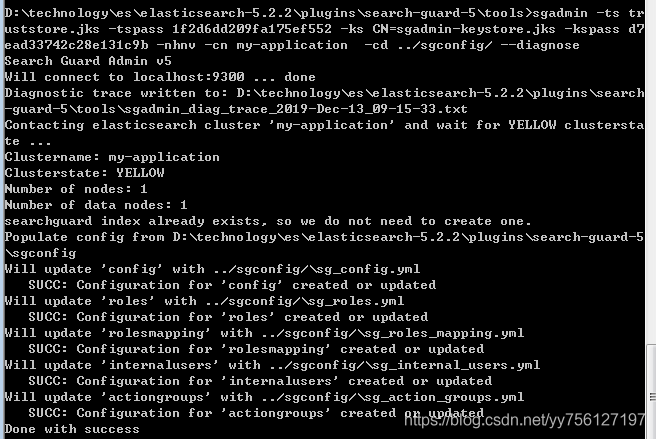
显示如上表示成功,之后每一次修改searchguard配置都需要执行一次。
注意:一定要在es运行中执行初始化,另开一个窗口执行
再次访问localhost:9200,输入admin/admin后显示如下:

6. 配置searchguard权限
6.1 用户和密码修改
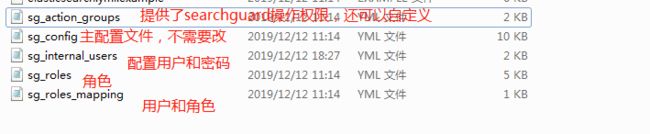
searchguard配置有内部用户数据库。如果我们没有任何外部认证系统(如LDAP或Active Directory),则可以使用此用户数据库。用户、密码hash和角色等存储在集群内部searchguard配置索引中。内部用户配置文件为:sg_internal_users.yml
在\elasticsearch-5.2.2\plugins\search-guard-5\sgconfig路径下
格式:
<username>:
hash: <hashed password>
roles:
- <rolename>
- <rolename>
事例:
# This is the internal user database
# The hash value is a bcrypt hash and can be generated with plugin/tools/hash.sh
admin:
hash: $2a$12$VcCDgh2NDk07JGN0rjGbM.Ad41qVR/YFJcgHp0UGns5JDymv..TOG
#password is: admin
logstash:
hash: $2a$12$u1ShR4l4uBS3Uv59Pa2y5.1uQuZBrZtmNfqB3iM/.jL0XoV9sghS2
#password is: logstash
kibanaserver:
hash: $2a$12$4AcgAt3xwOWadA5s5blL6ev39OXDNhmOesEoo33eZtrq2N0YrU3H.
#password is: kibanaserver
kibanaro:
hash: $2a$12$JJSXNfTowz7Uu5ttXfeYpeYE0arACvcwlPBStB1F.MI7f0U9Z4DGC
#password is: kibanaro
readall:
hash: $2a$12$ae4ycwzwvLtZxwZ82RmiEunBbIPiAmGZduBAjKN0TXdwQFtCwARz2
#password is: readall
注意,用户名不能包含“.”
