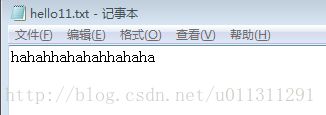
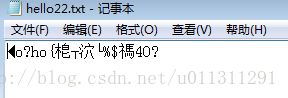
文件加密CryptEncrypt和导出密钥CryptExportKey学习笔记
刚刚接触C++,使用CryptEncrypt来对一个文件进行加密,代码都是MSDN上的,一开始使用起来比价困难,这里对代码解读和分享一下。
#include