Newstarctf week5逆向wp
拔丝溜肆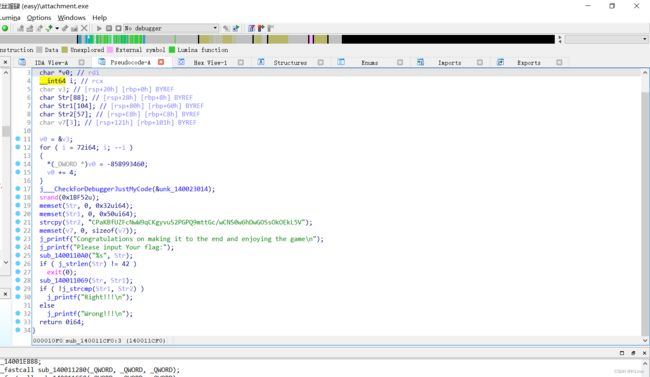
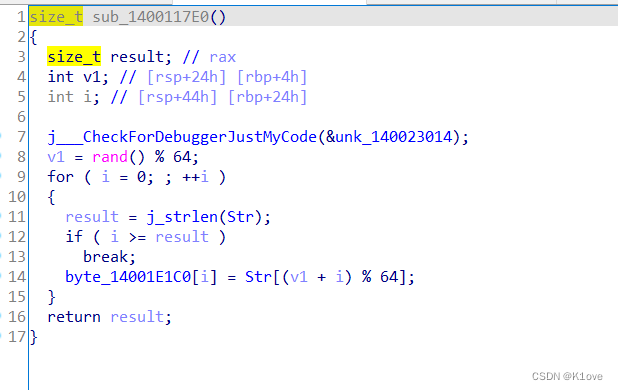
IDA f5后先找到主函数,很容易得出sub_140011069函数是输入函数,然后下面有一个判断,可以得出flag长度为42, sub_140011069函数先猜测是加密函数,然后进去看看
,看起来有点像base64,然后有一个sub_14001127b这个函数在这里有点奇怪,进去看看
用伪随机数把base64表顺序打乱,并且每次不一样,每次只加密三个字符
然后用c语言跑一下每次加密所使用的base64表。
#include
void init();
char key[100];
int main() {
int i=0;
srand(0x1BF52u);
for(i=0;i<64;i++) {
init();
}
}
void init() {
unsigned char Str[] =
{
0x41, 0x42, 0x43, 0x44, 0x45, 0x46, 0x47, 0x48, 0x49, 0x4A,
0x4B, 0x4C, 0x4D, 0x4E, 0x4F, 0x50, 0x51, 0x52, 0x53, 0x54,
0x55, 0x56, 0x57, 0x58, 0x59, 0x5A, 0x61, 0x62, 0x63, 0x64,
0x65, 0x66, 0x67, 0x68, 0x69, 0x6A, 0x6B, 0x6C, 0x6D, 0x6E,
0x6F, 0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78,
0x79, 0x7A, 0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37,
0x38, 0x39, 0x2B, 0x2F,0x00
};
int i=0;
int v1=rand() % 64;
printf("\"");
for(i=0;i<64;i++) {
key[i]=Str[(v1 + i) % 64];
printf("%c",key[i]);
}
printf("\",\n");
}
然后再用python跑一下
#include
void init();
char key[100];
int main() {
int i=0;
srand(0x1BF52u);
for(i=0;i<64;i++) {
init();
}
}
void init() {
unsigned char Str[] =
{
0x41, 0x42, 0x43, 0x44, 0x45, 0x46, 0x47, 0x48, 0x49, 0x4A,
0x4B, 0x4C, 0x4D, 0x4E, 0x4F, 0x50, 0x51, 0x52, 0x53, 0x54,
0x55, 0x56, 0x57, 0x58, 0x59, 0x5A, 0x61, 0x62, 0x63, 0x64,
0x65, 0x66, 0x67, 0x68, 0x69, 0x6A, 0x6B, 0x6C, 0x6D, 0x6E,
0x6F, 0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78,
0x79, 0x7A, 0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37,
0x38, 0x39, 0x2B, 0x2F,0x00
};
int i=0;
int v1=rand() % 64;
printf("\"");
for(i=0;i<64;i++) {
key[i]=Str[(v1 + i) % 64];
printf("%c",key[i]);
}
printf("\",\n");
} 得到flag
E4sy_Mix (hard)
打开ida发现这里有一个v4=sub_402000很奇怪,因为这个属于代码段,并且下面直接用这个值当成函数运行,说明这个dowhile循环里面是对其进行解密,然后手动提取一下解密一下再放回去,
得到sub_402000函数
这俩个函数很轻易就能发现一个是对rc4的盒子进行初始化,然后加密,key就是密钥
然后直接拿密文rc4解密得flag.
