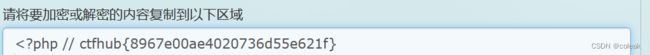
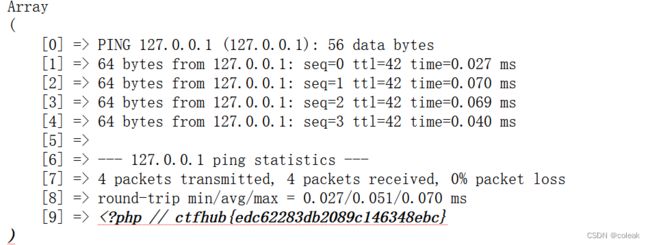
- Python 中的 `selectors`:构建高效的 I/O 复用程序
蜗牛沐雨
pythonjava开发语言
在现代编程中,高效地处理I/O操作是构建高性能应用程序的关键。无论是网络服务器、多任务文件处理还是实时数据流处理,都需要一种机制来同时监控多个I/O源,并在它们准备好时高效地处理数据。Python的selectors模块正是为了解决这一问题而设计的。它提供了一种高级的I/O复用接口,使得开发者可以轻松地实现高效的并发程序。一、什么是I/O复用?在多任务程序中,我们经常需要同时处理多个I/O操作,例
- 掌握 Python 网络爬虫技术:从基础入门到高级实践(附带爬虫案例)
一ge科研小菜鸡
Python编程语言python
个人主页:一ge科研小菜鸡-CSDN博客期待您的关注网络爬虫是自动访问网站并抓取网页数据的程序。Python凭借其丰富的库和易于使用的特性,成为开发网络爬虫的首选语言。本文将详细介绍如何使用Python进行网络爬虫开发,包括基本概念、主要工具、数据解析和高级爬取技术,并提供一个完整的实践案例。1.网络爬虫概述1.1什么是网络爬虫?网络爬虫(WebCrawler)是指用于访问和抓取网页内容的自动化脚
- 深度神经网络(DNN)详解
古龙飞扬
dnn人工智能神经网络
深度神经网络(DNN,DeepNeuralNetwork)是人工智能领域中的一种重要模型,它通过模拟人脑神经网络的结构和工作原理,实现了对复杂数据的处理和决策。以下是对深度神经网络(DNN)的超详细解析:一、DNN的基本概念DNN是一种具有多个隐藏层的神经网络模型,其核心在于其深度,即包含多个隐藏层。这些隐藏层通过非线性变换,使得模型能够捕捉到数据中的复杂关系和模式。DNN通常由输入层、隐藏层和输
- Swoole vs Workman
河南云和数据
互联网PHP编码
目前php通信服务框架最流行的有wwoole与workerman,swoole是有C语言开发的php扩展类,而workerman是纯PHP开发框架,可能swoole比workerman出名,在百度、腾讯公司都有在使用,使用频率也比较高,但workerman也有很多项目在用,哪到底谁能更胜一筹呢?首先我们一起来了解一下swoole:Swoole是面向生产环境的PHP异步网络通信引擎使PHP开发人员可
- DataGrip的数据库驱动的离线安装
一口酥Hac
数据库数据库
文章目录概要离线安装数据库驱动本地云桌面注意概要在某些工作环境中,由于网络访问受限,可能无法自动下载所需的数据库驱动。离线安装数据库驱动本地本地的DataGrip打开File->DataSources:云桌面云桌面的DataGrip打开File->DataSources:注意请确保下载的驱动版本与您所使用的数据库版本完全兼容,以避免出现连接或功能异常。
- workerman和swoole性能对比分析
csdndddsd
swoolephp后端
在大多数情况下,swoole具有更好的总体性能,因为它在并发能力、内存消耗、i/o吞吐量和网络吞吐量方面都胜过workerman。其性能优势归功于c扩展、高效的i/o事件循环和内存管理技术,使其适用于高并发、高吞吐量的web应用程序、实时应用程序和微服务架构。Workerman和Swoole性能对比结论:在大多数情况下,Swoole具有更好的总体性能。详细对比:Workerman和Swoole是两
- # 第一章:认识chatgpt
出门喝奶茶
chatgptchatgpt
