在上一节讲了一些tcpdump常用功能,本期我们继续学习tcpdump后续功能。
流量过滤
tcpdump不仅支持单个过滤表达式过滤,也还支持多个过滤表达式。但需要注意的是传入的过滤表达式如含有Shell通配符,需将过滤表达式放在单引号内,以预防Shell对其进行解释和通配。如果需要深入学习过滤表达式,可以使用以下命令进行查看:
man pcap-filter
1、只抓取UDP数据包
[root@localhost ~]# tcpdump -i ens5f1 -c 2 'udp'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens5f1, link-type EN10MB (Ethernet), capture size 262144 bytes
14:37:38.852304 IP gateway.35428 > 239.255.255.250.ssdp: UDP, length 395
14:37:38.852458 IP gateway.35428 > 239.255.255.250.ssdp: UDP, length 467
2 packets captured
15 packets received by filter
0 packets dropped by kernel
tcpdump另外还支持如下的协议类型:
ip、ip6、arp、tcp、rarp
2、抓取固定来源的数据包
对一台主机而言,后台运行的网络有很多个,所连接的服务器也会有很多个。那如果我们只想查看某一个服务器和主机的数据包情况了?在tcpdump中也支持这样的数据包抓包,但需要设置src(source)和dst(destination)就可以了,同时tcpdum也支持各条件间逻辑运算,如and、or等。
如果tcpdump未指定dst和src,则默认全匹配,而不区分是dst还是src
[root@localhost ~]# tcpdump -i ens5f1 -t -c 5 'udp' or 'dst 114.114.114.114' or 'src 192.168.8.1'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens5f1, link-type EN10MB (Ethernet), capture size 262144 bytes
IP6 fe80::b072:b447:2702:3fca.55407 > ff02::1:3.hostmon: UDP, length 33
IP 192.168.8.101.52468 > 224.0.0.252.hostmon: UDP, length 33
IP localhost.localdomain.52349 > gateway.domain: 14923+ PTR? 3.0.0.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa. (90)
IP gateway.domain > localhost.localdomain.52349: 14923 NXDomain 0/1/0 (154)
IP localhost.localdomain.43621 > gateway.domain: 25497+ PTR? a.c.f.3.2.0.7.2.7.4.4.b.2.7.0.b.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa. (90)
5 packets captured
14 packets received by filter
0 packets dropped by kernel
3、抓取特定端口的数据包
[root@localhost ~]# tcpdump -i ens5f1 -c 10 'src port 53 and udp or dst port 80'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens5f1, link-type EN10MB (Ethernet), capture size 262144 bytes
15:05:42.618107 IP localhost.localdomain.32980 > tsa03s06-in-f14.1e100.net.http: Flags [S], seq 712530441, win 29200, options [mss 1460,sackOK,TS val 792506576 ecr 0,nop,wscale 7], length 0
15:05:42.623275 IP gateway.domain > localhost.localdomain.51286: 19244 1/0/0 PTR tsa03s06-in-f14.1e100.net. (85)
15:05:42.627834 IP gateway.domain > localhost.localdomain.57579: 54387 NXDomain* 0/1/0 (101)
15:05:42.632411 IP gateway.domain > localhost.localdomain.37002: 35102 NXDomain* 0/1/0 (101)
15:05:43.259504 IP gateway.domain > localhost.localdomain.44708: 24032 1/0/0 A 116.62.82.159 (50)
15:05:43.261047 IP gateway.domain > localhost.localdomain.44708: 36078 0/1/0 (107)
15:05:43.337416 IP gateway.domain > localhost.localdomain.37886: 32328 1/0/0 A 118.178.109.187 (53)
