HCIA——wireshark抓包之RIP以及OSPF协议
ZY目录
- HCIA所有内容:
- wireshark抓包工具
-
- 一、RIP协议
-
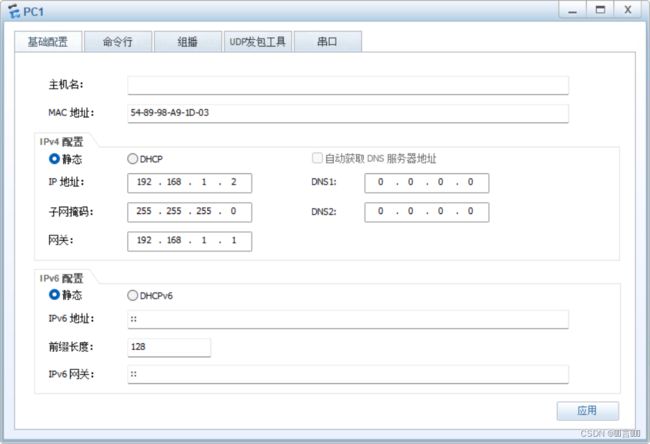
- 1、配接口IP以及手动配置PC端
-
- (1)实现代码:
- (2)截图:
- 2、启动RIP进程,选版本并进行宣告
-
- (1)实现代码:
- (2)路由表:
- (3)全局信息:
- 3、测试全网连通性
- 4、重启所有设备并快速抓包
- 5、抓包截图如下:
- request请求包
-
- 1、第一部分:
- 2、第二部分:
- 3、第三部分:
- 4、第四部分:
- 5、第五部分:
- response响应包
-
- 1、第一部分:
- 2、第二部分:
- 3、第三部分:
- 4、第四部分:
- 5、第五部分:
- 二、OSPF协议
-
- 1、配置接口IP,环回以及手动配置PC端
-
- (1)实现代码:
- (2)截图:
- 2、启动OSPF进程,划分区域并进行宣告
-
- (1)实现代码:
- (2)路由表:
- 3、测试全网连通性
- 4、抓包截图如下:
- hello包
- DBD包
- LSU包
- LSR包
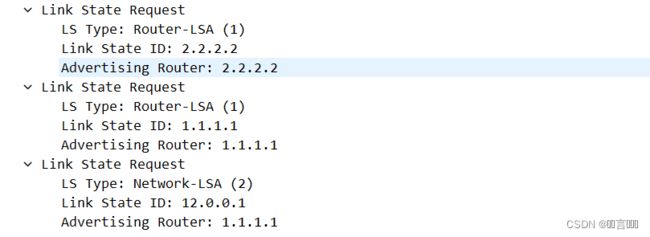
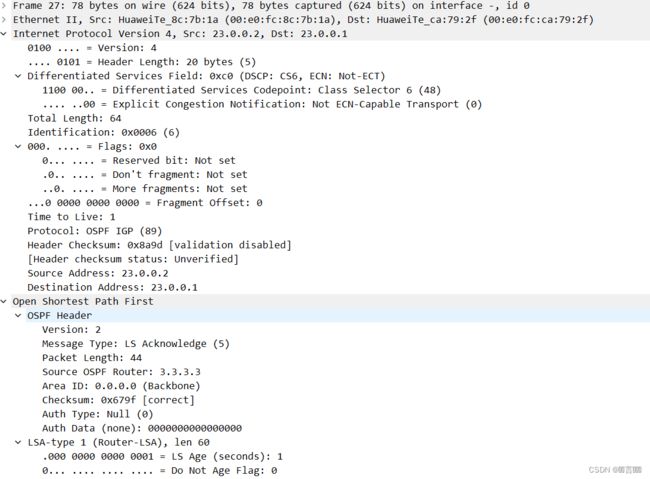
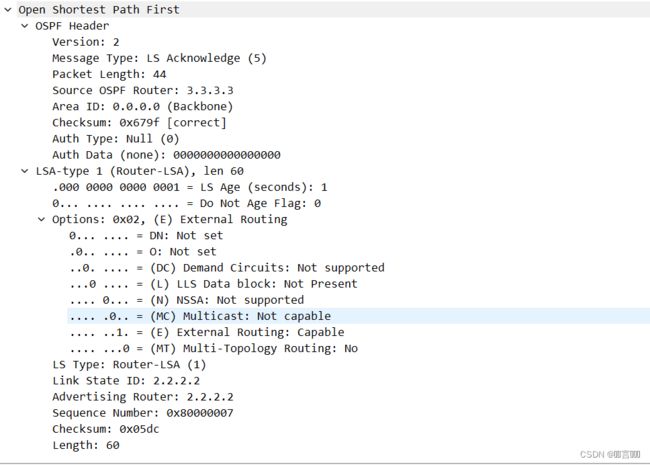
- LSA包
HCIA所有内容:
1、七层参考模型及IP讲解
2、TCP三次握手讲解
3、TCP四次挥手讲解及抓包分析
4、DHCP协议讲解及抓包分析
5、静态综合实验讲解
7、静态路由讲解
8、RIP路由信息协议讲解
9、动态路由协议讲解
10、抓包进行分析RIP以及OSPF的包
11、动态路由OSPF配置综合实验讲解
12、Vlan虚拟局域网技术讲解
13、ACL访问控制列表讲解
14、NAT技术讲解
15、网络综合实验讲解
wireshark抓包工具
在打TCP协议之后下篇的四次挥手中,用到了wireshark抓包工具来抓取并分析TCP的各种包。
链接地址
以及在之后的DHCP动态主机配置协议中,也进行了wireshark抓取DHCP的四种包。
链接地址
那么今天我将补充之前所遗留的RIP协议以及OSPF协议的数据包分析。
一、RIP协议
首先,我将还是以实验的形式进行数据包的抓取以及分析。
本实验只负责讲解RIP数据包在wireshark下直观分析,RIP协议详见:
RIP路由信息协议讲解
实验思路: 用ENSP模拟器搭建一个拓扑图,然后配置IP,网段,并且给各个路由器都让其内部采用RIP协议进行决定路由;
实验材料: ENSP华为模拟器以及wireshark抓包工具;
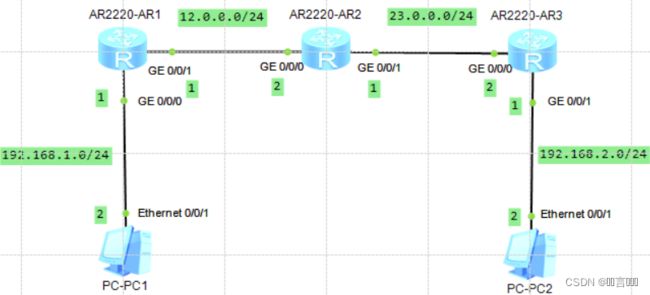
实验环境: 如下拓扑图所示:
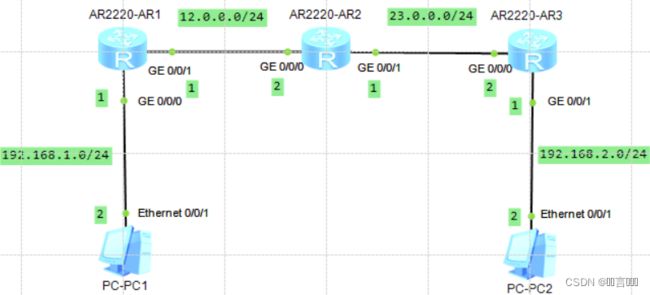
实验步骤:
1、配接口IP以及手动配置PC端
(1)实现代码:
R1实现代码:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sys
[Huawei]sysname r1
[r1]u
[r1]udp-helper
[r1]undo
[r1]user-bind
[r1]user-group
[r1]user-interface con
[r1]user-interface console 0
[r1-ui-console0]i
[r1-ui-console0]idle-timeout 0 0
[r1-ui-console0]int g0/0/0
[r1-GigabitEthernet0/0/0]ip ad
[r1-GigabitEthernet0/0/0]ip address 192.168.1.1 24
[r1-GigabitEthernet0/0/0]
May 1 2023 20:57:42-08:00 r1 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP
on the interface GigabitEthernet0/0/0 has entered the UP state.
