2021*CTF部分wp
一个废话连篇思路不清的wp,后续会完善
RE
stream
DIE查了一下elf文件,于是ubuntu下执行一下发现thread ‘main’ panicked at ‘open failed’, src/main.rs:10:19 note: run with RUST_BACKTRACE=1 environment variable to display a backtrace
rust没接触过的语言,安装rust环境很简单,rust是一种安全的语言
https://www.rust-lang.org/learn/get-started下载rustup-init.exe,输选项时输1,直接默认安装在c盘下,在把程序的安装环境加到path里面我的是C:\Users\Administrator.cargo\bin,然后查找rustc --version和cargo --version,全部成功,rust环境安装完后
编译一个helloworld吧
fn main(){
println!("Hello,world!");
}
切到路径下,rustc hello.rs编译出exe文件,拖入ida7.5,竟然反编译不了,恐怖
但这是个elf文件,所以linux下也要安装rust环境
https://blog.csdn.net/qq_41879343/article/details/104802548
找到这篇文章
curl https://sh.rustup.rs -sSf | sh
source $HOME/.cargo/env
安装好环境提示thread ‘main’ panicked at ‘open failed’, src/main.rs:10:19
动调解决,在主函数下断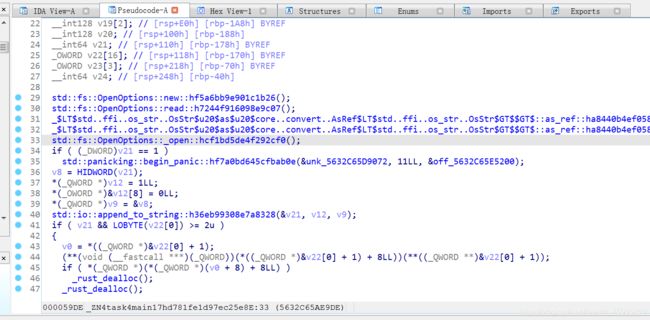
动调发现程序打开flag文件,而且判断flag文件里的内容是否是utf-8范围内,若是就继续向下执行
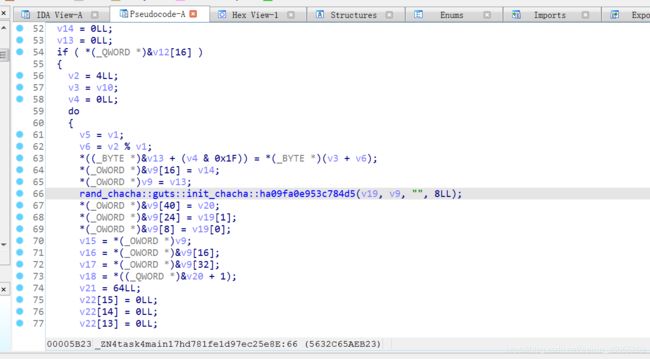
进入到一个rand_chacha,百度了一波发现是一种流密码,是随机数类的,init_chacha是在设置随机数种子
通过动调看函数的参数以及汇编,可以发现程序每次取i7 mod 46位置的值与某随机数异或,随机数是以目前所有取过的值为种子进行随机,所以可以爆破,从前往后加密字节所以我们可以使用popen枚举原文,依次枚举i7 mod 46位字节,然后读取output对比测试的第i*7 mod 46位字节是否和out_flag 一样,如果一样则代表该处字符是对的,可以继续向下枚举。
#!/usr/bin/python2
# -*- coding:utf-8 -*-
import os
import time
import subprocess
def excuteCommand(com):
ex = subprocess.Popen(com, stdout=subprocess.PIPE, shell=True)
out, err = ex.communicate()
status = ex.wait()
def genFile(flag):
f=open('flag','wb')
f.write(flag)
f.close()
def checkByte(index):
f1=open('output_flag','rb')
buf1=f1.read()
f1.close()
f2=open('output','rb')
buf2=f2.read()