15:05:43.339220 IP gateway.domain > localhost.localdomain.37886: 47697 0/1/0 (110)
15:05:43.344380 IP gateway.domain > localhost.localdomain.45436: 31901 6/0/0 CNAME images0.cnblogs.com.cdn.dnsv1.com., CNAME 1069954.p23.tc.cdntip.com., A 180.101.217.192, A 180.101.217.119, A 180.101.217.115, A 180.153.100.201 (181)
15:05:43.356015 IP gateway.domain > localhost.localdomain.45436: 24484 2/1/0 CNAME images0.cnblogs.com.cdn.dnsv1.com., CNAME 1069954.p23.tc.cdntip.com. (174)
10 packets captured
13 packets received by filter
0 packets dropped by kernel
tcpdump还支持的过滤类型如下所示:
- port:端口
- host:主机,如'host 112.65.12.245'
- portranger:端口范围,如'dst portrange 0-22'
- net:网络段,如'dst net 192.168'
如未设置过滤类型,则默认为主机(host)
4、抓取属于两台服务器之间的数据包
[root@localhost ~]# tcpdump -i ens5f1 -c 10 'host 192.168.8.8 and (www.cnblogs.com or www.baidu.com)'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens5f1, link-type EN10MB (Ethernet), capture size 262144 bytes
15:23:03.918266 IP localhost.localdomain.47234 > 115.239.210.27.https: Flags [P.], seq 660681023:660681721, ack 812631894, win 238, length 698
15:23:03.930901 IP 115.239.210.27.https > localhost.localdomain.47234: Flags [.], ack 698, win 944, length 0
15:23:03.939766 IP 115.239.210.27.https > localhost.localdomain.47234: Flags [.], seq 1:1461, ack 698, win 944, length 1460
15:23:03.939783 IP localhost.localdomain.47234 > 115.239.210.27.https: Flags [.], ack 1461, win 261, length 0
15:23:03.939950 IP 115.239.210.27.https > localhost.localdomain.47234: Flags [.], seq 1461:2921, ack 698, win 944, length 1460
15:23:03.939961 IP localhost.localdomain.47234 > 115.239.210.27.https: Flags [.], ack 2921, win 284, length 0
15:23:03.940137 IP 115.239.210.27.https > localhost.localdomain.47234: Flags [P.], seq 2921:4030, ack 698, win 944, length 1109
15:23:03.940146 IP localhost.localdomain.47234 > 115.239.210.27.https: Flags [.], ack 4030, win 307, length 0
15:23:03.940484 IP 115.239.210.27.https > localhost.localdomain.47234: Flags [P.], seq 4030:4155, ack 698, win 944, length 125
15:23:03.940496 IP localhost.localdomain.47234 > 115.239.210.27.https: Flags [.], ack 4155, win 307, length 0
10 packets captured
62 packets received by filter
0 packets dropped by kernel
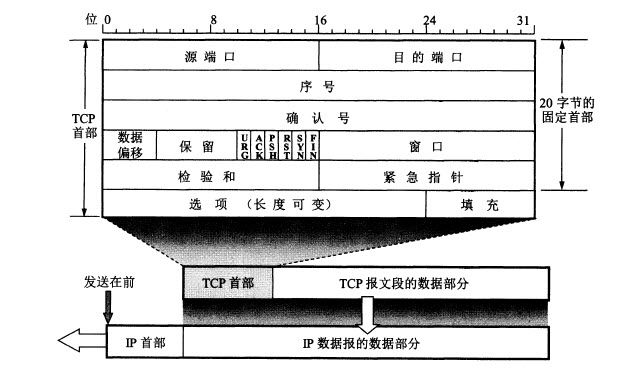
常用协议数据报格式
在此对协议不做深入讲解,仅列出TCP/IP的数据报格式,有兴趣的话,可以自行查阅相关资料。
-
IP协议数据报格式如下所示:
-
常用协议编号如下所示:
- TCP协议数据报格式如下所示:
- UDP协议数据报格式如下所示:
抓包进阶
在明白各常用协议的数据报格式后,我们先来看看以下几个示例:
1、抓取本机与百度之间TCP三次握手中的第一个网络包,且排除主机为cnblogs的数据包
[root@localhost ~]# tcpdump -i ens5f1 -c 5 'tcp[tcpflags] & tcp-syn != 0 and dst host www.baidu.com and not dst host www.cnblogs.com'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens5f1, link-type EN10MB (Ethernet), capture size 262144 bytes