生成密码
使用plugins/search-guard-5/tools/hash.sh生成密码hash值,格式如下:
./hash.sh -p passwd
事例:
$ ./hash.bat -p yang
$2a$12$7U6genGjgZBe9Ei2z8tEiupifHo9pDFpOuw6tuMoEgAXWlMnL17cW
生成后替换或者添加到sg_internal_users.yml中
注意:修改用户密码后需要使用sgadmin重新初始化searchguard, 如上文中初始化语句
参考:https://docs.search-guard.com/latest/internal-users-database
6.2 search-guard配置文件说明
7. es head插件使用Search Guard
es配置文件中加上
http.cors.allow-headers: Authorization,X-Requested-With,Content-Length,Content-Type
注意:后面有个空格,上文中已加
访问http://localhost:9100/?auth_user=admin&auth_password=admin
8. Kibana使用Search Guard
kibana配置文件中添加
elasticsearch.username: "admin"
elasticsearch.password: "admin"
9. Zipnkin使用Search Guard
启动命令添加ES_USERNAME和ES_PASSWORD:
STORAGE_TYPE=elasticsearch ES_HOSTS=localhost:9200 ES_USERNAME=admin ES_PASSWORD=admin java -jar zipkin-server-2.12.9-exec.jar
zipkin更多使用方式参见https://github.com/openzipkin/zipkin-dependencies
10. Java中连接es使用Search Guard
<dependency>
<groupId>com.floragunngroupId>
<artifactId>search-guard-sslartifactId>
<version>5.2.2-22version>
<scope>providedscope>
dependency>
3.client
import com.floragunn.searchguard.ssl.SearchGuardSSLPlugin;
import com.floragunn.searchguard.ssl.util.SSLConfigConstants;
import lombok.extern.slf4j.Slf4j;
import org.elasticsearch.client.transport.TransportClient;
import org.elasticsearch.common.network.InetAddresses;
import org.elasticsearch.common.settings.Settings;
import org.elasticsearch.common.transport.InetSocketTransportAddress;
import org.elasticsearch.common.transport.TransportAddress;
import org.elasticsearch.transport.client.PreBuiltTransportClient;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
/**
* @author 司马缸砸缸了
* @date 2019/12/13 17:36
* @description
*/
@Slf4j
@Configuration
public class EsConfig {
@Value("${es.cluster-name}")
private String clusterName;
@Value("${es.ip}")
private String ips;
@Value("${es.port}")
private String port;
@Bean("dataClient")
public TransportClient getTransPortClient() {
TransportClient client = null;
Settings settings = Settings.builder()
// 集群名, 如果你需要更改集群名(默认是elasticsearch)
.put("cluster.name", clusterName)
// 设置client.transport.sniff为true来使客户端去嗅探整个集群的状态,
// 把集群中其它机器的ip地址加到客户端中。这样做的好处是,一般你不用手动
// 设置集群里所有集群的ip到连接客户端,它会自动帮你添加,并且自动发现新加入集群的机器。
.put("client.transport.sniff", false)
// searchguard相关
.put("path.home", ".")
.put(SSLConfigConstants.SEARCHGUARD_SSL_HTTP_ENABLED, true)
.put(SSLConfigConstants.SEARCHGUARD_SSL_TRANSPORT_ENFORCE_HOSTNAME_VERIFICATION, false)
.put(SSLConfigConstants.SEARCHGUARD_SSL_TRANSPORT_KEYSTORE_FILEPATH, "../src/main/resources/config/CN=sgadmin-keystore.jks")
.put(SSLConfigConstants.SEARCHGUARD_SSL_TRANSPORT_TRUSTSTORE_FILEPATH, "../src/main/resources/config/truststore.jks")
.put(SSLConfigConstants.SEARCHGUARD_SSL_TRANSPORT_KEYSTORE_PASSWORD, "d7ead33742c28e131c9b")
.put( SSLConfigConstants.SEARCHGUARD_SSL_TRANSPORT_TRUSTSTORE_PASSWORD, "1f2d6dd209fa175ef552")
.build();
String[] ipArray = ips.split(",");
try {
client = new PreBuiltTransportClient(settings, SearchGuardSSLPlugin.class);
for (String ip : ipArray) {
//添加集群IP列表
TransportAddress transportAddress = new InetSocketTransportAddress(InetAddresses.forString(ip), Integer.parseInt(port));
client.addTransportAddresses(transportAddress);
}
} catch (Exception e) {
log.error("create es client error:{}", e);
if (client != null) {
client.close();
}
}
return client;
}
}
11. 坑
11.1 禁用https
searchguard.ssl.http.enabled: false
11.1 java TransportClient启动报错
javax.net.ssl.SSLException: Received fatal alert: certificate_unknown
at sun.security.ssl.Alerts.getSSLException(Alerts.java:208) ~[?:?]