[r1-GigabitEthernet0/0/0]int g0/0/1
[r1-GigabitEthernet0/0/1]ip ad
[r1-GigabitEthernet0/0/1]ip address 12.0.0.1 24
May 1 2023 20:58:03-08:00 r1 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/1 has entered the UP state.
[r1-GigabitEthernet0/0/1]quit
[r1]
R2实现代码:
<Huawei>sys
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]sys
[Huawei]sysname r2
[r2]u
[r2]udp-helper
[r2]undo
[r2]user-bind
[r2]user-group
[r2]user-interface con
[r2]user-interface console 0
[r2-ui-console0]i
[r2-ui-console0]idle-timeout 0 0
[r2-ui-console0]int g0/0/0
[r2-GigabitEthernet0/0/0]ip ad
[r2-GigabitEthernet0/0/0]ip address 12.0.0.2 24
[r2-GigabitEthernet0/0/0]
May 1 2023 21:00:28-08:00 r2 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP
on the interface GigabitEthernet0/0/0 has entered the UP state.
[r2-GigabitEthernet0/0/0]int g0/0/1
[r2-GigabitEthernet0/0/1]ip ad
[r2-GigabitEthernet0/0/1]ip address 23.0.0.1 24
May 1 2023 21:00:44-08:00 r2 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/1 has entered the UP state.
[r2-GigabitEthernet0/0/1]quit
[r2]
R3实现代码:
<Huawei>sys
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]sys
[Huawei]sysname r3
[r3]u
[r3]udp-helper
[r3]undo
[r3]user-bind
[r3]user-group
[r3]user-interface con
[r3]user-interface console 0
[r3-ui-console0]i
[r3-ui-console0]idle-timeout 0 0
[r3-ui-console0]int g0/0/0
[r3-GigabitEthernet0/0/0]ip ad
[r3-GigabitEthernet0/0/0]ip address 23.0.0.2 24
May 1 2023 21:01:53-08:00 r3 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP
on the interface GigabitEthernet0/0/0 has entered the UP state.
[r3-GigabitEthernet0/0/0]int g0/0/1
[r3-GigabitEthernet0/0/1]ip ad
[r3-GigabitEthernet0/0/1]ip address 192.168.2.1 24
[r3-GigabitEthernet0/0/1]
May 1 2023 21:02:16-08:00 r3 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/1 has entered the UP state.
