CPT101-Computer Systems 课程笔记
关于汇编的知识请移步文章 Assembly Language
文章目录
- 1. Overview
- 2. I-O Process
-
- 2.1 Input-Process-Output Model
- 2.2 Von Neumann Model
- 2.3 Harvard architecture
- 3. Machine instructions and HLL
-
- 3.1 Translation
- 3.2 Code sharing and reuse
- 4. Data, Information and Knowledge
-
- 4.1 ASCII code
- 4.2 Unicode
-
- 4.2.1 Representation of numbers
- 4.2.2 Representation of integers
- 4.2.3 Representation of real numbers
- 5. Operating systems
-
- 5.1 Functions
- 5.2 Onion ring model
- 6. Client-server computing
- 7. Principal components of a computer
-
- 7.2 Motherboard (主板)
- 7.2 Processor and Registers
- 7.3 Buses
- 7.4 Machine Cycle
-
- 7.4.1 The fetch phase
- 7.4.2 The execution phase
- 7.2 CISC & RISC
- 7.3 Output Hardware
- 7.4 Communications Hardware
- 7.5 Ports
- 7.6 Power Supply
- 8. CPU Registers
-
- 8.1 CPU status flags
- 9. Stack
- 10. Data codes
-
- 10.1 Unsigned integer
- 10.2 Signed integers
- 10.3 Addition
- 10.4 Subtraction
- 10.5 Overflow testing
- 10.6 Floating Point Numbers
- 11.Data storage
-
- 11.1 Main memory
-
- 11.1.1 RAM
- 11.1.2 ROM Chips
- 11.1.3 Other Forms of Memory
- 11.2 Mass storage
-
- 11.2.1 Hard Disk Drives (HDD)
- 11.2.2 Storage Technology
- 11.2.2 Virtual memory
- 11.3 More about Memory
-
- 11.3.1 Address Width
- 11.3.2 Memory mapping
- 11.3.3 Memory Levels
- 12. Building computers from logic
-
- 12.1 Engineering level
- 12.2 Digital Systems
- 12.3 Analog Systems
- 12.4 Boolean operations and Boolean Gates
- 12.5 Selector circuit
- 12.5 Multiplexer, or Data selector
- 12.6 Two-line decoder
- 12.7 How to Implementing a function
1. Overview
We treat Computer Systems as a study of the interaction of hardware and software which determines the performance of computer systems.
Four architectural levels of computer systems
- The assembly language level
- The instruction set architecture level
- The micro architecture level
- The digital logic level
CPU & ALU
- CPU : Central Processing Unit (中央处理器)
- ALU : Arithmetic and Logic Unit (算术逻辑单元) 能实现多组算术运算和逻辑运算的组合逻辑电路。是 CPU 的执行单元,是所有 CPU 的核心组成部分,主要功能是进行二元算术运算。
The components of a computer system
- Processors
- Controllers
- Primary memory (RAM) : 也被称为 main storage(主存),是计算机中存取速度较快的一级存储。他是唯一能被 CPU 直接访问的内存,通常被称为内存。
- Secondary memory : 也被称为 auxiliary storage(辅助存储),如硬盘、U盘等等。
- Peripherals
Types of computers
- Mainframe computers (1960s)
- Supercomputers (1970s)
- Microcomputers (1980s)
- Workstations (1980s)
- Personal computers (1980s)
- Microcontrollers (单片机) (1980s)
- Servers (1980s)
- Chip computer
Computer generations
- Vacuum tube (电子管) (1944 ~ 1958) : 推荐文章
- Transistor (晶体管) (1959 ~ 1963)
- IC (Integrated Circuit 集成电路) (1964 ~ 1970)
- VLSI (Very Large Scale Integration 超大规模集成电路) (1970 ~ now)
Backward (Downward) Compatibility for new hardware (向后/向下兼容)
Most software written for computers with old hardware can be run on computers with newer hardware.
VHDL (硬件描述语言)
- Very high speed integrated circuits Hardware Description Language.
- A programming language to be used to specify both the structure and function of hardware circuits.
- Supports computer simulations as well as providing input to automatic layout packages which arranges the final circuits.
Hierarchy of systems
Computers can always be viewed as hierarchical ordered systems which can be broken down into simple component parts in order to fully understand their operations.
Moore’s Law
The amount of circuitry (number of transistors) which can be placed on a given chip area approximately doubles every two years.
Windowing interfaces ---- WIMPs
A by-product of the microprocessor revolution, which allowed all users to have fast bitmapped graphics on their desks.
Trends of computing
- Scientific computing : Computation
- Business computing : Data
- Personal computing : Interaction
- Pervasive computing : Ubiquity
- Mobile computing : Mobility
2. I-O Process
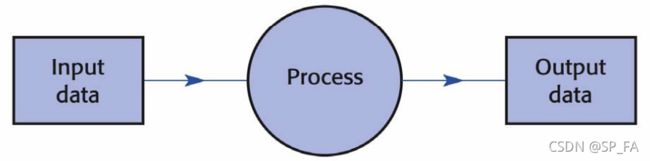
2.1 Input-Process-Output Model
- The Input-Process-Output Model is the fundamental structure of the current generation of digital computers.
- This was an essential scheme of the von Neumann model.
- There are three components required for the implementation of Input-Process-Output and von Neumann models:
- Hardware
- Software
- Data that is being manipulated
2.2 Von Neumann Model
John Von Neumann
An Austria-Hungary-born American mathematician. Made contributions to: quantum physics, functional analysis, set theory, topology, economics, computer science, numerical analysis, hydrodynamics.
