ansible加密模块ansible-vault
ansible加密模块ansible-vault
-
- ansible-vault简介
- 在配置文件中指定密码文件路径
- 创建加密文件
- 修改加密文件的密码
- 编辑加密文件
- 查看加密文件
- 将文件加密
- 解密文件
-
- 将文件解密
- 解密文件并保留原加密文件
- 非交互式加密解密--指定密码文件
-
- 指定密码文件加密数据
- 指定密码文件查看数据
- 指定密码文件解密数据
- 运行加密的playbook
-
- 提示输入密码来运行playbook
- 指定密码文件来运行加密playbook
- 调用多个加密变量文件时输入多个密码/加载多个密码文件
- RH294课程ansible-vault练习
-
- 开启对应章节的练习环境
- 完成本章练习
ansible-vault简介
为了配置被管理主机, ansible可能会使用一些敏感数据,比如密码或者api密钥。通常来说,这些以明的形式成 Inventory件或者ansible文件中。这种情况,任何用户访问了这些文件,都能看到敏感数据,非常不安全.
ansible vault是 ansible的组件,可以加密解密 ansible使用的数据。为了安全建议使用 ansible vault.
你可以使用 ansible-vault来创建,编辑,加密或解密或者查看文件。 ansible vault可以加密任何结构的数据。可以加密 nventory变量,定义变量的 playbook文件,传递到 playbook中的变量文件,或者 ansible role中的变量。
通常情况下,生产环境只使用ansible-vault来加密变量文件.
在配置文件中指定密码文件路径
# 编辑配置文件
vim ansible.cfg
# 指定密码密码文件路径
[defaults]