f2.close()
if len(buf2)!=46:
return False
if buf1[index]==buf2[index]:
return True
return False
def toStr(arr):
bb=''
for i in range(len(arr)):
bb+=chr(arr[i])
return bb
index=[4,11,18,25,32,39,0,7,14,21,28,35,42,3,10,17,24,31,38,45,6,13,20,27,34,41,2,9,16,23,30,37,44,5,12,19,26,33,40,1,8,15,22,29,36,43]
result=[]
for i in range(46):
result.append(0x41)
def dfs(i):
if i>=46:
print(toStr(result))
pass
for x in range(0x20,0x7F+1,1):
result[index[i]]=x
sflag=toStr(result)
genFile(sflag)
excuteCommand("./a")
if checkByte(index[i])==True:
print(sflag)
dfs(i+1)
else:
continue
dfs(0)
#*ctf{EbXZCOD56vEHNSofFvRHG7XtgFJXcUXUGnaaaaaa}
1rep
elf文件,ubuntu可以运行,提示输入字符串
perl语言逆向,没接触过,简单百度了一下Perl 是一种优秀的脚本语言,linux内预装,我的ida分析的停不下来
ChineseGame
elf,有catflag,符号表丢失,随便找一个c++的sig加载
竟然有congratulation和sorry
从ida的flair工具去理解它是怎么识别出静态链接程序中的库函数的
C语言关于*号的比较
“*p”表示地址为p存储单元的baidu;“p”表示地址;“&a”表示取a的地址;a为变量。
int *p;//初始化指针,但是该指针无指向地址!如果直接使用会有问题。
int *p=&a;//初始化指针,该形式只在定义时正确,表示以p指针所指向地址的值为变量a的值。
p=&a;//表示指针p所指向的地址就是a的地址。即地址间的赋值。
*p=a;//表示指针p所指向地址的值是a变量。
通过搜索字符串cat flag定位到主函数

动调过程中发现v4地址反复被传递,找到最开始引用的地方,查看怎么生成的,

发现是链表结构,为了方便分析,我们定义两个结构体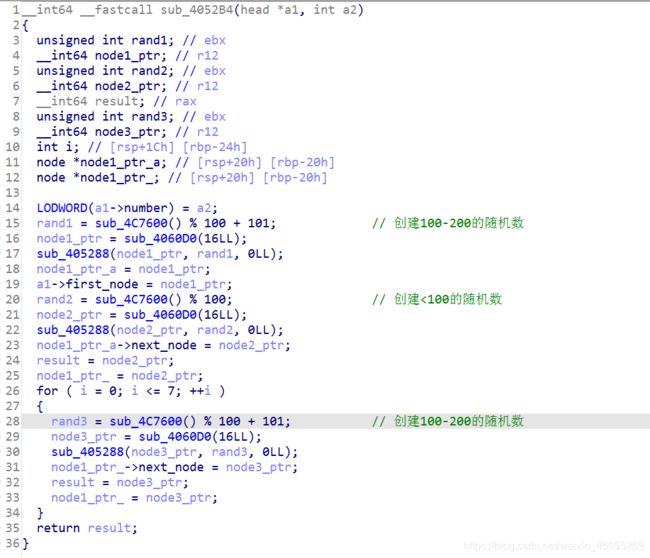
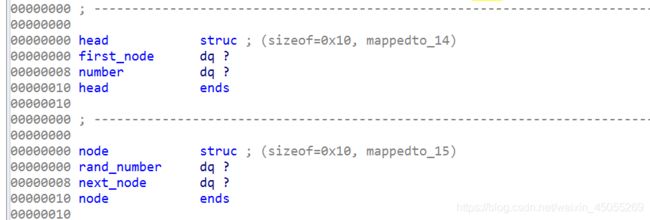
第一个结构体针对的是链表的第一个元素,存着第一个随机数的地址和链表元素的总个数,第二个结构体针对的是除第一个元素以外也就是后面的元素,第一个位置存的是当前的随机数,第二个位置存的是后面元素的地址。将结构体解析到相应的位置
接着分析main函数
发现只允许输入0和1
进入到两个函数分析
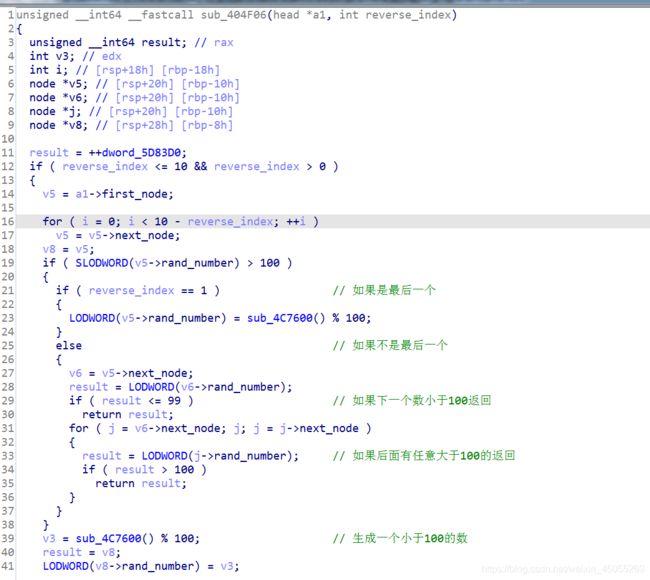
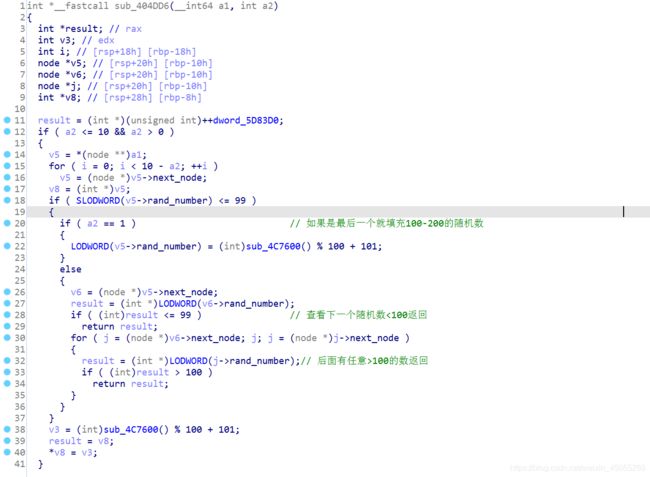
分析对0和对1的操作可知变化条件相同,但变换操作相反。
看眼check函数
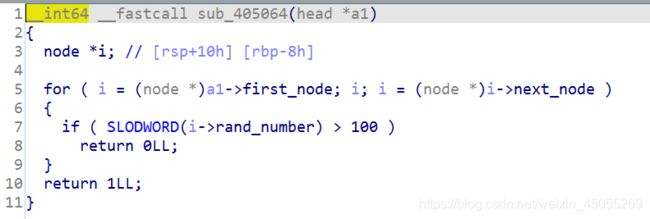
全部数都要<100,于是我们规定<100为true,>100为false。