chatgpt发展背景详细介绍一、基础理论背景人工智能和自然语言处理的兴起早期理论:20世纪中期,人工智能(AI)初见端倪,目标是模拟人类智能。自然语言处理作为AI的重要分支,致力于让机器理解和生成人类语言。关键里程碑:1980年代的统计方法和2000年代的神经网络技术,使NLP实现了从规则驱动到数据驱动的转变。神经网络与深度学习2010年代,深度学习的兴起极大推动了NLP的发展。基于大规模语料库
- 【性能调优】高性能实践
Forest 森林
性能调优性能优化
缓存思想性能优化,缓存为王,所以开始先介绍一下缓存。缓存在我们的架构设计中无处不在,常规请求是浏览器发起请求,请求服务端服务,服务端服务再查询数据库中的数据,每次读取数据都至少需要两次网络I/O,性能会差一些,我们可以在整个流程中增加缓存来提升性能。异步化处理例如Redis的bgsave,bgrewriteof就是分别用来异步保存RDB跟AOF文件的命令,bgsave执行后会立刻返回成功,主线程f
- 深入剖析移动通信系统的架构与关键技术
大苏牙
本文还有配套的精品资源,点击获取简介:移动通信系统是现代通信技术的重要组成部分,支持移动设备上的多种通信活动。本讲深入探讨了移动通信系统的基本原理、架构以及关键技术,如无线接口设计、核心网络功能和频谱效率优化。此外,分析了覆盖与容量平衡的策略,以及4G向5G演进所面临的挑战与机遇。通过本讲,学生将获得对移动通信系统全面而深入的认识。1.移动通信系统原理与架构移动通信系统是现代无线通讯的核心,它支持
- MAC与ARP
star9595
Linux
MAC全球范围内唯一,标识一个网络设备,MAC地址是物理地址,不可以改变的的,相当于建筑物地址;在网络世界中必须同时借助IP地址和对应的MAC地址,才可以唯一的确定一个通信设备,为了能够获得一个IP地址所对应的MAC地址需要ARP(addressresolutionprotocol)地址解析协议,基于一个ip地址解析出其对应的MAC地址,实现数据的完整封装。网络传输中的表:1.MAC地址表:说到M
- #深度学习:从基础到实践
single_ffish
深度学习gpt神经网络生成对抗网络1024程序员节
深度学习是人工智能领域近年来最为火热的技术之一。它通过构建由多个隐藏层组成的神经网络模型,能够从海量数据中自动学习特征和表征,在图像识别、自然语言处理、语音识别等领域取得了突破性进展。本文将全面介绍深度学习的基础知识、主要算法和实践应用,帮助您快速掌握这一前沿技术。1.深度学习的基础1.1人工神经网络深度学习是基于人工神经网络(ArtificialNeuralNetwork,ANN)的一种机器学习
- L2tp环境搭建笔记- Openwrt平台
月光技术杂谈
OpenWRT5GCPE5GCPE5GopenwrtL2TPdefaultrouteVPN虚拟局域网
L2tp环境搭建笔记-Openwrt平台安装L2tp服务配置L2tpserverL2TP客户端配置(使用配置文件)L2TP客户端配置(LUCI)客户端拔号(命令行方式)defaultroute路由问题L2TP(Layer2TunnelingProtocol)是一种工作在二层的隧道协议,是一种虚拟专用网络(VPN)协议。L2TP通常基于IPSEC作底层链路加密,并且使用PPP协议进行拔号。本文使用3
- 深入理解TCP/IP协议:互联网通信的核心
M乔木
网络协议tcp/ipphp网络网络协议
深入理解TCP/IP协议:互联网通信的核心在数字化时代,TCP/IP协议是支撑全球互联网通信的基石。它不仅负责数据的传输和路由,还确保了信息传递的准确性和完整性。本文将深入探讨TCP/IP协议的工作原理、结构以及它在网络编程中的应用。TCP/IP协议概述TCP/IP是一组用于数据通信的协议集合,包含了多个层次和协议。它的名字来源于其中最重要的两个协议:传输控制协议(TCP)和网际协议(IP)。TC
- 深入解析TCP/IP协议:网络通信的基石
一休哥助手
网络tcp/ip网络协议网络
