Introduction
There are a number of command line options available to configure Window Server 2008 over the network. For example, Windows Powershell, ServerManager.exe, or a telnet server. However, the tried and true method that has worked so well with just about every type of infrastructure device in use today (including Windows Server 2008, Cisco Routers, Linux servers, and more) is SSH. In this article, learn how to install a SSH Server in Windows Server 2008.
What is SSH?
SSH is the secure shell, a standard defined in RFC 4251. It is a network protocol that opens up a secure channel between two devices using TCP port 22. This channel can also be used for SFTP and SCP (secure FTP and secure copy, respectively). To make this work, you need a secure server on the system you are connecting to and a secure client on the client you are connecting from.
Keep in mind that SSH is completely interoperable between different platforms. For example, you could connect to a SSH server on a Cisco router from a Windows client, you could connect to a Linux server from a Cisco router, and you could connect to a Windows 2008 Server from a Linux client.
The only possible compatibility issue is that there are two versions of SSH, SSH version 1 and SSH version 2. You should make sure that the server and client support the same versions so that you know which version you are using when you connect. Usually, this version can be negotiated.
While none of the Windows operating systems come with a SSH Server or Client, they are very easy to install.
By having a SSH Server on your Windows 2008 Server, you can:
- Remotely access the command line of your Windows 2008 Server
- Control the Server over the network, even if you cannot access the GUI interface
- Remotely manage your Windows 2008 Server from any device that has a SSH Client
- Do all this over an encrypted connection that could even securely traverse the Internet
What SSH Server options are available for Windows 2008 Server?
There are a number of SSH Server options available for Windows Server 2008. Here are just some of the few that I ran across:
- SSH.com – Free non-commercial SSH Server
- SSH.com – SSH Tectia Client and Server (commercial)
- OpenSSH – see article on how to install openssh server in Vista (applies to Windows Server 2008)
- Van Dyke – vShell 3.0 Server (commercial)
- Free SSHd
- WinSSHd (commercial)
- Kpym Telnet/SSH Server
- copSSH for Windows (a modified build of OpenSSH)
- Sysax Multi-Server (SSH Server) for Windows
Once you have your SSH Server running, you will most likely need a SSH Client for Windows. Here are a couple of the most popular SSH Clients for Windows that I have found:
- PuTTY
- Van Dyke - SecureCRT (commercial)
How do I install FreeSSHd - SSH Server in Windows Server 2008?
Because the installation for Free SSHd is so simple as compared to others (especially as compared to OpenSSH in Windows), I have chosen to demonstrate how to install and use Free SSHd. Remember that FreeSSHd is totally free (as the name says) both for personal / non-commercial use but also for commercial use.
To start this process, I downloaded FreeSSHd.exe on my Windows Server 2008 system and ran the downloaded program. The graphical installation began.
I took all the defaults for the installation options and clicked Install to being the install.
When done, I opted not to run SSHd as a service but that may be what you want to do on your production server.
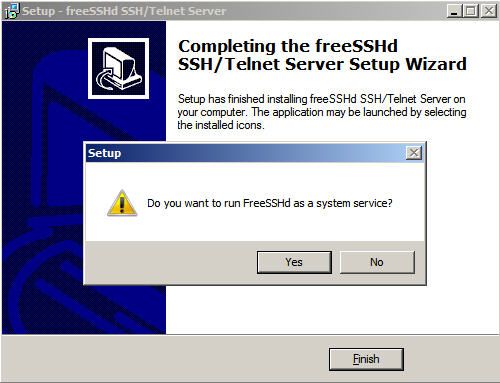
Figure 1: Do you want to run FreeSSHd as a service?
By running FreeSSHd as service, it would be available no matter if you were logged into the console or not. I also chose to create private keys for the SSH server.
Next, I ran the FreeSSHd shortcut on the desktop in order to configure and start the SSH server.

Figure 2: Running the FreeSSH Application
I could see that the SSHd server was already running.