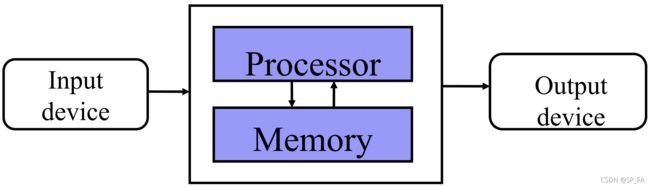
- The computer is a general-purpose machine controlled by an executable program.
- A program is a list of instructions used to direct a task.
- Both program and data are held in computer’s memory and both represented by binary codes.
- The fact that memory is re-writeable makes a von Neumann machine especially powerful.
- A processor is an active part of the machine that executes the program instructions.
Von Neumann bottleneck
CPU is continuously forced to wait for vital data (and instructions) to be transferred to or from memory.
指令和数据放在一起的后果是取指令和取数据不能同时进行,否则会引起访存的混乱。发展到今天,CPU的运算速度已经远远超过了访存速度,因此CPU必须浪费时间等数据。
由于指令与数据放在同一内存带来的CPU利用率(吞吐率)限制就是冯诺依曼瓶颈。
实际上,绝大多数现代计算机使用的是所谓的 “Modified Harvard Architecture”,指令和数据共享同一个 address space,但缓存是分开的。在内存里,指令和数据是在一起的。而在CPU内的缓存中,还是会区分指令缓存和数据缓存,最终执行的时候,指令和数据是从两个不同的地方出来的。可以理解为在CPU外部,采用的是冯诺依曼模型,而在CPU内部用的是哈佛结构。
————————————————
原文链接
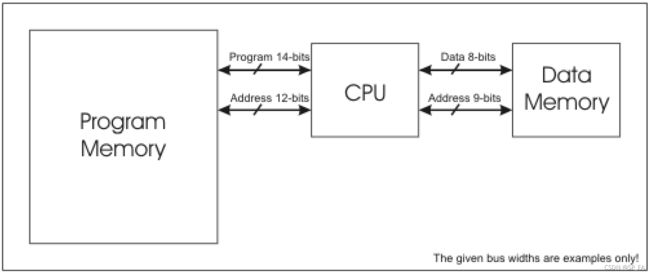
2.3 Harvard architecture
- Separates data from programs.
- Requires different memories and access buses for programs and data.
为什么电脑还沿用冯·诺伊曼结构而不使用哈佛结构
3. Machine instructions and HLL
Semantic gap
The term expresses the enormous difference between the way human languages expressing ideas and actions and the way computer instructions representing data processing activities.
3.1 Translation
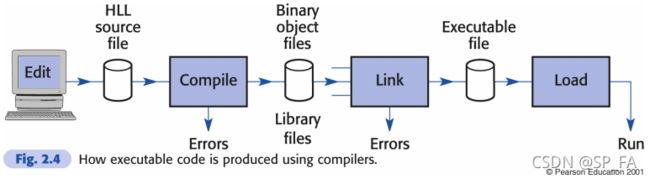
Translation is done by special programs such as:
Compilers: translating HLL instructions into machine code (sequence of instructions) before the code can be run on the machineAssemblers: translating mnemonic form of machine instructions (like MOV, ADD, etc) into their binary codesInterpreters: translating HLL instructions into machine code on-the-fly (while the program is running)
Linking
- Big programs usually are divided into several separate parts or modules
- Each module has to be designed, coded and compiled
- There are frequent occasions when code in one module needs to reference data or subroutines in another module
- A compiler can translate a module into binary codes, but it cannot resolve those references to other modules
- Those external references remain symbolic after the compilation, until the linker gets to work
- The linker is to join together all the binary parts
- The linker will report errors if it cannot find the module or code referred to by those external references
Library files
- Translated object code
- Provide many functions for programmers, but are only usable if linked into your code
- In Unix : Directories
/liband/usr/libe/ - In Windows : DLL files
Interpreters ---- alternative way of running HLL programs
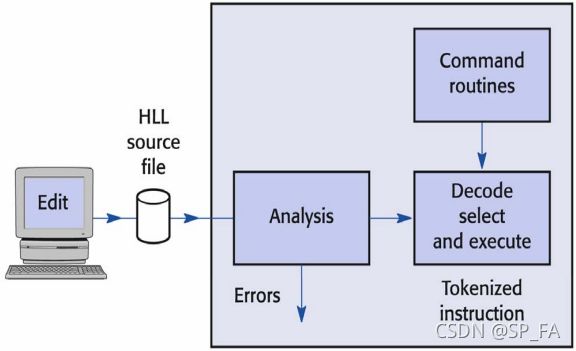
- Instructions are converted into an intermediate form, consisting of tokens
- In Java, tokens such as : static, boolean, file, string, void ,return
- Tokens are then passed to the decoder, which selects appropriate routines for execution.
- The processes of translation and execution are interlaced
Java compilers and interpreters
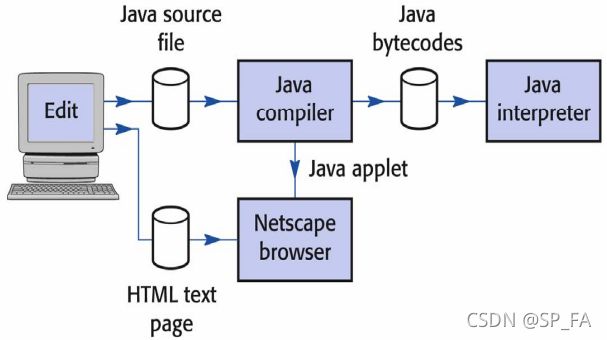
Interpreters vs. Compilers
- Execution of compiled code is much faster than execution of interpreted code
- Interpreters are more suitable for rapid prototyping and for other situations when a program is frequently modified
- Interpreters are more accurate in terms of error reporting
- Interpretation can provide uniform execution environment across several diverse computers (Portable)
Interpreters as Virtual Machines
- Interpreters are somewhat similar to the computer hardware (take one instruction at a time and execute it)
- Because of that sometimes they are referred to as a virtual machine (JVM)
3.2 Code sharing and reuse
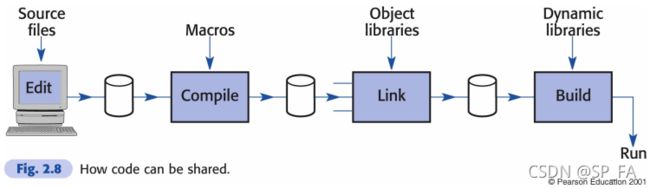
How to reuse existing proven software when developing new systems?