Virtual Self (middle)
先看一下ida主函数内容 ,主要逻辑就是先输入,然后mov,sub,xor,add四个函数在for循环里进行运算,
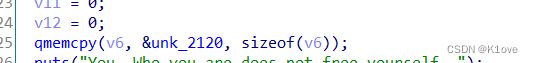
从如下图的unk_2120中取值,然后在for循环中判断中进行不同的运算根据unk_2120的值
仔细观察一下这个地址藏着的数据,发现0xe0每轮有五个,也就是说每次其实只加密一个字节并且放回原处, 我想了半天也没想到怎么可以逆出这个算法,然后我想到了模拟,然后爆破,我直接把数据和加密运算的函数直接照搬,然后爆破,每次运算都找一个准确的数,直到爆破出准确的flag值,代码如下
#include
unsigned char reg[4];
void mov(unsigned char *a1);
void xor(unsigned char *a1);
void sub(unsigned char *a1);
void add(unsigned char *a1);
void exp(unsigned char *start,unsigned char *end);
int main() {
unsigned char encode[50]={
0x84,0x1f,0x3c,0x7b,0xb9,0x2a,0x6c,0x63,
0xA4,0x72, 0x1B, 0x08, 0x76, 0x5F, 0x96, 0x88 ,
0x86 ,0x5F ,0x7B ,0x67 ,0xCD ,0x86 ,0x97 ,0x66,
0x64 ,0x99 ,0xFC, 0x7D,0x81,0x00
};
unsigned char ida[] =
{
0xE0, 0x01, 0xD0, 0x03, 0xE0, 0x03, 0xD1, 0xB5, 0xE0, 0x03,
0xD2, 0xDE, 0xE0, 0x03, 0xD3, 0xA1, 0xA2, 0x00, 0xD1, 0xD3,
0xA2, 0x00, 0xD3, 0xD3, 0xA1, 0x01, 0xD0, 0x02, 0xA0, 0x00,
0xD0, 0xD1, 0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x01, 0xD0, 0x00,
0xA2, 0x00, 0xD3, 0xD3, 0xA1, 0x00, 0xD1, 0xD2, 0xA2, 0x01,
0xD0, 0x02, 0xA2, 0x01, 0xD0, 0x00, 0xE0, 0x02, 0x03, 0xD0,
0xE0, 0x01, 0xD0, 0x0A, 0xE0, 0x03, 0xD1, 0x61, 0xE0, 0x03,
0xD2, 0x71, 0xE0, 0x03, 0xD3, 0x7A, 0xA0, 0x01, 0xD0, 0x03,
0xA0, 0x00, 0xD0, 0xD1, 0xA1, 0x00, 0xD3, 0xD2, 0xA0, 0x00,
0xD2, 0xD1, 0xA2, 0x00, 0xD2, 0xD3, 0xA2, 0x01, 0xD0, 0x00,
0xA2, 0x00, 0xD2, 0xD3, 0xA2, 0x00, 0xD1, 0xD3, 0xA2, 0x00,
0xD2, 0xD3, 0xA1, 0x01, 0xD0, 0x00, 0xE0, 0x02, 0x0A, 0xD0,
0xE0, 0x01, 0xD0, 0x11, 0xE0, 0x03, 0xD1, 0xC5, 0xE0, 0x03,
0xD2, 0xA2, 0xE0, 0x03, 0xD3, 0x7B, 0xA1, 0x00, 0xD1, 0xD2,
0xA0, 0x01, 0xD0, 0x01, 0xA0, 0x00, 0xD2, 0xD1, 0xA1, 0x01,
0xD0, 0x00, 0xA0, 0x00, 0xD1, 0xD1, 0xA0, 0x01, 0xD0, 0x00,
0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x01, 0xD0, 0x02, 0xA2, 0x00,
0xD1, 0xD3, 0xA0, 0x01, 0xD0, 0x03, 0xE0, 0x02, 0x11, 0xD0,
0xE0, 0x01, 0xD0, 0x16, 0xE0, 0x03, 0xD1, 0x8C, 0xE0, 0x03,
0xD2, 0xE6, 0xE0, 0x03, 0xD3, 0xFC, 0xA2, 0x01, 0xD0, 0x02,
0xA0, 0x00, 0xD2, 0xD1, 0xA2, 0x00, 0xD0, 0xD3, 0xA1, 0x01,
0xD0, 0x02, 0xA0, 0x01, 0xD0, 0x01, 0xA0, 0x00, 0xD2, 0xD1,
0xA0, 0x00, 0xD1, 0xD1, 0xA1, 0x00, 0xD1, 0xD2, 0xA1, 0x00,