1.引言TCP/IP协议是现代计算机网络的核心,它为互联网上的设备提供了通信的基础。在网络通信中,TCP/IP协议栈是无处不在的,无论是个人设备的浏览器请求,还是大型分布式系统的内部通信,都依赖于它的稳定、高效与可靠。本文将详细介绍TCP/IP协议的历史、分层模型、核心协议(TCP、IP等),并深入探讨其在网络通信中的重要角色。2.TCP/IP协议简介2.1TCP/IP的历史背景TCP/IP协议由
- TCP/IP协议族
dlz0836
网络tcp/ip网络协议
理解常见的网络协议,特别是TCP/IP协议族,对于网络通信的深入学习至关重要。TCP/IP协议族是支撑互联网通信的基础,涉及一系列协议来保证数据在网络上的正确传输。下面,我将对TCP/IP协议的工作原理进行深入浅出的讲解,分为多个部分来解释它的主要协议及其作用。一、TCP/IP协议族概述TCP/IP(TransmissionControlProtocol/InternetProtocol)是一个协
- 【计算机网络】NAT应用
酱学编程
计算机网络计算机网络网络智能路由器
NAT(NetworkAddressTranslation)的定义:NAT(NetworkAddressTranslation)的定义:NAT是一种网络技术,用于在IP数据包通过路由器或防火墙时修改其源IP地址或目的IP地址。主要目的是解决IP地址短缺问题,同时也能为网络提供一定程度的安全保护。NAT的主要功能和作用:地址转换源地址转换****(SNAT):iptables-tnat-APOSTR
- TCP/IP协议:构建互联网的基石
亿林数据
tcp/ip网络协议网络
TCP/IP协议,(TransmissionControlProtocol/lntemetProtocol)即传输控制协议/网际协议,是互联网通信的基础协议。它由一系列协议组成,共同构建了一个可靠、高效的网络通信体系。TCP/IP协议不仅实现了计算机之间的数据传输,还确保了数据的完整性和可靠性,为互联网的各种应用提供了坚实的基础。TCP和IP协议不仅仅是两个协议,而是指一个由FTP、TCP、UDP
- TCP/IP 协议:互联网通信的基石
froginwe11
开发语言
TCP/IP协议:互联网通信的基石引言TCP/IP协议,全称为传输控制协议/互联网协议,是互联网上应用最为广泛的通信协议。它定义了数据如何在网络上传输,是构建现代互联网的基础。本文将深入探讨TCP/IP协议的原理、结构、应用以及其在互联网通信中的重要性。TCP/IP协议概述定义TCP/IP协议是一套用于数据通信的协议集合,它包括了传输控制协议(TCP)和互联网协议(IP)等多个协议。这些协议共同构
- 基于R-CNN深度学习的无人机目标检测系统:数据集、模型和UI界面的完整实现
2025年数学建模美赛
R-CNN检测系统深度学习cnn无人机计算机视觉目标检测人工智能
摘要随着无人机技术的迅猛发展,无人机在军事、农业、环境监测等多个领域的应用日益广泛。无人机目标检测系统的建设成为提升无人机自主飞行和环境感知能力的重要环节。本文将详细介绍如何构建一个基于深度学习的无人机目标检测系统,采用R-CNN(区域卷积神经网络)算法,通过用户界面设计和数据集处理,实现高效的目标检测功能。通过本项目,旨在为无人机目标检测提供一种可行的解决方案,并提高其在复杂环境下的工作效率。目
- 搭建Hadoop与Hive环境
达达玲玲
hadoophive大数据
当搭建Hadoop与Hive环境时,以下是每个步骤的详细操作说明:1.安装并配置CentOS7操作系统:-下载CentOS7ISO镜像文件,并通过虚拟机或物理机安装CentOS7操作系统。-在安装过程中,为系统分配必要的网络、用户和权限。2.安装Java开发环境:-下载适合您的系统的JavaJDK版本。-使用命令或GUI工具安装JavaJDK。-配置JAVA_HOME环境变量:-打开终端,输入以下
- 字节iOS面试经验分享:HTTP与网络编程
LucianaiB