[r3-GigabitEthernet0/0/1]quit
[r3]
(2)截图:
2、启动RIP进程,选版本并进行宣告
(1)实现代码:
R1实现代码:
[r1]rip 1
[r1-rip-1]v
[r1-rip-1]verify-source
[r1-rip-1]version 2
[r1-rip-1]undo s
[r1-rip-1]undo silent-interface
[r1-rip-1]undo summary
[r1-rip-1]n
[r1-rip-1]network 192.168.1.0
[r1-rip-1]network 12.0.0.0
[r1-rip-1]q
[r1]
R2实现代码:
[r2]rip 1
[r2-rip-1]v
[r2-rip-1]verify-source
[r2-rip-1]version 2
[r2-rip-1]un
[r2-rip-1]undo s
[r2-rip-1]undo silent-interface
[r2-rip-1]undo summary
[r2-rip-1]n
[r2-rip-1]network 12.0.0.0
[r2-rip-1]network 23.0.0.0
[r2-rip-1]quit
R3实现代码:
[r3]rip 1
[r3-rip-1]v
[r3-rip-1]verify-source
[r3-rip-1]version 2
[r3-rip-1]un
[r3-rip-1]undo s
[r3-rip-1]undo silent-interface
[r3-rip-1]undo summary
[r3-rip-1]n
[r3-rip-1]network 23.0.0.0
[r3-rip-1]network 192.168.2.0
[r3-rip-1]quit
[r3]
(2)路由表:
实现代码: display rip 1 route
R1路由表:
[r1]display rip 1 route
Route Flags : R - RIP
A - Aging, G - Garbage-collect
----------------------------------------------------------------------------
Peer 12.0.0.2 on GigabitEthernet0/0/1
Destination/Mask Nexthop Cost Tag Flags Sec
23.0.0.0/24 12.0.0.2 1 0 RA 23
192.168.2.0/24 12.0.0.2 2 0 RA 23
[r1]
R2路由表:
[r2]display rip 1 route
Route Flags : R - RIP
A - Aging, G - Garbage-collect
----------------------------------------------------------------------------
Peer 12.0.0.1 on GigabitEthernet0/0/0
Destination/Mask Nexthop Cost Tag Flags Sec
192.168.1.0/24 12.0.0.1 1 0 RA 23
Peer 23.0.0.2 on GigabitEthernet0/0/1
Destination/Mask Nexthop Cost Tag Flags Sec
192.168.2.0/24 23.0.0.2 1 0 RA 17
[r2]
R3路由表:
[r3]display rip 1 route
Route Flags : R - RIP
A - Aging, G - Garbage-collect
----------------------------------------------------------------------------
Peer 23.0.0.1 on GigabitEthernet0/0/0
Destination/Mask Nexthop Cost Tag Flags Sec
192.168.1.0/24 23.0.0.1 2 0 RA 1
12.0.0.0/24 23.0.0.1 1 0 RA 1
[r3]
(3)全局信息:
实现代码:display rip 1
查看RIP进程的当前运行状态及配置信息。
R1全局信息:
[r1]display rip 1
Public VPN-instance
RIP process : 1
RIP version : 2
Preference : 100
Checkzero : Enabled
Default-cost : 0
Summary : Disabled
Host-route : Enabled
Maximum number of balanced paths : 8
Update time : 30 sec Age time : 180 sec
Garbage-collect time : 120 sec
Graceful restart : Disabled
BFD : Disabled
Silent-interfaces : None
Default-route : Disabled
Verify-source : Enabled
Networks :
12.0.0.0 192.168.1.0
Configured peers : None
Number of routes in database : 6
Number of interfaces enabled : 2
Triggered updates sent : 2
Number of route changes : 2
Number of replies to queries : 1
Number of routes in ADV DB : 4
[r1]
R2全局信息:
[r2]display rip 1
Public VPN-instance
RIP process : 1
RIP version : 2
Preference : 100
Checkzero : Enabled
Default-cost : 0
Summary : Disabled
Host-route : Enabled
Maximum number of balanced paths : 8
Update time : 30 sec Age time : 180 sec
Garbage-collect time : 120 sec
Graceful restart : Disabled
BFD : Disabled
Silent-interfaces : None
Default-route : Disabled
Verify-source : Enabled
Networks :
23.0.0.0 12.0.0.0
Configured peers : None
Number of routes in database : 6
Number of interfaces enabled : 2
Triggered updates sent : 1
Number of route changes : 2
Number of replies to queries : 1
Number of routes in ADV DB : 4
[r2]
R3全局信息:
[r3]display rip 1
Public VPN-instance
RIP process : 1
RIP version : 2
Preference : 100
Checkzero : Enabled
Default-cost : 0
Summary : Disabled
Host-route : Enabled
Maximum number of balanced paths : 8
Update time : 30 sec Age time : 180 sec
Garbage-collect time : 120 sec
Graceful restart : Disabled
BFD : Disabled
Silent-interfaces : None
Default-route : Disabled
Verify-source : Enabled
Networks :