所以整体逻辑是:有10个格子,初始化的时候第二个置为true(<100),其他条件置为false(>100),然后从输入接受0和1
的序列,当碰到0时满足某种条件,会把false变为true,碰到1时相反
发生变化的条件
- 当前选中是最后一个格子
- 当前格子的下一个格子是false且下一个格子之后的格子都是true
当所有的格子都变为true(<100)时就可cat flag
每次选中的格子由固定数组提供序列
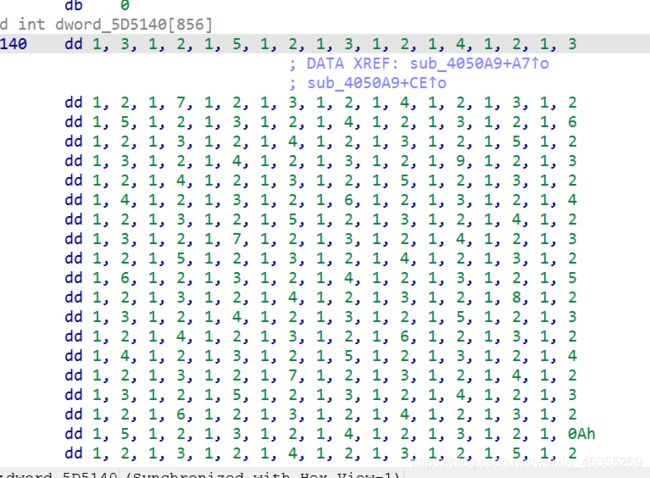
简单试玩了一下,固定数组的序列和让10个块变为true的顺序相同。所以写个脚本跑一下数组
array=[0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x9,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x8,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0xa,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x8,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x9,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x8,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x7,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x6,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x5,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x4,0x1,0x2,0x1,0x3,0x1,0x2,0x1,0x0,0x4058a0,0x0]
ans=[False]*10
ans[1]=True
cnt=0
for i in array[:-3]:
reverse_index=0-i
if not ans[reverse_index]:
print('0',end='')
else:
print('1',end='')
ans[reverse_index]=not ans[reverse_index]
cnt+=1
print(cnt)
nc连接上去,将0和1的那串输入得到flag
Favourite Architecture
好几个文件
单看逆向的话,文件在share里,qemu-riscv64和main,在ubuntu下执行./qemu-riscv64 main后,程序可以执行,发现关键字符串
Ghidra打开,搜索字符串找到关键函数,反编译不了,动调失败,安装qemu后程序可以运行(就是不用程序给的qemu-riscv64),gdb调但是调不了,所以就看Ghidra汇编,现学riscv64架构的汇编。
简单记录一下,异或+tea算法逆向
MISC
MineGame
mine就有地雷的意思,扫雷游戏
If you love reverse, you can try it, otherwise, you must finish it as quickly as possible.