0xD3, 0xD2, 0xA0, 0x00, 0xD0, 0xD1, 0xE0, 0x02, 0x16, 0xD0,
0xE0, 0x01, 0xD0, 0x05, 0xE0, 0x03, 0xD1, 0x4A, 0xE0, 0x03,
0xD2, 0x70, 0xE0, 0x03, 0xD3, 0x17, 0xA2, 0x00, 0xD0, 0xD3,
0xA0, 0x00, 0xD0, 0xD1, 0xA2, 0x01, 0xD0, 0x01, 0xA2, 0x00,
0xD0, 0xD3, 0xA1, 0x01, 0xD0, 0x00, 0xA1, 0x00, 0xD0, 0xD2,
0xA0, 0x00, 0xD0, 0xD1, 0xA0, 0x01, 0xD0, 0x01, 0xA2, 0x01,
0xD0, 0x00, 0xA1, 0x01, 0xD0, 0x01, 0xE0, 0x02, 0x05, 0xD0,
0xE0, 0x01, 0xD0, 0x00, 0xE0, 0x03, 0xD1, 0x1F, 0xE0, 0x03,
0xD2, 0x0B, 0xE0, 0x03, 0xD3, 0xD9, 0xA2, 0x00, 0xD0, 0xD3,
0xA1, 0x00, 0xD0, 0xD2, 0xA0, 0x01, 0xD0, 0x00, 0xA2, 0x01,
0xD0, 0x02, 0xA1, 0x00, 0xD3, 0xD2, 0xA0, 0x01, 0xD0, 0x00,
0xA2, 0x00, 0xD3, 0xD3, 0xA0, 0x00, 0xD0, 0xD1, 0xA2, 0x01,
0xD0, 0x03, 0xA0, 0x01, 0xD0, 0x02, 0xE0, 0x02, 0x00, 0xD0,
0xE0, 0x01, 0xD0, 0x07, 0xE0, 0x03, 0xD1, 0xB7, 0xE0, 0x03,
0xD2, 0xF0, 0xE0, 0x03, 0xD3, 0x56, 0xA2, 0x01, 0xD0, 0x01,
0xA0, 0x00, 0xD1, 0xD1, 0xA0, 0x01, 0xD0, 0x02, 0xA2, 0x00,
0xD2, 0xD3, 0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x01, 0xD0, 0x01,
0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x01, 0xD0, 0x03, 0xA2, 0x00,
0xD2, 0xD3, 0xA2, 0x01, 0xD0, 0x02, 0xE0, 0x02, 0x07, 0xD0,
0xE0, 0x01, 0xD0, 0x19, 0xE0, 0x03, 0xD1, 0xC6, 0xE0, 0x03,
0xD2, 0x80, 0xE0, 0x03, 0xD3, 0x4E, 0xA2, 0x00, 0xD0, 0xD3,
0xA1, 0x01, 0xD0, 0x00, 0xA1, 0x00, 0xD0, 0xD2, 0xA2, 0x00,
0xD2, 0xD3, 0xA0, 0x01, 0xD0, 0x01, 0xA1, 0x01, 0xD0, 0x02,
0xA2, 0x00, 0xD2, 0xD3, 0xA2, 0x01, 0xD0, 0x02, 0xA2, 0x00,
0xD1, 0xD3, 0xA2, 0x01, 0xD0, 0x02, 0xE0, 0x02, 0x19, 0xD0,
0xE0, 0x01, 0xD0, 0x17, 0xE0, 0x03, 0xD1, 0xC6, 0xE0, 0x03,
0xD2, 0xD4, 0xE0, 0x03, 0xD3, 0x29, 0xA0, 0x00, 0xD1, 0xD1,
0xA2, 0x01, 0xD0, 0x02, 0xA0, 0x01, 0xD0, 0x01, 0xA0, 0x01,
0xD0, 0x03, 0xA1, 0x01, 0xD0, 0x03, 0xA0, 0x00, 0xD3, 0xD1,
0xA2, 0x01, 0xD0, 0x03, 0xA2, 0x01, 0xD0, 0x00, 0xA0, 0x01,
0xD0, 0x03, 0xA0, 0x00, 0xD2, 0xD1, 0xE0, 0x02, 0x17, 0xD0,
0xE0, 0x01, 0xD0, 0x0E, 0xE0, 0x03, 0xD1, 0x50, 0xE0, 0x03,
0xD2, 0xE4, 0xE0, 0x03, 0xD3, 0xF9, 0xA2, 0x00, 0xD0, 0xD3,
0xA0, 0x00, 0xD3, 0xD1, 0xA1, 0x00, 0xD2, 0xD2, 0xA1, 0x01,
0xD0, 0x00, 0xA1, 0x01, 0xD0, 0x01, 0xA2, 0x00, 0xD0, 0xD3,
0xA2, 0x01, 0xD0, 0x01, 0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x01,
