Kali渗透测试之端口扫描1——UDP、TCP、僵尸扫描、隐蔽扫描
端口扫描
每个服务器上面都会跑很多应用,每个应用都会侦听某些端口,通过侦听端口接收来自客户端或其他用户对应用程序的访问。所以在发现目标主机存活后,我们需要知道目标主机上都开放了那些端口,应用程序的漏洞都是通过端口体现出来的。后续的渗透测试如果能攻击进入一个操作系统的话,都是通过端口后面的应用程序的漏洞攻击进去的。所以说,二三四层主机发现只是为了准确发现活着的IP,确定攻击面;端口扫描发现开放的端口,确定攻击点。
- 端口对应网络服务及应用端程序
- 服务端程序的漏洞通过端口攻入
一、UDP端口扫描
基于端口的扫描,都是针对存活的主机而言。使用UDP端口扫描,如果目标主机不存活或者目标主机存活且端口开放,则目标系统不会有响应;如果端口关闭,则目标系统会响应端口不可达。
- 端口关闭:ICMP port unreachable
- 端口开放:没有回包
使用脚本的方式实现扫描多个端口
#!/usr/bin/python
#该脚本使用UDP协议扫描多个目标主机端口
from scapy.all import *
import time
import sys
if len( sys.argv ) !=4:
print "Example: ./UDP_scan.py 1.1.1.1 50 150"
sys.exit()
ip=sys.argv[1] //目标主机IP
start=int(sys.argv[2]) //起始端口
end=int(sys.argv[3]) //终止端口
for port in range(start,end):
a=sr1(IP(dst=ip)/UDP(dport=port),timeout=1,verbose=0) //udp的探测命令
time.sleep(1) //防止因扫描过快,造成误判
if a==None: //响应包为空,则目标主机端口开放,打印该端口
print port
else:
pass结果如下:
root@root:~# chmod +x UDP_scapy.py //赋予文件执行权限
root@root:~# ./UDP_scapy.py 192.168.247.129 1 100
53
88Nmap
- nmap -sU 192.168.247.129 //-sU:使用UDP协议
- nmap -sU 192.168.247.129 -p 53
- nmap -iL iplist.txt -sU -p 1-200 //指定扫描地址列表
root@kali:~# nmap -sU 192.168.247.129 //如果没有使用-p 指定扫描端口,默认扫描1000个常用端口;如果没有回应目标端口不可达,则该端口开放;否则,则端口关闭
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 17:32 CST
Nmap scan report for bogon (192.168.247.129)
Host is up (0.00096s latency).
Not shown: 991 closed ports
PORT STATE SERVICE
123/udp open|filtered ntp
137/udp open netbios-ns
138/udp open|filtered netbios-dgm
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
1032/udp open|filtered iad3
1033/udp open|filtered netinfo-local
1034/udp open|filtered activesync-notify
4500/udp open|filtered nat-t-ike
MAC Address: 00:0C:29:8F:74:74 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.47 secondsroot@kali:~# nmap -sU 192.168.247.129 -p 53 //-p 扫描指定端口
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-13 17:38 CST
Nmap scan report for bogon (192.168.247.129)
Host is up (0.00023s latency).
PORT STATE SERVICE
53/udp closed domain
MAC Address: 00:0C:29:8F:74:74 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds二、TCP端口扫描
- TCP是基于连接的协议
- TCP扫描可以分为隐蔽扫描、僵尸扫描、全连接扫描
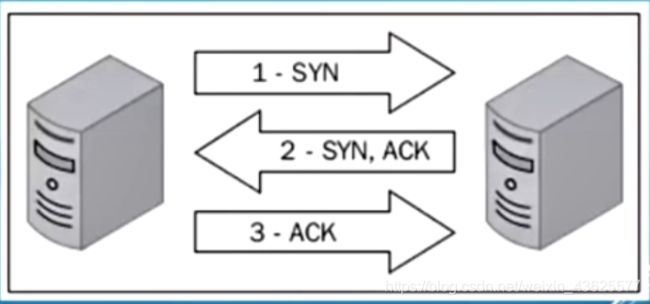
- 所有TCP扫描方式,都是基于三次握手的变化来判断目标端口的状态
三次握手过程:
1、隐蔽扫描——syn
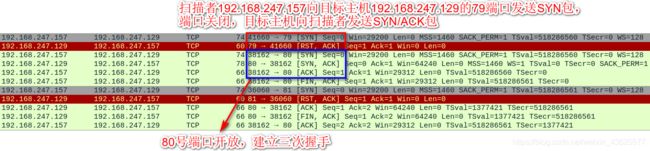
我给你发SYN包,只要你给我回SYN+ACK包,说明端口就是开放的;端口没开放,会回RST+ACK。不管目标主机会什么包,我都不会回ACK数据包,所以目标系统的应用层日志中不会有日志(因为没有建立完整的TCP连接),但是网络层会有一些迹象,所以该扫描方式较隐蔽。
- SYN——SYN|ACK——RST //目标端口开放
- SYN——RST|ACK //目标端口不开放
1)Scapy
root@kali:~# scapy
WARNING: No route found for IPv6 destination :: (no default route?)