游戏题,感觉应该不难,在下MATLAB Runtime,没装这个版本的matlab,根据提示装一下支持运行matlab程序的环境,需要安装对应版本的,题目提供的是MATLAB Runtime for R2020b 。
题目开始加载复旦6星的队标,然后打开一个扫雷,简单玩了一下,在规定时间内完不成游戏就退出,思路转变到扫雷游戏外挂制作
发现了这篇文章https://www.cnblogs.com/csnd/p/11785696.html
little tricks
给了一个二进制文件,winhex打开vhdxfileM头,
https://bbs.csdn.net/topics/397323056,电脑还是win7,尝试一下能不能恢复
下载了IsoBuster,打开之后找到一个已撤销的文件.bmp(位图文件),想办法保存下来,保存不下来
puzzle
一张图片常规的方法不行,只有两个神仙做出来了,但是就只有一张图片,从图片中恢复数据
chess
更狠,直接给了个地址个端口nc 52.249.253.150 8083
能执行一些系统调用

但是没有回显
CRYPTO
GuessKey
有三个随机的地方,第一个随机的地方可以输出,自然被破掉了,然后是p和q,p和q是生成key的二进制的0的位置,最好的情况是之间都是1,不是1有点难受,一个菜鸡妄图满足全是两个相邻的p和q
from random import randint
import os
from flag import flag
N=64
key=randint(0,2**N)
print key
key=bin(key)[2:].rjust(N,'0')
count=0
while True:
p=0
q=0
new_key=''
zeros=[0]
for j in range(len(key)):
if key[j]=='0':
zeros.append(j)
p=zeros[randint(0,len(zeros))-1]
q=zeros[randint(0,len(zeros))-1]
try:
mask=int(raw_input("mask:"))
except:
exit(0)
mask=bin(mask)[2:]
if p>q:
tmp=q
q=p
p=tmp
cnt=0
for j in range(0,N):
if j in range(p,q+1):
new_key+=str(int(mask[cnt])^int(key[j]))
else:
new_key+=key[j]
cnt+=1
cnt%=len(mask)
key=new_key
try:
guess=int(raw_input("guess:"))
except:
exit(0)
if guess==int(key,2):
count+=1
print 'Nice.'
else:
count=0
print 'Oops.'
if count>2:
print flag
GuessKey2
开始给了你key,现在连key也不给你,挺有意思,能看懂但是不会做
MyCurve
我的曲线
找到一个算法库的解释文档
http://codingdict.com/sources/py/Crypto.Util.number.html
https://www.mrskye.cn/amp/19找到了一些相关的关于Crypto库的说明
https://blog.csdn.net/weixin_34239592/article/details/88712750
关于算法的一些函数
https://segmentfault.com/a/1190000016851956
MyEnc
不难能读懂