0xD0, 0x03, 0xA1, 0x00, 0xD0, 0xD2, 0xE0, 0x02, 0x0E, 0xD0,
0xE0, 0x01, 0xD0, 0x13, 0xE0, 0x03, 0xD1, 0x6D, 0xE0, 0x03,
0xD2, 0x07, 0xE0, 0x03, 0xD3, 0x01, 0xA2, 0x01, 0xD0, 0x00,
0xA0, 0x01, 0xD0, 0x00, 0xA2, 0x00, 0xD1, 0xD3, 0xA1, 0x00,
0xD2, 0xD2, 0xA2, 0x01, 0xD0, 0x01, 0xA0, 0x00, 0xD3, 0xD1,
0xA1, 0x01, 0xD0, 0x00, 0xA0, 0x00, 0xD2, 0xD1, 0xA1, 0x01,
0xD0, 0x00, 0xA1, 0x00, 0xD1, 0xD2, 0xE0, 0x02, 0x13, 0xD0,
0xE0, 0x01, 0xD0, 0x1A, 0xE0, 0x03, 0xD1, 0xB1, 0xE0, 0x03,
0xD2, 0x3A, 0xE0, 0x03, 0xD3, 0x4F, 0xA1, 0x00, 0xD0, 0xD2,
0xA0, 0x00, 0xD0, 0xD1, 0xA0, 0x01, 0xD0, 0x02, 0xA2, 0x00,
0xD2, 0xD3, 0xA1, 0x00, 0xD0, 0xD2, 0xA2, 0x01, 0xD0, 0x03,
0xA2, 0x01, 0xD0, 0x03, 0xA2, 0x01, 0xD0, 0x03, 0xA1, 0x00,
0xD1, 0xD2, 0xA0, 0x01, 0xD0, 0x03, 0xE0, 0x02, 0x1A, 0xD0,
0xE0, 0x01, 0xD0, 0x14, 0xE0, 0x03, 0xD1, 0x95, 0xE0, 0x03,
0xD2, 0x04, 0xE0, 0x03, 0xD3, 0x46, 0xA0, 0x01, 0xD0, 0x02,
0xA1, 0x00, 0xD2, 0xD2, 0xA1, 0x00, 0xD0, 0xD2, 0xA1, 0x00,
0xD0, 0xD2, 0xA0, 0x00, 0xD2, 0xD1, 0xA0, 0x01, 0xD0, 0x01,
0xA2, 0x00, 0xD2, 0xD3, 0xA1, 0x00, 0xD3, 0xD2, 0xA2, 0x00,
0xD1, 0xD3, 0xA1, 0x00, 0xD0, 0xD2, 0xE0, 0x02, 0x14, 0xD0,
0xE0, 0x01, 0xD0, 0x02, 0xE0, 0x03, 0xD1, 0xF4, 0xE0, 0x03,
0xD2, 0x7A, 0xE0, 0x03, 0xD3, 0x18, 0xA1, 0x00, 0xD1, 0xD2,
0xA2, 0x00, 0xD0, 0xD3, 0xA1, 0x00, 0xD3, 0xD2, 0xA1, 0x00,
0xD2, 0xD2, 0xA1, 0x01, 0xD0, 0x00, 0xA0, 0x00, 0xD3, 0xD1,
0xA1, 0x01, 0xD0, 0x02, 0xA1, 0x00, 0xD0, 0xD2, 0xA1, 0x01,
0xD0, 0x00, 0xA2, 0x01, 0xD0, 0x03, 0xE0, 0x02, 0x02, 0xD0,
0xE0, 0x01, 0xD0, 0x12, 0xE0, 0x03, 0xD1, 0xDA, 0xE0, 0x03,
0xD2, 0x13, 0xE0, 0x03, 0xD3, 0x9A, 0xA1, 0x00, 0xD1, 0xD2,
0xA0, 0x01, 0xD0, 0x03, 0xA2, 0x01, 0xD0, 0x00, 0xA0, 0x00,
0xD0, 0xD1, 0xA0, 0x01, 0xD0, 0x01, 0xA0, 0x00, 0xD3, 0xD1,
0xA0, 0x00, 0xD0, 0xD1, 0xA1, 0x01, 0xD0, 0x02, 0xA1, 0x01,
0xD0, 0x03, 0xA2, 0x00, 0xD1, 0xD3, 0xE0, 0x02, 0x12, 0xD0,
0xE0, 0x01, 0xD0, 0x04, 0xE0, 0x03, 0xD1, 0xD8, 0xE0, 0x03,
0xD2, 0x2A, 0xE0, 0x03, 0xD3, 0xBC, 0xA0, 0x01, 0xD0, 0x02,
0xA2, 0x00, 0xD1, 0xD3, 0xA1, 0x01, 0xD0, 0x01, 0xA1, 0x00,
0xD0, 0xD2, 0xA0, 0x00, 0xD0, 0xD1, 0xA2, 0x00, 0xD3, 0xD3,
0xA2, 0x01, 0xD0, 0x01, 0xA0, 0x00, 0xD3, 0xD1, 0xA1, 0x01,
