使用AWS 管理控制台和 AWS CLI创建EKS集群
Amazon Elastic Kubernetes Service (Amazon EKS) 是一种托管服务,用户可以使用它在 AWS 上运行 Kubernetes,而无需安装、操作和维护Kubernetes 控制层面或节点。
Amazon EKS 为每个集群运行一个单租户 Kubernetes 控制层面。控制层面基础设施不在集群或 AWS 账户之间共享。控制面包含至少两个 API 服务器实例和三个etcd跨一个区域内三个可用区运行的实例。Amazon EKS:
- 主动监控控制平面实例上的负载,并自动缩放它们以确保高性能。
- 可以根据需要在区域内跨可用区重新启动运行状况不佳的控制层面实例。
- 利用 AWS 区域的架构来保持高可用性。
本实验利用AWS管理控制台和AWS CLI来创建EKS集群。
环境准备
账号
使用已有AWS账号创建Administrator
用户:Administration
组:Administrators
组策略:AdministratorAccess
Client 设备
操作系统:CentOS 7 1908
安装和配置创建和管理 Amazon EKS 集群所需的以下工具和资源:
- AWS CLI,参考在 Linux 上安装、更新和卸载 AWS CLI 版本 2
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install
- 安装kubectl,下载AWS EKS 提供的集群的 Kubernetes 版本二进制文件,并安装,选择Kubernetes 1.19
curl -o kubectl https://amazon-eks.s3.us-west-2.amazonaws.com/1.19.6/2021-01-05/bin/linux/amd64/kubectl
openssl sha1 -sha256 kubectl
chmod +x ./kubectl
mkdir -p $HOME/bin && cp ./kubectl $HOME/bin/kubectl && export PATH=$PATH:$HOME/bin
echo 'export PATH=$PATH:$HOME/bin' >> ~/.bashrc
[root@aws-client ~]# aws configure
AWS Access Key ID [None]: AKIARXXXXXXXXXX75
AWS Secret Access Key [None]: 9jH2NgzHv7NEeXXBW2lRkUqQj0fCm2VS2xpQMTSe
Default region name [None]: sp-southeast-1
Default output format [None]: json
创建 Amazon EKS 群集
参考官方文档:亚马逊 EKS 入门 — AWS 管理控制台和 AWS CLI
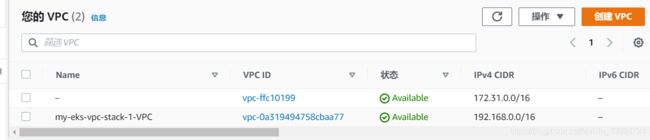
创建专用VPC
使用符合 Amazon EKS 要求的公有和私有子网创建 Amazon VPC,AWS已经做了相应的yaml文件
aws cloudformation create-stack \
--stack-name my-eks-vpc-stack \
--template-url https://s3.us-west-2.amazonaws.com/amazon-eks/cloudformation/2020-10-29/amazon-eks-vpc-private-subnets.yaml
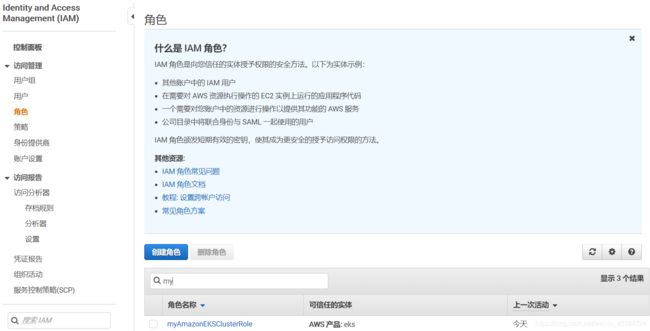
创建集群 IAM 角色
由 Amazon EKS 管理的 Kubernetes 集群代表您调用其他 AWS 服务以管理服务所使用的资源。
创建文件:cluster-role-trust-policy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "eks.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
创建角色
aws iam create-role \
--role-name myAmazonEKSClusterRole \
--assume-role-policy-document file://"cluster-role-trust-policy.json"
将所需的 Amazon EKS 托管的 IAM 策略附加到角色
aws iam attach-role-policy \
--policy-arn arn:aws:iam::aws:policy/AmazonEKSClusterPolicy \
--role-name myAmazonEKSClusterRole
创建集群
首先使用前面创建的Administrator登录
导航到EKS-cluster-create cluster

名字
集群服务角色:刚才建的myAmazonEKSClusterRole

网络选择建的新vpc
其他的默认就好。
创建完成以后

Client与集群通信
创建或更新kubeconfig文件中的集群
[root@aws-client ~]# aws eks --region ap-southeast-1 update-kubeconfig --name my-cluster
Updated context arn:aws:eks:ap-southeast-1:098246620002:cluster/my-cluster in /root/.kube/config
