AOSP ~ RK3568 ANDROID11 增加分区
客户要求保存一段数据,可写入读取,恢复出厂后数据也不会被删除。增加private分区,专门给客户app使用
增加分区有俩种方式,俩种方式不能同时使用
方法一类似于system分区,方法二类似于recovery分区
通过升级工具烧录镜像的方式
下面以一个实例来说明,假设需要增加一个oem分区,大小为 8MB,升级固件时,需要升级工具把oem.img文件写入到oem分区。
oem.img文件可以是任意格式的文件,比如一个ext4 的镜像文件,或者一个视频文件,或者一个资源文件等等,大小不能超过分区定义的大小。
下面是修改步骤:
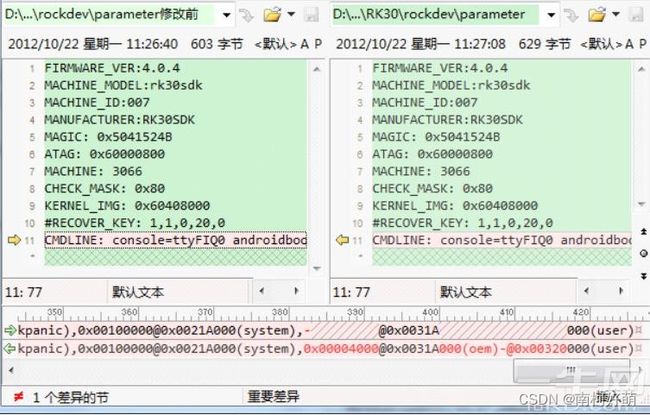
- 打开parameter文件
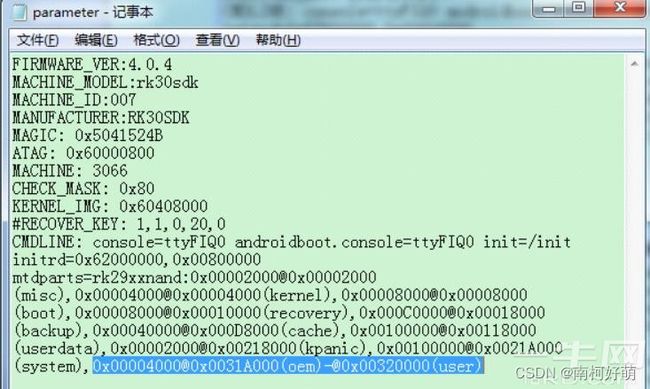
- 在mtdparts里面加入oem分区
参考文档“Rockchip Parameter File Format Ver1.2.pdf”,oem分区 8MB,那么大小就是 0x4000 个扇区,将oem分区加在system分区之后。
-
在package-file文件中加入oem分区对应的烧写文件配置
如果不需要工具升级oem.img文件到oem分区,跳过这一步。这里我们配置成 ,把需要写到oem分区的文件改名为oem.img,拷贝到Image目录即可。
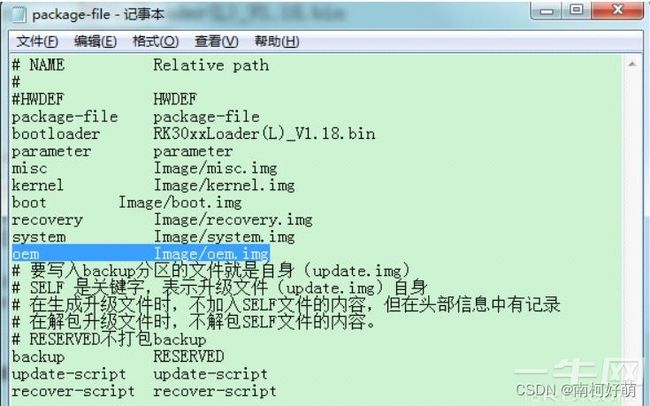
-
双击文件“mkupdate.bat”生成update.img固件,这个固件就包含了oem分区的配置信息和需要烧写到oem分区的文件。
-
开发工具配置,打开工具RKAndroidTool.exe,增加oem分区配置
如果不需要工具升级oem.img文件到oem分区,跳过这一步。
原来的界面:
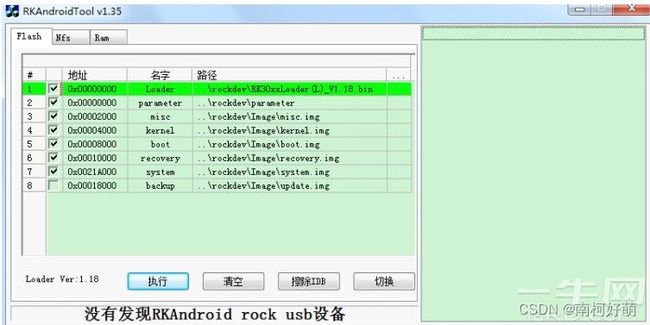
在分区表空白处单击右键,再弹出的对话框中选择“添加项”
RECOVERY代码中格式化后挂载的方式(不需要烧录镜像文件)
1. 修改分区文件
parameter.txt 使用的是脚本方式编译而成,所以需要修改对应的脚本配置文件
device/rockchip/common/build/rockchip/RebuildParameter.mk
partition_list := $(partition_list),backup:384M,cache:$(BOARD_CACHEIMAGE_PARTITION_SIZE),metadata:16M
+partition_list := $(partition_list),private:4M
ifeq ($(strip $(BUILD_WITH_GOOGLE_FRP)), true)
partition_list := $(partition_list),frp:512K
endif
增加private分区,大小4M。
2. 修改fstab文件
修改挂载分区分拣fstab,fstab.rk30board同样是使用脚本方式编译而成,需要修改对应的脚本文件
device/rockchip/common/scripts/fstab_tools/fstab.in