192.168.2.0 23.0.0.0
Configured peers : None
Number of routes in database : 6
Number of interfaces enabled : 2
Triggered updates sent : 0
Number of route changes : 2
Number of replies to queries : 0
Number of routes in ADV DB : 4
[r3]
解读代码:
Public VPN-instance
RIP process : 1 RIP 进程1
RIP version : 2 版本号2
Preference : 100 进程优先级100
Checkzero : Enabled 命令用来开启对RIP-1报文的零域进行检查的功能
Default-cost : 0 命令用来配置引入路由的缺省度量值。
Summary : Disabled 路由聚合功能是否开启
Host-route : Enabled 是否允许接收主机路由,
Maximum number of balanced paths : 8 等价路由的最大数目
Update time : 30 sec 周期更新时间为30s
Age time : 180 sec 失效时间为180s
Garbage-collect time : 120 sec 缓存删除时间为120s
Graceful restart : Disabled 是否使能GR。
BFD : Disabled 是否使能BFD。
Silent-interfaces : None 抑制接口数(这些接口不发送周期更新报文)
Default-route : Disabled 去使能生成缺省路由功能。
Verify-source : Enabled 是否使能源验证。
Networks : 网络地址。
192.168.2.0 23.0.0.0
Configured peers : None 配置的邻居。
Number of routes in database : 6 数据库中路由的条数。
Number of interfaces enabled : 2 使能协议的接口数。
Triggered updates sent : 0 发送的触发更新报文数。
Number of route changes : 2数据库中对已经发生改变的路由的统计数据。
Number of replies to queries : 0 RIP请求的响应报文数。
3、测试全网连通性
4、重启所有设备并快速抓包
思路: 由于rip的request请求包在启动设备配置好后立即发送,所以此时我需要重新启动设备。
5、抓包截图如下:
首先呢,前两个ARP包来判断路径中是否存在IP冲突;
然后,我们可以看到12.0.0.1发送了一个响应包,当然,在这之前,12.0.0.1必然收到了来自12.0.0.2的请求包,这里没有抓取到;
之后,12.0.0.1发送了一个请求包,以及12.0.0.2进行了响应,实际就是交换路由条目的过程。
那么我们接下来逐一进行分析RIP的两个数据包:
request请求包
1、第一部分:
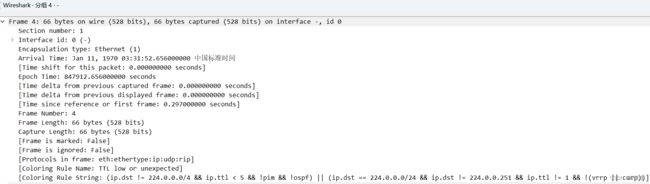
Frame 4: 4号帧,接口0上传输66个字节,实际捕获66字节
interface id:0 接口id 0 ;
Encapsulation type: Ethernet (1) 封装类型采用Ethernet (1);
Arrival Time: 捕获日期和时间;
[Time shift for this packet: 0.000000000 seconds] 此数据包的偏移时间
Epoch Time: 847912.656000000 seconds 周期时长
[Time delta from previous captured frame: 0.000000000 seconds]
此包与前一包的捕获时间间隔;
[Time delta from previous displayed frame: 0.000000000 seconds]
此包与前一个包的显示时间间隔;
[Time since reference or first frame: 0.297000000 seconds]
此包与前一帧的时间间隔;
Frame Number: 4 帧序号为4;
Frame Length 帧长;
Capture Length 捕获帧长;
[Frame is marked: False] 此帧是否做了标记:否;
[Frame is ignored: False] 此帧是否被忽略:否;
[Protocols in frame: eth:ethertype:ip:udp:rip] 帧内封装的协议层次结构;
[Coloring Rule Name: TTL low or unexpected] 着色标记的协议名称 ;
[Coloring Rule String: ] 着色规则显示的字符串
2、第二部分:
Destination 目的MAC地址;
Source 源MAC地址;
Type 使用协议:0X0800 IPV4协议
3、第三部分:
Version: 4 高四位展示版本 使用互联网协议
Header Length: 低四位展示IP包头部长度,长度为20字节;指数据报协议头长度,表示协议头具有32位字长的数量。指向数据起点。正确协议头最小值为5。
Differentiated Services Field: 0xc0 (DSCP: CS6, ECN: Not-ECT) :
差分服务字段
Total Length:52 IP包的总长度为52字节;指定整个 IP 数据包的字节长度,包括数据和协议头。其最大值为65,535字节
Identification:0x0002(2) 标志字段;包含一个整数,用于识别当前数据报。该字段由发送端分配帮助接收端集中数据报分片。
Flags: 0x0 标记字段;由3位字段构成,其中最低位(MF)控制分片,存在下一个分片置为1,否则置0代表结束分片。中间位(DF)指出数据包是否可进行分片。第三位即最高位保留不使用,但是必须为0
Fragment offset: 0 分的偏移量为0;13位字段,指出与源数据报的起始端相关的分片数据位置,支持目标IP适当重建源数据报
Time-to-Live:14 生存周期,是一种计数器,在丢弃数据报的每个点值依次减1直至减少为0。这样确保数据包无止境的环路过程(即TTL)
Protocol: UDP (17) 此包内封装的上层协议为UDP;指出在 IP 处理过程完成之后,有哪种上层协议接收导入数据包
Header checksum: 0xa9d0 [validation disabled] 头部数据检验和; 帮助确保 IP 协议头的完整性。由于某些协议头字段的改变,如生存期(Time to Live),这就需要对每个点重新计算和检验。Internet 协议头需要进行处理
Source: 12.0.0.1 源主机IP地址
Destination: 224.0.0.9 目标主机IP地址
4、第四部分:
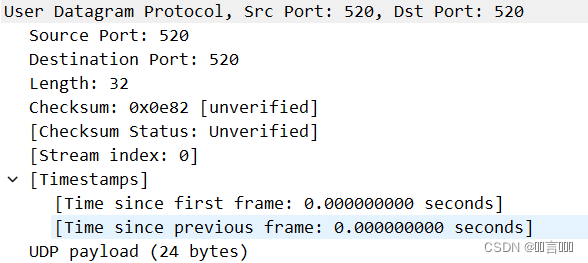
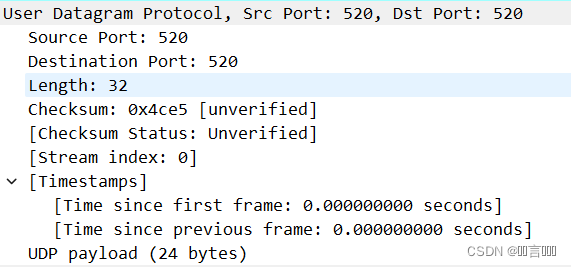
User Datagram Protocol, src Port: 520,Dst Port: 520
用户数据报协议,Src端口:520,Dst端口:520
Source Port: 520 源端口为520
Destination Port: 520 目的端口为520
Length: 32 UDP报文长度
Checksum: 0x0e82 [unverified] UDP报文校验和
Checksum status: Unverified 校验和状态:未验证
[stream index: 0]
[Timestamps]
[Time since first frame: .009999000 seconds]
第一帧开始的时间:0秒
[Time since previous frame: @.ogooe seconds]
自上一帧以来的时间为0秒
UDp payload (24 bytes) UDP有效负载(24字节)
5、第五部分:
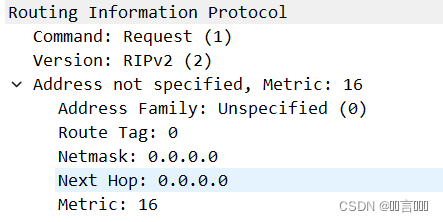