- Source-level subroutines and macro libraries
- Pre-translated re-locatable binary librarie
- Dynamic libraries and dynamic linking
Source-level subroutines and macro libraries
Take copies of the library routines, edit them into your new code and then translate the whole together
Disadvantages:
- Who owned the code?
- Who should maintain it?
Pre-translated relocatable binary libraries
Libraries are pre-translated into relocatable binary code, can be linked into your new code, but not altered.
Disadvantage : Each program is to have a private copy of the subroutines, wasting valuable memory space, and swapping time, in a multitasking system.
Dynamic libraries and dynamic linking
Load a program which uses “public” routines already loaded into memory, the memory-resident libraries are mapped, through the memory management system to control access and avoid multiple code copies.
Successful through Microsoft’s ActiveX standard.
4. Data, Information and Knowledge
Data: raw facts, figures, measurementsInformation: data organized into useful representationKnowledge: application of reasoned analysis of information
Measurement of Information
In 1948, motivated by the problem of efficiently transmitting information over a noisy communication channel, Claude Shannon introduced a revolutionary new probabilistic way of thinking about communication and simultaneously created the first truly mathematical theory of entropy. His ideas created two main lines of development: information theory and coding theory. Entropy of an event X is related to p(X).
如何理解信息熵
Alphanumeric codes
ASCII: American Standard Code for Information interchange (7-bit code) and its extensions (8-bit codes)EBCDIC: Extended Binary Coded Decimal Interchange Code (8-bit code). (IBM mainframe computersUnicode: Recent 16-bit standard
4.1 ASCII code
Only half of possible byte patterns is used. The second half is used in the 8-bit extension to represent the codes of additional symbols, line shapes, foreign letters, etc.
The table is divided into two classes of codes
- Printing characters : Produce output on the screen or on a printer.
- Control characters : To control the position of output on the screen or paper, to cause some action to occur or to communicate status between the computer and an I/O device
Limitations of ASCII code
- Too limited for the display requirements of modern Windows-based word-processors.
- The requirement of global software market for handling international character sets
4.2 Unicode
Standard includes the European alphabetic scripts, Middle Eastern right-to-left scripts, and scripts of Asia, Africa and America, ideographic characters of China, Japan, etc
In a Java program, if you want to show some Chinese characters, you have to use their Unicode representations
4.2.1 Representation of numbers
Any representation of numbers capable of supporting arithmetic manipulation has to deal with both integers and real values, positive and negative.
4.2.2 Representation of integers
使用补码表示整数 (Two’s complement)
原码,反码和补码
4.2.3 Representation of real numbers
IEEE 754 standard :
- The most widely-used standard for floating-point computation.
- defines formats for representing floating-point numbers, special values, and a set of floating-point operations that operate on these values.
IEEE 754 浮点数标准详解
5. Operating systems
5.1 Functions
Functions of OS : to interpret and carry out commands issued by users of the computer or application programs running on the computer.
Purposes
- Management : To control and operate hardware in a efficient way.
- Provide functionalities : To allow the user efficient, fair, protected access to the facilities of the machine (Interaction with the user)
5.2 Onion ring model
To realise the purposes of an operating system, the software system is often arranged in multiple layers.
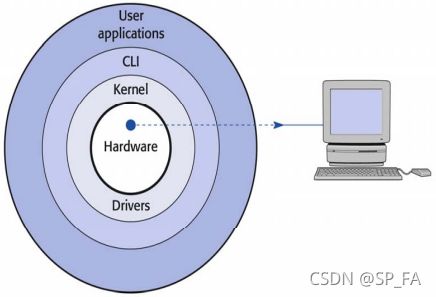
Core of operating system: dealing directly with the hardware.
kernel : device drivers, memory allocator, etc.
CLI (命令行界面) : provide user accessibilities to the system
Many modern operating systems also allow for the simultaneous processing of multiple programs and support for multiple users.