INFO: Can't import python ecdsa lib. Disabled certificate manipulation tools
Welcome to Scapy (2.3.3)
#测试80端口是否开放
>>> a=sr1(IP(dst="192.168.247.130")/TCP(dport=80),timeout=1,verbose=0)
>>> a
>>
#测试66端口是否开放
>>> a=sr1(IP(dst="192.168.247.130")/TCP(dport=66),timeout=1,verbose=0)
>>> a
>>
Wireshark抓包分析:
使用脚本实现隐蔽扫描
#!/usr/bin/python
# -*- coding: utf-8 -*-
#该脚本用户实现扫描目标主机中开放的TCP端口
from scapy.all import*
import sys
if len( sys.argv ) !=4:
print "Example - ./syn_scan.py 1.1.1.1 1 100"
sys.exit()
ip = str(sys.argv[1])
start = int(sys.argv[2])
end = int(sys.argv[3])
for port in range(start,end+1):
a=sr1(IP(dst=ip)/TCP(dport=port),timeout=0.1,verbose=0)
if a ==None:
pass
else:
if int(a[TCP].flags)==18: #SYN+ACK值为18
print (port)
else:
pass执行结果如下:
root@kali:~# chmod +x SYN_scan.py
root@kali:~# ./SYN_scan.py 192.168.247.130 1 200
22
80
111
2)隐蔽端口扫描——nmap
- nmap 192.168.247.130 -p 1-100
- nmap -sS 192.168.247.130 -p 80,88,53,22,25
- nmap -sS -iL IP.txt -p 80,88,53,22 //扫描指定文件中的IP地址
root@kali:~# nmap 192.168.247.130 -p 1-100 //默认-sS,扫描端口1-100
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-20 21:30 CST
Nmap scan report for bogon (192.168.247.130)
Host is up (0.00083s latency).
Not shown: 98 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:74:BA:34 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.48 seconds
3)隐蔽端口扫描——hping3
- hping3 192.168.247.130 --scan 1-100 -S
- hping3 192.168.247.130 --scan 80,88,53,22 -S
- hping3 -c 100 -S --spoof 伪造的IP地址 -p ++1 源IP地址
root@kali:~# hping3 192.168.247.130 --scan 1-100 -S //-S:SYN包
Scanning 192.168.247.130 (192.168.247.130), port 1-100
100 ports to scan, use -V to see all the replies
+----+-----------+---------+---+-----+-----+-----+
|port| serv name | flags |ttl| id | win | len |
+----+-----------+---------+---+-----+-----+-----+
22 ssh : .S..A... 64 0 14600 46
80 http : .S..A... 64 0 14600 46
All replies received. Done.
Not responding ports: #源地址欺骗,但是不知道扫描后的结果
root@kali:~# hping3 -c 100 -S --spoof 192.168.247.140 -p ++1 192.168.247.130
HPING 192.168.247.130 (eth0 192.168.247.130): S set, 40 headers + 0 data bytes
--- 192.168.247.130 hping statistic ---
100 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms2、僵尸扫描
Kali渗透测试之端口扫描——僵尸扫描(Scapy、python脚本、nmap)
3、全连接端口扫描
全连接扫描(SYN、ACK+SYN、ACK)不隐蔽。只要建立完整的三次握手,行为就很容易被识别出来
1)全连接端口扫描——nmap
- nmap -sT 192.168.247.129 //扫描1000个常见端口
- nmap -sT 192.168.247.129 -p 1-100 //-p 指定端口进行扫描
root@kali:~# nmap -sT 192.168.247.129
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-14 20:17 CST
Nmap scan report for bogon (192.168.247.129)
Host is up (0.0011s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
3306/tcp open mysql
MAC Address: 00:0C:29:8F:74:74 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.51 seconds2)全连接端口扫描——dmitry
- 功能简单,使用简单
- 默认扫描150个最常用的端口
root@kali:~# dmitry -p 192.168.247.129 //-p 执行TCP扫描
Deepmagic Information Gathering Tool
"There be some deep magic going on"
HostIP:192.168.247.129
HostName:bogon
Gathered TCP Port information for 192.168.247.129
---------------------------------
Port State
80/tcp open
135/tcp open
139/tcp open
Portscan Finished: Scanned 150 ports, 146 ports were in state closed
All scans completed, exiting3)全连接端口扫描——nc
root@kali:~# nc -nv -w 1 -z 192.168.247.129 1-200
(UNKNOWN) [192.168.247.129] 139 (netbios-ssn) open
(UNKNOWN) [192.168.247.129] 135 (loc-srv) open
(UNKNOWN) [192.168.247.129] 80 (http) open