Routing Information Protocol 路由信息协议
Command: Request (1) 命令:1为RIP请求信息;2为RIP响应信息
Version: RIPV2 (2) 版本:使用RIPv2版本
Address not specified,Metric: 16 未指定地址
Address Family: Unspecified 地址族:未列明
Route Tag:0 路线标签:0
Netmask: 0.0.0.0 网络掩码:0.0.0.0
Next Hop: 0.0.0.0 下一跳:0.0.0.0
Metric: 16 跳数
response响应包
1、第一部分:
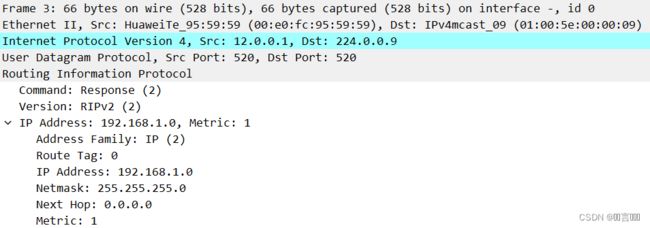
Frame 3: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) on interface -,id 0
第二帧:66个字节(528位) 在接口上捕获66个字节(528位) id 0
section number: 1 分段编号:1
Interface id: 0 (-) 接口标识:0
Interface name:- 接口名称
Encapsulation type: Ethernet (1) 封装类型:以太网(1)
Arrival Time: Jan 11,1970 03:31:52.65600000 中国标准时间
到达时间:1970年1月11日03:31:52656000000中国标准时间
[Time shift for this packet: 0.00 seconds]
[此数据包的时间位移:0秒]
Epoch Time: 847912.656000000 seconds
[Time delta from previous captured frame: 0.20300000 seconds]
[与前一帧相比的时间:0.203秒]
[Time delta from previous displayed frame: 0.203000000 seconds]
[与上一个显示帧的时间差:0.203秒]
[Time since reference or first frame: 0.297000000 seconds]
[自参考或第一帧起的时间:029秒]
Frame Number: 3 帧数:3
Frame Length: 66 bytes (528 bits) 帧长度:66字节(528位)
Capture Length: 66 bytes (528 bits) 捕获长度:66字节(528位)
[Frame is marked: False] [框架标记为:错误]
[Frame is ignored: False][帧被忽略:错误]
[Protocols in frame: eth:ethertype:ip;udp:rip]
[帧中的协议:以太网类型:ip:udp;rip]
[Coloring Rule Name: TTL low or unexpected]
[着色规则名称:TTL低或意外]
[Coloring Rule string; (ip.dst 224.0.0.0/4 & iptl < 5 8& pm 8 !ospf) || (ip.dst == 224.0.0.024 8 ip.dst |= 224.0.0.251 && ip.ttl != 1 && !(vrrp || carp))]
2、第二部分:
Destination 目的MAC地址;
Source 源MAC地址;
Type 使用协议:0X0800 IPV4协议
3、第三部分:
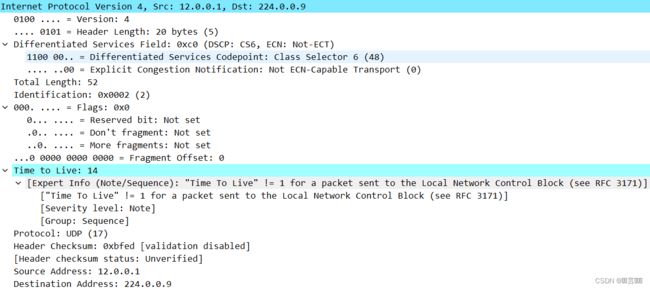
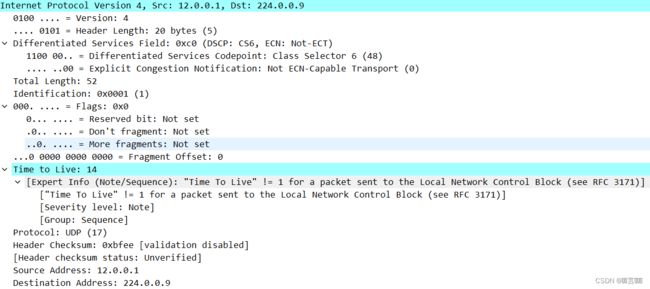
Internet Protocol Version 4,src: 12.0.0.1, Dst: 224.0.0.9
互联网协议版本4 源IP地址:12.0.0.1 目标IP地址:224.0.0.9
Differentiated Services Field: 0xc0 (DSCP: CS,ECN: Not-ECT)
Total Length: 52 总长度:52
Identification: 0x0001 (1) id:0x0001(1)
Time to Live: 14 生存时间:14
[Expert Info (Note/Sequence): “Time To live” != 1 for a packet sent to the local Network Control Block (see RFC 3171
[“Time To Live” != 1 for a packet sent to the Local Network Control Block (see RFC 3171]
[severity level: Note]
[Group: Sequence] 组:序列
Protocol: UDP (17) 协议:UDP(17)
Header Checksum: Oxbfee /validation disabled
标头校验和:Oxbfee[已停用验证]
Header checksum status: Unverified7 头校验和状态:未验证
source Address: 12.0.0.1 源地址:12.0.0.1
Destination Address: 224.0.0.9 目标地址:224.0.0.9
4、第四部分:
User Datagram Protocol, Src Port: 520,Dst Port: 520
用户数据报协议,源端口:520,目标端口:520
Source Port: 520 源端口:520
Destination Port: 520 目标端口:520
Length: 32 长度:32
Checksum: 0x4ce5 [unverified7]
[Checksum status: Unverified] [校验和状态:未核实]
[stream index: 0]
[Timestamps]
[Time since first frame: o.ogoggege seconds]
[第一顿开始的时间:0秒]
[Time since previous frame: 9.0ggg9 seconds]
自上一顿以来的时间:0秒
UDP payload (24 bytes) UDP有效负载(24字节)
5、第五部分:
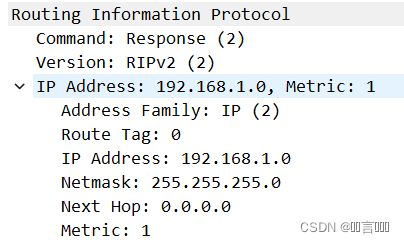
Routing Information Protocol 路由信息协议
Command: Response(2) 命令:响应(2)
Version: RIPV2 (2) 版本:RIP2
IP Address: 192.168.1.0 Metric: 1 IP地址;192.168.1.0 跳数:1
Address Family: IP (2)
Route Tag: 0 路线标签:0
IP Address: 192.168.1.9 IP地址:192.168.1.9
Netmask: 255.255.255.0 子网掩码:255.255.255.0
Next Hop: 0.0.0.0 下一跳:0.0.0.0
Metric: 1 跳数:1
以上便是RIP的两种数据包在wireshark下的分析。
二、OSPF协议
这里依旧用实验进行分析;
本实验只负责讲解RIP数据包在wireshark下直观分析,OSPF协议详见:
https://blog.csdn.net/weixin_63172698/article/details/130429584
实验思路: 用ENSP模拟器搭建一个拓扑图,然后配置IP,网段,并且给各个路由器都让其内部采用OSPF协议进行决定路由;
实验材料: ENSP华为模拟器以及wireshark抓包工具;
实验环境: 如下图所示的拓扑图:
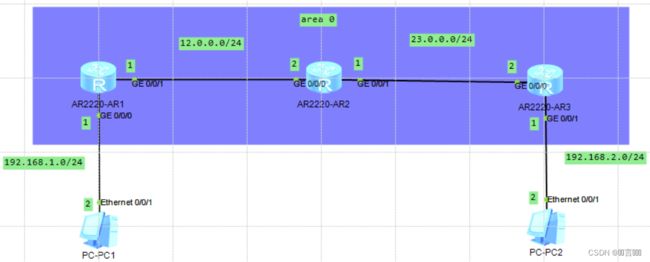
实验步骤:
1、配置接口IP,环回以及手动配置PC端
(1)实现代码:
R1实现代码:
<Huawei>SYS
Enter system view, return user view with Ctrl+Z.