6. Client-server computing
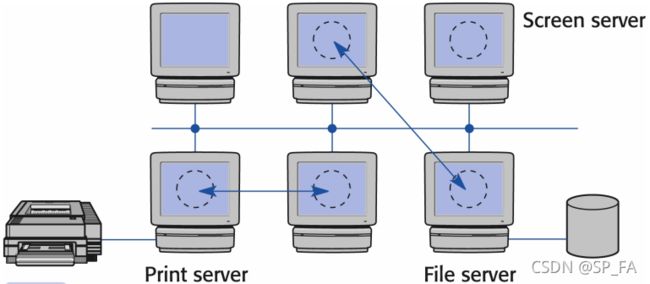
Client : The originator of a request
Server : The supplier of the service
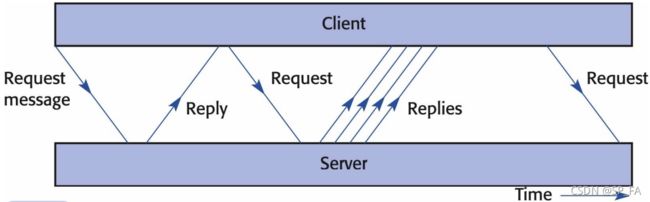
- Client starts the interaction by sending a request message to the server
- Server responds by sending replies back
7. Principal components of a computer
These are the minimum set of components for a working digital computer
7.2 Motherboard (主板)
7.2 Processor and Registers
Processor :
- arithmetic / logic unit (ALU)
- control unit : part of a CPU responsible for performing the machine cycle
CPU、Processor、Core的区别
Registers :
small block of fast memory, temporarily store for data and address variables
- CPU registers
- Program counter (PC) or Instruction Pointer (IP) : contains the address of the next instruction to execute
- Instruction register (IR) : part of a CPU control unit that stores an instruction
- Accumulator (AX, EAX in Pentium) : General purpose data register
- Memory address register (MAR) : Temporarily holds address of the memory location during a bus transfer
- MBR (主引导目录 or 主引导扇区) : 计算机开机以后访问硬盘时所必须要读取的第一个扇区。主引导目录(MBR)结构及作用详解
Coprocessor : microprocessors performing specialized functions that CPU cannot perform or cannot perform as well and as quickly
80486CPU 之前有协处理器,那时 CPU 算力较弱,现在 PC 一般不存在协处理器了。
7.3 Buses
On the motherboard, all the components are interconnected by buses (“signal highways”). A bus is a bundle of conductors, wires, or tracks. Typically, there are address, data and control buses, each including several signal lines
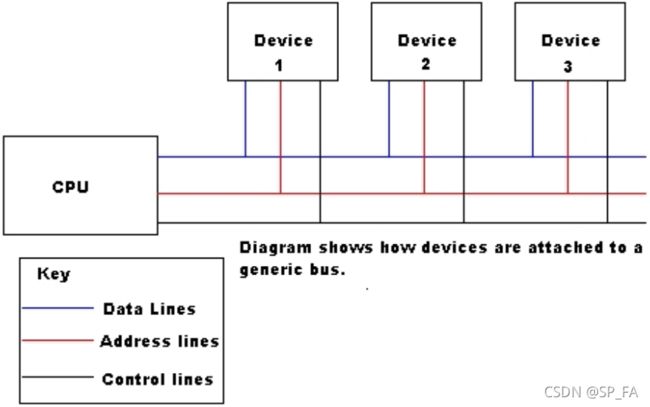
Each hardware unit is connected to all these buses. It is a simple way of building up complex systems in which each unit can communicate with each other. Little disruption when plugging in new units and swapping out failed units. The connected devices can have access to any signal line they require
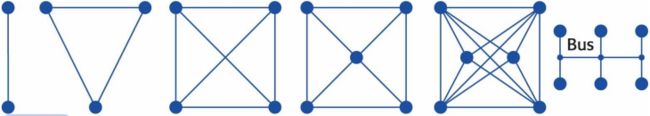
The number of wires required for a bus is much smaller than that for point-to-point connections. But a bus can only transfer one item of data at a time, termed the Bus Bottleneck, it cannot be solved by simply increasing the speed of a processor.
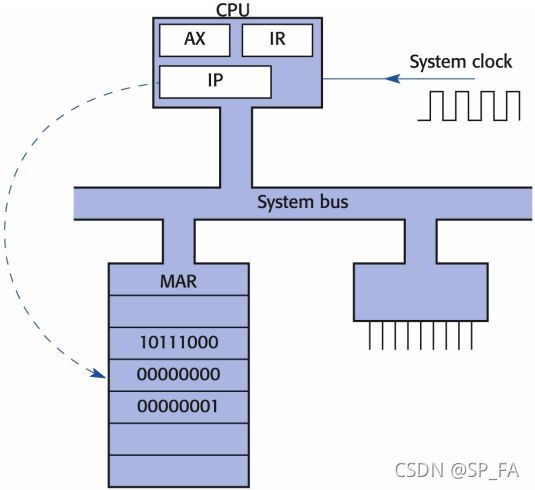
7.4 Machine Cycle
The fetch-execute cycle or machine cycle is the sequence whereby each instruction of the program is executed
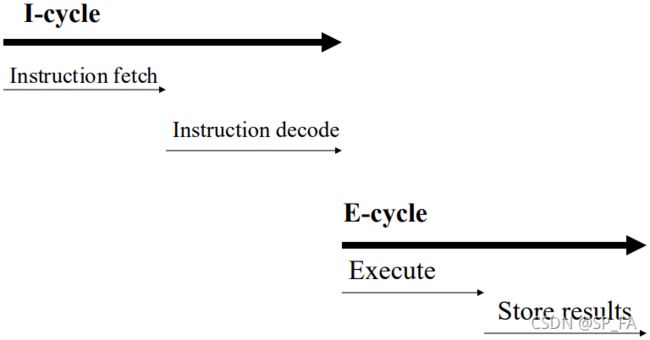
- Fetch the instruction from memory. Brings the instruction into the instruction register so that it can be decoded and executed
- Decode the instruction
- Read the effective address from memory if the instruction has an indirect address
- Execute the instruction
- Store the results
7.4.1 The fetch phase
- The address in IP register is copied onto the address bus and further to MAR register.
- IP is incremented ready for the next cycle. IP now points to the next location in the program memory.
- Memory selects location and copies the content onto the data bus.
- CPU copies the instruction code from the data bus into IR.
- Decoding of the instruction starts.
7.4.2 The execution phase
Execute phase depends on the type of instruction.
e.g. MOV AX, 256
- IP is copied to address bus and latched into memory.
- IP is incremented.
- The value selected in memory is copied onto the data bus
- CPU copies the value from the data bus into AX.
