华为IPSECVPN和GRE的配置实验
gre_over_ipsec
- 概述
-
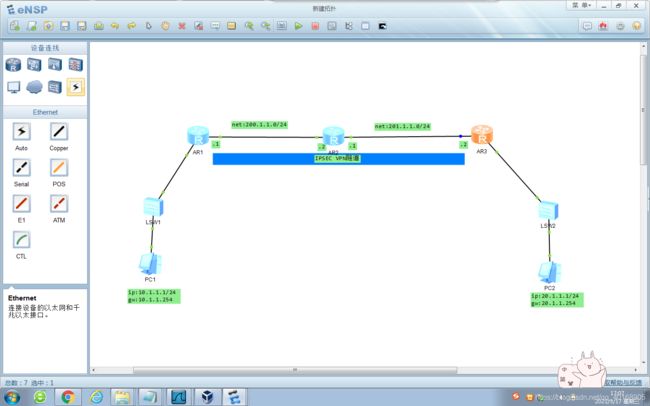
- 网络拓扑图
- 需求分析
- 配置
-
- 配置验证
- 连通性测试
- 抓包分析
- 总结:
概述
网络拓扑图
需求分析
1.网络都能互动,然后搭建IPSECVPN加密(私网路由可以放到公网里面传输OSPF)。
2.私网路由不允许通过公网传输:我们得在OSPF里面去掉私网路由
配置
路由器R1的配置:
acl number 3000
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 20.1.1.0 0.0.0.255
acl number 3001
rule 5 permit ip source 200.1.1.1 0 destination 201.1.1.2 0
ipsec proposal test
ipsec policy p1 10 manual
security acl 3001
proposal test
tunnel local 200.1.1.1
tunnel remote 201.1.1.2
sa spi inbound esp 654321
sa string-key inbound esp simple 123456
sa spi outbound esp 123456
sa string-key outbound esp simple 123456
interface GigabitEthernet0/0/0
ip address 200.1.1.1 255.255.255.0
ipsec policy p1
interface GigabitEthernet0/0/1
ip address 10.1.1.254 255.255.255.0
interface GigabitEthernet0/0/2
interface NULL0
interface Tunnel0/0/0
ip address 1.1.1.1 255.255.255.255
tunnel-protocol gre
source 200.1.1.1
destination 201.1.1.2
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.0 0.0.0.255
network 200.1.1.0 0.0.0.255
ip route-static 20.1.1.0 255.255.255.0 Tunnel0/0/0
路由器R2的配置:
interface GigabitEthernet0/0/0
ip address 200.1.1.2 255.255.255.0
interface GigabitEthernet0/0/1
ip address 201.1.1.1 255.255.255.0
interface GigabitEthernet0/0/2
interface NULL0
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 200.1.1.0 0.0.0.255