[Huawei]SYS
[Huawei]sysname R1
[R1]U
[R1]udp-helper
[R1]undo
[R1]user-bind
[R1]user-group
[R1]user-interface CON
[R1]user-interface console 0
[R1-ui-console0]i
[R1-ui-console0]idle-timeout 0 0
[R1-ui-console0]int g0/0/0
[R1-GigabitEthernet0/0/0]ip ad
[R1-GigabitEthernet0/0/0]ip address 192.168.1.1 24
May 2 2023 16:36:16-08:00 R1 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP
on the interface GigabitEthernet0/0/0 has entered the UP state.
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip ad
[R1-GigabitEthernet0/0/1]ip address 12.0.0.1 24
May 2 2023 16:36:55-08:00 R1 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/1 has entered the UP state.
[R1-GigabitEthernet0/0/1]int l0
[R1-LoopBack0]ip ad
[R1-LoopBack0]ip address 1.1.1.1 24
[R1-LoopBack0]quit
[R1]
R2实现代码:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sys R2
[R2]u
[R2]udp-helper
[R2]undo
[R2]user-bind
[R2]user-group
[R2]user-interface con
[R2]user-interface console 0
[R2-ui-console0]i
[R2-ui-console0]idle-timeout 0 0
[R2-ui-console0]int g0/0/0
[R2-GigabitEthernet0/0/0]ip ad
[R2-GigabitEthernet0/0/0]ip address 12.0.0.2 24
May 2 2023 16:39:20-08:00 R2 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP
on the interface GigabitEthernet0/0/0 has entered the UP state.
[R2-GigabitEthernet0/0/0]
[R2-GigabitEthernet0/0/0]int g0/0/1
[R2-GigabitEthernet0/0/1]ip ad
[R2-GigabitEthernet0/0/1]ip address 23.0.0.1 24
May 2 2023 16:39:35-08:00 R2 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/1 has entered the UP state.
[R2-GigabitEthernet0/0/1]int l0
[R2-LoopBack0]ip ad
[R2-LoopBack0]ip address 2.2.2.2 24
[R2-LoopBack0]quit
[R2]
R3实现代码:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sys R3
[R3]u
[R3]udp-helper
[R3]undo
[R3]user-bind
[R3]user-group
[R3]user-interface on
[R3]user-interface con
[R3]user-interface console 0
[R3-ui-console0]i
[R3-ui-console0]idle-timeout 0 0
[R3-ui-console0]int g0/0/0
[R3-GigabitEthernet0/0/0]ip ad
[R3-GigabitEthernet0/0/0]ip address 23.0.0.2 24
May 2 2023 16:41:46-08:00 R3 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP
on the interface GigabitEthernet0/0/0 has entered the UP state.
[R3-GigabitEthernet0/0/0]int g0/0/1
[R3-GigabitEthernet0/0/1]ip ad
[R3-GigabitEthernet0/0/1]ip address 192.168.2.1 24
May 2 2023 16:42:04-08:00 R3 %%01IFNET/4/LINK_STATE(l)[1]:The line protocol IP
on the interface GigabitEthernet0/0/1 has entered the UP state.