完整文件如下
# Android fstab file.
#
# The filesystem that contains the filesystem checker binary (typically /system) cannot
# specify MF_CHECK, and must come before any filesystems that do specify MF_CHECK
${_block_prefix}system /system ext4 ro,barrier=1 ${_flags_vbmeta},first_stage_mount${_flags_avbpubkey}
${_block_prefix}vendor /vendor ext4 ro,barrier=1 ${_flags},first_stage_mount
${_block_prefix}odm /odm ext4 ro,barrier=1 ${_flags},first_stage_mount
${_block_prefix}product /product ext4 ro,barrier=1 ${_flags},first_stage_mount
${_block_prefix}system_ext /system_ext ext4 ro,barrier=1 ${_flags},first_stage_mount
/dev/block/by-name/metadata /metadata ext4 nodev,noatime,nosuid,discard,sync wait,formattable,first_stage_mount,check
/dev/block/by-name/misc /misc emmc defaults defaults
/dev/block/by-name/cache /cache ext4 noatime,nodiratime,nosuid,nodev,noauto_da_alloc,discard wait,check
+/dev/block/by-name/private /private ext4 noatime,nodiratime,nosuid,nodev,noauto_da_alloc,discard wait,check
/devices/platform/*usb* auto vfat defaults voldmanaged=usb:auto
# For sata
/devices/platform/*.sata* auto vfat defaults voldmanaged=sata:auto
# For pcie ssd
/devices/platform/*.pcie* auto vfat defaults voldmanaged=pcie:auto
/dev/block/zram0 none swap defaults zramsize=50%
# For sdmmc
/devices/platform/${_sdmmc_device}/mmc_host* auto auto defaults voldmanaged=sdcard1:auto