0xD0, 0x02, 0xA0, 0x01, 0xD0, 0x00, 0xE0, 0x02, 0x04, 0xD0,
0xE0, 0x01, 0xD0, 0x06, 0xE0, 0x03, 0xD1, 0x6E, 0xE0, 0x03,
0xD2, 0x4A, 0xE0, 0x03, 0xD3, 0x35, 0xA0, 0x01, 0xD0, 0x03,
0xA1, 0x01, 0xD0, 0x02, 0xA2, 0x00, 0xD1, 0xD3, 0xA0, 0x00,
0xD3, 0xD1, 0xA0, 0x01, 0xD0, 0x03, 0xA2, 0x01, 0xD0, 0x03,
0xA2, 0x00, 0xD3, 0xD3, 0xA2, 0x01, 0xD0, 0x02, 0xA1, 0x01,
0xD0, 0x03, 0xA2, 0x01, 0xD0, 0x01, 0xE0, 0x02, 0x06, 0xD0,
0xE0, 0x01, 0xD0, 0x0B, 0xE0, 0x03, 0xD1, 0x70, 0xE0, 0x03,
0xD2, 0x04, 0xE0, 0x03, 0xD3, 0xAE, 0xA2, 0x01, 0xD0, 0x02,
0xA1, 0x00, 0xD0, 0xD2, 0xA2, 0x00, 0xD1, 0xD3, 0xA1, 0x00,
0xD1, 0xD2, 0xA1, 0x01, 0xD0, 0x02, 0xA2, 0x01, 0xD0, 0x03,
0xA0, 0x00, 0xD0, 0xD1, 0xA2, 0x00, 0xD0, 0xD3, 0xA0, 0x00,
0xD1, 0xD1, 0xA0, 0x01, 0xD0, 0x00, 0xE0, 0x02, 0x0B, 0xD0,
0xE0, 0x01, 0xD0, 0x15, 0xE0, 0x03, 0xD1, 0x99, 0xE0, 0x03,
0xD2, 0x07, 0xE0, 0x03, 0xD3, 0xE5, 0xA1, 0x00, 0xD1, 0xD2,
0xA0, 0x01, 0xD0, 0x03, 0xA1, 0x00, 0xD3, 0xD2, 0xA2, 0x00,
0xD0, 0xD3, 0xA2, 0x00, 0xD0, 0xD3, 0xA2, 0x01, 0xD0, 0x00,
0xA2, 0x01, 0xD0, 0x03, 0xA0, 0x01, 0xD0, 0x02, 0xA2, 0x00,
0xD3, 0xD3, 0xA1, 0x01, 0xD0, 0x03, 0xE0, 0x02, 0x15, 0xD0,
0xE0, 0x01, 0xD0, 0x09, 0xE0, 0x03, 0xD1, 0x77, 0xE0, 0x03,
0xD2, 0x0A, 0xE0, 0x03, 0xD3, 0x00, 0xA2, 0x01, 0xD0, 0x01,
0xA1, 0x00, 0xD2, 0xD2, 0xA1, 0x00, 0xD0, 0xD2, 0xA1, 0x01,
0xD0, 0x02, 0xA1, 0x00, 0xD3, 0xD2, 0xA1, 0x01, 0xD0, 0x03,
0xA0, 0x00, 0xD1, 0xD1, 0xA2, 0x01, 0xD0, 0x01, 0xA0, 0x01,
0xD0, 0x02, 0xA2, 0x01, 0xD0, 0x02, 0xE0, 0x02, 0x09, 0xD0,
0xE0, 0x01, 0xD0, 0x1C, 0xE0, 0x03, 0xD1, 0x1C, 0xE0, 0x03,
0xD2, 0x12, 0xE0, 0x03, 0xD3, 0xF6, 0xA1, 0x01, 0xD0, 0x01,
0xA1, 0x01, 0xD0, 0x00, 0xA2, 0x01, 0xD0, 0x01, 0xA1, 0x00,
0xD3, 0xD2, 0xA0, 0x00, 0xD3, 0xD1, 0xA1, 0x01, 0xD0, 0x03,
0xA0, 0x00, 0xD0, 0xD1, 0xA1, 0x01, 0xD0, 0x01, 0xA0, 0x00,
0xD0, 0xD1, 0xA2, 0x00, 0xD1, 0xD3, 0xE0, 0x02, 0x1C, 0xD0,
0xE0, 0x01, 0xD0, 0x0F, 0xE0, 0x03, 0xD1, 0xA5, 0xE0, 0x03,
0xD2, 0x35, 0xE0, 0x03, 0xD3, 0xB1, 0xA0, 0x01, 0xD0, 0x03,
0xA1, 0x01, 0xD0, 0x00, 0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x00,
0xD2, 0xD3, 0xA2, 0x01, 0xD0, 0x00, 0xA2, 0x01, 0xD0, 0x02,
0xA0, 0x01, 0xD0, 0x03, 0xA1, 0x00, 0xD0, 0xD2, 0xA2, 0x00,