网络ios面试
字节iOS面试经验分享:HTTP与网络编程嗨,我是LucianaiB!总有人间一两风,填我十万八千梦。路漫漫其修远兮,吾将上下而求索。目录字节iOS面试经验分享:HTTP与网络编程HTTP协议简介iOS中HTTP请求的实现原理HTTPS与HTTP的区别TCP与UDP的区别三次握手四次挥手Cookie与Session流量控制与拥塞控制虚拟内存多线程并发访问共享资源iOS中线程数量的限制堆和栈的区别a
- Python 使用期物处理并发
weixin_30267785
操作系统pythonjavascriptViewUI
抨击线程的往往是系统程序员,他们考虑的使用场景对一般的应用程序员来说,也许一生都不会遇到……应用程序员遇到的使用场景,99%的情况下只需知道如何派生一堆独立的线程,然后用队列收集结果。示例:网络下载的三种风格为了高效处理网络I/O,需要使用并发,因为网络有很高的延迟,所以为了不浪费CPU周期去等待,最好在收到网络响应之前做些其他的事。为了通过代码说明这一点,我写了三个示例程序,从网上下载20个国家
- 独立服务器在网络游戏中的优势
wanhengidc
服务器运维
独立服务器是指单个客户端具有着独占访问权的服务器类型,让企业可以安装业务中所需的任何软件,其中包括多个操作系统和应用程序,本文主要来介绍独立服务器在网络游戏中都有哪些优势和作用。独立服务器在网络游戏中的优势之一就在于让用户可以控制自己的游戏体验感,用户能够根据自身的需求来配置服务器,可以选择操作系统、安装自定义脚本和设置游戏配置,同时还能够控制游戏中的玩家数量来释放内存。在大型多人在线网络游戏中,
- 导致服务器数据包丢失的原因有哪些?
wanhengidc
服务器运维
服务器出现数据包丢失的情况通常是在网络传输的过程中,服务器无法接收到数据来传输到目标设备中,从而导致数据包丢失的情况,这种现象会影响着网站的访问速度,严重的话会导致业务出现中断。本文就来探讨一下导致服务器数据包丢失的原因都有哪些吧!服务器出现数据包丢失的情况可能是机房网络不稳定引起的,当服务器所放置的机房线路质量较差,网络波动比较大,就会出现数据包丢失的情况,所以企业在选择服务器租用时,需要了解机
- JSON-RPC是什么?和HTTP request的区别?
virusos
随便记一下rpchttpjson
RPC(RemoteProcedureCall)指的是远程过程调用,简单的说,RPC就是从一台机器上通过参数传递的方式调用另一台机器上的一个函数或方法并得到响应结果。JSON-RPC:remoteprocedurecallprotocolencodedinJSONHTTP:可以看作是RPC的一种具体形式区别:HTTP有标准,具有通用性,如格式、字段等等,可以方便地在网络上开放HTTPAPI让别的机
- _知识图谱
大哥喝阔落
知识图谱人工智能
知识图谱(KnowledgeGraph)是一种结构化的知识表示形式,用于描述现实世界中的实体、概念及其之间的关系。它以图结构的形式组织知识,节点表示实体或概念,边表示实体之间的关系。知识图谱的核心目标是让机器能够理解和利用人类知识,从而支持智能问答、语义搜索、推荐系统等应用。1.知识图谱的定义知识图谱是一种语义网络,它通过图结构(节点和边)来表示知识:节点(Node):表示实体(如人、地点、事物)
- 修改 ssh 默认访问端口
技术分享,共享成长
linuxssh运维
Linux最小化安装后默认带有ssh服务并正常运行,服务默认端口为“22”。为了确保访问网络的安全,很多用户的网络设备对“22”端口做了限制,这时我们需要修改ssh服务默认的端口。此步骤建议直接在服务器上通过鼠标键盘操作修改配置文件vi/etc/ssh/sshd_config上图中将默认的“22”端口修改为端口“22345”,如上图所示,修改完毕后保存退出防火墙端口放行firewall-cmd--
- RPC是什么?