默认情况下,config文件创建在~/.kube或者新群集的配置添加到现有config中的文件 ~/.kube
测试配置
[root@aws-client ~]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.100.0.1 443/TCP 2m18s
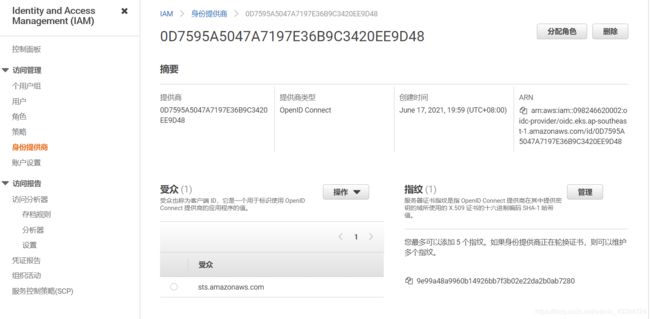
创建 IAM OpenID Connect (OIDC)
对于集群只需完成一次此步骤。
- 选择配置” 选项卡。
- 在详细信息部分中,复制OpenID Connect。
- 通过以下网址打开 IAM 控制台:https://console.aws.amazon.com/iam/
- 在导航面板中,选择身份提供商。
- 选择添加提供程序。
- 适用于提供商类型中,选择OpenID Connect。
- 适用于提供商 URL,请从步骤 2 中粘贴集群的 OIDC 提供商 URL,然后选择获取指纹。
- 适用于受众,输入sts.amazonaws.com,然后选择添加提供程序。
创建节点集群nodeCluster
nodeCluster两种类型
- Fargate — Linux— 如果要在 AWS Fargate 上运行 Linux 应用程序
- 托管节点 — Linux— 如果要在 Amazon EC2 实例上运行 Amazon Linux 应用程序,我们选择此类型
创建 Amazon EC2 Linux 托管节点组
CNI 插件创建 IAM 角色
为 Amazon VPC CNI 插件创建 IAM 角色,并将所需的 Amazon EKS IAM 托管策略附加到其中。默认情况下,亚马逊 EKS 亚马逊 VPC CNI 插件安装在集群上。该插件允许 Kubernetes Pod 在 Pod 内具有与其在 VPC 网络上相同的 IP 地址。
创建文件cni-role-trust-policy.json
[root@aws-client ~]# cat cni-role-trust-policy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::09824xxx0002:oidc-provider/oidc.eks.ap-southeast-1.amazonaws.com/id/0D7595A5047A7197E36B9C3420EE9D48"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.ap-southeast-1.amazonaws.com/id/0D7595A5047A7197E36B9C3420EE9D48:sub": "system:serviceaccount:kube-system:aws-node"
}
}
}
]
}
其中,09824xxx0002是我的账户 ID,0D7595A5047A7197E36B9C3420EE9D48是刚才建的 IAM OpenID Connect ID。
为 Amazon VPC CNI 插件创建 IAM 角色
[root@aws-client ~]# aws iam create-role \
> --role-name myAmazonEKSCNIRole \
> --assume-role-policy-document file://"cni-role-trust-policy.json"
{
"Role": {
"Path": "/",
"RoleName": "myAmazonEKSCNIRole",
"RoleId": "AROARNX7UONRF7YP4HK6D",
"Arn": "arn:aws:iam::098246620002:role/myAmazonEKSCNIRole",
"CreateDate": "2021-06-17T12:08:53+00:00",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::098246620002:oidc-provider/oidc.eks.ap-southeast-1.amazonaws.com/id/0D7595A5047A7197E36B9C3420EE9D48"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.ap-southeast-1.amazonaws.com/id/0D7595A5047A7197E36B9C3420EE9D48:sub": "system:serviceaccount:kube-system:aws-node"
}
}
}
]
}
}
}
将所需的 Amazon EKS 托管的 IAM 策略附加到角色
[root@aws-client ~]# aws iam attach-role-policy \
> --policy-arn arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy \
> --role-name myAmazonEKSCNIRole
[root@aws-client ~]# aws eks update-addon \
> --cluster-name my-cluster \
> --addon-name vpc-cni \
> --service-account-role-arn arn:aws:iam::098246620002:role/myAmazonEKSCNIRole