7.2 CISC & RISC
CISC: complex instruction setRISC: reduced instruction set
CISC 和 RISC 的区别
7.3 Output Hardware
Hardcopy output: graphics, lettersSoftcopy output: video, audio
7.4 Communications Hardware
- modems
- hubs
- etc.
7.5 Ports
Parallel port: printers, some scanners …Serial port: modems, mice
串并口
USB (Universal Serial Bus): replaced earlier interfaces, such as serial and parallel ports
7.6 Power Supply
protected by power surge protector or uninterrupted power supply unit (UPS)
8. CPU Registers
8.1 CPU status flags
EFLAG: The Flag register holds the CPU status flags. It is a way of communication between one instruction and the subsequent instructions.Status flag: The status flags are separate bits inEFLAGwhere information on important arising conditions such asoverfloworcarry bitsis recorded.
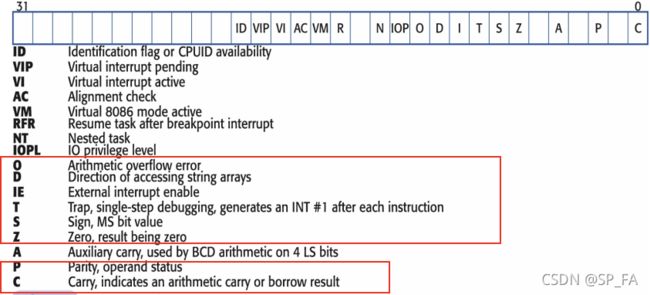
How CPU flags are operated
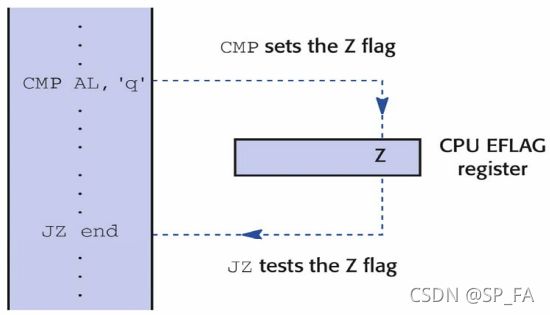
9. Stack
数据结构-栈
The order of storing and retrieving the values for the stack can be described as LIFO (last in, first out).
10. Data codes
10.1 Unsigned integer
- Unsigned binary representation : just store any whole number in its binary representation
- BCD : 类似于十六进制,用四位二进制表示一位十进制数
10.2 Signed integers
- 10’s complementary coding : 使得计算机可以用加法代替减法。In 10’s complement system the range is
unevenly divided between positive and negative integers 4-digit complement system represents all the integer values between -5000 and 4999 - 见 4.2.2
10.3 Addition
Operation of addition for n-digit numbers represented by 10’s complementary convention:
- Addition modulo: 1 0 ⋯ 0 ⏟ n \begin{matrix} 1\underbrace{0\cdots0} \\ n \end{matrix} 1 0⋯0n
- Use existing addition procedure, except that any carry beyond the specified number of digits (n) is “thrown away”.
10.4 Subtraction
To subtract B B B from A A A one may first compute negated B B B and add it to A A A. Given B in 10’s complement, how to
compute − B -B −B:
- Just subtract B from 1 0 ⋯ 0 ⏟ n \begin{matrix} 1\underbrace{0\cdots0} \\ n \end{matrix} 1 0⋯0n
10.5 Overflow testing
If both inputs to an addition have the same sign, and the output sign is different, overflow has occurred.
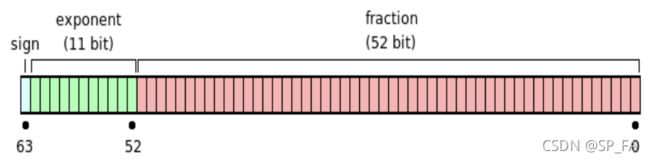
10.6 Floating Point Numbers
浮点数表示法详解
Exponent biasing
The exponent is biased by 28-1-1, that is, biased by 127. Exponents in the range -127 to +127 are
representable. e=128 reserved for NaN, infinity
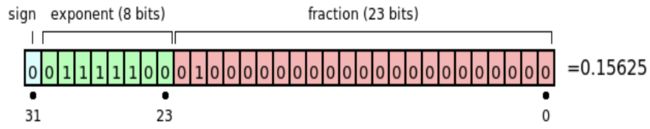
Special cases (e = 128)
- If exponent is 0 0 0 and fraction is 0 0 0, the number is ± 0 \pm0 ±0 (depending on the sign bit)
- If exponent = 2 8 − 1 = 2^8− 1 =28−1 and fraction is 0 0 0, the number is ± \pm ±infinity (again depending on the sign bit)
- If exponent = 2 8 − 1 = 2^8− 1 =28−1 and fraction is not 0 0 0, the number being represented is NaN
11.Data storage
Two main types of storage in a computer:
- Main memory
- Mass storage
11.1 Main memory
It refers to physical memory that is internal to the computer. The computer can manipulate only data that is
inside the main memory.
- It determines how many programs can be executed at one time
- How much space can be allocated to a program
11.1.1 RAM
Random Access Memory. The name is to set it apart from serial tape storage with which you cannot access data stored in the second or following blocks without going through the first block of data.
The memory can be seen as a set of numbered storage elements, called words, each of which contains some
information. Each word is numbered with its address. Any word of memory can be accessed “without touching” the preceding words (Random Access) so the access time is the same for all the stored items.
There are two basic types of RAM :
- Dynamic RAM (DRAM)
- Cheaper, but slower
- Implemented via capacitors
- DRAM needs to be refreshed (Real capacitors leak charge, then stored data eventually fades, to retain data, capacitor charge has to be refreshed periodically)
- Static RAM (SRAM)
- Faster, but more expensive
- Implemented via flip-flops
- No need for refreshing
Both types of RAM are volatile, they lose their contents when the power is turned off.