# Full disk encryption has less effect on rk3326, so default to enable this.
/dev/block/by-name/userdata /data f2fs noatime,nosuid,nodev,discard,reserve_root=32768,resgid=1065 latemount,wait,check,fileencryption=aes-256-xts:aes-256-cts:v2+inlinecrypt_optimized,keydirectory=/metadata/vold/metadata_encryption,quota,formattable,reservedsize=128M,checkpoint=fs
# for ext4
#/dev/block/by-name/userdata /data ext4 discard,noatime,nosuid,nodev,noauto_da_alloc,data=ordered,user_xattr,barrier=1 latemount,wait,formattable,check,fileencryption=software,quota,reservedsize=128M,checkpoint=block
参考cache分区就可以
3. 修改fstab文件修改recovery.fstab,文件目录device/rockchip/rk356x/项目/recovery.fstab
# Android fstab file.
#
/dev/block/platform/ff0f0000.dwmmc/by-name/user /mnt/internal_sd vfat defaults defaults
/dev/block/mmcblk0p1 /mnt/external_sd vfat /dev/block/mmcblk0 defaults
/dev/block/by-name/system /system ext4 defaults defaults
/dev/block/by-name/vendor /vendor ext4 defaults defaults
/dev/block/by-name/odm /odm ext4 defaults defaults
/dev/block/by-name/product /product ext4 defaults defaults
/dev/block/by-name/system_ext /system_ext ext4 defaults defaults
/dev/block/by-name/cache /cache ext4 defaults defaults
/dev/block/by-name/metadata /metadata ext4 defaults defaults
+/dev/block/by-name/private /private ext4 defaults defaults
/dev/block/by-name/userdata /data f2fs defaults defaults
/dev/block/by-name/cust /cust ext4 defaults defaults
/dev/block/by-name/custom /custom ext4 defaults defaults
/dev/block/by-name/radical_update /radical_update ext4 defaults defaults
/dev/block/by-name/misc /misc emmc defaults defaults
/dev/block/by-name/uboot /uboot emmc defaults defaults
/dev/block/by-name/charge /charge emmc defaults defaults
/dev/block/by-name/resource /resource emmc defaults defaults
/dev/block/by-name/parameter /parameter emmc defaults defaults
/dev/block/by-name/boot /boot emmc defaults defaults
/dev/block/by-name/recovery /recovery emmc defaults defaults
/dev/block/by-name/backup /backup emmc defaults defaults
/dev/block/by-name/frp /frp emmc defaults defaults
/dev/block/by-name/trust /trust emmc defaults defaults
/dev/block/by-name/baseparamer /baseparamer emmc defaults defaults
/dev/block/by-name/vbmeta /vbmeta emmc defaults defaults
/dev/block/by-name/dtbo /dtbo emmc defaults defaults
/dev/block/by-name/vendor_boot /vendor_boot emmc defaults defaults
4. 修改挂载目录对应权限,由于5.1以后的系统启动了selinux,所以5.1以后的系统在recovery格式化这种方式,需要给新加分区设置相关属性
system/core/rootdir/init.rc
on post-fs-data
mark_post_data
# Start checkpoint before we touch data
exec - system system -- /system/bin/vdc checkpoint prepareCheckpoint
# We chown/chmod /data again so because mount is run as root + defaults
chown system system /data
chmod 0771 /data
# We restorecon /data in case the userdata partition has been reset.
restorecon /data
# Make sure we have the device encryption key.
installkey /data
+ mkdir /private 0777 system system
# Start bootcharting as soon as possible after the data partition is
# mounted to collect more data.
mkdir /data/bootchart 0755 shell
修改private目录权限,app对目录可读写。
private目录添加属性
===================================================================
--- device/rockchip/common/sepolicy/vendor/device.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/device.te (revision 418)
@@ -13,6 +13,7 @@
type baseparameter_block_device, dev_type;
type sensor_device, dev_type;
type e2fsck_cache_block_device, dev_type;
+type e2fsck_private_block_device, dev_type;
type e2fsck_metadata_block_device, dev_type;
type e2fsck_system_block_device, dev_type;
type e2fsck_frp_block_device, dev_type;
Index: device/rockchip/common/sepolicy/vendor/file_contexts
===================================================================