vault_password_file = /path/to/vault_password_file
创建加密文件
# 创建加密文件
[student@workstation data-variables]$ ansible-vault create test.yml
New Vault password: # 输入文件密码
Confirm New Vault password: # 输入确认密码
# 输入完密码后就进入了编辑界面,想vim一样正常编辑即可.
# 查看文件,发现文件已经被加密了
[student@workstation data-variables]$ cat test.yml
$ANSIBLE_VAULT;1.1;AES256
37393965386233633466663233376436356238303931313262373730623663376161376631623231
6339313134366265346231363962326335663866323432340a633661653161646264633235313939
61303431653734663330613766373531323836396264636638313933663733356636613161356434
6464313964373464330a346565313434623137376331376431353737646563386637613832623031
65316336663238613664323233386332613035396234666161373964343934653131393438613665
65303261343462393538343332356136386164666430396632333230646138376163666564623064
39616234616462623837396435366438663266343333333735626430356435316362653763653235
36323630303634656235
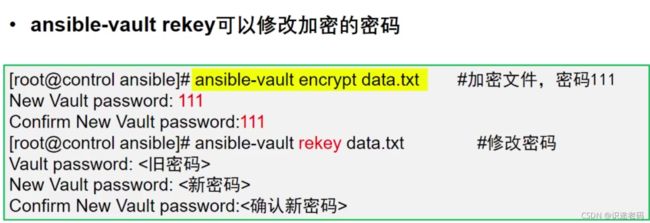
修改加密文件的密码
# 修改加密文件的密码
[student@workstation data-variables]$ ansible-vault rekey test.yml
Vault password: # 输入原密码
New Vault password: # 输入新密码
Confirm New Vault password: # 输入确认密码
Rekey successful # 提示密码修改成功
编辑加密文件
# 编辑加密文件
[student@workstation data-variables]$ ansible-vault edit test.yml
Vault password: # 输入密码
# 输入正确密码后,进入编辑界面,像使用vim一样进行编辑.
查看加密文件
# 查看加密文件
[student@workstation data-variables]$ ansible-vault view test.yml
Vault password: # 输入文件密码
# 输入正确密码后可以查看文件中的明文信息
---
- name:
hosts: all
tasks:
user:
- name: test
将文件加密
# 将文件加密
[student@workstation data-variables]$ ansible-vault encrypt test.yml
New Vault password: # 输入密码
Confirm New Vault password: # 确认密码
Encryption successful # 提示加密成功
解密文件
将文件解密
# 解密文件
[student@workstation data-variables]$ ansible-vault decrypt test.yml
Vault password: # 输入密码
Decryption successful # 提示解密成功
# 查看解密后的明文文件
[student@workstation data-variables]$ cat test.yml
---
- name:
hosts: all
tasks:
user:
- name: test
解密文件并保留原加密文件
# 解密文件并保留原加密文件
[student@workstation data-variables]$ ansible-vault decrypt test.yml --output=test1.yml
Vault password: # 输入密码
Decryption successful # 提示解密成功
# 原加密文件和输出的解密文件都在
[student@workstation data-variables]$ ls
ansible.cfg inventory playbook.yml test1.yml test.yml vars_playbook.yml
# 查看解密后的文件
[student@workstation data-variables]$ cat test1.yml
---
- name:
hosts: all
tasks:
user:
- name: test
# 查看原加密文件
[student@workstation data-variables]$ cat test.yml
$ANSIBLE_VAULT;1.1;AES256
33663437613833393165376362623535343534363064356230383836303737373434393237396230
3266366339336539326462343932626639653663363566360a326265313532323234616561373536
39613231343230326636393433303639376236613031353765353462373535353763316337323365
3963306435306634360a366239636534373136646631306262343237646265663634313766306537
38306530396230366137613439363431326238386161636332623261643032383564393233323036
34376566323965643163623838643033383662303663316339353263656166313035373231646364
39613630623164653332383734343636303534323363663434633765313938373063613962636237
62623661646665643161
非交互式加密解密–指定密码文件
指定密码文件加密数据
# 创建密码文件
## 将密码写在pass.txt文件中
echo 'redhat' > pass.txt
# 将密码文件权限设为600或5500
chmod 600 pass.txt
# 指定密码文件加密文件
[student@workstation data-variables]$ ansible-vault encrypt --vault-id=pass.txt playbook.yml
Encryption successful
[student@workstation data-variables]$ cat playbook.yml
$ANSIBLE_VAULT;1.1;AES256
38393130353833646232643630383435333266636261363362643930326364356131306561343664
指定密码文件查看数据
# 创建密码文件
vim pass.txt
## 将密码写在pass.txt文件中
# 指定密码文件查看加密文件--旧版本2.4以前
[student@workstation data-variables]$ ansible-vault --vault-password-file=./pass.txt view test
.yml
---
- name:
hosts: all
tasks:
user:
- name: test
# 指定密码文件查看加密文件--新版本--2.4以后
[student@workstation data-variables]$ ansible-vault --vault-id=./pass.txt view test.yml
---
- name:
hosts: all
tasks:
user:
- name: test
指定密码文件解密数据
# 指定密码文件解密文件
[student@workstation data-variables]$ ansible-vault decrypt --vault-id=pass.txt playbook.yml
Decryption successful
[student@workstation data-variables]$ cat playbook.yml
---
- name: test use var
hosts: all
运行加密的playbook
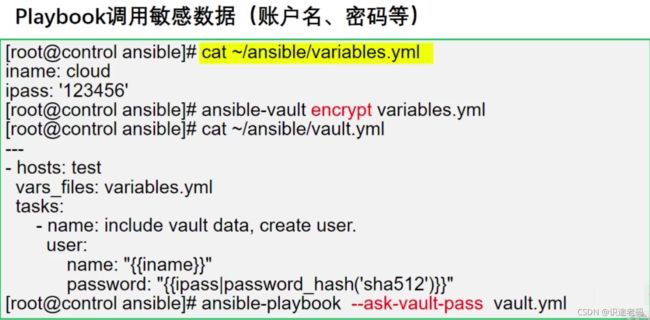
提示输入密码来运行playbook
可以使用–ask-vault-pass参数来提示输入密码运行加密剧本
也可以使用–vault-id @prompt参数来提示输入密码
# 运行加密剧本提示输入密码---2.4以前版本
[student@workstation data-secret]$ ansible-playbook --ask-vault-pass test.yml
Vault password: # 输入密码
PLAY [create user] ***************************************************************************
TASK [Gathering Facts] ***********************************************************************
ok: [servera.lab.example.com]
# 运行加密剧本并使用@prompt提示输入密码---2.4以后版本的功能
[student@workstation data-variables]$ ansible-playbook --vault-id @prompt playbook.yml
Vault password (default):
PLAY [test use var] **************************************************************************
TASK [Gathering Facts] ***********************************************************************
指定密码文件来运行加密playbook
# 使用--vault-id=pass.txt来指定密码文件运行playbook
[student@workstation data-variables]$ ansible-playbook --vault-id=pass.txt playbook.yml
PLAY [test use var] **************************************************************************
TASK [Gathering Facts] ***********************************************************************
调用多个加密变量文件时输入多个密码/加载多个密码文件
# 输入多个密码
ansible-playbook --vault-id one@prompt --vault-id two@prompt playbook.yml
vault password (one): # 提示输入第一个密码
vault password (two): # 提示输入第二个密码
# 加载多个密码文件----未测试!
ansible-playbook --vault-id=pass1.txt --vault-id=pass2.txt playbook.yml
RH294课程ansible-vault练习
开启对应章节的练习环境
[student@workstation data-secret]$ lab data-secret start
Setting up workstation for lab exercise work:
· Verifying Ansible installation.............................. SUCCESS
· Creating working directory.................................. SUCCESS
· Downloading secret.yml file................................. SUCCESS
. Creating inventory directory................................ SUCCESS
. Creating Ansible configuration file......................... SUCCESS
. Creating host file.......................................... SUCCESS
完成本章练习
[student@workstation data-secret]$ lab data-secret finish
Cleaning up the lab on workstation:
. Undoing the playbook tasks.................................. SUCCESS