0xD1, 0xD3, 0xA0, 0x00, 0xD3, 0xD1, 0xE0, 0x02, 0x0F, 0xD0,
0xE0, 0x01, 0xD0, 0x10, 0xE0, 0x03, 0xD1, 0xE3, 0xE0, 0x03,
0xD2, 0xBE, 0xE0, 0x03, 0xD3, 0x61, 0xA1, 0x01, 0xD0, 0x02,
0xA2, 0x01, 0xD0, 0x00, 0xA0, 0x00, 0xD0, 0xD1, 0xA1, 0x01,
0xD0, 0x02, 0xA0, 0x00, 0xD1, 0xD1, 0xA0, 0x01, 0xD0, 0x00,
0xA2, 0x01, 0xD0, 0x03, 0xA2, 0x00, 0xD2, 0xD3, 0xA0, 0x00,
0xD1, 0xD1, 0xA1, 0x01, 0xD0, 0x03, 0xE0, 0x02, 0x10, 0xD0,
0xE0, 0x01, 0xD0, 0x08, 0xE0, 0x03, 0xD1, 0x2B, 0xE0, 0x03,
0xD2, 0x35, 0xE0, 0x03, 0xD3, 0xD4, 0xA0, 0x00, 0xD0, 0xD1,
0xA1, 0x01, 0xD0, 0x01, 0xA2, 0x01, 0xD0, 0x00, 0xA1, 0x01,
0xD0, 0x03, 0xA2, 0x01, 0xD0, 0x03, 0xA0, 0x00, 0xD3, 0xD1,
0xA1, 0x00, 0xD2, 0xD2, 0xA0, 0x00, 0xD2, 0xD1, 0xA0, 0x00,
0xD0, 0xD1, 0xA1, 0x00, 0xD0, 0xD2, 0xE0, 0x02, 0x08, 0xD0,
0xE0, 0x01, 0xD0, 0x01, 0xE0, 0x03, 0xD1, 0xB0, 0xE0, 0x03,
0xD2, 0xB2, 0xE0, 0x03, 0xD3, 0x5B, 0xA0, 0x00, 0xD1, 0xD1,
0xA1, 0x00, 0xD0, 0xD2, 0xA2, 0x00, 0xD1, 0xD3, 0xA0, 0x01,
0xD0, 0x00, 0xA0, 0x01, 0xD0, 0x00, 0xA2, 0x01, 0xD0, 0x00,
0xA1, 0x00, 0xD2, 0xD2, 0xA2, 0x01, 0xD0, 0x00, 0xA2, 0x00,
0xD1, 0xD3, 0xA0, 0x01, 0xD0, 0x01, 0xE0, 0x02, 0x01, 0xD0,
0xE0, 0x01, 0xD0, 0x0D, 0xE0, 0x03, 0xD1, 0xE8, 0xE0, 0x03,
0xD2, 0x39, 0xE0, 0x03, 0xD3, 0xF4, 0xA1, 0x00, 0xD2, 0xD2,
0xA0, 0x01, 0xD0, 0x00, 0xA0, 0x01, 0xD0, 0x02, 0xA1, 0x00,
0xD3, 0xD2, 0xA1, 0x00, 0xD2, 0xD2, 0xA2, 0x00, 0xD2, 0xD3,
0xA0, 0x01, 0xD0, 0x00, 0xA0, 0x00, 0xD2, 0xD1, 0xA0, 0x01,
0xD0, 0x03, 0xA0, 0x01, 0xD0, 0x01, 0xE0, 0x02, 0x0D, 0xD0,
0xE0, 0x01, 0xD0, 0x18, 0xE0, 0x03, 0xD1, 0x72, 0xE0, 0x03,
0xD2, 0xA1, 0xE0, 0x03, 0xD3, 0x7C, 0xA0, 0x01, 0xD0, 0x01,
0xA1, 0x00, 0xD2, 0xD2, 0xA1, 0x01, 0xD0, 0x00, 0xA0, 0x01,
0xD0, 0x00, 0xA1, 0x01, 0xD0, 0x00, 0xA2, 0x01, 0xD0, 0x00,
0xA0, 0x01, 0xD0, 0x03, 0xA1, 0x00, 0xD3, 0xD2, 0xA2, 0x01,
0xD0, 0x01, 0xA2, 0x00, 0xD3, 0xD3, 0xE0, 0x02, 0x18, 0xD0,
0xE0, 0x01, 0xD0, 0x0C, 0xE0, 0x03, 0xD1, 0x98, 0xE0, 0x03,
0xD2, 0xB5, 0xE0, 0x03, 0xD3, 0x2B, 0xA0, 0x01, 0xD0, 0x03,
0xA2, 0x01, 0xD0, 0x02, 0xA2, 0x01, 0xD0, 0x00, 0xA1, 0x01,
0xD0, 0x03, 0xA0, 0x00, 0xD3, 0xD1, 0xA2, 0x01, 0xD0, 0x02,
0xA1, 0x01, 0xD0, 0x01, 0xA1, 0x00, 0xD2, 0xD2, 0xA1, 0x01,