11.1.2 ROM Chips
Read-only memory. Software stored inside also known as firmware. Helps boot up the system.
BIOS : Basic Input Output System
11.1.3 Other Forms of Memory
- Cache memory (cash) : quick access memory, internal or external to the processor. Between the processor and RAM. Including simultaneous read / write
- Video memory (VRAM)
11.2 Mass storage
It refers to various techniques and devices for storing a large amount of data. Unlike main memory, mass storage devices retain data even when the computer is turned off.
11.2.1 Hard Disk Drives (HDD)
Hard disk drives are the most important types of permanent storage used in computers. Hard disks differ from the other mass storage devices in three ways:
- Size (usually larger)
- Speed (usually faster)
- Permanence (usually fixed in computer and not removable)
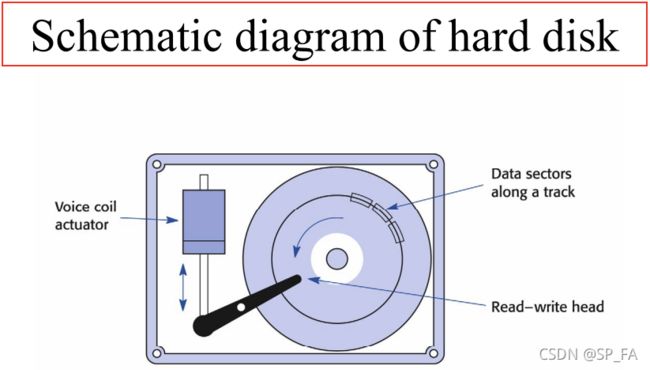
Each disk platter has its information recorded on both surfaces, each platter has two heads.
The information is recorded in concentric circles called tracks. Each track is broken down into
smaller pieces called sectors, each of which holds 512 bytes of information.
磁盘的结构
Addressing
CHS: Cylinder, Head, Sector system, can be mapped ontoLBA.LBA: Large Block Addressing, by absolute number of a sector
Assume that A piece of information needs to be read
- The first step is to figure out where on the disk to look for the needed information
- The location on the disk → \rightarrow → address expressed either in terms of
CHSorLBA - A request is sent to the drive over the disk drive interface giving it this address and asking for the sector to be read
Disk cache
A portion of main memory used as a buffer to temporarily hold data for the disk. Because disks write operations are clustered, some data written out may be needed again (The data are retrieved rapidly from the disk cache instead of slowly from disk)
11.2.2 Storage Technology
Retrieving files into RAM is called reading. Copying data from RAM onto a secondary storage device is called writing
11.2.2 Virtual memory
It is the use of low-level memory to ‘expand’ high-level (main) memory. It provides a convenient expansion of main memory by ‘overflowing’ data and program code onto magnetic disk
The area on disk reserved for this purpose is known as the swap area
Improves flexibility but is slower than RAM to which the processor has direct access
Virtual Memory Management
Main memory is divided into frames, often 4KB. The executable program is similarly divided into frame-sized chunks known as pages. When a program is invoked not all the pages are loaded into main memory, only sufficient to get it started. The rest are copied into the swap area
When an instruction is needed from a page not yet in the main memory it is loaded from the disk. If no empty frames exist at the moment the least used frame is freed to allow the new pages to be loaded. (This is called swapping)
Virtual Memory Addressing
Within an user program addresses are in a form of 32 bit logical address.
In the case of 4KB paging system : – The lower 12 bits are ‘address within a page’. The upper 20 bits serve as the ‘page number’.
Memory Management Unit maps logical addresses into references to frame numbers and addresses within the frames
11.3 More about Memory
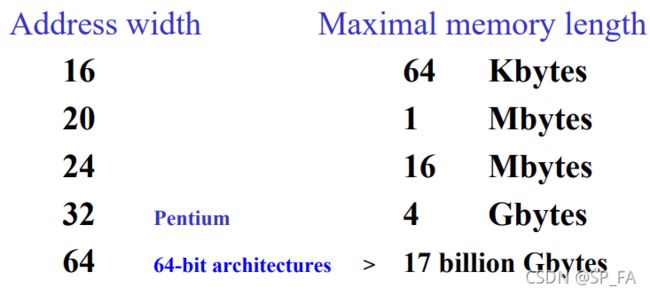
11.3.1 Address Width
Maximal memory length depends on address width.
Address width is determined by:
- The number of bits in the CPU address registers such as
IP,MAR - The number of lines in the address bus
11.3.2 Memory mapping
When the CPU sends out an address, a part of the address locates the correct chip, another part specifies an address within the correct chip

11.3.3 Memory Levels
- Registers
- Cache memory (Level 1 and Level 2)
- Main memory
- Mass storage
Why we need memory levels?
- To keep up with the demands of faster CPUs.
- To limit system cost.
- To cope with ever-expanding software systems.
Registers
Registers are the memory cells which are core part of the processor itself. It has very fast access
Cahe memory
A memory placed between CPU and main memory. Contains a copy of the portion of main memory. The aim is to maintain in fast cache the currently active sections of code and data. Processor when needs some information first checks cache. If not found in cache, the block of memory containing the needed information is moved into the cache.