network 201.1.1.0 0.0.0.255
路由器R3的配置:
acl number 3000
rule 5 permit ip source 20.1.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
acl number 3001
rule 5 permit ip source 201.1.1.2 0 destination 200.1.1.1 0
ipsec proposal test
ipsec policy p1 10 manual
security acl 3001
proposal test
tunnel local 201.1.1.2
tunnel remote 200.1.1.1
sa spi inbound esp 123456
sa string-key inbound esp simple 123456
sa spi outbound esp 654321
sa string-key outbound esp simple 123456
interface GigabitEthernet0/0/0
ip address 201.1.1.2 255.255.255.0
ipsec policy p1
interface GigabitEthernet0/0/1
ip address 20.1.1.254 255.255.255.0
interface GigabitEthernet0/0/2
interface NULL0
interface Tunnel0/0/0
ip address 3.3.3.3 255.255.255.255
tunnel-protocol gre
source 201.1.1.2
destination 200.1.1.1
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 201.1.1.0 0.0.0.255
ip route-static 10.1.1.0 255.255.255.0 Tunnel0/0/0
配置验证
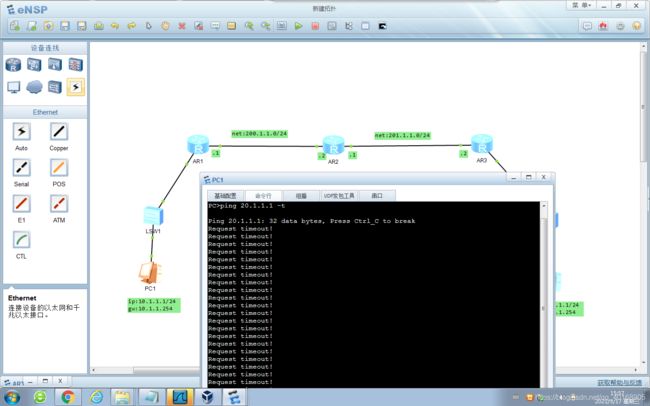
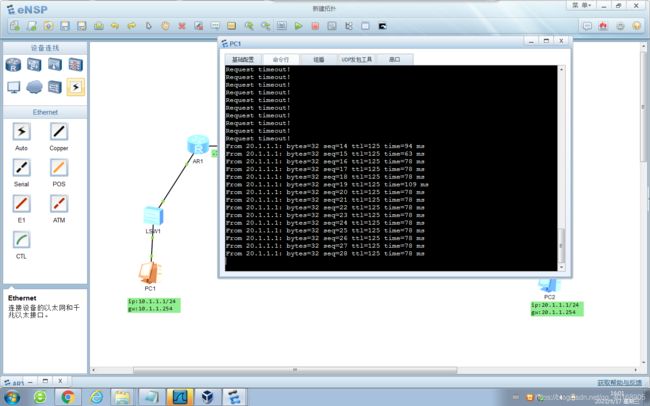
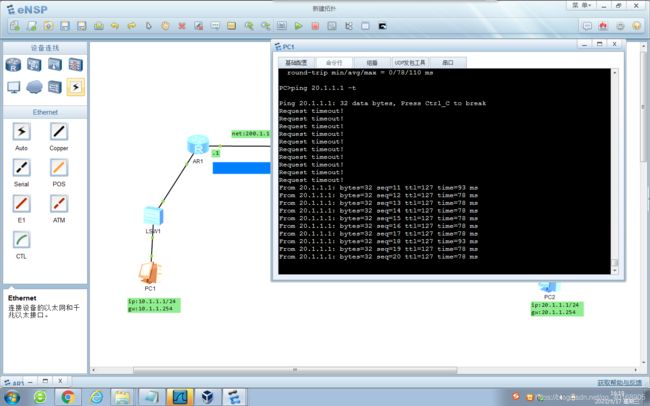
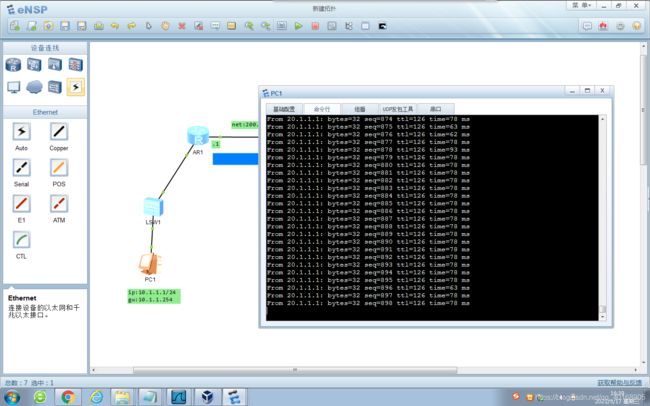
连通性测试
IPSEC VPN配置完成后
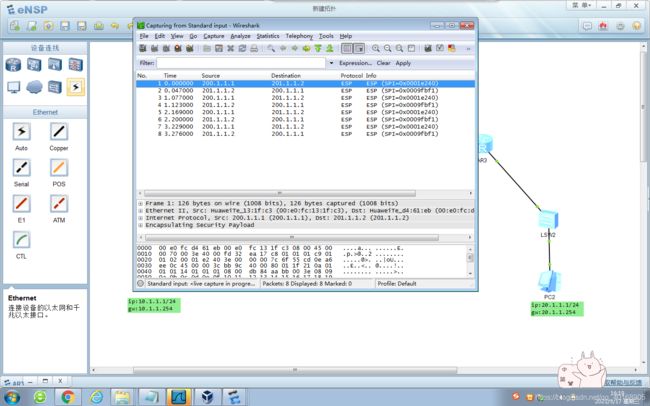
抓包分析

私网路由不允许通过公网传输:我们得在OSPF里面去掉私网路由
连通性测试:
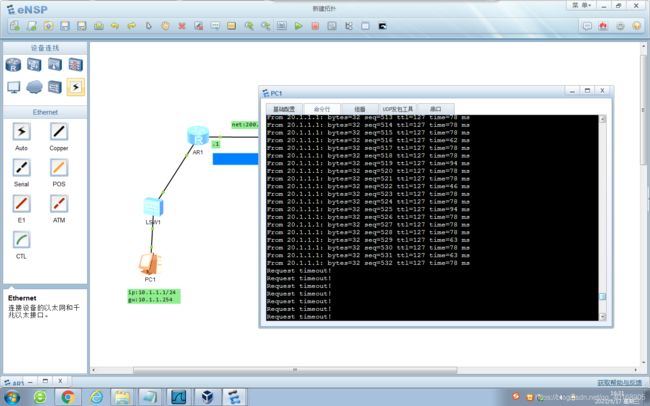
注释:数据包先路由,再IPSEC。
抓取感兴趣的流量GRE进行加密,说白了,就是要把私网的数据包封装到公网GRE头里面
先私网的数据包–>gre—>新IP–>路由–>acl–>ipsec
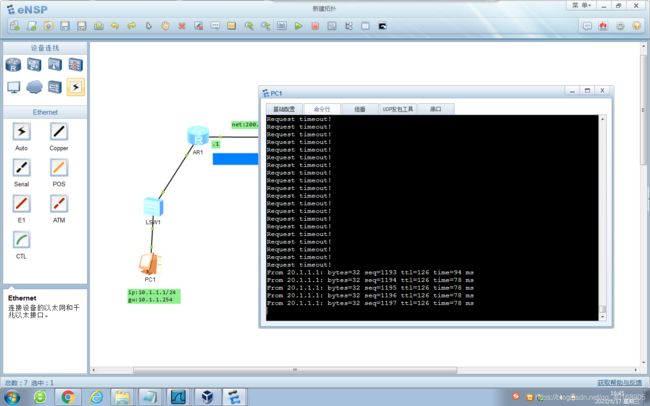
总结:
想加密的,放到Tunnel0/0/0隧道里面;不想加密的,不放在隧道里面,走非隧道路由协议。