[R3-GigabitEthernet0/0/1]int l0
[R3-LoopBack0]ip ad
[R3-LoopBack0]ip address 3.3.3.3 24
[R3-LoopBack0]quit
[R3]
(2)截图:
2、启动OSPF进程,划分区域并进行宣告
(1)实现代码:
R1实现代码:
[R1]osp
[R1]ospf 1 ro
[R1]ospf 1 router-id 1.1.1.1
[R1-ospf-1]area 0
[R1-ospf-1-area-0.0.0.0]n
[R1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]network 12.0.0.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
[R1-ospf-1-area-0.0.0.0]q
[R1-ospf-1]q
[R1]
R2实现代码:
[R2]os
[R2]ospf 1 ro
[R2]ospf 1 router-id 2.2.2.2
[R2-ospf-1]ar
[R2-ospf-1]area 0
[R2-ospf-1-area-0.0.0.0]ip ad
[R2-ospf-1-area-0.0.0.0]n
[R2-ospf-1-area-0.0.0.0]nssa
[R2-ospf-1-area-0.0.0.0]network 12.0.0.0 0.0.0.255
[R2-ospf-1-area-0.0.0.0]
May 2 2023 16:49:41-08:00 R2 %%01OSPF/4/NBR_CHANGE_E(l)[2]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.12, NeighborE
vent=HelloReceived, NeighborPreviousState=Down, NeighborCurrentState=Init)
[R2-ospf-1-area-0.0.0.0]
May 2 2023 16:49:41-08:00 R2 %%01OSPF/4/NBR_CHANGE_E(l)[3]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.12, NeighborE
vent=2WayReceived, NeighborPreviousState=Init, NeighborCurrentState=2Way)
[R2-ospf-1-area-0.0.0.0]
May 2 2023 16:49:41-08:00 R2 %%01OSPF/4/NBR_CHANGE_E(l)[4]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.12, NeighborE
vent=AdjOk?, NeighborPreviousState=2Way, NeighborCurrentState=ExStart)
[R2-ospf-1-area-0.0.0.0]
May 2 2023 16:49:41-08:00 R2 %%01OSPF/4/NBR_CHANGE_E(l)[5]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.12, NeighborE
vent=NegotiationDone, NeighborPreviousState=ExStart, NeighborCurrentState=Exchan
ge)
[R2-ospf-1-area-0.0.0.0]
May 2 2023 16:49:41-08:00 R2 %%01OSPF/4/NBR_CHANGE_E(l)[6]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.12, NeighborE
vent=ExchangeDone, NeighborPreviousState=Exchange, NeighborCurrentState=Loading)
[R2-ospf-1-area-0.0.0.0]
May 2 2023 16:49:41-08:00 R2 %%01OSPF/4/NBR_CHANGE_E(l)[7]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.12, NeighborE
vent=LoadingDone, NeighborPreviousState=Loading, NeighborCurrentState=Full)
[R2-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.255
[R2-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
[R2-ospf-1-area-0.0.0.0]q
[R2-ospf-1]q
[R2]
R3实现代码:
[R3]os
[R3]ospf 1 ro
[R3]ospf 1 router-id 3.3.3.3
[R3-ospf-1]area 0
[R3-ospf-1-area-0.0.0.0]n
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.255
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.255
May 2 2023 16:51:43-08:00 R3 %%01OSPF/4/NBR_CHANGE_E(l)[2]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.23, NeighborE
vent=HelloReceived, NeighborPreviousState=Down, NeighborCurrentState=Init)
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.255
May 2 2023 16:51:43-08:00 R3 %%01OSPF/4/NBR_CHANGE_E(l)[3]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.23, NeighborE
vent=2WayReceived, NeighborPreviousState=Init, NeighborCurrentState=2Way)
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.25
May 2 2023 16:51:43-08:00 R3 %%01OSPF/4/NBR_CHANGE_E(l)[4]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.23, NeighborE
vent=AdjOk?, NeighborPreviousState=2Way, NeighborCurrentState=ExStart)
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.25
May 2 2023 16:51:43-08:00 R3 %%01OSPF/4/NBR_CHANGE_E(l)[5]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.23, NeighborE
vent=NegotiationDone, NeighborPreviousState=ExStart, NeighborCurrentState=Exchan
ge)
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.25
May 2 2023 16:51:43-08:00 R3 %%01OSPF/4/NBR_CHANGE_E(l)[6]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.23, NeighborE
vent=ExchangeDone, NeighborPreviousState=Exchange, NeighborCurrentState=Loading)
[R3-ospf-1-area-0.0.0.0]network 23.0.0.0 0.0.0.25
May 2 2023 16:51:43-08:00 R3 %%01OSPF/4/NBR_CHANGE_E(l)[7]:Neighbor changes eve
nt: neighbor status changed. (ProcessId=256, NeighborAddress=1.0.0.23, NeighborE
vent=LoadingDone, NeighborPreviousState=Loading, NeighborCurrentState=Full)
[R3-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[R3-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.0