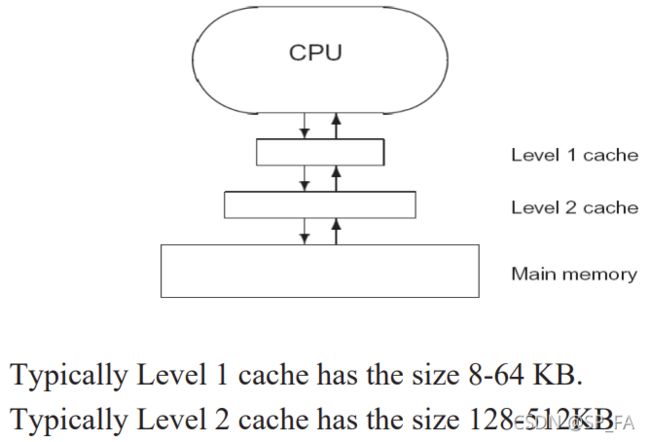
The idea of cache memory exploits Localisation of Memory Access principle: Computers tend to spend periods of time accessing the same locality of memory. Therefore, A portion of code or data which require access needs to be loaded into the fastest memory nearest to CPU. Other sections of the program and data can be held in readiness lower down the memory hierarchy.
12. Building computers from logic
Computer systems may be described at different levels of understanding. At the architectural level the computer is described as a machine for executing instructions.
12.1 Engineering level
Engineering model of the computer represents the machine as a complex electrical circuit. Within the circuit there are a large number of physical connections, along each of which a current may flow during the operation of the machine.
12.2 Digital Systems
Presence of a current is used to represent transmission of the binary digit 1, while absence of a current represents a value 0
This kind of circuit is called digital electronic circuit, because the relevant characteristic is the presence or absence of current (digit 1 or 0), rather than the amount of current flowing
12.3 Analog Systems
continuously variable values, along a range, such as temperature and pressure values
traditional analog recording devices are humidity recorders, mercury thermometers and, pressure gauges
standard telephone lines transmit analog signals
12.4 Boolean operations and Boolean Gates
All operations that computers perform may be defined in terms of basic boolean functions, operating on bits