The FreeSSHd application can offer the following:
- Both SSH Server and Telnet Server capabilities
- Options to run SSHd on only certain interfaces
- Multiple methods of authentication, including integrated NTLM authentication to Windows AD
- Multiple methods of encryption including AES 128, AES 256, 3DES, Blowfish, and more
- Options to bring up a secure tunnel upon connection
- Optional Secure FTP (sFTP) - for secure FTP, see the FreeFTPd website
- The ability to administer users and restrict access to secure shell, secure tunnel, or secure FTP
- Ability to allow access to only certain hosts or subnets
- Ability to log all connections and commands performed through FreeSSHd
- View currently connected users
- Update FreeSSHd automatically
For me to be able to login, I had to do two things:
- Add a new user account and allow SSH command line access
- Open an exception in my Windows Server 2008 Firewall
To add a new user, I went to the Users tab and clicked Add.
I opted to set up a login for my local Windows administrator account. I set the authorization to NTLM. That way, there was no local password in the FreeSSHd database and if the administrator password changes in the local Windows account database, you don’t have to change the password in the FreeSSHd account database.
I authorized this new administrator SSH user to log in with SSH only.
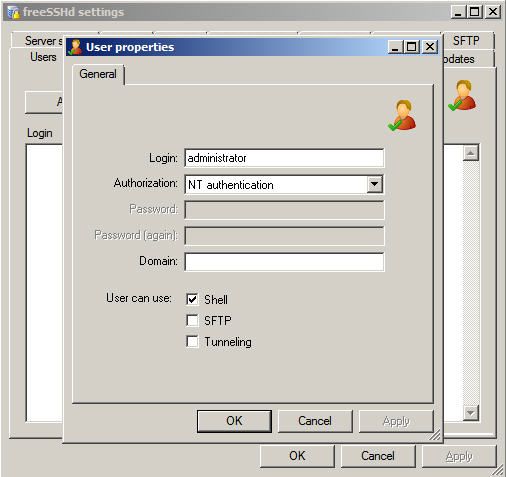
Figure 3: Adding a SSHd user account with NTLM authorization
Here are the results:
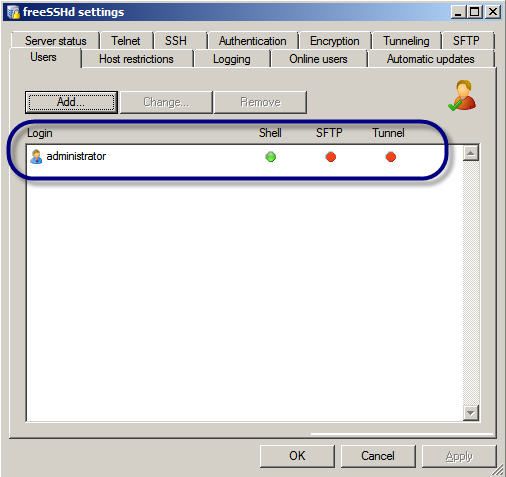
Figure 4: A new SSHd user account added
The second thing I had to do to allow me to login was to open an exception in the Windows Firewall. While I could disable the Windows Firewall completely instead of opening the ports, of course the most secure option is to leave the firewall up and allow for an exception for SSH – TCP port 22.
To do that, I went to Start -> Administrative Tools -> Windows Firewall with Advanced Security.
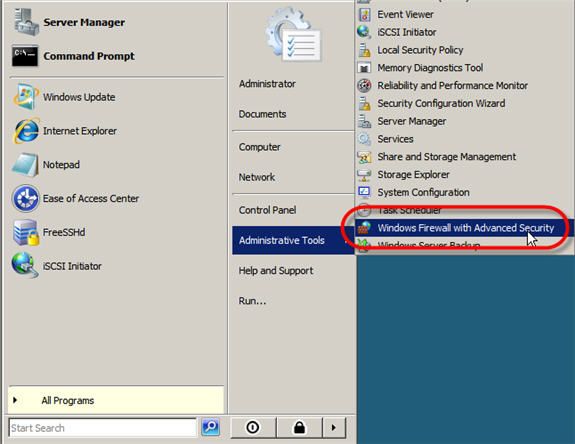
Figure 5: Opening Windows Firewall with Advanced Security
Next, I clicked on Inbound Rules, then on New Rule.
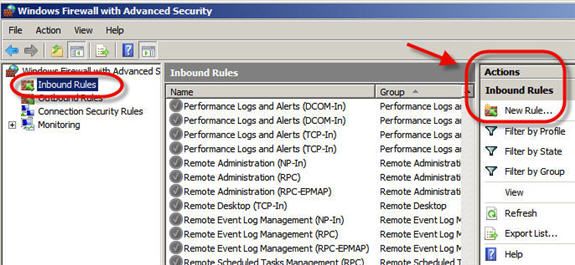
Figure 6: Adding a new Inbound Rule
Next, I chose to add a Port rule.