{
"update": {
"id": "19d870d3-4fda-4cb3-b902-460363c4065f",
"status": "InProgress",
"type": "AddonUpdate",
"params": [
{
"type": "ServiceAccountRoleArn",
"value": "arn:aws:iam::098246620002:role/myAmazonEKSCNIRole"
}
],
"createdAt": "2021-06-17T08:09:40.104000-04:00",
"errors": []
}
}
创建节点 IAM 角色
创建节点 IAM 角色并向其附加所需的 Amazon EKS IAM 托管策略。Amazon EKS 节点kubelet守护程序代表您调用 AWS API。节点通过 IAM 实例配置文件和关联的策略获得这些 API 调用的权限。
创建文件:node-role-trust-policy.json
[root@aws-client ~]# cat node-role-trust-policy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
创建节点 IAM 角色
[root@aws-client ~]# aws iam create-role \
> --role-name myAmazonEKSNodeRole \
> --assume-role-policy-document file://"node-role-trust-policy.json"
{
"Role": {
"Path": "/",
"RoleName": "myAmazonEKSNodeRole",
"RoleId": "AROARNX7UONRNXZF7GWP3",
"Arn": "arn:aws:iam::098246620002:role/myAmazonEKSNodeRole",
"CreateDate": "2021-06-17T12:10:28+00:00",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
}
}
将所需的 Amazon EKS 托管 IAM 策略附加到角色
[root@aws-client ~]# aws iam attach-role-policy \
> --policy-arn arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy \
> --role-name myAmazonEKSNodeRole
[root@aws-client ~]# aws iam attach-role-policy \
> --policy-arn arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly \
> --role-name myAmazonEKSNodeRole
在控制台创建nodeCluster
- 在上面建好的my-cluster集群选择配置” 选项。
- 在存储库的配置选项卡上,选择计算选项卡,然后选择Add 节点组。
- 在存储库的配置节点组页面上,填写相应参数,接受剩余默认值,然后选择下一步。
- 名称— 为托管节点组输入唯一名称,例如my-nodegroup。
- 节点 IAM 角色名称— 选择myAmazonEKSNodeRole。 在本实验中,此角色必须仅用于此节点组,而不能用于其他节点组。
- 在存储库的设置计算和扩展配置页面上,接受默认值并选择下一步。
- 在存储库的指定网络页面上,选 key pair 用于SSH key pair,然后选择下一步。如果还没有 key pair,可以使用下面的命令进行创建。
aws ec2 create-key-pair --region ap-southeast-1 --key-name myKeyPair
- Review and create (审核并创建) 页面上,审核托管节点组配置并选择 Create (创建)
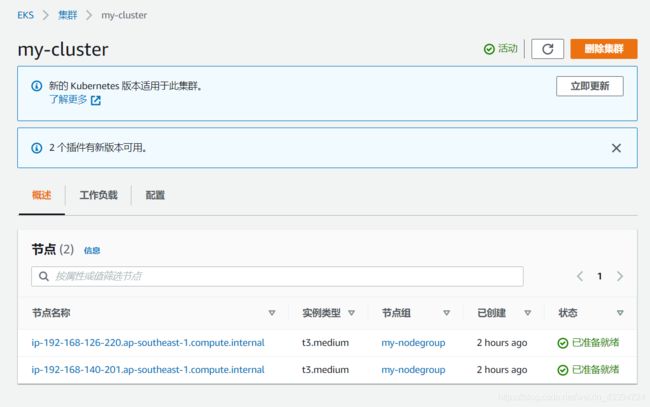
[root@aws-client ~]# kubectl get node
NAME STATUS ROLES AGE VERSION
ip-192-168-126-220.ap-southeast-1.compute.internal Ready 3m4s v1.19.6-eks-49a6c0
ip-192-168-140-201.ap-southeast-1.compute.internal Ready 2m58s v1.19.6-eks-49a6c0
测试
简单的运行命令建立pod
[root@aws-client ~]# kubectl run nginx --image=nginx
pod/nginx created
[root@aws-client ~]# kubectl get po
NAME READY STATUS RESTARTS AGE
nginx 1/1 Running 0 14s
[root@aws-client ~]# kubectl get po -owide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx 1/1 Running 0 38s 192.168.143.38 ip-192-168-140-201.ap-southeast-1.compute.internal
集群工作正常。