--- device/rockchip/common/sepolicy/vendor/file_contexts (revision 417)
+++ device/rockchip/common/sepolicy/vendor/file_contexts (revision 418)
@@ -74,6 +74,7 @@
/dev/block/by-name/vendor u:object_r:system_block_device:s0
/dev/block/by-name/oem u:object_r:e2fsck_oem_block_device:s0
/dev/block/by-name/cache u:object_r:e2fsck_cache_block_device:s0
+/dev/block/by-name/private u:object_r:e2fsck_private_block_device:s0
/dev/block/by-name/metadata u:object_r:metadata_block_device:s0
/dev/block/by-name/userdata u:object_r:userdata_block_device:s0
/dev/block/by-name/boot u:object_r:boot_block_device:s0
Index: device/rockchip/common/sepolicy/vendor/fsck.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/fsck.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/fsck.te (revision 418)
@@ -1,3 +1,4 @@
allow fsck e2fsck_oem_block_device:blk_file rw_file_perms;
allow fsck e2fsck_cache_block_device:blk_file rw_file_perms;
+allow fsck e2fsck_private_block_device:blk_file rw_file_perms;
allow fsck e2fsck_frp_block_device:blk_file rw_file_perms;
Index: device/rockchip/common/sepolicy/vendor/init.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/init.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/init.te (revision 418)
@@ -38,6 +38,7 @@
allow init frp_block_device:lnk_file { relabelto };
allow init metadata_block_device:lnk_file { relabelto };
allow init e2fsck_cache_block_device:lnk_file { relabelto };
+allow init e2fsck_private_block_device:lnk_file { relabelto };
allow init system_file:system { module_load };
allow init debugfs:dir mounton;
allow init configfs:file rw_file_perms;
Index: device/rockchip/common/sepolicy/vendor/recovery.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/recovery.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/recovery.te (revision 418)
@@ -36,6 +36,9 @@
allow recovery e2fsck_cache_block_device:blk_file ioctl;
allowxperm recovery e2fsck_cache_block_device:blk_file ioctl { BLKPBSZGET };
1. allow recovery e2fsck_private_block_device:blk_file ioctl;
2. allowxperm recovery e2fsck_private_block_device:blk_file ioctl { BLKPBSZGET };
3. allow shell rootfs:file { entrypoint read};
allow recovery sysfs_power:dir {search};
allow recovery sysfs_power:file {read open};
Index: device/rockchip/common/sepolicy/vendor/untrusted_app_27.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/untrusted_app_27.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/untrusted_app_27.te (revision 418)
@@ -86,6 +86,9 @@
allow untrusted_app_27 property_socket:sock_file { read open getattr setattr write map execute };
allow untrusted_app_27 init:unix_stream_socket { connectto };
allow untrusted_app_27 proc_tty_drivers:file { read open write getattr setattr ioctl map };
+allow untrusted_app_27 unlabeled:dir { write add_name create };
+allow untrusted_app_27 unlabeled:file { write create read getattr setattr map open };
+typeattribute unlabeled mlstrustedobject;
typeattribute adbd_prop mlstrustedobject;
typeattribute serialno_prop mlstrustedobject;
typeattribute serial_device mlstrustedobject;
Index: device/rockchip/common/sepolicy/vendor/vendor_init.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/vendor_init.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/vendor_init.te (revision 418)
@@ -24,6 +24,7 @@
allow vendor_init recovery_block_device:lnk_file { relabelto };
allow vendor_init misc_block_device:lnk_file { relabelto };
allow vendor_init e2fsck_cache_block_device:lnk_file { relabelto };
+allow vendor_init e2fsck_private_block_device:lnk_file { relabelto };
allow vendor_init security_block_device:lnk_file { relabelto };
allow vendor_init device:lnk_file { create write};
allow vendor_init tmpfs:dir { write add_name create };