[R3-ospf-1-area-0.0.0.0]q
[R3-ospf-1]q
[R3]
(2)路由表:
R1路由表:
[R1]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 17 Routes : 17
Destination/Mask Proto Pre Cost Flags NextHop Interface
1.1.1.0/24 Direct 0 0 D 1.1.1.1 LoopBack0
1.1.1.1/32 Direct 0 0 D 127.0.0.1 LoopBack0
1.1.1.255/32 Direct 0 0 D 127.0.0.1 LoopBack0
2.2.2.2/32 OSPF 10 1 D 12.0.0.2 GigabitEthernet
0/0/1
3.3.3.3/32 OSPF 10 2 D 12.0.0.2 GigabitEthernet
0/0/1
12.0.0.0/24 Direct 0 0 D 12.0.0.1 GigabitEthernet
0/0/1
12.0.0.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
12.0.0.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
23.0.0.0/24 OSPF 10 2 D 12.0.0.2 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.1.0/24 Direct 0 0 D 192.168.1.1 GigabitEthernet
0/0/0
192.168.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.1.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
192.168.2.0/24 OSPF 10 3 D 12.0.0.2 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[R1]
R2路由表:
[R2]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 17 Routes : 17
Destination/Mask Proto Pre Cost Flags NextHop Interface
1.1.1.1/32 OSPF 10 1 D 12.0.0.1 GigabitEthernet
0/0/0
2.2.2.0/24 Direct 0 0 D 2.2.2.2 LoopBack0
2.2.2.2/32 Direct 0 0 D 127.0.0.1 LoopBack0
2.2.2.255/32 Direct 0 0 D 127.0.0.1 LoopBack0
3.3.3.3/32 OSPF 10 1 D 23.0.0.2 GigabitEthernet
0/0/1
12.0.0.0/24 Direct 0 0 D 12.0.0.2 GigabitEthernet
0/0/0
12.0.0.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
12.0.0.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
23.0.0.0/24 Direct 0 0 D 23.0.0.1 GigabitEthernet
0/0/1
23.0.0.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
23.0.0.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.1.0/24 OSPF 10 2 D 12.0.0.1 GigabitEthernet
0/0/0
192.168.2.0/24 OSPF 10 2 D 23.0.0.2 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[R2]
R3路由表:
[R3]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 17 Routes : 17
Destination/Mask Proto Pre Cost Flags NextHop Interface
1.1.1.1/32 OSPF 10 2 D 23.0.0.1 GigabitEthernet
0/0/0
2.2.2.2/32 OSPF 10 1 D 23.0.0.1 GigabitEthernet
0/0/0
3.3.3.0/24 Direct 0 0 D 3.3.3.3 LoopBack0
3.3.3.3/32 Direct 0 0 D 127.0.0.1 LoopBack0
3.3.3.255/32 Direct 0 0 D 127.0.0.1 LoopBack0
12.0.0.0/24 OSPF 10 2 D 23.0.0.1 GigabitEthernet
0/0/0
23.0.0.0/24 Direct 0 0 D 23.0.0.2 GigabitEthernet
0/0/0
23.0.0.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
23.0.0.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.1.0/24 OSPF 10 3 D 23.0.0.1 GigabitEthernet
0/0/0
192.168.2.0/24 Direct 0 0 D 192.168.2.1 GigabitEthernet
0/0/1
192.168.2.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
192.168.2.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[R3]
3、测试全网连通性
思路: 用PC1去pingPC2
实现代码: ping 192.168.2.2
截图:

即为全网可达。
4、抓包截图如下:
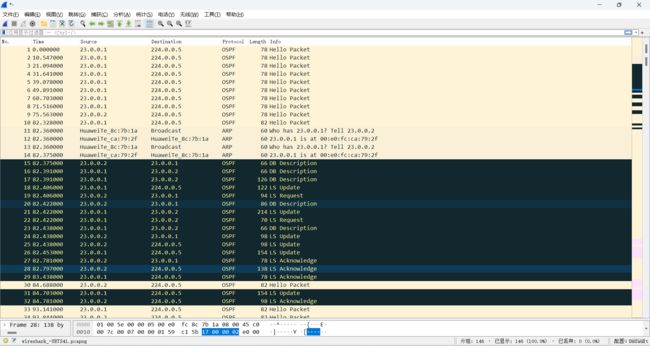
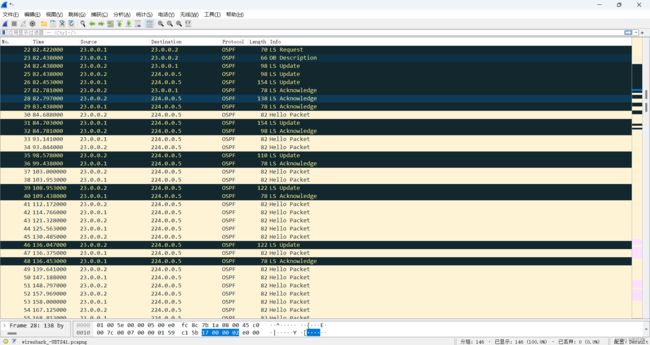
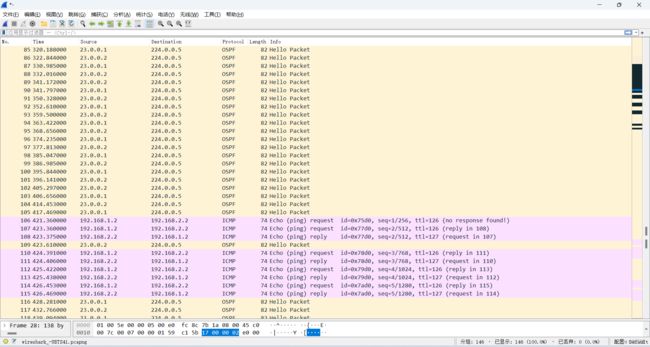
抓包开始时间为配置好IP之后,进行了抓包,然后配置ospf之后我们就可以直观的看到数据包的信息。
最后一张截图中,ICMP协议的包便是我们的ping包,即为第三步用PC1去pingPC 2的数据包。下面我们来分析OSPF协议下的几种数据包。
hello包
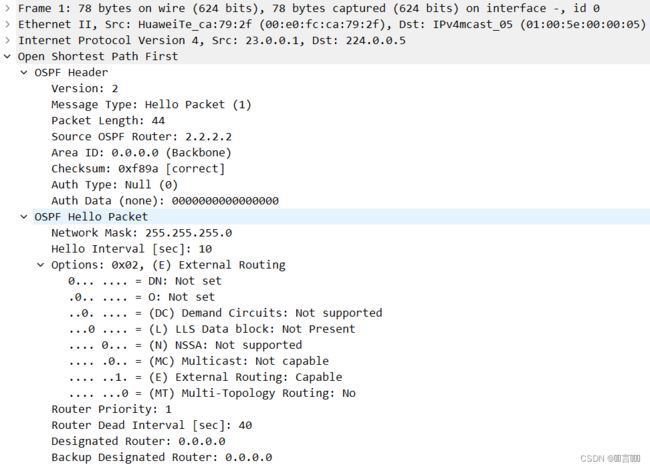
最上面三层即为物理层的数据信息,数据链路层的数据信息以及传输层的数据信息,我们在RIP中已经详细的解释了。
所以我们将主要看最后一行:Open shortest Path First
开放性最短路径优先:
Open shortest Path First
OSPF头部:
OSPF Header
Version: 2 描述协议版本号
Message Type: Hello packet (1) 协议报文类型
Packet Length: 44
Source OSPF Router: 2.2.2.2 描述发送该hello报文的路由器ID
Area ID: 0.0.0.0 (Backbone) 描述发送该报文的接口在哪个区域
Checksum: 0xf89a [correct] 校验和,用保证报文的完整性
Auth Type: Null (0) 认证类型,NULL
Auth Data (none): 0000000000000000 认证数据
HELLO报文包数据:
OSPF Hello Packet
Network Mask: 255.255.255.0 用于描述发送该Hello报文路由器的接口掩码长度。
Hello Interval [sec]: 10 用于描述自身hello报文发送的时间间隔。
Options: 0x92,(E) External Routing 可选项,OSPF邻居建立的时候需要满足Ebit和Nbit一致。
Router Priority: 1 用于发送该OSPF报文接口的DR优先级。
Router Dead Interval [sec]: 40 用于描述邻居的失效时间。
Designated Router: 0.0.0.0 指定路由器,用于描述该链路上的DR,取值为DR的接口IP地址。
Backup Designated Router: 0.0.0.0 备份指定路由器,用于描述该链路上的BDR,取值为BDR的接口IP地址。
DBD包

主要与HELLO包不同的地方有:
头部主要是:协议报文的类型,长度以及DBD包的路由器的ID