项三城
笔记
RPC概述RPC是什么RPC(RemoteProcedureCall)远程过程调用协议,一种通过网络从远程计算机上请求服务,而不需要了解底层网络技术的协议。RPC它假定某些协议的存在,例如TPC/UDP等,为通信程序之间携带信息数据。在OSI网络七层模型中,RPC跨越了传输层和应用层,RPC使得开发,包括网络分布式多程序在内的应用程序更加容易。过程是什么?过程就是业务处理、计算任务,更直白的说,就
- 智能工厂的设计软件 应用场景的一个例子:为AI聊天工具添加一个知识系统 之4 两种描述文件:source的自述文件和resource的描述文件
一水鉴天
人工智能
本文要点前面是为“描述”格式中描述项的未尽描述所所的扩展思考。现在我们回到前面的讨论。前面分析了我拿出来做例句的一段话中的三行文字(“自述”)--也基本上是文档“为AI聊天工具添加一个知识系统”的“枢纽”。进一步讨论这样的“枢纽”要怎样才能具备这个资格?那么,我们是否能基于这些讨论进一步准确根据三种处理器的描述文字确定三者在系统中的地位或作用呢?---就像刚刚我们确定了”语言处理器“或”网络“组件
- 智能工厂的设计软件 应用场景的一个例子:为AI聊天工具添加一个知识系统 之6 三端架构的本质/内在/外观:自明性/信念/bank词扇
一水鉴天
软件智能智能制造人工语言人工智能
本文提要一些补充在为前端和后端锁定的两个中心词“概念”(命题“作文”的程序公共逻辑语言)和“描述”(谓词“描述”的自然描述语言)的基础上,暂时将中端的中心词锁定在“环境”(情境“意义”的人工语义网络语言)。三者的共同性--都需要通过“演算”得到(命题演算/谓词演算/情境演算)。每种演算都以本地或局部的this此岸为输入(A-box,最初是一个条件分支符--条件表达式),远处或全局的彼岸that(T
- ztree设置禁用节点
3213213333332132
JavaScriptztreejsonsetDisabledNodeAjax
ztree设置禁用节点的时候注意,当使用ajax后台请求数据,必须要设置为同步获取数据,否者会获取不到节点对象,导致设置禁用没有效果。
$(function(){
showTree();
setDisabledNode();
});
- JVM patch by Taobao
bookjovi
javaHotSpot
在网上无意中看到淘宝提交的hotspot patch,共四个,有意思,记录一下。
7050685:jsdbproc64.sh has a typo in the package name
7058036:FieldsAllocationStyle=2 does not work in 32-bit VM
7060619:C1 should respect inline and
- 将session存储到数据库中
dcj3sjt126com
sqlPHPsession
CREATE TABLE sessions (
id CHAR(32) NOT NULL,
data TEXT,
last_accessed TIMESTAMP NOT NULL,
PRIMARY KEY (id)
);
<?php
/**
* Created by PhpStorm.
* User: michaeldu
* Date
- Vector
171815164
vector
public Vector<CartProduct> delCart(Vector<CartProduct> cart, String id) {
for (int i = 0; i < cart.size(); i++) {
if (cart.get(i).getId().equals(id)) {
cart.remove(i);
- 各连接池配置参数比较
g21121
连接池
排版真心费劲,大家凑合看下吧,见谅~
Druid
DBCP
C3P0
Proxool
数据库用户名称 Username Username User
数据库密码 Password Password Password
驱动名
- [简单]mybatis insert语句添加动态字段
53873039oycg
mybatis
mysql数据库,id自增,配置如下:
<insert id="saveTestTb" useGeneratedKeys="true" keyProperty="id"
parameterType=&
- struts2拦截器配置
云端月影
struts2拦截器
struts2拦截器interceptor的三种配置方法
方法1. 普通配置法
<struts>
<package name="struts2" extends="struts-default">
&
- IE中页面不居中,火狐谷歌等正常
aijuans
IE中页面不居中
问题是首页在火狐、谷歌、所有IE中正常显示,列表页的页面在火狐谷歌中正常,在IE6、7、8中都不中,觉得可能那个地方设置的让IE系列都不认识,仔细查看后发现,列表页中没写HTML模板部分没有添加DTD定义,就是<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3
- String,int,Integer,char 几个类型常见转换
antonyup_2006
htmlsql.net
如何将字串 String 转换成整数 int?
int i = Integer.valueOf(my_str).intValue();
int i=Integer.parseInt(str);
如何将字串 String 转换成Integer ?