Index: device/rockchip/common/sepolicy/vendor/vendor_install_recovery.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/vendor_install_recovery.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/vendor_install_recovery.te (revision 418)
@@ -10,6 +10,7 @@
allow vendor_install_recovery block_device:dir { search read open getattr };
allow vendor_install_recovery baseparameter_block_device:blk_file { read write };
allow vendor_install_recovery e2fsck_cache_block_device:blk_file { read write };
+allow vendor_install_recovery e2fsck_private_block_device:blk_file { read write };
allow vendor_install_recovery mnt_media_rw_file:dir { read search open getattr };
allow vendor_install_recovery fuseblk:dir { read search open getattr };
allow vendor_install_recovery fuseblk:file { read open getattr };
@@ -20,4 +21,4 @@
#allow vendor_install_recovery vendor_install_recovery:capability { dac_read_search };
allow vendor_install_recovery fuse:dir { r_file_perms search };
allow vendor_install_recovery fuse:file r_file_perms;
-set_prop(vendor_install_recovery, vendor_system_public_prop)
\ No newline at end of file
+set_prop(vendor_install_recovery, vendor_system_public_prop)
Index: device/rockchip/common/sepolicy/vendor/vold.te
===================================================================
--- device/rockchip/common/sepolicy/vendor/vold.te (revision 417)
+++ device/rockchip/common/sepolicy/vendor/vold.te (revision 418)
@@ -6,6 +6,7 @@
allow vold unlabeled:filesystem { mount };
allow vold kernel:system { module_request };
allow vold e2fsck_cache_block_device:blk_file getattr;
+allow vold e2fsck_private_block_device:blk_file getattr;
allow vold self:capability { setgid setuid };
allow vold vold_device:blk_file ioctl;
allow vold vold_exec:file execute_no_trans;
Index: system/sepolicy/prebuilts/api/30.0/private/file_contexts
===================================================================
--- system/sepolicy/prebuilts/api/30.0/private/file_contexts (revision 417)
+++ system/sepolicy/prebuilts/api/30.0/private/file_contexts (revision 418)
@@ -26,6 +26,7 @@
/config u:object_r:rootfs:s0
/data_mirror u:object_r:mirror_data_file:s0
/debug_ramdisk u:object_r:tmpfs:s0
+/private u:object_r:tmpfs:s0
/mnt u:object_r:tmpfs:s0
/postinstall u:object_r:postinstall_mnt_dir:s0
/postinstall/apex u:object_r:postinstall_apex_mnt_dir:s0
Index: system/sepolicy/prebuilts/api/30.0/public/domain.te
===================================================================
--- system/sepolicy/prebuilts/api/30.0/public/domain.te (revision 417)
+++ system/sepolicy/prebuilts/api/30.0/public/domain.te (revision 418)
@@ -348,7 +348,7 @@
neverallowxperm * devpts:chr_file ioctl TIOCSTI;
# Do not allow any domain other than init to create unlabeled files.
-neverallow { domain -init -recovery } unlabeled:dir_file_class_set create;
+#neverallow { domain -init -recovery } unlabeled:dir_file_class_set create;
# Limit device node creation to these whitelisted domains.
neverallow {
Index: system/sepolicy/private/file_contexts
===================================================================
--- system/sepolicy/private/file_contexts (revision 417)
+++ system/sepolicy/private/file_contexts (revision 418)
@@ -26,6 +26,7 @@
/config u:object_r:rootfs:s0
/data_mirror u:object_r:mirror_data_file:s0
/debug_ramdisk u:object_r:tmpfs:s0
+/private u:object_r:tmpfs:s0
/mnt u:object_r:tmpfs:s0
/postinstall u:object_r:postinstall_mnt_dir:s0
/postinstall/apex u:object_r:postinstall_apex_mnt_dir:s0
Index: system/sepolicy/public/domain.te
===================================================================
--- system/sepolicy/public/domain.te (revision 417)
+++ system/sepolicy/public/domain.te (revision 418)
@@ -348,7 +348,7 @@
neverallowxperm * devpts:chr_file ioctl TIOCSTI;
