Keeping the Network Safe!
1. Keeping the Network Safe
1.1 Network Device Security Measures
After the hacker gains access to the network, four types of threats may arise:
- Information theft
- Identity theft
- Data loss/manipulation
- Disruption of service
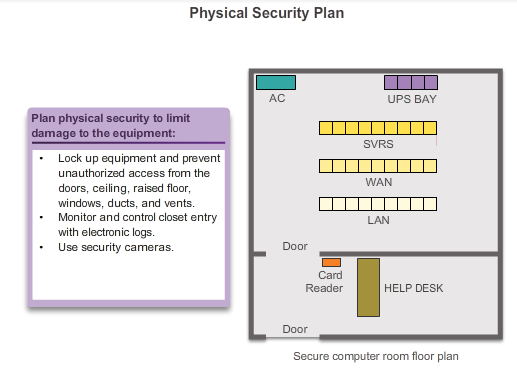
The four classes of physical threats are:
- Hardware threats - physical damage to servers, routers, switches, cabling plant, and workstations
- Environmental threats - temperature extremes (too hot or too cold) or humidity extremes (too wet or too dry)
- Electrical threats - voltage spikes, insufficient supply voltage (brownouts), unconditioned power (noise), and total power loss
- Maintenance threats - poor handling of key electrical components (electrostatic discharge), lack of critical spare parts, poor cabling, and poor labeling
vulnerabilities - technology:
- TCP/IP protocols weakness
- operating system weakness
- Network equipment weakness
vulnerabilities - Configuration
- unsecured user accounts
- system accounts with easily guessed passwords
- misconfigured internet services
- unsecured default settings within products
- misconfigured netwrok equipment
vulnerabilities - policy
- lack of written security policy
- politics
- lack of access control not applied
- software and hardware installation and changes do not follow policy
- disaster recovery plane is nonexistent
1.2 Vulnerabilities and Network Attacks
Viruses
A computer virus is a type of malware that propagates by inserting a copy of itself into and becoming part of another program. It spreads from one computer to another, leaving infections as it travels. Viruses can range in severity from causing mildly annoying effects to damaging data or software and causing denial-of-service (DoS) conditions. Almost all viruses are attached to an executable file, which means the virus may exist on a system but will not be active or able to spread until a user runs or opens the malicious host file or program. When the host code is executed, the viral code is executed as well. Normally, the host program keeps functioning after it is infected by the virus. However, some viruses overwrite other programs with copies of themselves, which destroys the host program altogether. Viruses spread when the software or document they are attached to is transferred from one computer to another using the network, a disk, file sharing, or infected e-mail attachments.
Worms
Computer worms are similar to viruses in that they replicate functional copies of themselves and can cause the same type of damage. In contrast to viruses, which require the spreading of an infected host file, worms are standalone software and do not require a host program or human help to propagate. To spread, worms either exploit a vulnerability on the target system or use some kind of social engineering to trick users into executing them. A worm enters a computer through a vulnerability in the system and takes advantage of file-transport or information-transport features on the system, allowing it to travel unaided.
Trojan Horses
A Trojan horse is another type of malware named after the wooden horse the Greeks used to infiltrate Troy. It is a harmful piece of software that looks legitimate. Users are typically tricked into loading and executing it on their systems. After it is activated, it can achieve any number of attacks on the host, from irritating the user (popping up windows or changing desktops) to damaging the host (deleting files, stealing data, or activating and spreading other malware, such as viruses). Trojan horses are also known to create back doors to give malicious users access to the system.
Password Atttack
attackers can implement password attacks using several different methods:
- brute-force attacks
- Trojan horse programs
- packet sniffers
Trust Exploitation
port redirection is a type of trust-exploitation attack that uses a compromised host to pass traffic through a firewall that would otherwise be dropped.
Man-in-the-middle
Dos Attack
ping of death
SYN Flood
DDoS
smurf attack
2.3 Mitigating Network
Authentication
Users and administrators must prove that they are who they say they are. Authentication can be established using username and password combinations, challenge and response questions, token cards, and other methods. For example: "I am user 'student'. I know the password to prove that I am user 'student'."
In a small network, local authentication is often used. With local authentication, each device maintains its own database of username/password combinations. However, when there are more than a few user accounts in a local device database, managing those user accounts becomes complex. Additionally, as the network grows and more devices are added to the network, local authentication becomes difficult to maintain and does not scale. For example, if there are 100 network devices, all user accounts must be added to all 100 devices.
For larger networks, a more scalable solution is external authentication. External authentication allows all users to be authenticated through an external network server. The two most popular options for external authentication of users are RADIUS and TACACS+:
- RADIUS is an open standard with low use of CPU resources and memory. It is used by a range of network devices, such as switches, routers, and wireless devices.
- TACACS+ is a security mechanism that enables modular authentication, authorization, and accounting services. It uses a TACACS+ daemon running on a security server.
Authorization
After the user is authenticated, authorization services determine which resources the user can access and which operations the user is allowed to perform. An example is, "User 'student' can access host serverXYZ using Telnet only."
Accounting
Accounting records what the user does, including what is accessed, the amount of time the resource is accessed, and any changes that were made. Accounting keeps track of how network resources are used. An example is, "User 'student' accessed host serverXYZ using Telnet for 15 minutes."