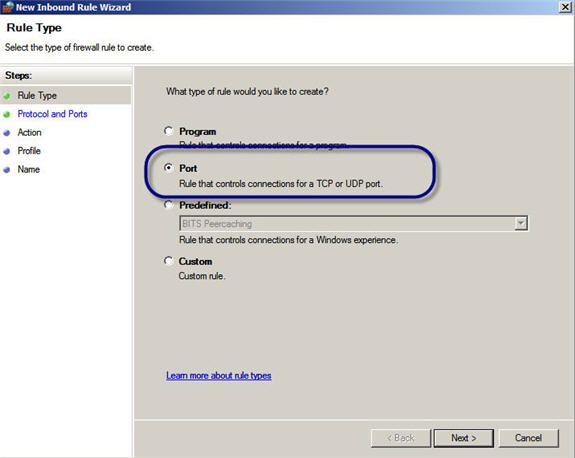
Figure 7: Choosing to add a Rule for a Port
I specified TCP port 22 only.
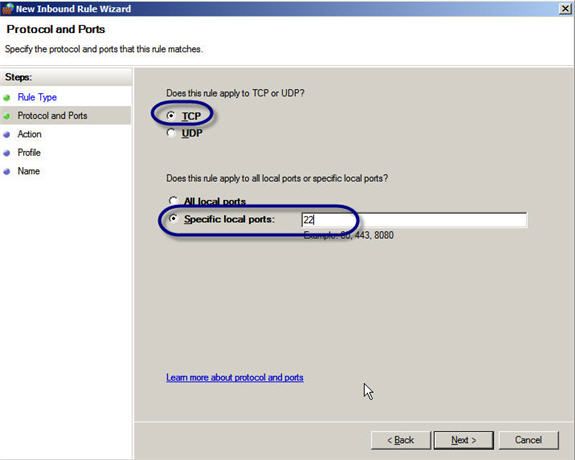
Figure 8: Specifying TCP port 22 only
Take the defaults to Allow the Connection, apply this to All domains, and give the rule a Name of your choice.
Test the Connection
To test the connection, I used SecureCRT from my Windows XP machine to the Windows Server 2008 server, via SSH.
To do this, I connected to the server via the IP address (or domain name). I chose to Accept the server’s certificate and save it.
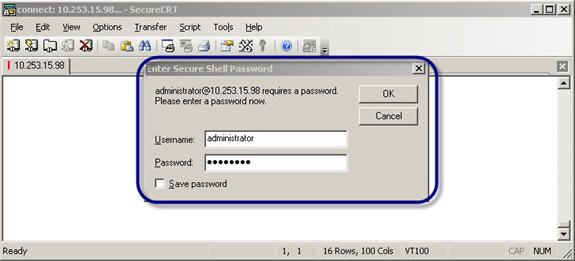
Figure 9: Connecting via SSH and logging in with your Windows username & password
I logged into the server using the administrator login and password.
And, success! I was able to access the server via SSH!
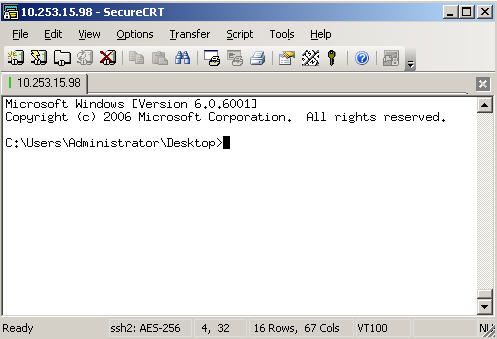
Figure 10: A successful connection to the Windows 2008 Server via SSH
In Summary
SSH is an excellent tool for Windows Server 2008 administrators to consider for remote server management. In this article, you learned how SSH can help you, the options available for SSH Server and SSH Client installations, and how to install one of those options, FreeSSHd.
(来自http://www.windowsnetworking.com/articles-tutorials/windows-server-2008/install-SSH-Server-Windows-Server-2008.html)