# Do not allow any domain other than init to create unlabeled files.
-neverallow { domain -init -recovery } unlabeled:dir_file_class_set create;
+#neverallow { domain -init -recovery } unlabeled:dir_file_class_set create;
5. recovery时挂载private分区
参考metadata分区,补丁如下
Index: bootable/recovery/install/include/install/wipe_data.h
===================================================================
--- bootable/recovery/install/include/install/wipe_data.h (revision 419)
+++ bootable/recovery/install/include/install/wipe_data.h (revision 420)
@@ -30,6 +30,8 @@
bool WipeData(Device* device, bool convert_fbe);
void SureMetadataMount();
+void SurePrivateMount();
int erase_baseparameter();
void WipeFrp();
int ResizeData();
Index: bootable/recovery/install/wipe_data.cpp
===================================================================
--- bootable/recovery/install/wipe_data.cpp (revision 419)
+++ bootable/recovery/install/wipe_data.cpp (revision 420)
@@ -36,6 +36,8 @@
constexpr const char* CACHE_ROOT = "/cache";
constexpr const char* DATA_ROOT = "/data";
constexpr const char* METADATA_ROOT = "/metadata";
+constexpr const char* PRIVATE_ROOT = "/private";
/**
* reset hdmi after restore factory.
@@ -171,6 +173,16 @@
ensure_path_mounted(METADATA_ROOT);
}
}
+void SurePrivateMount() {
+ if (ensure_path_mounted(PRIVATE_ROOT)) {
+ printf("mount private fail,so formate...\n");
+ reset_tmplog_offset();
+ format_volume(PRIVATE_ROOT);
+ ensure_path_mounted(PRIVATE_ROOT);
+ }
+}
+
void WipeFrp() {
printf("begin to wipe frp partion!\n");
int ret = format_volume("/frp");
Index: bootable/recovery/recovery.cpp
===================================================================
--- bootable/recovery/recovery.cpp (revision 419)
+++ bootable/recovery/recovery.cpp (revision 420)
@@ -1170,6 +1170,10 @@
device->StartRecovery();
SureMetadataMount();
+ SurePrivateMount();
printf("Command:");
for (const auto& arg : args) {v
编译成功烧录后,可以看到根目录下有private文件夹
drwxrwxrwx 5 system system 4096 2022-07-28 08:38 private
权限,组 用户都是对的
mount下也可以看到已经挂载到分区上了
/dev/block/mmcblk2p12 on /private type ext4 (rw,seclabel,nosuid,nodev,noatime,nodiratime,discard,noauto_da_alloc)
添加分区成功
其他说明
添加ok后,发现只有adb root后才能看到private的权限,否则显示的是????,如果想不root就可以看到private权限,需要修改shell.te
allow shell unlabeled:dir { write add_name create search getattr read open };
allow shell unlabeled:file { write create read getattr setattr map open };
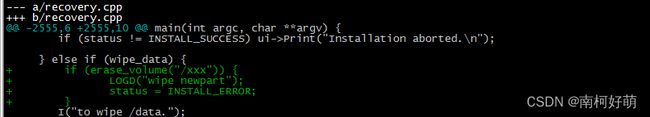
else if (wipe_data)—这个条件可以根据自己的实际需求来定,wipe_data的值来源misc文件的解析,所以可以参考这个参数的赋值,结合自己的实际情况来定义格式化新增分区的条件,
没有特别的需求,一般建议放到wipe_all的条件下,这个条件成立一般表示是第一次升级或者是烧录了misc文件,恢复出厂设置时,wipe_all为false,wipe_data为true,具体请自行阅读recovery.cpp的源码