0xD0, 0x00, 0xA0, 0x01, 0xD0, 0x00, 0xE0, 0x02, 0x0C, 0xD0,
0xE0, 0x01, 0xD0, 0x1B, 0xE0, 0x03, 0xD1, 0x8D, 0xE0, 0x03,
0xD2, 0x39, 0xE0, 0x03, 0xD3, 0x4E, 0xA2, 0x01, 0xD0, 0x03,
0xA1, 0x01, 0xD0, 0x01, 0xA1, 0x01, 0xD0, 0x03, 0xA0, 0x01,
0xD0, 0x01, 0xA1, 0x01, 0xD0, 0x02, 0xA2, 0x00, 0xD1, 0xD3,
0xA1, 0x00, 0xD3, 0xD2, 0xA2, 0x01, 0xD0, 0x00, 0xA1, 0x01,
0xD0, 0x01, 0xA1, 0x00, 0xD0, 0xD2, 0xE0, 0x02, 0x1B, 0xD0,
0x00, 0x00, 0x00, 0xFF
};
int i=0,num=0;
unsigned char j=0;
unsigned char *start,*end;
//printf("%s\n",encode);
while(ida[i]!=0x00) {
start=&ida[i];
while(!(ida[i]==0xe0&&num==4)) {
if(ida[i]==0xe0){
num++;
}
i=i+4;
}
num=0;
end=&ida[i];
for(j=0;j<=256;j++) {
reg[0]=j;
exp(start+4,end);
if(reg[0]==encode[end[2]]){
encode[end[2]]=j;
//printf("0x%x\n",j);
break;
}
}
i+=4;
}
printf("%s",encode);
}
void exp(unsigned char *start,unsigned char *end) {
unsigned char *flag;
unsigned char num;
// printf("start == 0x%x end == 0x%x\n",start,(end));
//printf("*start == 0x%x *end == 0x%x",*start,*(end));
for(flag=start;flag!=end;flag+=4) {
num =*flag;
if(num==0xe0){
mov(flag);
}
else if(num==0xA2) {
sub(flag);
}
else if(num==0xa0){
xor(flag);
}
else if (num==0xa1){
add(flag);
}
}
}
void mov(unsigned char *a1) {
unsigned char result;
if(a1[1]) {
if(a1[1]==3){
reg[a1[2]-0xd0]=a1[3];
}
}
else {
result=reg[a1[2]-0xd0];
reg[a1[3]-0xd0]=result;
}
}
void add(unsigned char *a1) {
if(a1[1]) {
if(a1[1]==1)
reg[a1[2]-0xd0]+=a1[3];
}
else {
reg[a1[2]-0xd0]+=reg[a1[3]-0xd0];
}
}
void sub(unsigned char *a1) {
if(a1[1]) {
if(a1[1]==1)
reg[a1[2]-0xd0]-=a1[3];
}
else {
reg[a1[2]-0xd0]-=reg[a1[3]-0xd0];
}
}
void xor(unsigned char *a1) {
if(a1[1]) {
if(a1[1]==1)
reg[a1[2]-0xd0]^=a1[3];
}
else {
reg[a1[2]-0xd0]^=reg[a1[3]-0xd0];
}
}
Petals Level Up (easy)
f5之后发现有花指令,直接去具体地址patch一下
,进入这个loc_120d的地方,发现就是一个初始化盒子,然后下面还有个花指令,我改了半天也没patch出来,然后直接选择分析了汇编
看汇编这段花指令中想隐藏的就是这段代码,大概的意思就是,拿盒子对input的输入的数字进行加密大概就是input[i]=box[input[i]]
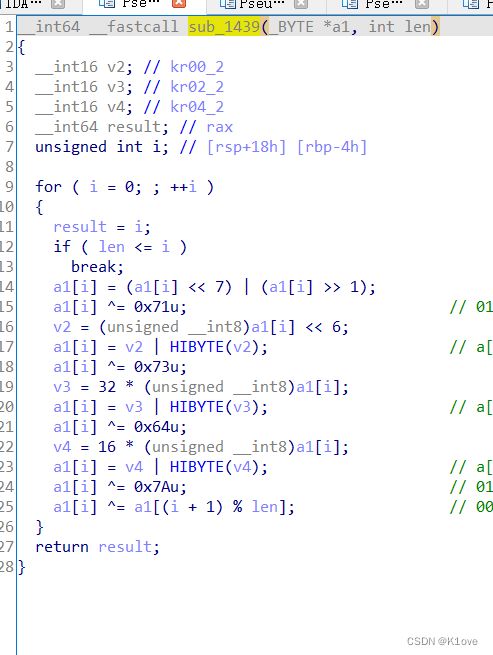
根据下面的花指令中的汇编代码找到sub_1439函数也就是关键函数
这一段加密其实就是移位运算和异或运算,是可逆的,一点点来
#include
void decode2(unsigned char a[]);
void decode1(unsigned char a[]);
void f(unsigned char a[]);
int main() {
unsigned char enc[] =
{