Integer integer=Integer.valueOf(str);
如何将整数 int 转换成字串 String ?
1.
- PL/SQL的游标类型
百合不是茶
显示游标(静态游标)隐式游标游标的更新和删除%rowtyperef游标(动态游标)
游标是oracle中的一个结果集,用于存放查询的结果;
PL/SQL中游标的声明;
1,声明游标
2,打开游标(默认是关闭的);
3,提取数据
4,关闭游标
注意的要点:游标必须声明在declare中,使用open打开游标,fetch取游标中的数据,close关闭游标
隐式游标:主要是对DML数据的操作隐
- JUnit4中@AfterClass @BeforeClass @after @before的区别对比
bijian1013
JUnit4单元测试
一.基础知识
JUnit4使用Java5中的注解(annotation),以下是JUnit4常用的几个annotation: @Before:初始化方法 对于每一个测试方法都要执行一次(注意与BeforeClass区别,后者是对于所有方法执行一次)@After:释放资源 对于每一个测试方法都要执行一次(注意与AfterClass区别,后者是对于所有方法执行一次
- 精通Oracle10编程SQL(12)开发包
bijian1013
oracle数据库plsql
/*
*开发包
*包用于逻辑组合相关的PL/SQL类型(例如TABLE类型和RECORD类型)、PL/SQL项(例如游标和游标变量)和PL/SQL子程序(例如过程和函数)
*/
--包用于逻辑组合相关的PL/SQL类型、项和子程序,它由包规范和包体两部分组成
--建立包规范:包规范实际是包与应用程序之间的接口,它用于定义包的公用组件,包括常量、变量、游标、过程和函数等
--在包规
- 【EhCache二】ehcache.xml配置详解
bit1129
ehcache.xml
在ehcache官网上找了多次,终于找到ehcache.xml配置元素和属性的含义说明文档了,这个文档包含在ehcache.xml的注释中!
ehcache.xml : http://ehcache.org/ehcache.xml
ehcache.xsd : http://ehcache.org/ehcache.xsd
ehcache配置文件的根元素是ehcahe
ehcac
- java.lang.ClassNotFoundException: org.springframework.web.context.ContextLoaderL
白糖_
javaeclipsespringtomcatWeb
今天学习spring+cxf的时候遇到一个问题:在web.xml中配置了spring的上下文监听器:
<listener>
<listener-class>org.springframework.web.context.ContextLoaderListener</listener-class>
</listener>
随后启动
- angular.element
boyitech
AngularJSAngularJS APIangular.element
angular.element
描述: 包裹着一部分DOM element或者是HTML字符串,把它作为一个jQuery元素来处理。(类似于jQuery的选择器啦) 如果jQuery被引入了,则angular.element就可以看作是jQuery选择器,选择的对象可以使用jQuery的函数;如果jQuery不可用,angular.e
- java-给定两个已排序序列,找出共同的元素。
bylijinnan
java
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
public class CommonItemInTwoSortedArray {
/**
* 题目:给定两个已排序序列,找出共同的元素。
* 1.定义两个指针分别指向序列的开始。
* 如果指向的两个元素
- sftp 异常,有遇到的吗?求解
Chen.H
javajcraftauthjschjschexception
com.jcraft.jsch.JSchException: Auth cancel
at com.jcraft.jsch.Session.connect(Session.java:460)
at com.jcraft.jsch.Session.connect(Session.java:154)
at cn.vivame.util.ftp.SftpServerAccess.connec
- [生物智能与人工智能]神经元中的电化学结构代表什么?
comsci
人工智能
我这里做一个大胆的猜想,生物神经网络中的神经元中包含着一些化学和类似电路的结构,这些结构通常用来扮演类似我们在拓扑分析系统中的节点嵌入方程一样,使得我们的神经网络产生智能判断的能力,而这些嵌入到节点中的方程同时也扮演着"经验"的角色....