at sun.security.ssl.SSLEngineImpl.fatal(SSLEngineImpl.java:1666) ~[?:?]
at sun.security.ssl.SSLEngineImpl.fatal(SSLEngineImpl.java:1634) ~[?:?]
at sun.security.ssl.SSLEngineImpl.recvAlert(SSLEngineImpl.java:1800) ~[?:?]
at sun.security.ssl.SSLEngineImpl.readRecord(SSLEngineImpl.java:1083) ~[?:?]
at sun.security.ssl.SSLEngineImpl.readNetRecord(SSLEngineImpl.java:907) ~[?:?]
at sun.security.ssl.SSLEngineImpl.unwrap(SSLEngineImpl.java:781) ~[?:?]
at javax.net.ssl.SSLEngine.unwrap(SSLEngine.java:624) ~[?:1.8.0_102]
at io.netty.handler.ssl.SslHandler$SslEngineType$2.unwrap(SslHandler.java:218) ~[netty-handler-4.1.7.Final.jar:4.1.7.Final]
at io.netty.handler.ssl.SslHandler.unwrap(SslHandler.java:1028) ~[netty-handler-4.1.7.Final.jar:4.1.7.Final]
at io.netty.handler.ssl.SslHandler.decode(SslHandler.java:950) ~[netty-handler-4.1.7.Final.jar:4.1.7.Final]
at io.netty.handler.codec.ByteToMessageDecoder.callDecode(ByteToMessageDecoder.java:411) ~[netty-codec-4.1.7.Final.jar:4.1.7.Final]
at io.netty.handler.codec.ByteToMessageDecoder.channelRead(ByteToMessageDecoder.java:248) ~[netty-codec-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:363) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:349) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.AbstractChannelHandlerContext.fireChannelRead(AbstractChannelHandlerContext.java:341) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.DefaultChannelPipeline$HeadContext.channelRead(DefaultChannelPipeline.java:1334) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:363) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:349) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.DefaultChannelPipeline.fireChannelRead(DefaultChannelPipeline.java:926) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.nio.AbstractNioByteChannel$NioByteUnsafe.read(AbstractNioByteChannel.java:129) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.nio.NioEventLoop.processSelectedKey(NioEventLoop.java:642) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.nio.NioEventLoop.processSelectedKeysPlain(NioEventLoop.java:527) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.nio.NioEventLoop.processSelectedKeys(NioEventLoop.java:481) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.channel.nio.NioEventLoop.run(NioEventLoop.java:441) [netty-transport-4.1.7.Final.jar:4.1.7.Final]
at io.netty.util.concurrent.SingleThreadEventExecutor$5.run(SingleThreadEventExecutor.java:858) [netty-common-4.1.7.Final.jar:4.1.7.Final]
at java.lang.Thread.run(Thread.java:745) [?:1.8.0_102]
解决办法:
添加如下Setting配置
.put(SSLConfigConstants.SEARCHGUARD_SSL_HTTP_ENABLED, true)
.put(SSLConfigConstants.SEARCHGUARD_SSL_TRANSPORT_ENFORCE_HOSTNAME_VERIFICATION, false)
12. 文献
官方文档 https://search-guard.com/searchguard-elasicsearch-transport-clients/
linux下安装参考 https://www.cnblogs.com/autohome7390/p/7452476.html https://www.cnblogs.com/Orgliny/p/6168986.html
项目推荐
IT-CLOUD :IT服务管理平台,集成基础服务,中间件服务,监控告警服务等。
IT-CLOUD-ACTIVITI6 :Activiti教程源码。博文在本CSDN Activiti系列中。
IT-CLOUD-ELASTICSEARCH :elasticsearch教程源码。博文在本CSDN elasticsearch系列中。开源项目,持续更新中,喜欢请 Star~