The digital electronic circuits and their components can be built from the devices implementing basic boolean operations – boolean gates (logic gates)
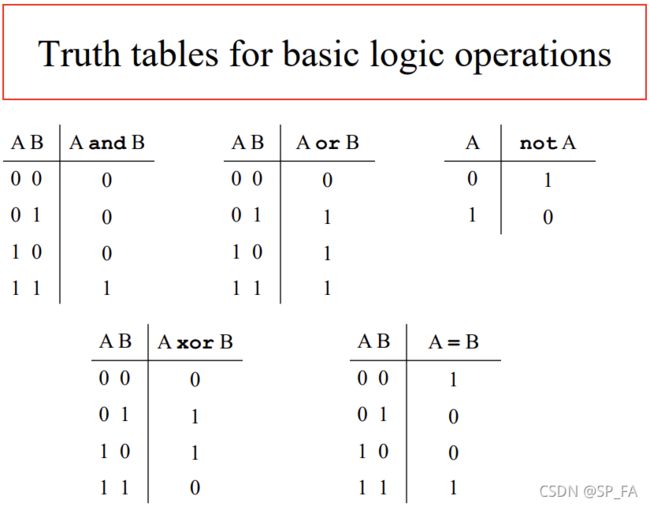

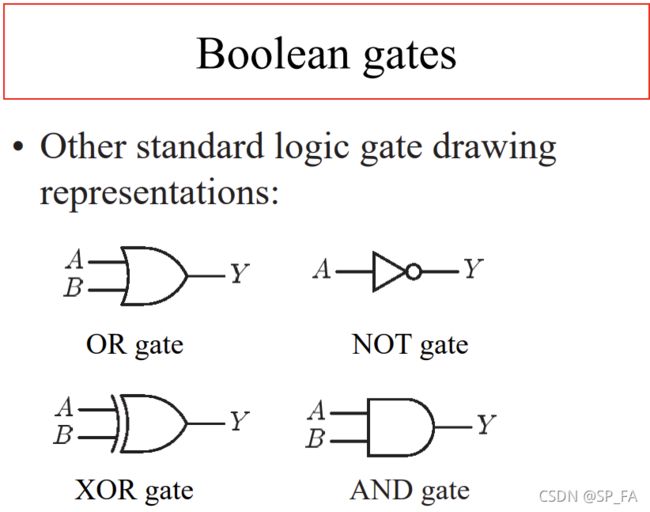
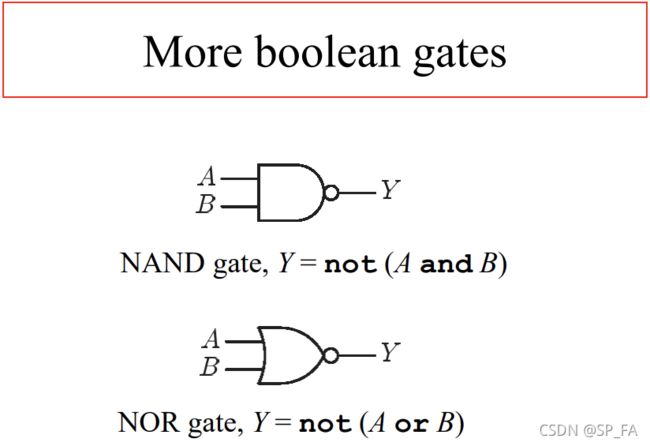
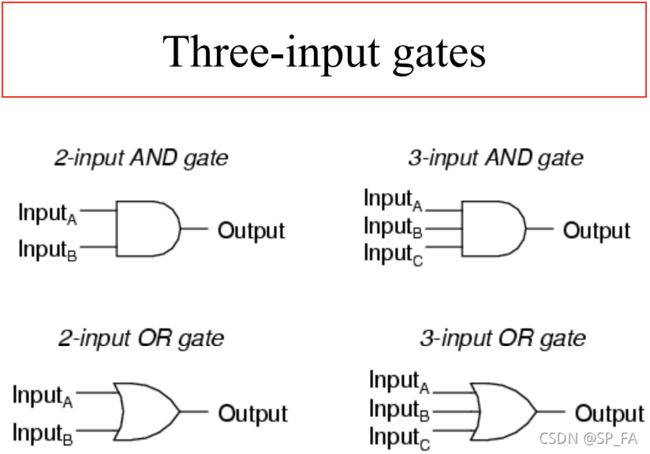
Boolean circuits
Elementary boolean gates can be combined into boolean circuits, implementing more complex boolean functions (operations). In fact, any boolean function can be implemented with this set of basic boolean gates
12.5 Selector circuit
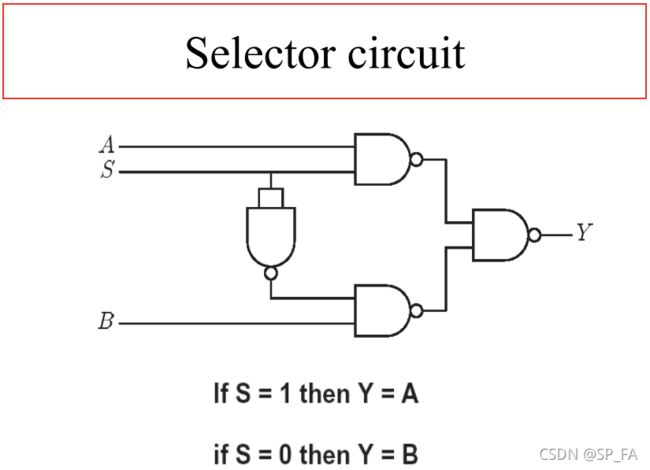
a definition of the function : Y = ( S ∧ A ) ∨ ( ¬ S ∧ B ) Y=(S\land A)\lor(\lnot S\land B) Y=(S∧A)∨(¬S∧B)
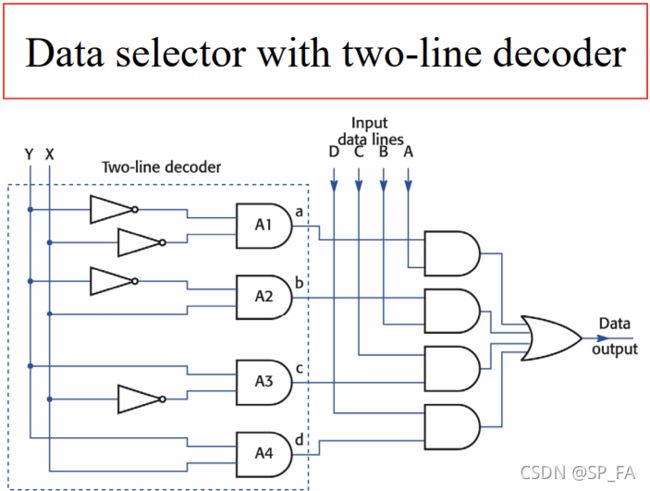
12.5 Multiplexer, or Data selector
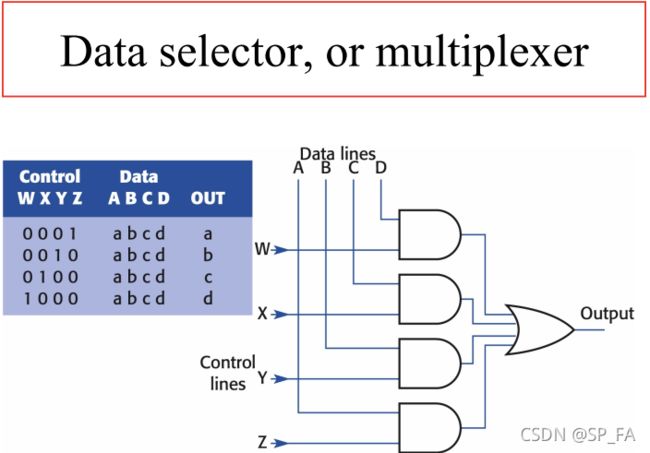
The circuit is a straightforward implementation of the function : O = ( A ∧ Z ) ∨ ( B ∧ Y ) ∨ ( C ∧ X ) ∨ ( D ∧ W ) O=(A\land Z)\lor(B\land Y)\lor(C\land X)\lor(D\land W) O=(A∧Z)∨(B∧Y)∨(C∧X)∨(D∧W)
The problem with the circuit :
- if more than one control line has the signal 1, the circuit does not behave as a selector
So we need Two-line decoder
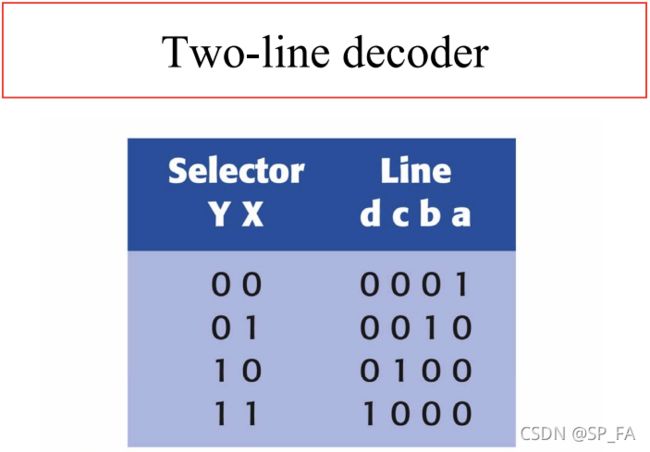
12.6 Two-line decoder
12.7 How to Implementing a function
Given a truth table for a logic function, to implement the function by a logic circuit one may proceed as follows :
- Implement detectors (using AND/NOT gates) for all input patterns on which the function gives the output 1
- Connect the outputs of all detectors to the inputs by an OR gate