15:39:26.311628 IP localhost.localdomain.53062 > 115.239.211.112.https: Flags [S], seq 735716502, win 29200, options [mss 1460,sackOK,TS val 794530269 ecr 0,nop,wscale 7], length 0
15:39:26.505795 IP localhost.localdomain.53078 > 115.239.211.112.https: Flags [S], seq 4031881731, win 29200, options [mss 1460,sackOK,TS val 794530463 ecr 0,nop,wscale 7], length 0
15:39:26.505863 IP localhost.localdomain.53080 > 115.239.211.112.https: Flags [S], seq 867030794, win 29200, options [mss 1460,sackOK,TS val 794530463 ecr 0,nop,wscale 7], length 0
15:39:29.222164 IP localhost.localdomain.53100 > 115.239.211.112.https: Flags [S], seq 4207431041, win 29200, options [mss 1460,sackOK,TS val 794533180 ecr 0,nop,wscale 7], length 0
15:39:29.235246 IP localhost.localdomain.53102 > 115.239.211.112.https: Flags [S], seq 548060444, win 29200, options [mss 1460,sackOK,TS val 794533193 ecr 0,nop,wscale 7], length 0
5 packets captured
15 packets received by filter
0 packets dropped by kernel
2、抓取IP包长度大于500的数据包
[root@localhost ~]# tcpdump -i ens5f1 -c 5 'ip[2:2]>500'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens5f1, link-type EN10MB (Ethernet), capture size 262144 bytes
15:35:27.613243 IP localhost.localdomain.5902 > 112.65.12.245.35445: Flags [.], seq 1864189501:1864198141, ack 2730205778, win 229, length 8640
15:35:27.613255 IP localhost.localdomain.5902 > 112.65.12.245.35445: Flags [P.], seq 8640:9410, ack 1, win 229, length 770
15:35:28.181058 IP localhost.localdomain.5902 > 112.65.12.245.35445: Flags [.], seq 9410:13730, ack 11, win 229, length 4320
15:35:28.181073 IP localhost.localdomain.5902 > 112.65.12.245.35445: Flags [.], seq 13730:18050, ack 11, win 229, length 4320
15:35:28.181090 IP localhost.localdomain.5902 > 112.65.12.245.35445: Flags [.], seq 18050:22370, ack 11, win 229, length 4320
5 packets captured
6 packets received by filter
0 packets dropped by kernel
proto[expr:size]详细解释如下所示:
proto:就是protocol的缩写,表示协议的名称。可以指定的协议类型大致如下:
- ether:链路层协议 - fddi:链路层协议
- wlan:链路层协议 - ppp:链路层协议
- link:链路层协议 - ip:网络层
- arp:网络层 - rarp:网络层
- icmp:网络层 - ip6:网络层
- tcp:传输层 - udp:传输层
expr:用来指定数据包偏移量,表示从某个协议数据包的第多个位开始提取内容,默认起始位置为0
size:表示从expr之后提取多少个字节
- 如果只设置expr,而未设置size,则默认提取1个字节
- ip[2:2]:则提取第3和第4个字节
- ip[0]:则提取ip协议的第1个字节
比较运算符:常用的比较运算符如下所示:
< > <= >= = !=
为了增加可读性,TCP协议数据报头中有6个tcpflags标志字段域,在tcpdump中可以用以下方式进行表达:
tcp-urg tcp-ack tcp-psuh tcp-rst tcp-syn tcp-fin
逻辑运算符:如果一个过滤表达式中包含多个过滤表达式,则可以使用逻辑运算符进行串联
- ! / not:表示非关系
- && / and :表示与关系
- || / or:表示或关系
要详细理解上面的这些示例,需要对常用协议的数据报格式有足够的了解和掌握。
[参考资料]
1.计算机网络(第七版) 谢希仁