0xB3, 0x79, 0xF1, 0x70, 0xB3, 0x79, 0xF1, 0x70, 0xB3, 0x31,
0xC3, 0x6E, 0x24, 0xE3, 0x7C, 0xFF, 0xDA, 0xF9, 0x75, 0xF2,
0x60, 0xBF, 0x33, 0xE3, 0x65, 0xA6, 0x62, 0x2A, 0x65, 0x24,
0xB4, 0xBA
};
decode1(enc);
decode2(enc);
printf("%s",enc);
}
void decode1(unsigned char a[]) {
int i=0,len=32;
for(i=31;i>=0;i--) {
a[i]^=a[(i+1)%len];
a[i]^=0x7a;
a[i] = a[i]>>4|a[i]<<4;
a[i]^=0x64;
a[i]=a[i]<<3|a[i]>>5;
a[i]^=0x73;
a[i]=a[i]<<2|a[i]>>6;
a[i]^=0x71;
a[i]=a[i]>>7|a[i]<<1;
}
}
void decode2(unsigned char a[]) {
int i=0,len=32,j;
unsigned char b[300]={0};
for (int i=0;i<256;i++) {
b[i]=~(i^32);
// printf("%x ",b[i]);
}
for (i=0;i babycode (middle)
根据提示是llvm的中间代码,然后直接上了llvm的官网文档,最后可以变成elf文件就可以把其拖入ida中进行我们的算法逆向拉!!
根据提示魔改的base64和rc4,就看看他是怎么魔改的吧,先看看base64吧
就是去掉了base64的表,根据我给的注释很容易就可以写出逆向脚本,rc4中也就是多了一个异或运算,逆出来了也不难,唯一有点恶心的地方我认为他就是分了俩次加密,第二次rc4加密盒子会变,他先加密前16个字符,再解密剩下的字符,途中还经历前后异或,所以我们进行后半部分解密的时候rc4的盒子要进行变化。
#include
unsigned char s[300],t[300];
void b64decode(unsigned char * enc,unsigned char* dec);
void rc4_decode1(int len, unsigned char *enc);
void rc4_init(char *key,int len);
void rc4_decode2(int len, unsigned char *enc);
int main() {
unsigned char enc[50]="TSz`kWKgbMHszXaj`@kLBmRrnTxsNtZsSOtZzqYikCw=";
unsigned char dec1[50]={0x00};
char key[10] ="llvmbitc";
unsigned char a[50];
int i=0;
b64decode(enc,dec1);
rc4_init(key,8);
rc4_decode1(16,&dec1[16]);
for(i=0;i<16;i++) {
dec1[i+16]^=dec1[i];
}
rc4_init(key,8);
rc4_decode2(16,dec1);
printf("%s",dec1);
return 0;
}
void b64decode(unsigned char * enc,unsigned char* dec) {
int i=0,j=0;
for(i=0;i<40;i+=4) {
dec[j] = ((enc[i]-59)<<2)&0xfc | (((enc[i+2]-59)>>4))&3;
dec[j+1] = (((enc[i+2]-59)&0xf)<<4) | (((enc[i+1]-59)>>2)&0xf);
dec[j+2] = (((enc[i+1]-59)&3)<<6) | ((enc[i+3]-59)&0x3f);
j+=3;
}
dec[j] = ((enc[i]-59)<<2)&0xfc | (((enc[i+1]-59)>>4))&3;
dec[j+1] = (((enc[i+2]-59)>>2)&0xf) | (((enc[i+1]-59)<<4)&0xf0);
dec[j+2]=0;
}
void rc4_init(char *key,int len) {
int i=0,v5=0;
unsigned char temp;
for(i=0;i<256;i++) {
s[i] =i;
t[i] = key[i%len];
}
for(i=0;i<256;i++) {
v5=(s[i]+t[i]+v5)%256;
temp = s[i];
s[i]= s[v5];
s[v5]=temp;
}
}
void rc4_decode1(int len, unsigned char *enc) {
int v3=0,v5=0,i,j;
unsigned char temp;
for(i=0;i