我们可以尝试一下...在某些神经
- 通过LAC和CID获取经纬度信息
dai_lm
laccid
方法1:
用浏览器打开http://www.minigps.net/cellsearch.html,然后输入lac和cid信息(mcc和mnc可以填0),如果数据正确就可以获得相应的经纬度
方法2:
发送HTTP请求到http://www.open-electronics.org/celltrack/cell.php?hex=0&lac=<lac>&cid=&
- JAVA的困难分析
datamachine
java
前段时间转了一篇SQL的文章(http://datamachine.iteye.com/blog/1971896),文章不复杂,但思想深刻,就顺便思考了一下java的不足,当砖头丢出来,希望引点和田玉。
-----------------------------------------------------------------------------------------
- 小学5年级英语单词背诵第二课
dcj3sjt126com
englishword
money 钱
paper 纸
speak 讲,说
tell 告诉
remember 记得,想起
knock 敲,击,打
question 问题
number 数字,号码
learn 学会,学习
street 街道
carry 搬运,携带
send 发送,邮寄,发射
must 必须
light 灯,光线,轻的
front
- linux下面没有tree命令
dcj3sjt126com
linux
centos p安装
yum -y install tree
mac os安装
brew install tree
首先来看tree的用法
tree 中文解释:tree
功能说明:以树状图列出目录的内容。
语 法:tree [-aACdDfFgilnNpqstux][-I <范本样式>][-P <范本样式
- Map迭代方式,Map迭代,Map循环
蕃薯耀
Map循环Map迭代Map迭代方式
Map迭代方式,Map迭代,Map循环
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
蕃薯耀 2015年
- Spring Cache注解+Redis
hanqunfeng
spring
Spring3.1 Cache注解
依赖jar包:
<!-- redis -->
<dependency>
<groupId>org.springframework.data</groupId>
<artifactId>spring-data-redis</artifactId>
- Guava中针对集合的 filter和过滤功能
jackyrong
filter
在guava库中,自带了过滤器(filter)的功能,可以用来对collection 进行过滤,先看例子:
@Test
public void whenFilterWithIterables_thenFiltered() {
List<String> names = Lists.newArrayList("John"
- 学习编程那点事
lampcy
编程androidPHPhtml5
一年前的夏天,我还在纠结要不要改行,要不要去学php?能学到真本事吗?改行能成功吗?太多的问题,我终于不顾一切,下定决心,辞去了工作,来到传说中的帝都。老师给的乘车方式还算有效,很顺利的就到了学校,赶巧了,正好学校搬到了新校区。先安顿了下来,过了个轻松的周末,第一次到帝都,逛逛吧!
接下来的周一,是我噩梦的开始,学习内容对我这个零基础的人来说,除了勉强完成老师布置的作业外,我已经没有时间和精力去
- 架构师之流处理---------bytebuffer的mark,limit和flip
nannan408
ByteBuffer
1.前言。
如题,limit其实就是可以读取的字节长度的意思,flip是清空的意思,mark是标记的意思 。
2.例子.
例子代码:
String str = "helloWorld";
ByteBuffer buff = ByteBuffer.wrap(str.getBytes());
Sy
- org.apache.el.parser.ParseException: Encountered " ":" ": "" at line 1, column 1
Everyday都不同
$转义el表达式
最近在做Highcharts的过程中,在写js时,出现了以下异常:
严重: Servlet.service() for servlet jsp threw exception
org.apache.el.parser.ParseException: Encountered " ":" ": "" at line 1,
- 用Java实现发送邮件到163
tntxia
java实现
/*
在java版经常看到有人问如何用javamail发送邮件?如何接收邮件?如何访问多个文件夹等。问题零散,而历史的回复早已经淹没在问题的海洋之中。
本人之前所做过一个java项目,其中包含有WebMail功能,当初为用java实现而对javamail摸索了一段时间,总算有点收获。看到论坛中的经常有此方面的问题,因此把我的一些经验帖出来,希望对大家有些帮助。
此篇仅介绍用
- 探索实体类存在的真正意义
java小叶檀
POJO
一. 实体类简述
实体类其实就是俗称的POJO,这种类一般不实现特殊框架下的接口,在程序中仅作为数据容器用来持久化存储数据用的
POJO(Plain Old Java Objects)简单的Java对象
它的一般格式就是
public class A{
private String id;
public Str